厳密検証されたNSE7_OTS-6.4試験問題集と解答で無料提供のNSE7_OTS-6.4問題と正解付き
あなたを合格させるNSE7_OTS-6.4問題集で無料最新Fortinet練習テスト
Fortinet NSE7_OTS-6.4 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
質問 12
Refer to the exhibit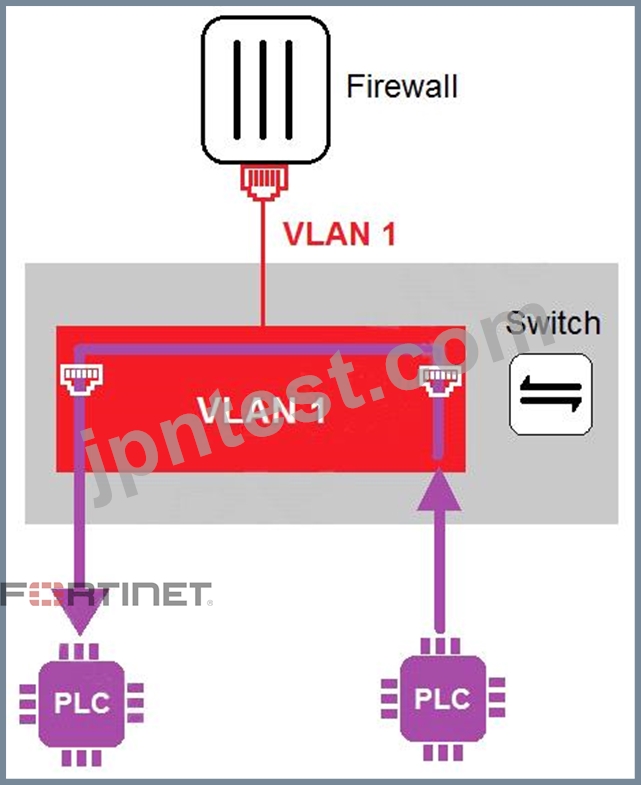
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A. There is no micro-segmentation in this topology.
- B. PLCs use IEEE802.1Q protocol to communicate each other.
- C. An administrator can create firewall policies in the switch to secure between PLCs.
- D. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
正解: A
質問 13
An OT architect has deployed a Layer 2 switch in the OT network at Level 1 the Purdue model-process control. The purpose of the Layer 2 switch is to segment traffic between PLC1 and PLC2 with two VLANs. All the traffic between PLC1 and PLC2 must first flow through the Layer 2 switch and then through the FortiGate device in the Level 2 supervisory control network.
What statement about the traffic between PLC1 and PLC2 is true?
- A. The Layer 2 switch rewrites VLAN tags before sending traffic to the FortiGate device.
- B. PLC1 and PLC2 traffic must flow through the Layer-2 switch trunk link to the FortiGate device.
- C. The Layer 2 switches routes any traffic to the FortiGate device through an Ethernet link.
- D. In order to communicate, PLC1 must be in the same VLAN as PLC2.
正解: B
質問 14
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Local authentication on FortiGate
- B. FSSO authentication on FortiGate
- C. Two-factor authentication on FortiAuthenticator
- D. Role-based authentication on FortiNAC
正解: C,D
質問 15
Refer to the exhibit.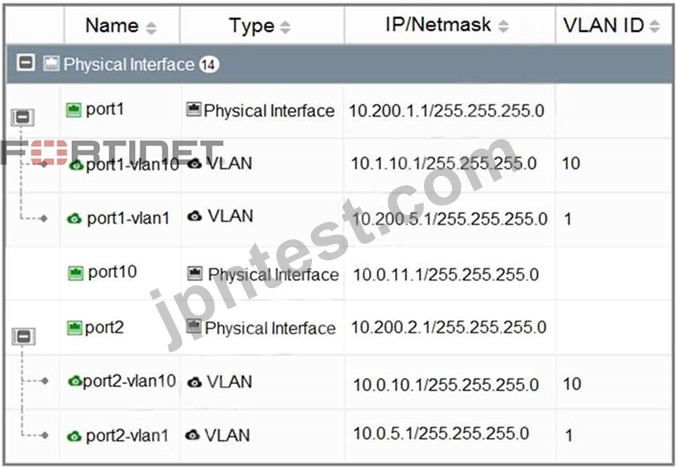
Which statement about the interfaces shown in the exhibit is true?
- A. port1-vlan10 and port2-vlan10 are part of the same broadcast domain
- B. port2, port2-vlan10, and port2-vlan1 are part of the software switch interface.
- C. The VLAN ID of port1-vlan1 can be changed to the VLAN ID 10.
- D. port1, port1-vlan10, and port1-vlan1 are in different broadcast domains
正解: D
質問 16
Which three common breach points can be found in a typical OT environment? (Choose three.)
- A. Black hat
- B. Global hat
- C. Hard hat
- D. VLAN exploits
- E. RTU exploits
正解: A,D,E
質問 17
Refer to the exhibit.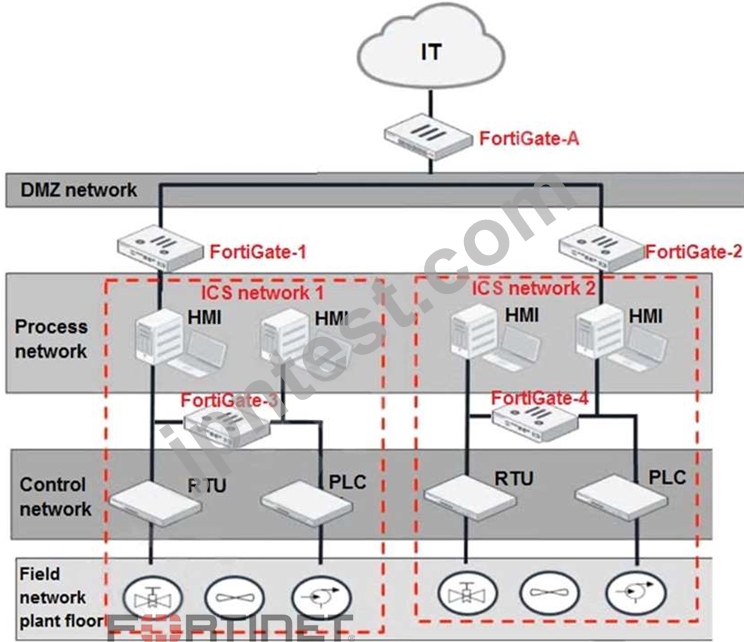
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
- A. Firewall policies should be configured on FortiGate-3 and FortiGate-4 with industrial protocol sensors.
- B. Micro-segmentation can be achieved only by replacing FortiGate-3 and FortiGate-4 with a pair of FortiSwitch devices.
- C. IT and OT networks are separated by segmentation.
- D. FortiGate-3 and FortiGate-4 devices must be in a transparent mode.
正解: C,D
質問 18
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A. Under config user settings configure set auth-on-demand implicit.
- B. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
- C. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- D. Enable two-factor authentication with FSSO.
正解: A
質問 19
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
- A. FortiGate determined the user by passive authentication
- B. The user was determined by Security Fabric
- C. FortiNAC determined the user by DHCP fingerprint method
- D. Two-factor authentication is not configured with RADIUS authentication method
正解: C
質問 20
Refer to the exhibit, which shows a non-protected OT environment.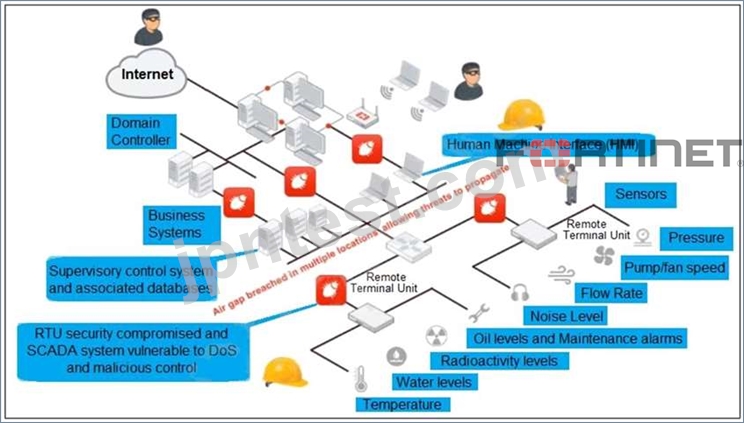
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A. Configure firewall policies with industrial protocol sensors
- B. Deploy a FortiGate device within each ICS network.
- C. Use segmentation
- D. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- E. Configure firewall policies with web filter to protect the different ICS networks.
正解: A,D,E
質問 21
Refer to the exhibit.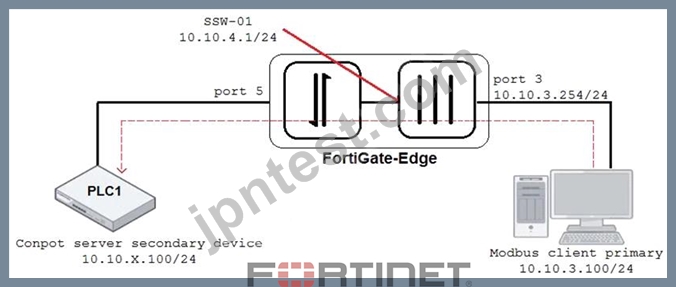
An OT architect has implemented a Modbus TCP with a simulation server Conpot to identify and control the Modus traffic in the OT network. The FortiGate-Edge device is configured with a software switch interface ssw-01.
Based on the topology shown in the exhibit, which two statements about the successful simulation of traffic between client and server are true? (Choose two.)
- A. NAT is disabled in the FortiGate firewall policy from port3 to ssw-01.
- B. Port5 is not a member of the software switch.
- C. The FortiGate devices is in offline IDS mode.
- D. The FortiGate-Edge device must be in NAT mode.
正解: C,D
質問 22
What are two benefits of a Nozomi integration with FortiNAC? (Choose two.)
- A. Enhanced point of connection details
- B. Direct VLAN assignment
- C. Adapter consolidation for multi-adapter hosts
- D. Importation and classification of hosts
正解: A,B
質問 23
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM.
Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
- A. List
- B. Risk
- C. IPS
- D. Security
- E. Overview
正解: A,B,E
質問 24
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
- A. SNMP
- B. ICMP
- C. RADIUS
- D. API
- E. TACACS
正解: A,C,D
質問 25
An OT administrator configured and ran a default application risk and control report in FortiAnalyzer to learn more about the key application crossing the network. However, the report output is empty despite the fact that some related real-time and historical logs are visible in the FortiAnalyzer.
What are two possible reasons why the report output was empty? (Choose two.)
- A. The administrator selected the wrong hcache table for the report.
- B. The administrator selected the wrong time period for the report.
- C. The administrator selected the wrong devices in the Devices section.
- D. The administrator selected the wrong logs to be indexed in FortiAnalyzer.
正解: A,B
質問 26
......
無料でゲット!高評価Fortinet NSE7_OTS-6.4試験問題集今すぐダウンロード!:https://www.jpntest.com/shiken/NSE7_OTS-6.4-mondaishu
