PDF問題(2023年最新)実際のPalo Alto Networks PCNSE試験問題
問題集返金保証付きのPCNSE問題集には90%オフされます
質問 63
Which option would an administrator choose to define the certificate and protocol that Panorama and its
managed devices use for SSL/TLS services?
- A. Configure a Decryption Profile and select SSL/TLS services.
- B. Set up Security policy rule to allow SSL communication.
- C. Configure an SSL/TLS Profile.
- D. Set up SSL/TLS under Polices > Service/URL Category>Service.
正解: C
解説:
Explanation/Reference:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/web-interface-help/device/device-
certificate-management-ssltls-service-profile
質問 64
Refer to the exhibit.
An administrator is using DNAT to map two servers to a single public IP address. Traffic will be steered to the specific server based on the application, where Host A (10.1.1.100) receives HTTP traffic and HOST B (10.1.1.101) receives SSH traffic.) Which two security policy rules will accomplish this configuration? (Choose two.)
- A. Untrust (Any) to DMZ (10.1.1.100.10.1.1.101), ssh, web-browsing -Allow
- B. Untrust (Any) to DMZ (1.1.1.100), web-browsing -Allow
- C. Untrust (Any) to DMZ (1.1.1.100), SSH -Allow
- D. Untrust (Any) to Untrust (10.1.1.1), web-browsing -Allow
- E. Untrust (Any) to Untrust (10.1.1.1), SSH -Allow
正解: B,C
解説:
https://docs.paloaltonetworks.com/pan-os/8-0/pan-os-admin/networking/nat/nat-configuration-examples/destination-nat-exampleone-to-many-mapping#
質問 65
In a device group, which two configuration objects are defined? (Choose two )
- A. SSL/TLS profiles
- B. address groups
- C. URL Filtering profiles
- D. DNS Proxy
正解: B,C
解説:
Objects are configuration elements that policy rules reference, for example: IP addresses, URL categories, security profiles, users, services, and applications. Rules of any type (pre-rules, post- rules, default rules, and rules locally defined on a firewall) and any rulebase (Security, NAT, QoS, Policy Based Forwarding, Decryption, Application Override, Captive Portal, and DoS Protection) can reference objects.
https://docs.paloaltonetworks.com/panorama/8-1/panorama-admin/panorama- overview/centralized-firewall-configuration-and-update-management/device-groups/device-group- objects.html#id0fee714c-9e17-43a0-aac5-54e0c34f37e3
質問 66
Which Panorama objects restrict administrative access to specific device-groups?
- A. authentication profiles
- B. admin roles
- C. templates
- D. access domains
正解: D
解説:
Explanation
Access domains control administrative access to specific Device Groups and templates, and also control the ability to switch context to the web interface of managed firewalls.
https://docs.paloaltonetworks.com/panorama/10-1/panorama-admin/panorama-overview/role-based-access-contr
質問 67
Which Captive Portal mode must be configured to support MFA authentication?
- A. NTLM
- B. Transparent
- C. Redirect
- D. Single Sign-On
正解: C
解説:
Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan- os/authentication/configure-multi-factor-authentication
質問 68
A company wants to use their Active Directory groups to simplify their Security policy creation from Panorama.
Which configuration is necessary to retrieve groups from Panorama?
- A. Configure a group mapping profile to retrieve the groups in the target template.
- B. Configure an LDAP Server profile and enable the User-ID service on the management interface.
- C. Configure a master device within the device groups.
- D. Configure a Data Redistribution Agent to receive IP User Mappings from User-ID agents.
正解: C
解説:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClFQCA0
質問 69
Which User-ID method maps IP address to usernames for users connecting through a web proxy that has already authenticated the user?
- A. Port mapping
- B. Client Probing
- C. Server monitoring
- D. Syslog listening
正解: D
解説:
Explanation
To obtain user mappings from existing network services that authenticate users-such as wireless controllers, 802.1x devices, Apple Open Directory servers, proxy servers, or other Network Access Control (NAC) mechanisms-Configure User-ID to Monitor Syslog Senders for User Mapping.While you can configure either the Windows agent or the PAN-OS integrated User-ID agent on the firewall to l isten for authentication syslog messages from the network services, because only the PAN-OS integrated agent supports syslog listening over TLS, it is the preferred configuration.
質問 70
An administrator needs to troubleshoot a User-ID deployment. The administrator believes that there is an issue related to LDAP authentication. The administrator wants to create a packet capture on the management plane.
Which CLI command should the administrator use to obtain the packet capture for validating the configuration?
- A. > ftp export mgmt-pcap from mgmt.pcap to <FTP host>
- B. > scp export pcap from pcap to (usernameQhost:path)
- C. > scp export poap-mgmt from poap.mgmt to (username@host:path)
- D. > scp export mgmt-pcap from mgmt.pcap to (username@host:path)
正解: D
解説:
Additionally, you can manually export the PCAP via SCP or TFTP, i.e.:
> scp export mgmt-pcap from mgmt.pcap to
<value> Destination (username@host:path)
Ref: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000CleECAS
質問 71
An administrator sees several inbound sessions identified as unknown-tcp in the traffic logs. The administrator determines that these sessions are from external users accessing the company's proprietary accounting application. The administrator wants to reliably identify this as their accounting application and to scan this traffic for threats. Which option would achieve this result?
- A. Create a custom App-ID and use the "ordered conditions" check box
- B. Create an Application Override policy
- C. Create a custom App ID and enable scanning on the advanced tab
- D. Create an Application Override policy and a custom threat signature for the application
正解: C
質問 72
An administrator is configuring an IPSec VPN to a Cisco ASA at the administrator's home and experiencing issues completing the connection. the following is the output from the command:
What could be the cause of this problem?
- A. The public IP addresses do not match for both the Palo Alto Networks Firewall and the ASA.
- B. The dead peer detection settings do not match between the Palo Alto Networks Firewall and the ASA.
- C. The shared secrets do not match between the Palo Alto Networks Firewall and the ASA.
- D. The Proxy IDs on the Palo Alto Networks Firewall do not match the setting on the ASA.
正解: A
質問 73
Which log file can be used to identify SSL decryption failures?
- A. Configuration
- B. Traffic
- C. ACC
- D. Threats
正解: B
解説: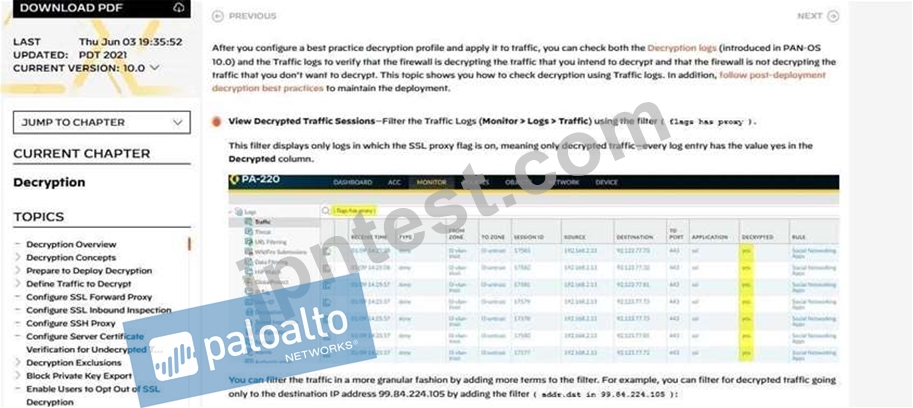
https://docs.paloaltonetworks.com/pan-os/10-0/pan-os-admin/decryption/verify-decryption.html
質問 74
What is the purpose of the firewall decryption broker?
- A. force decryption of previously unknown cipher suites
- B. decrypt SSL traffic and then send it as cleartext to a security chain of inspection tools.
- C. reduce SSL traffic to a weaker cipher before sending it to a security chain of inspection tools.
- D. inspect traffic within IPsec tunnels
正解: B
解説:
Explanation/Reference: https://www.paloaltonetworks.com/documentation/81/pan-os/newfeaturesguide/decryption- features/decryption-broker
質問 75
What can be used to create dynamic address groups?
- A. region objects
- B. dynamic address
- C. tags
- D. FODN addresses
正解: C
質問 76
An engineer must configure the Decryption Broker feature.
Which Decryption Broker security chain supports bi-directional traffic flow?
- A. Layer 2 security chain
- B. Layer 3 security chain
- C. Transparent Proxy security chain
- D. Transparent Bridge security chain
正解: B
解説:
Together, the primary and secondary interfaces form a pair of decryption forwarding interfaces.
Only interfaces that you have enabled to be Decrypt Forward interfaces are displayed here. Your security chain type (Layer 3 or Transparent Bridge) and the traffic flow direction (unidirectional or bidirectional) determine which of the two interfaces forwards allowed, clear text traffic to the security chain, and which interface receives the traffic back from the security chain after it has undergone additional enforcement.
質問 77
Which two interface types can be used when configuring GlobalProtect Portal?(Choose two)
- A. Loopback
- B. Virtual Wire
- C. Tunnel
- D. Layer 3
正解: A,D
質問 78
The SSL Forward Proxy decryption policy is configured. The following four certificate authority (CA) certificates are installed on the firewall.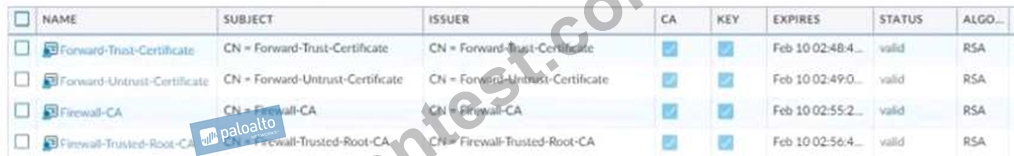
Which certificate authority (CA) certificate will be used to sign the untrusted webserver certificate?
- A. Firewall-CA
- B. Firewall-Trusted-Root-CA
- C. Forward-Trust-Certificate
- D. Forward-Untrust-Certificate
正解: C
質問 79
What should an administrator consider when planning to revert Panorama to a pre-PAN-OS 8.1 version?
- A. Administrators need to manually update variable characters to those used in pre-PAN-OS 8.1.
- B. An administrator must use the Expedition tool to adapt the configuration to the pre-PAN-OS 8.1 state.
- C. When Panorama is reverted to an earlier PAN-OS release, variables used in templates or template stacks will be removed automatically.
- D. Panorama cannot be reverted to an earlier PAN-OS release if variables are used in templates or template stacks.
正解: D
解説:
You are unable to downgrade from PAN-OS 8.1 to an earlier PAN-OS release if variables are used in your template or template stack configuration. Variables must be removed from the template and template stack configuration to downgrade.
質問 80
An engineer is troubleshooting traffic routing through the virtual router. The firewall uses multiple routing protocols, and the engineer is trying to determine routing priority Match the default Administrative Distances for each routing protocol.
正解:
解説:
質問 81
......
Palo Alto Networks PCNSE 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
更新された2023年03月合格させるPCNSE試験リアル練習テスト問題:https://www.jpntest.com/shiken/PCNSE-mondaishu
