リアルな156-315.80は100%カバー試験問題をゲット [2022年10月]
問題集まとめ概要は156-315.80試験問題集はここ
質問 119
What is the recommended number of physical network interfaces in a Mobile Access cluster deployment?
- A. 1 Interface - an interface leading to the organization and the Internet, and configure for synchronization.
- B. 4 Interfaces - an interface leading to the organization, a second interface leading to the internet, a third interface for synchronization, a fourth interface leading to the Security Management Server.
- C. 2 Interfaces - a data interface leading to the organization and the Internet, a second interface for synchronization.
- D. 3 Interfaces - an interface leading to the organization, a second interface leading to the Internet, a third interface for synchronization.
正解: D
質問 120
The fwd process on the Security Gateway sends logs to the fwd process on the Management Server via which 2 processes?
- A. fwd via cpm
- B. cpm via cpd
- C. fwd via cpd
- D. fwm via fwd
正解: A
質問 121
Which Check Point feature enables application scanning and the detection?
- A. Application Dictionary
- B. AppWiki
- C. CPApp
- D. Application Library
正解: B
質問 122
In what way are SSL VPN and IPSec VPN different?
- A. IPSec VPN uses an additional virtual adapter; SSL VPN uses the client network adapter only.
- B. IPSec VPN does not support two factor authentication, SSL VPN does support this
- C. SSL VPN is using HTTPS in addition to IKE, whereas IPSec VPN is clientless
- D. SSL VPN adds an extra VPN header to the packet, IPSec VPN does not
正解: A
質問 123
What is the purpose of Priority Delta in VRRP?
- A. When a box fail, Effective Priority = Priority - Priority Delta
- B. When a box up, Effective Priority = Priority + Priority Delta
- C. When an Interface fail, Effective Priority = Priority - Priority Delta
- D. When an Interface is up, Effective Priority = Priority + Priority Delta
正解: C
解説:
Explanation/Reference:
Explanation:
Each instance of VRRP running on a supported interface may monitor the link state of other interfaces.
The monitored interfaces do not have to be running VRRP.
If a monitored interface loses its link state, then VRRP will decrement its priority over a VRID by the specified delta value and then will send out a new VRRP HELLO packet. If the new effective priority is less than the priority a backup platform has, then the backup platform will beging to send out its own HELLO packet.
Once the master sees this packet with a priority greater than its own, then it releases the VIP.
Reference: https://supportcenter.checkpoint.com/supportcenter/portal?
eventSubmit_doGoviewsolutiondetails=&solutionid=sk38524
質問 124
To accelerate the rate of connection establishment, SecureXL groups all connection that match a particular service and whose sole differentiating element is the source port. The type of grouping enables even the very first packets of a TCP handshake to be accelerated. The first packets of the first connection on the same service will be forwarded to the Firewall kernel which will then create a template of the connection. Which of the these is NOT a SecureXL template?
- A. Deny Template
- B. Drop Template
- C. NAT Template
- D. Accept Template
正解: A
質問 125
What will be the effect of running the following command on the Security Management Server?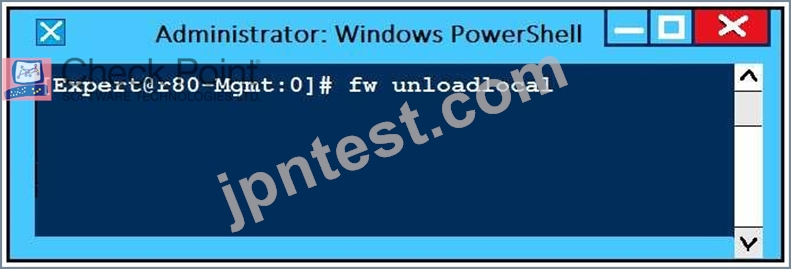
- A. Reset SIC on all gateways.
- B. Remove the local ACL lists.
- C. No effect.
- D. Remove the installed Security Policy.
正解: D
解説:
Explanation/Reference: https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/6751.htm
質問 126
Which one of the following is true about Capsule Connect?
- A. It is a full layer 3 VPN client
- B. It offers full enterprise mobility management
- C. It does not support all VPN authentication methods
- D. It is supported only on iOS phones and Windows PCs
正解: A
質問 127
CoreXL is NOT supported when one of the following features is enabled: (Choose three)
- A. Overlapping NAT
- B. Route-based VPN
- C. IPv6
- D. IPS
正解: A,B,C
解説:
Explanation
CoreXL does not support Check Point Suite with these features:
* Check Point QoS (Quality of Service)
* Route-based VPN
* IPv6 on IPSO
* Overlapping NAT
質問 128
Which features are only supported with R80.10 Gateways but not R77.x?
- A. The rule base can be built of layers, each containing a set of the security rules. Layers are inspected in
the order in which they are defined, allowing control over the rule base flow and which security
functionalities take precedence. - B. Limits the upload and download throughput for streaming media in the company to 1 Gbps.
- C. Access Control policy unifies the Firewall, Application Control & URL Filtering, Data Awareness, and
Mobile Access Software Blade policies - D. Time object to a rule to make the rule active only during specified times.
正解: A
質問 129
Which firewall daemon is responsible for the FW CLI commands?
- A. fwm
- B. fwd
- C. cpm
- D. cpd
正解: B
質問 130
Here you can see and search records of action done by R80 SmartConsole administrations?
- A. In the Logs $ Monitor view select:"open Adult Log view"
- B. In Smartview Tracker, open action log
- C. In Smartlog all logs
- D. In SmartAdult Log view
正解: A
質問 131
What is the valid range for Virtual Router Identifier (VRID) value in a Virtual Routing Redundancy Protocol (VRRP) configuration?
- A. 1-255
- B. 1-254
- C. 0-254
- D. 0 - 255
正解: A
質問 132
What is the recommended configuration when the customer requires SmartLog indexing for 14 days and SmartEvent to keep events for 180 days?
- A. Install Management and SmartEvent on different machines.
- B. Choose different setting for log storage and SmartEvent db
- C. it is not possible.
- D. Use Multi-Domain Management Server.
正解: B
質問 133
How would you enable VMAC Mode in ClusterXL?
- A. Cluster Object -> Edit -> ClusterXL and VRRP -> Use Virtual MAC
- B. Cluster Object -> Edit -> Cluster Members -> Edit -> Use Virtual MAC
- C. cphaconf vmac_mode set 1
- D. fw ctl set int vmac_mode 1
正解: A
質問 134
To add a file to the Threat Prevention Whitelist, what two items are needed?
- A. MD5 signature and Gateway
- B. File name and Gateway
- C. Object Name and MD5 signature
- D. IP address of Management Server and Gateway
正解: C
質問 135
Check Point APIs allow system engineers and developers to make changes to their organization's security policy with CLI tools and Web Services for all the following except:
- A. Create products that use and enhance 3rd party solutions
- B. Execute automated scripts to perform common tasks
- C. Create new dashboards to manage 3rd party task
- D. Create products that use and enhance the Check Point Solution
正解: C
解説:
Explanation
Check Point APIs let system administrators and developers make changes to the security policy with CLI tools and web-services. You can use an API to:
* Use an automated script to perform common tasks
* Integrate Check Point products with 3rd party solutions
* Create products that use and enhance the Check Point solution
References:
質問 136
When gathering information about a gateway using CPINFO, what information is included or excluded when using the "-x" parameter?
- A. Includes the registry
- B. Does not resolve network addresses
- C. Gets information about the specified Virtual System
- D. Output excludes connection table
正解: C
解説:
Explanation/Reference: https://www.networksecurityplus.net/2015/02/check-point-how-to-collect-cpinfo-cli.html
質問 137
Which file contains the host address to be published, the MAC address that needs to be associated with the IP Address, and the unique IP of the interface that responds to ARP request?
- A. /opt/CPshrd-R80/conf/local.arp
- B. /var/opt/CPshrd-R80/conf/local.arp
- C. $CPDIR/conf/local.arp
- D. $FWDIR/conf/local.arp
正解: D
質問 138
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- A. Limits the upload and download throughput for streaming media in the company to 1 Gbps.
- B. Time object to a rule to make the rule active only during specified times.
- C. Sub Policies are sets of rules that can be created and attached to specific rules. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule.
- D. The rule base can be built of layers, each containing a set of the security rules. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
正解: C
質問 139
Which statement is correct about the Sticky Decision Function?
- A. It is automatically disabled if the Mobile Access Software Blade is enabled on the cluster
- B. It is not supported with either the Performance pack of a hardware based accelerator card
- C. It is not required L2TP traffic
- D. Does not support SPI's when configured for Load Sharing
正解: B
解説:
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_ClusterXL_AdminGuide/7290.htm
質問 140
When running a query on your logs, to find records for user Toni with machine IP of 10.0.4.210 but exclude her tablet IP of 10.0.4.76, which of the following query syntax would you use?
- A. To** AND 10.0.4.210 NOT 10.0.4.76
- B. "Toni" AND 10.0.4.210 NOT 10.0.4.76
- C. Ton* AND 10.0.4.210 NOT 10.0.4.75
- D. Toni? AND 10.0.4.210 NOT 10.0.4.76
正解: B
質問 141
By default, which port does the WebUI listen on?
- A. 0
- B. 1
- C. 2
- D. 3
正解: C
解説:
References:
質問 142
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- A. Limits the upload and download throughput for streaming media in the company to 1 Gbps.
- B. Sub Policies ae sets of rules that can be created and attached to specific rules. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule.
- C. Time object to a rule to make the rule active only during specified times.
- D. The rule base can be built of layers, each containing a set of the security rules. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
正解: B
解説:
References:
質問 143
Which statement is correct about the Sticky Decision Function?
- A. It is automatically disabled if the Mobile Access Software Blade is enabled on the cluster
- B. It is not supported with either the Performance pack of a hardware based accelerator card
- C. It is not required L2TP traffic
- D. Does not support SPI's when configured for Load Sharing
正解: B
解説:
References:
質問 144
......
CheckPoint 156-315.80 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
認定トレーニングは156-315.80試験問題集テストエンジン:https://www.jpntest.com/shiken/156-315.80-mondaishu
