更新された2022年02月28日検証済み!5V0-91.20問題集と解答で100%合格できる
2022年最新のの問題5V0-91.20問題集を試そう!更新されたVMware試験合格させます
VMware 5V0-91.20 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
質問 68
An Enterprise EDR administrator sees the process in the graphic on the Investigate page but does not see an alert for this process:
How can the administrator generate an alert for future hits against this watchlist?
- A. select the watchlist on the watchlists page, select the Scheduled Task Created report, and use Take Action to select Alert on hit for the report.
- B. Select the watchlist on the watchlists page, use Take Action to select Edit, and select Alert on hit.
- C. Select the watchlist on the watchlists page, select the Scheduled Task Created report, and use Take Action to toggle Alert on hit to On.
- D. Select the watchlist on the watchlists page and click on Alerts: Off to toggle the alerts to On.
正解: B
質問 69
What occurs when an administrator selects "Enable private logging level" in Sensor Settings under Policy?
- A. Live Response is disabled.
- B. Script Files that have unknown reputations are not uploaded.
- C. Domain names are obfuscated.
- D. Delay execute for cloud scan is disabled.
正解: B
質問 70
An administrator observes the following event detail in the Investigate tab for an application with an unknown reputation making network connections:
Upon further review of the event details returned, the reputation is observed as NOT_LISTED, and the applied (cloud) reputation is UNKNOWN.
Why is the applied (cloud) reputation UNKNOWN and not NOT_LISTED?
- A. The application was UNKNOWN at the time of the event but then later determined to be NOT_LISTED.
- B. NOT_LISTED was applied by the sensor after observing no cloud reputation, as evidenced by the applied cloud reputation UNKNOWN.
- C. The sensor demoted the local reputation from NOT_LISTED to UNKNOWN based on the cloud reputation.
- D. The sensor demoted the local reputation from UNKNOWN to NOT_LISTED based on the coud reputation.
正解: A
質問 71
An analyst is investigating an alert within Enterprise EDR. The alert is tied to an unusual process name. When navigating to the binary details page, for the binary used in the alert, the analyst sees the following: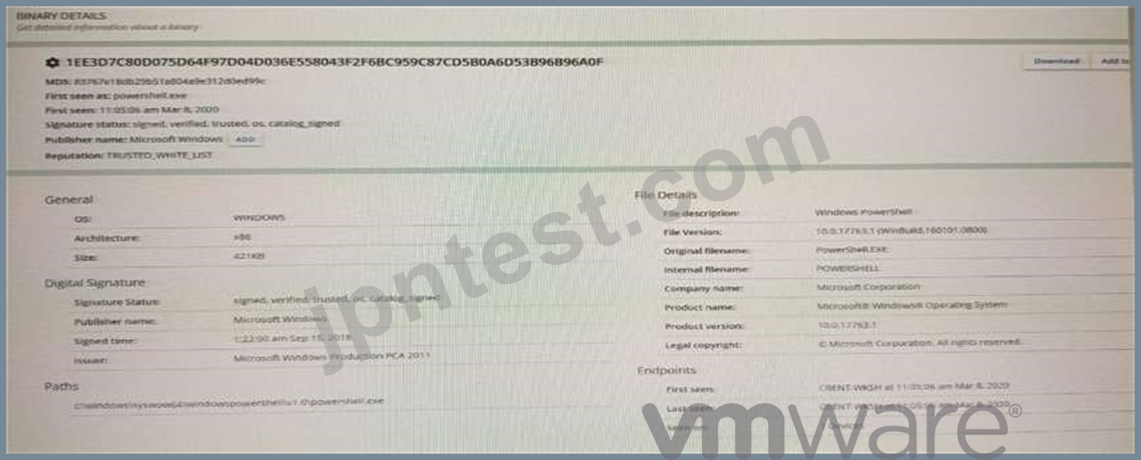
The analyst wants to find any instances of this process executing regardless of the process name used.
Which two details from the binary can be used to search for the application regardless of the seen name?
(Choose two.)
- A. The original filename
- B. The path
- C. The publisher name
- D. The product version
- E. The binary's hash
正解: B,D
質問 72
Which enforcement level does not block unapproved files but will block files that have been specifically banned?
- A. Low Enforcement
The protection level applied to computers running the App Control
Agent. A range of levels from High (Block Unapproved) to None
(Disabled) enable you to specify the level of file blocking required. - B. Disabled
- C. Medium Enforcement
- D. Visibility
正解: B
質問 73
An analyst is investigating an alert within Enterprise EDR on the process analysis page. The process tree can be seen below: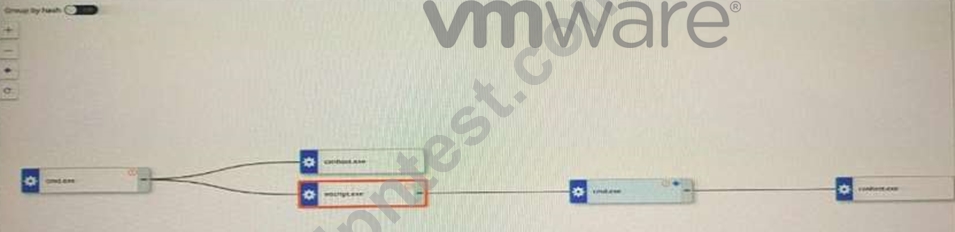
Which statement accurately characterizes this situation?
- A. The analyst navigated to this process analysis page from the wscrlpt.exe process.
- B. Several nodes in this process tree have watchlist hits.
- C. The solid line between the nodes denotes a process was injected into by another process.
- D. Conhost.exe has one or more child processes.
正解: C
質問 74
Examine the following EDR query:
file_desc:"Windows Command Processor" AND -process_name:cmd.exe
Which process will show in the query results?
- A. Any process named something other than cmd.exe with the file description of "Windows Command Processor"
- B. Any process with the binary file description "Windows Command Processor" named cmd.exe
- C. Any process named cmd.exe
- D. Any process with the binary file description "Windows Command Processor"
正解: B
質問 75
An administrator needs to query all endpoints in the HR group for instances of an obfuscated copy of cmd.exe.
Given this Enterprise EDR query:
process_name:cmd.exe AND device_group:HR AND NOT enriched:true
Which example could be added to the query to provide the desired results?
- A. NOT process_original_filename:cmd.exe
- B. NOT process_company_name:cmd.exe
- C. NOT process_name:cmd.exe
- D. NOT process_internal_name:cmd.exe
正解: C
質問 76
Refer to the exhibit: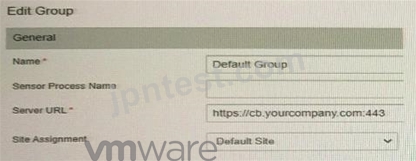
Which statement is true in regards to communication between the sensor and server?
- A. The sensor will communicate on a non-default port.
- B. The server must have an entry in the host file for cb.yourcompany.com.
- C. The communication is unencrypted.
- D. The sensor must be able to resolve the name cb.yourcompany.com.
正解: C
質問 77
Which Live Query statement is properly constructed?
- A. select from users;
- B. SELECT * FROM 'users'
- C. SELECT * FROM users;
- D. select * from *:
正解: C
質問 78
Which actions are available for Permissions?
- A. Deny Operation, Terminate Process
- B. Performs any Operation, Runs or is running
- C. Approve, Upload, No Upload
- D. Allow, Allow & Log, Bypass
正解: D
質問 79
When dismissing alerts, when should an administrator select "If alert occurs in the future, automatically dismiss it from all devices"?
- A. When the administrator wishes to apply this action to all future alerts from the device
- B. When the administrator wishes to be notified again to this behavior
- C. When the administrator wishes to mark the alert instance as a false positive
- D. When the administrator wishes to remove the alert
正解: A
質問 80
An administrator is searching for any child processes of email clients with this query in Carbon Black Enterprise EDR:
parent_name:outlook.exe OR parent_name:thunderbird.exe OR parent_name:eudora.exe The administrator would like to modify this query to only show child processes that do not have a known reputation in the Carbon Black Cloud.
Which search field can be added to the query to show the desired results?
- A. process_privileges
- B. process_cloud_reputation
- C. process_reputation
- D. process_integrity_level
正解: C
質問 81
An administrator is concerned that someone may be using unauthorized commands from cmd.exe. These commands are not considered suspicious or malicious, and there is no policy based around them.
Which page should the administrator use to find these commands?
- A. Alerts
- B. Policies
- C. Sensor Management
- D. Investigate
正解: C
質問 82
Review this result after executing a query in the Process Search page, noting the circled black dot:
What is the meaning of the black dot shown under Tags?
- A. The execution of the process resulted in watchlist hits.
- B. The execution of the process resulted in feed hits.
- C. The events for the process were tagged in an investigation.
- D. The events for the process were also sent to the Syslog Server.
正解: B
質問 83
Which ID in Endpoint Standard is associated with one specific action, involves up to three different hashes (Parent, Process, Target), and occurs on a single device at a specific time?
- A. Process ID
- B. Alert ID
- C. Threat ID
- D. Event ID
正解: D
質問 84
An analyst is investigating a specific alert in Endpoint Standard. The analyst selects the investigate button from the alert triage page and sees the following: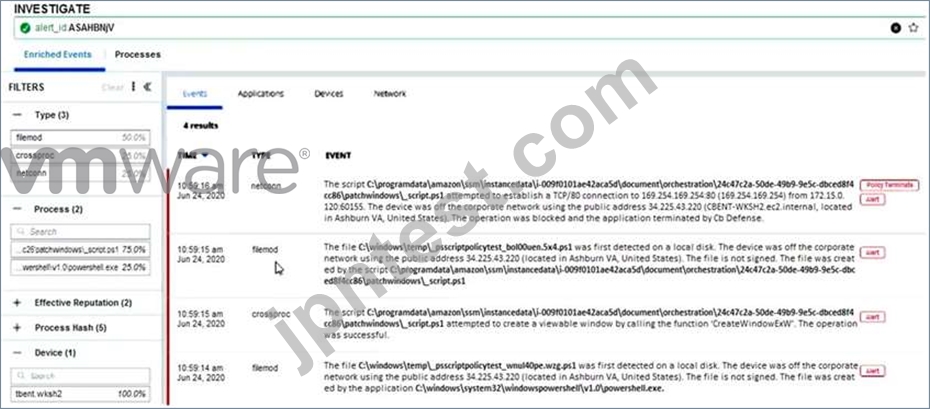
Which statement accurately characterizes this situation?
- A. Each event listed contributed to the overall alert score and severity.
- B. These events are tied to an observed alert within the user interface.
- C. The events shown will all have the same event ID, correlating them to the alert.
- D. The policy had no blocking and isolation rules set.
正解: A
質問 85
How can an analyst disregard alerts on multiple devices with the least amount of administrative effort?
- A. Search by hash and dismiss.
- B. Make a note in the Notes/Tags option.
- C. Select the "Dismiss on all devices" option.
- D. Turn off the Group Alerts option.
正解: D
解説:
Reference:
sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwjv6pryl4XvAhWagVwKHTCMDTE QFjAAegQIARAD&url=https%3A%2F%2Fcommunity.carbonblack.com%2Ft5%2FKnowledge-Base%
2FCarbon-Black-Cloud-How-to-Dismiss-Alerts%2Fta-p%
2F51766&usg=AOvVaw2x1mST1tWpuASUMLmFhyuI (80)
質問 86
An alert for a device running a proprietary application is tied to a vital business operation.
Which action is appropriate to take?
- A. Terminate the process.
- B. Add the application to the Approved List.
- C. Deny the operation.
- D. Quarantine the device.
正解: B
質問 87
What information does the Alert Details panel provide on the Alert Triage page in Endpoint Standard?
- A. Process ID
- B. Device ID
- C. Alert ID
- D. Threat ID
正解: D
質問 88
Given an event rule: Approve nVidia Drivers, changes the local state to Approved for file writes or execution blocks when the publisher is NVIDIA Corporation.
How is an alert created that is triggered whenever an nVidia driver is approved by the event rule?
- A. Create a custom rule name Approve nVidia that approves writes or blocks when the publisher is NVIDIA Corporation. Create an alert for rule name Approve nVidia. Click Create and add email recipients.
- B. Click Create Alert on the event rule Approve nVidia Drivers details page. Add email recipients. Create and Exit.
- C. Add a new Alert of type Event Alert. Set Subtype to New unapproved file to computer and Execution block (unapproved file) and Publisher to NVIDIA Corporation. Click Create and add email recipients.
- D. Click Create Alert on the event rule Approve nVidia Drivers details page. Click Create and add email recipients. Create and Exit.
正解: D
質問 89
Given the following query:
SELECT * FROM users WHERE UID >= 500;
Which statement is correct?
- A. This query limits the number of columns to display in the results.
- B. This query filters results sent to the cloud.
- C. This query is missing a parameter for validity.
- D. This query returns all accounts found on systems.
正解: A
質問 90
Given the following query:
SELECT hostname, cpu_type, cpu_brand, cpu_physical_cores, cpu_logical_cores, cpu_microcode, (1.0 * physical_memory / (1000*1000*1000)) AS physical_mem_gb, hardware_vendor, hardware_model, hardware_version, hardware_serial FROM system_info; Which statement Is correct?
- A. This query combines data from several different tables.
- B. This query is missing a filter option.
- C. This query shows data from the physical_mem_gb column.
- D. This query customizes the results returned by the system.
正解: B
質問 91
After an emergency, what does the Restore computer button do on the App Control Home page?
- A. Move all computers to Medium Enforcement level
- B. Move all computers to High Enforcement level
- C. Move all computers to Low Enforcement level
- D. Move all computers to the original Enforcement level
正解: D
質問 92
In which two ways can the tamper protection on an App Control agent be disabled when diagnosing agent issues or removing the agent? (Choose two.)
- A. From the Computer Details page on the web console
- B. From the Files on Computers page on the web console
- C. From the File Catalog page on the web console
- D. Run RepCLI on Windows command prompt
- E. Run authenticated DasCLI on Windows command prompt
正解: A,E
解説:
Reference:
Tamper-Protection/ta-p/37220
質問 93
......
最新の5V0-91.20試験問題集でVMwareトレーニング試験には:https://www.jpntest.com/shiken/5V0-91.20-mondaishu
