最新のCisco 350-701試験問題解答がズラリ
350-701試験練習テスト問題(更新された600問あります)
質問 199
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast packets have been flooding the network. What must be configured, based on a predefined threshold, to address this issue?
- A. access control lists
- B. Storm Control
- C. embedded event monitoring
- D. Bridge Protocol Data Unit guard
正解: B
解説:
Explanation
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/eem/command/eem-cr-book/eem-cr-e1.html
質問 200
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
- A. Add entries in the DHCP snooping database
- B. Enable ARP inspection for the required VLAN
- C. Set the DHCP snooping bit to 1
- D. Set a trusted interface for the DHCP server
正解: D
解説:
Explanation
To understand DHCP snooping we need to learn about DHCP spoofing attack first.
DHCP spoofing is a type of attack in that the attacker listens for DHCP Requests from clients and answers them with fake DHCP Response before the authorized DHCP Response comes to the clients. The fake DHCP Response often gives its IP address as the client default gateway -> all the traffic sent from the client will go through the attacker computer, the attacker becomes a "man-in-the-middle".
The attacker can have some ways to make sure its fake DHCP Response arrives first. In fact, if the attacker is "closer" than the DHCP Server then he doesn't need to do anything. Or he can DoS the DHCP Server so that it can't send the DHCP Response.
DHCP snooping can prevent DHCP spoofing attacks. DHCP snooping is a Cisco Catalyst feature that determines which switch ports can respond to DHCP requests. Ports are identified as trusted and untrusted.
Only ports that connect to an authorized DHCP server are trusted, and allowed to send all types of DHCP messages. All other ports on the switch are untrusted and can send only DHCP requests. If a DHCP response is seen on an untrusted port, the port is shut down.
質問 201
Which Cisco solution extends network visibility, threat detection, and analytics to public cloud environments?
- A. Cisco Umbrella
- B. Cisco CloudLock
- C. Cisco Stealthwatch Cloud
- D. Cisco Appdynamics
正解: C
質問 202
Refer to the exhibit.
When configuring a remote access VPN solution terminating on the Cisco ASA, an administrator would like to utilize an external token authentication mechanism in conjunction with AAA authentication using machine certificates. Which configuration item must be modified to allow this?
- A. SAML Server
- B. Group Policy
- C. DHCP Servers
- D. Method
正解: D
解説:
In order to use AAA along with an external token authentication mechanism, set the "Method" as "Both" in the Authentication.
質問 203
What is the difference between deceptive phishing and spear phishing?
- A. Deceptive phishing is an attacked aimed at a specific user in the organization who holds a C-level role.
- B. Spear phishing is when the attack is aimed at the C-level executives of an organization.
- C. Deceptive phishing hijacks and manipulates the DNS server of the victim and redirects the user to a false webpage.
- D. A spear phishing campaign is aimed at a specific person versus a group of people.
正解: D
質問 204
How is DNS tunneling used to exfiltrate data out of a corporate network?
- A. It leverages the DNS server by permitting recursive lookups to spread the attack to other DNS servers.
- B. It corrupts DNS servers by replacing the actual IP address with a rogue address to collect information or start other attacks.
- C. It redirects DNS requests to a malicious server used to steal user credentials, which allows further damage and theft on the network.
- D. It encodes the payload with random characters that are broken into short strings and the DNS server rebuilds the exfiltrated data.
正解: D
解説:
Domain name system (DNS) is the protocol that translates human-friendly URLs, such as securitytut.com, into IP addresses, such as 183.33.24.13. Because DNS messages are only used as the beginning of each communication and they are not intended for data transfer, many organizations do not monitor their DNS traffic for malicious activity. As a result, DNS-based attacks can be effective if launched against their networks. DNS tunneling is one such attack.
An example of DNS Tunneling is shown below:
The attacker incorporates one of many open-source DNS tunneling kits into an authoritative DNS nameserver (NS) and malicious payload.
2. An IP address (e.g. 1.2.3.4) is allocated from the attacker's infrastructure and a domain name (e.g. attackerdomain.com) is registered or reused. The registrar informs the top-level domain (.com) nameservers to refer requests for attackerdomain.com to ns.attackerdomain.com, which has a DNS record mapped to 1.2.3.4
3. The attacker compromises a system with the malicious payload. Once the desired data is obtained, the payload encodes the data as a series of 32 characters (0-9, A-Z) broken into short strings (3KJ242AIE9, P028X977W,...).
4. The payload initiates thousands of unique DNS record requests to the attacker's domain with each string as a part of the domain name (e.g. 3KJ242AIE9.attackerdomain.com). Depending on the attacker's patience and stealth, requests can be spaced out over days or months to avoid suspicious network activity.
5. The requests are forwarded to a recursive DNS resolver. During resolution, the requests are sent to the attacker's authoritative DNS nameserver,
6. The tunneling kit parses the encoded strings and rebuilds the exfiltrated data.
質問 205
How does DNS Tunneling exfiltrate data?
- A. An attacker registers a domain that a client connects to based on DNS records and sends malware through that connection.
- B. An attacker opens a reverse DNS shell to get into the client's system and install malware on it.
- C. An attacker sends an email to the target with hidden DNS resolvers in it to redirect them to a malicious domain.
- D. An attacker uses a non-standard DNS port to gain access to the organization's DNS servers in order to poison the resolutions.
正解: A
質問 206
Drag and drop the descriptions from the left onto the encryption algorithms on the right.
正解:
解説: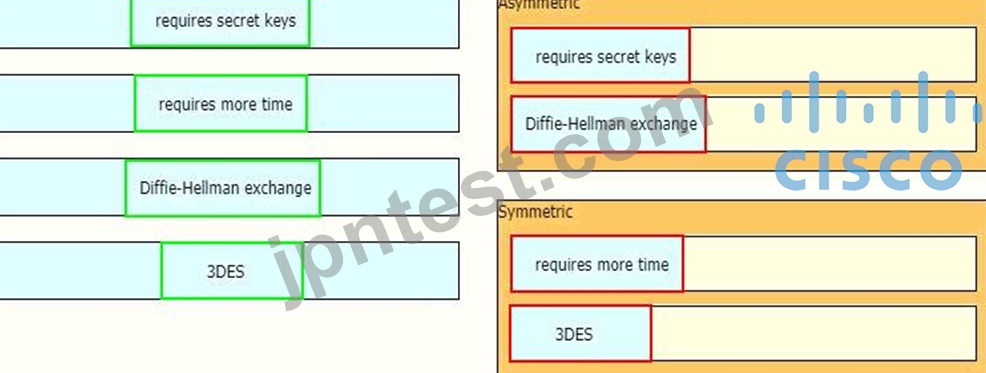
質問 207 
Refer to the exhibit. What is a result of the configuration?
- A. Traffic from the inside network is redirected.
- B. All TCP traffic is redirected.
- C. Traffic from the DMZ network is redirected.
- D. Traffic from the inside and DMZ networks is redirected.
正解: D
質問 208
What is the function of SDN southbound API protocols?
- A. to enable the controller to use REST
- B. to allow for the dynamic configuration of control plane applications
- C. to allow for the static configuration of control plane applications
- D. to enable the controller to make changes
正解: D
解説:
Southbound APIs enable SDN controllers to dynamically make changes based on real-time demands and scalability needs. Reference: https://www.ciscopress.com/articles/article.asp?p=3004581&seqNum=2 scalability needs.
Southbound APIs enable SDN controllers to dynamically make changes based on real-time demands and scalability needs. Reference: https://www.ciscopress.com/articles/article.asp?p=3004581&seqNum=2
Note: Southbound APIs helps us communicate with data plane (not control plane) applications
質問 209
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
- A. Hybrid managed
- B. Enterprise managed
- C. Service Provider managed
- D. Public managed
- E. User managed
正解: B,C
解説:
Explanation
質問 210
Which Cisco AMP file disposition valid?
- A. pristine
- B. nonmalicios
- C. dirty
- D. malware
正解: D
質問 211
Which action controls the amount of URI text that is stored in Cisco WSA logs files?
- A. Configure a small log-entry size.
- B. Configure the advancedproxyconfig command with the HTTPS subcommand
- C. Configure the datasecurityconfig command
- D. Configure a maximum packet size.
正解: B
質問 212
When Cisco and other industry organizations publish and inform users of known security findings and vulnerabilities, which name is used?
- A. Common Vulnerabilities, Exploits and Threats
- B. Common Security Exploits
- C. Common Exploits and Vulnerabilities
- D. Common Vulnerabilities and Exposures
正解: D
解説:
Explanation
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/cve/174/cve-addressed-1741.html
質問 213
What do tools like Jenkins, Octopus Deploy, and Azure DevOps provide in terms of application and infrastructure automation?
- A. compile-time instrumentation
- B. continuous integration and continuous deployment
- C. container orchestration
- D. cloud application security broker
正解: B
質問 214
What is managed by Cisco Security Manager?
- A. ESA
- B. ASA
- C. access point O
- D. WSA
正解: B
解説:
https://www.cisco.com/c/en/us/products/collateral/security/security-manager/datasheet-C78-737182.html
質問 215
Drag and drop the capabilities of Cisco Firepower versus Cisco AMP from the left into the appropriate category on the right.
正解:
解説:
https://www.cisco.com/c/en/us/products/collateral/security/ngips/datasheet-c78-742472.html
https://www.cisco.com/c/en/us/td/docs/security/firepower/60/configuration/guide/fpmc-config-guide-v60/Reference_a_wrapper_Chapter_topic_here.html
https://www.cisco.com/c/en/us/solutions/collateral/enterprise-networks/advanced-malware-protection/solution-overview-c22-734228.html
質問 216
Which benefit does endpoint security provide the overall security posture of an organization?
- A. It allows the organization to mitigate web-based attacks as long as the user is active in the domain.
- B. It allows the organization to detect and respond to threats at the edge of the network.
- C. It streamlines the incident response process to automatically perform digital forensics on the endpoint.
- D. It allows the organization to detect and mitigate threats that the perimeter security devices do not detect.
正解: D
質問 217
Refer to the exhibit.
Consider that any feature of DNS requests, such as the length off the domain name and the number of subdomains, can be used to construct models of expected behavior to which observed values can be compared. Which type of malicious attack are these values associated with?
- A. Eternal Blue Windows
- B. Heartbleed SSL Bug
- C. Spectre Worm
- D. W32/AutoRun worm
正解: D
質問 218
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
- A. Enable two-factor authentication through a TACACS+ server and then join the cluster by using the Cisco ESA CLI
- B. Enable two-factor authentication through a TACACS+ server and then join the cluster by using the Cisco ESA GUI.
- C. Enable two-factor authentication through a RADIUS server and then join the cluster by using the Cisco ESA CLI.
- D. Enable two-factor authentication through a RADIUS server and then join the cluster by using the Cisco ESA GUI
正解: C
質問 219
Refer to the exhibit.
A network administrator configures command authorization for the admm5 user. What is the admin5 user able to do on HQ_Router after this configuration?
- A. set the IP address of an interface
- B. complete no configurations
- C. add subinterfaces
- D. complete all configurations
正解: B
質問 220
An organization received a large amount of SPAM messages over a short time period. In order to take action on the messages, it must be determined how harmful the messages are and this needs to happen dynamically.
What must be configured to accomplish this?
- A. Configure the Cisco WSA to receive real-time updates from Talos.
- B. Configure the Cisco ESA to receive real-time updates from Talos
- C. Configure the Cisco WSA to modify policies based on the traffic seen.
- D. Configure the Cisco ESA to modify policies based on the traffic seen.
正解: B
解説:
Explanation
https://www.cisco.com/c/en/us/td/docs/security/esa/esa120/user_guide/b_ESA_Admin_Guide_12_0/b_ESA_Adm
質問 221
......
Cisco 350-701 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
| トピック 9 |
|
| トピック 10 |
|
| トピック 11 |
|
| トピック 12 |
|
| トピック 13 |
|
| トピック 14 |
|
| トピック 15 |
|
あなたを合格させるCisco試験には350-701試験問題集:https://www.jpntest.com/shiken/350-701-mondaishu
