100%更新されたのはCheckPoint 156-215.81限定版PDF問題集
有効な試験問題を試そう156-215.81には無料サイトで限定お試しチャンス
チェックポイント156-215.81認定試験の準備をするために、候補者はチェックポイントのトレーニングおよび認定プログラムを活用できます。これは、さまざまなトレーニングコース、学習ガイド、練習試験を提供します。候補者は、サードパーティのプロバイダーからの本、オンラインコース、練習試験などの学習資料を見つけることもできます。適切な準備と研究により、候補者は試験に合格し、チェックポイント認定セキュリティ管理者R81認定を獲得する可能性を高めることができます。
CheckPoint 156-215.81試験の準備には、ネットワークの基礎をしっかりと理解し、ネットワーク管理の経験があることが勧められます。また、Check Point Security GatewayおよびManagement Software Bladesシステムに対して実地経験を持つことも望ましいです。試験に備えるためには、様々なトレーニングコースや学習資料が用意されています。
質問 # 30
What are the advantages of a "shared policy" in R80?
- A. Allows the administrator to share a policy between all the users identified by the Security Gateway
- B. Allows the administrator to share a policy so that it is available to use in another Policy Package
- C. Allows the administrator to share a policy between all the administrators managing the Security Management Server
- D. Allows the administrator to install a policy on one Security Gateway and it gets installed on another managed Security Gateway
正解:B
解説:
Ref: https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_SecurityManagement_AdminGuide/Topics-SECMG/SmartConsole-Toolbars-Shared-Policies.htm
質問 # 31
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- A. Sub Policies are sets of rules that can be created and attached to specific rules. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule.
- B. Limits the upload and download throughput for streaming media in the company to 1 Gbps.
- C. Time object to a rule to make the rule active only during specified times.
- D. The rule base can be built of layers, each containing a set of the security rules. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
正解:A
質問 # 32
Which policy type is used to enforce bandwidth and traffic control rules?
- A. QoS
- B. Threat Emulation
- C. Threat Prevention
- D. Access Control
正解:A
解説:
Check Point's QoS Solution
QoS is a policy-based QoS management solution from Check Point Software Technologies Ltd., satisfies your needs for a bandwidth management solution. QoS is a unique, software-only based application that manages traffic end-to-end across networks, by distributing enforcement throughout network hardware and software.
質問 # 33
Security Gateway software blades must be attached to what?
- A. Management server
- B. Management container
- C. Security Gateway
- D. Security Gateway container
正解:C
質問 # 34
Fill in the blanks: A ____ license requires an administrator to designate a gateway for attachment whereas a _____ license is automatically attached to a Security Gateway.
- A. Local; formal
- B. Formal; corporate
- C. Central; local
- D. Local; central
正解:C
質問 # 35
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
- A. Packet Filtering
- B. Next-Generation Firewall
- C. INSPECT Engine
- D. Application Layer Firewall
正解:B
解説:
Explanation
The INSPECT Engine is a technology that extracts detailed information from packets and stores that information in state tables. It enables stateful inspection and application layer filtering12 References: INSPECT Engine, Stateful Inspection
質問 # 36
View the rule below. What does the pen-symbol in the left column mean?
- A. Rules have been edited by the logged in administrator, but the policy has not been published yet.
- B. Those rules have been published in the current session.
- C. Another user has currently locked the rules for editing.
- D. The configuration lock is present. Click the pen symbol in order to gain the lock.
正解:A
質問 # 37
VPN gateways must authenticate to each other prior to exchanging information.
What are the two types of credentials used for authentication?
- A. Certificates and IPsec
- B. IPsec and VPN Domains
- C. 3DES and MD5
- D. Certificates and pre-shared secret
正解:D
質問 # 38
You have successfully backed up your Check Point configurations without the OS information. What command would you use to restore this backup?
- A. migrate import
- B. import backup
- C. restore_backup
- D. cp_merge
正解:C
解説:
Explanation
The command to restore a backup of Check Point configurations without the OS information is restore_backup4. This command restores the Gaia OS configuration and the firewall database from a compressed file. The other commands are not valid for this purpose. import backup is not a valid command. cp_merge is a command to merge policies or objects from different databases. migrate import is a command to import a previously exported database using migrate export. References: System Backup and Restore feature in Gaia, [cp_merge], [migrate import]
質問 # 39
Fill in the blanks: There are ________ types of software containers ________.
- A. Three; Security gateway, endpoint security, and gateway management
- B. Two; endpoint security and Security Gateway
- C. Three; security management, Security Gateway, and endpoint security
- D. Two; security management and endpoint security
正解:C
質問 # 40
Which deployment adds a Security Gateway to an existing environment without changing IP routing?
- A. Bridge Mode
- B. Standalone
- C. Distributed
- D. Remote
正解:A
質問 # 41
You believe Phase 2 negotiations are failing while you are attempting to configure a site-to-site VPN with one of your firm's business partners. Which SmartConsole application should you use to confirm your suspicious?
- A. SmartUpdate
- B. SmartView Status
- C. SmartDashboard
- D. SmartView Tracker
正解:D
質問 # 42
What does it mean if Deyra sees the gateway status:
Choose the BEST answer.
- A. Security Gateway's MGNT NIC card is disconnected.
- B. There is a blade reporting a problem
- C. VPN software blade is reporting a malfunction
- D. SmartCenter Server cannot reach this Security Gateway
正解:B
解説:
Explanation
If Deyra sees the gateway status as shown in the image, it means that there is a blade reporting a problem.
The red "X" in the status column indicates that one or more blades on the Security Gateway have a problem that requires attention. The other options are not correct, as they do not match the status shown in the image. If the SmartCenter Server cannot reach this Security Gateway, the status column would show a yellow triangle with an exclamation mark. If the VPN software blade is reporting a malfunction, the blades column would show a red "X" on the VPN icon. If the Security Gateway's MGNT NIC card is disconnected, the IP column would show "N/A" instead of the IP address.
References: Remote Access VPN R81 Administration Guide, Check Point R81.10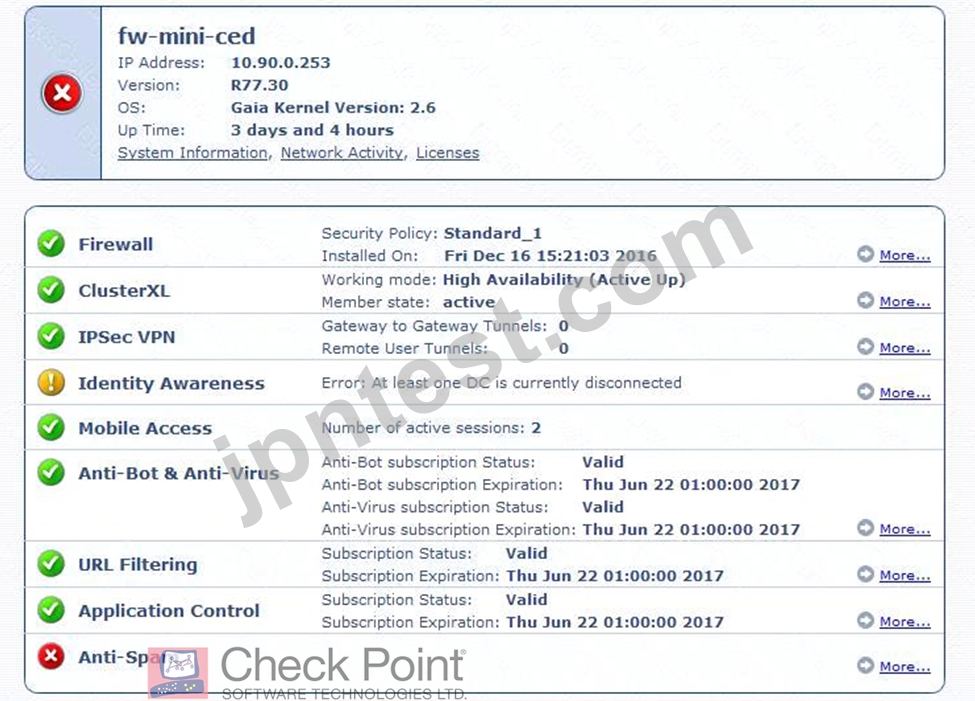
質問 # 43
In which VPN community is a satellite VPN gateway not allowed to create a VPN tunnel with another satellite VPN gateway?
- A. Combined
- B. Pentagon
- C. Meshed
- D. Star
正解:D
解説:
VPN communities are based on Star and Mesh topologies. In a Mesh community, there are VPN connections between each Security Gateway. In a Star community, satellites have a VPN connection with the center Security Gateway, but not to each other.
質問 # 44
How is communication between different Check Point components secured in R81? As with all questions, select the best answer.
- A. By using ICA
- B. By using 3DES
- C. By using IPSEC
- D. By using SIC
正解:D
質問 # 45
Your boss wants you to closely monitor an employee suspected of transferring company secrets to the competition. The IT department discovered the suspect installed a WinSCP client in order to use encrypted communication. Which of the following methods is BEST to accomplish this task?
- A. Use SmartDashboard to add a rule in the firewall Rule Base that matches his IP address, and those of potential targets and suspicious protocols. Apply the alert action or customized messaging.
- B. Watch his IP in SmartView Monitor by setting an alert action to any packet that matches your Rule Base and his IP address for inbound and outbound traffic.
- C. Use SmartView Tracker to follow his actions by filtering log entries that feature the WinSCP destination port. Then, export the corresponding entries to a separate log file for documentation.
- D. Send the suspect an email with a keylogging Trojan attached, to get direct information about his wrongdoings.
正解:C
質問 # 46
A stateful inspection firewall works by registering connection data and compiling this information. Where is the information stored?
- A. In the Sessions table.
- B. In a CSV file on the firewall hard drive located in $FWDIR/conf/.
- C. In State tables.
- D. In the system SMEM memory pool.
正解:C
解説:
The information stored in the state tables provides cumulative data that can be used to evaluate future connections...... https://www.checkpoint.com/cyber-hub/network-security/what-is-firewall/what-is-a-stateful-firewall/
質問 # 47
When should you generate new licenses?
- A. Before installing contract files.
- B. Only when the license is upgraded.
- C. When the existing license expires, license is upgraded or the IP-address where the license is tied changes.
- D. After an RMA procedure when the MAC address or serial number of the appliance changes.
正解:C
解説:
Explanation
You should generate new licenses when the existing license expires, license is upgraded or the IP-address where the license is tied changes13. These scenarios require a new license to be generated and activated on the Security Gateway or Management Server13. Therefore, the correct answer is C. When the existing license expires, license is upgraded or the IP-address where the license is tied changes
質問 # 48
When installing a dedicated R80 SmartEvent server, what is the recommended size of the root partition?
- A. Less than 20GB
- B. Any size
- C. At least 20GB
- D. More than 10GB and less than 20 GB
正解:C
解説:
Explanation
The correct answer is D because the recommended size of the root partition for a dedicated R80 SmartEvent server is at least 20GB2. Any size, less than 20GB, or more than 10GB and less than 20GB are not sufficient for the SmartEvent server. References: Check Point R80.40 Installation and Upgrade Guide
質問 # 49
What command would show the API server status?
- A. api status
- B. show api status
- C. api restart
- D. cpm status
正解:B
解説:
Explanation
The command api status shows the API server status, including whether it is enabled or not, the port number, and the API version1. References: Check Point R81 API Reference Guide
質問 # 50
......
CheckPoint 156-215.81公式認定ガイドPDF:https://www.jpntest.com/shiken/156-215.81-mondaishu
