[2021年12月]更新のFortinet NSE4_FGT-6.4試験基本問題には解答が付きます
2021年最新の実際に出るFortinet NSE4_FGT-6.4試験問題集と解答
質問 46
Refer to the exhibit.
Which contains a session list output. Based on the information shown in the exhibit, which statement is true?
- A. One-to-one NAT IP pool is used in the firewall policy.
- B. Port block allocation IP pool is used in the firewall policy.
- C. Destination NAT is disabled in the firewall policy.
- D. Overload NAT IP pool is used in the firewall policy.
正解: C
質問 47
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
- A. NetAPI polling can increase bandwidth usage in large networks.
- B. The NetSessionEnum functionis user] to track user logouts.
- C. The collector agent must search security event logs.
- D. The collector agent uses a Windows API to query DCs for user logins.
正解: D
質問 48
Refer to the exhibit.
Based on the administrator profile settings, what permissions must the administrator set to run the diagnose firewall auth list CLI command on FortiGate?
- A. Read/Write permission for Log & Report
- B. Custom permission for Network
- C. Read/Write permission for Firewall
- D. CLI diagnostics commands permission
正解: B
質問 49
Refer to the exhibit.
Given the security fabric topology shown in the exhibit, which two statements are true? (Choose two.)
- A. Device detection is disabled on all FortiGate devices.
- B. There are 19 security recommendations for the security fabric.
- C. There are five devices that are part of the security fabric.
- D. This security fabric topology is a logical topology view.
正解: A,D
質問 50
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
- A. get system status
- B. diagnose sys top
- C. get system arp
- D. get system performance status
正解: C
質問 51
Examine the two static routes shown in the exhibit, then answer the following question.
Which of the following is the expected FortiGate behavior regarding these two routes to the same destination?
- A. FortiGate will load balance all traffic across both routes.
- B. FortiGate will only actuate the port1 route in the routing table
- C. FortiGate will route twice as much traffic to the port2 route
- D. FortiGate will use the port1 route as the primary candidate.
正解: D
解説:
Explanation
"If multiple static routes have the same distance, they are all active; however, only the one with the lowest priority is considered the best path."
質問 52
Refer to the exhibit.
According to the certificate values shown in the exhibit, which type of entity was the certificate issued to?
- A. A subordinate
- B. A user
- C. A root CA
- D. A bridge CA
正解: B
質問 53
Refer to the exhibit.


The exhibit contains a network interface configuration, firewall policies, and a CLI console configuration.
How will FortiGate handle user authentication for traffic that arrives on the LAN interface?
- A. Authentication is enforced at a policy level; all users will be prompted for authentication.
- B. If there is a full-through policy in place, users will not be prompted for authentication.
- C. Users from the HR group will be prompted for authentication and can authenticate successfully with the correct credentials.
- D. Users from the Sales group will be prompted for authentication and can authenticate successfully with the correct credentials.
正解: A
質問 54
Examine the exhibit, which contains a virtual IP and firewall policy configuration.


The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP address
10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP address 10.0.1.10/24?
- A. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
- B. 10.200.1.1
- C. 10.0.1.254
- D. 10.200.1.10
正解: D
解説:
Explanation
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-firewall-52/Firewall%20Objects/Virtual%20IPs.
質問 55
Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question below.
When detecting attacks, which anomaly, signature, or filter will FortiGate evaluate first?
- A. ip_src_session
- B. IMAP.Login.brute.Force
- C. SMTP.Login.Brute.Force
- D. Location: server Protocol: SMTP
正解: B
質問 56
You have enabled logging on your FortiGate device for Event logs and all Security logs, and you have set up logging to use the FortiGate local disk.
What is the default behavior when the local disk is full?
- A. No new log is recorded after the warning is issued when log disk usage reaches the threshold of 95%.
- B. Logs are overwritten and the only warning is issued when log disk usage reaches the threshold of 95%.
- C. No new log is recorded until you manually clear logs from the local disk.
- D. Logs are overwritten and the first warning is issued when log disk usage reaches the threshold of 75%.
正解: D
解説:
Explanation/Reference: https://docs.fortinet.com/document/fortigate/6.4.0/cli-reference/462620/log-disk-setting
質問 57
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
- A. Log in to a downstream FortiSwitch device.
- B. Disable FortiAnalyzer logging for a downstream FortiGate device.
- C. Shut down/reboot a downstream FortiGate device.
- D. Ban or unban compromised hosts.
正解: B,C
質問 58
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
- A. Allow
- B. Exempt
- C. Learn
- D. Warning
正解: A,D
質問 59
An administrator does not want to report the logon events of service accounts to FortiGate. What setting on the collector agent is required to achieve this?
- A. Add user accounts to the FortiGate group fitter.
- B. Add useraccounts to Active Directory (AD).
- C. Add the support of NTLM authentication.
- D. Add user accounts to the Ignore User List.
正解: A
質問 60
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
- A. To remove the NAT operation
- B. To finish any inspection operations
- C. To generate logs
- D. To allow for out-of-order packets that could arrive after the FIN/ACK packets
正解: B
質問 61
Refer to the exhibit.
The exhibit displays the output of the CLI command: diagnose sys ha dump-by vcluster.
Which two statements are true? (Choose two.)
- A. FortiGate devices are not in sync because one device is down.
- B. FortiGate SN FGVM010000064692 has the higher HA priority.
- C. FortiGate SN FGVM010000064692 is the primary because of higher HA uptime.
- D. FortiGate SN FGVM010000065036 HA uptime has been reset.
正解: B,D
質問 62
Which three CLI commands can you use to troubleshoot Layer 3 issues if the issue is in neither the physical layer nor the link layer? (Choose three.)
- A. diagnose sys top
- B. execute traceroute
- C. get system arp
- D. execute ping
- E. diagnose sniffer packet any
正解: A,D,E
質問 63
Which engine handles application control traffic on the next-generation firewall (NGFW) FortiGate?
- A. Intrusion prevention system engine
- B. Flow engine
- C. Detection engine
- D. Antivirus engine
正解: A
質問 64
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
- A. It limits the scope of application control to scan application traffic on DNS protocol only.
- B. It limits the scope of application control to scan application traffic using parent signatures only
- C. It limits the scope of application control to scan application traffic based on application category only.
- D. It limits the scope of application control to the browser-based technology category only.
正解: C
質問 65
Refer to the exhibit.
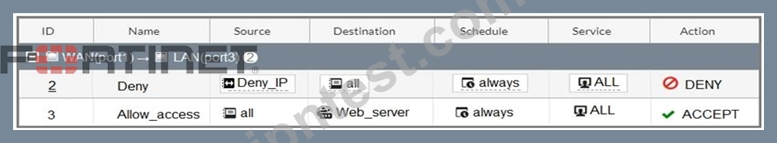

The exhibit contains a network diagram, firewall policies, and a firewall address object configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-user2.
Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
- A. Set the Destination address as
- B. Enable match vip in the Deny policy.
- C. Disable match-vip in the Deny
- D. Set the Destination address as Web_server in the Deny policy.
正解: A,C
質問 66
View the exhibit.
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
- A. Addicting.Games is blocked on the Filter Overrides configuration.
- B. Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
- C. Addcting.Games is allowed based on the Categories configuration.
- D. Addicting.Games is allowed based on the Application Overrides configuration.
正解: D
質問 67
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
- A. The NetSessionEnum function is used to track user logouts.
- B. NetAPI polling can increase bandwidth usage in large networks.
- C. The collector agent uses a Windows API to query DCs for user logins.
- D. The collector agent must search security event logs.
正解: B
解説:
Explanation/Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD34906
質問 68
......
Fortinet NSE4_FGT-6.4 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
| トピック 9 |
|
合格保証付きのFortinet NSE 4 NSE4_FGT-6.4試験問題集:https://www.jpntest.com/shiken/NSE4_FGT-6.4-mondaishu
