2023年最新の本日更新された最新のPCCETのPDFにはPCCETテスト限定無料!
完全版最新の問題集PDFで最新PCCET試験問題と解答
質問 # 82
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
- A. Prisma access uses Uniform Resource Locator (URL) Web categorization to provide protection and sharing visibility
- B. Prisma SaaS connects to an organizations internal print and file sharing services to provide protection and sharing visibility
- C. Prisma SaaS does not provide protection for Sanctioned SaaS applications because they are secure
- D. Prisma SaaS connects directly to sanctioned external service providers SaaS application service to provide protection and sharing visibility
正解:D
解説:
Explanation
Prisma SaaS connects directly to the applications themselves, therefore providing continuous silent monitoring of the risks within the sanctioned SaaS applications, with detailed visibility that is not possible with traditional security solutions.
質問 # 83
Which type of LAN technology is being displayed in the diagram?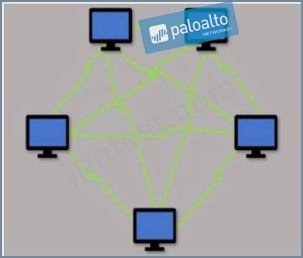
- A. Bus Topology
- B. Mesh Topology
- C. Star Topology
- D. Spine Leaf Topology
正解:C
質問 # 84
What is the recommended method for collecting security logs from multiple endpoints?
- A. Connect to the endpoints remotely and download the logs.
- B. Build a script that pulls down the logs from all endpoints.
- C. Configure endpoints to forward logs to a SIEM.
- D. Leverage an EDR solution to request the logs from endpoints.
正解:C
質問 # 85
Which of the following is a CI/CD platform?
- A. Github
- B. Jenkins
- C. Atom.io
- D. Jira
正解:B
質問 # 86
Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
- A. Case management
- B. Ticketing system
- C. Integrations
- D. Playbooks
正解:D
質問 # 87
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
- A. Global Protect
- B. WildFire
- C. AutoFocus
- D. STIX
正解:C
質問 # 88
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Static
- B. Dynamic
- C. Pre-exploit protection
- D. Bare-metal
正解:B
解説:
Explanation
The WildFire cloud-based malware analysis environment is a cyber threat prevention service that identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment.
質問 # 89
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
- A. containers and developers
- B. connectors and interfaces
- C. data center and UPS
- D. infrastructure and containers
正解:B
質問 # 90
Which pillar of Prisma Cloud application security does vulnerability management fall under?
- A. identity security
- B. compute security
- C. dynamic computing
- D. network protection
正解:B
解説:
Explanation
Prisma Cloud comprises four pillars:
Visibility, governance, and compliance. Gain deep visibility into the security posture of multicloud environments. Track everything that gets deployed with an automated asset inventory, and maintain compliance with out-of-the-box governance policies that enforce good behavior across your environments.
Compute security. Secure hosts, containers, and serverless workloads throughout the application lifecycle. Detect and prevent risks by integrating vulnerability intelligence into your integrated development environment (IDE), software configuration management (SCM), and CI/CD workflows. Enforce machine learning-based runtime protection to protect applications and workloads in real time.
Network protection. Continuously monitor network activity for anomalous behavior, enforce microservice-aware micro-segmentation, and implement industry-leading firewall protection. Protect the network perimeter and the connectivity between containers and hosts.
Identity security. Monitor and leverage user and entity behavior analytics (UEBA) across your environments to detect and block malicious actions. Gain visibility into and enforce governance p
質問 # 91
What are three benefits of the cloud native security platform? (Choose three.)
- A. Digital transformation
- B. Exclusivity
- C. Agility
- D. Flexibility
- E. Increased throughput
正解:A、D、E
質問 # 92
Web 2.0 applications provide which type of service?
- A. SaaS
- B. PaaS
- C. FWaaS
- D. IaaS
正解:B
質問 # 93
Match the Identity and Access Management (IAM) security control with the appropriate definition.
正解:
解説:
質問 # 94
Which aspect of a SaaS application requires compliance with local organizational security policies?
- A. Types of physical storage media used
- B. Acceptable use of the SaaS application
- C. Data-at-rest encryption standards
- D. Vulnerability scanning and management
正解:B
質問 # 95
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
- A. Static
- B. Dynamic
- C. Pre-exploit protection
- D. Bare-metal
正解:B
質問 # 96
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
- A. PaaS
- B. SaaS
- C. DaaS
- D. IaaS
正解:D
質問 # 97
In a traditional data center what is one result of sequential traffic analysis?
- A. causes security policies to be complex
- B. improves security policy application ID enforcement
- C. simplifies security policy management
- D. reduces network latency
正解:A
解説:
Explanation
Multiple policies, no policy reconciliation tools: Sequential traffic analysis (stateful inspection, application control, intrusion prevention system (IPS), anti-malware, etc.) in traditional data center security solutions requires a corresponding security policy or profile, often using multiple management tools. The result is that your security policies become convoluted as you build and manage a firewall policy with source, destination, user, port, and action; an application control policy with similar rules; and any other threat prevention rules required. Multiple security policies that mix positive (firewall) and negative (application control, IPS, and anti-malware) control models can cause security holes by missing traffic and/or not identifying
質問 # 98
Which IPsec feature allows device traffic to go directly to the Internet?
- A. Diffie-Hellman groups
- B. Split tunneling
- C. IKE Security Association
- D. d.Authentication Header (AH)
正解:B
解説:
Explanation
"Or split tunneling can be configured to allow internet traffic from the device to go directly to the internet, while other specific types of traffic route through the IPsec tunnel, for acceptable protection with much less performance degradation."
質問 # 99
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
- A. SecDevOps
- B. SecOps
- C. DevOps
- D. NetOps
正解:B
解説:
Security operations (SecOps) is a necessary function for protecting the digital way of life, for global businesses and customers. SecOps requires continuous improvement in operations to handle fast-evolving threats. SecOps needs to arm security operations professionals with high-fidelity intelligence, contextual data, and automated prevention workflows to quickly identify and respond to these threats. SecOps must leverage automation to reduce strain on analysts and execute the Security Operation Center's (SOC) mission to identify, investigate, and mitigate threats.
質問 # 100
During the OSI layer 3 step of the encapsulation process, what is the Protocol Data Unit (PDU) called when the IP stack adds source (sender) and destination (receiver) IP addresses?
- A. Data
- B. Segment
- C. Packet
- D. Frame
正解:C
質問 # 101
What is a key advantage and key risk in using a public cloud environment?
- A. Dedicated Hosts
- B. Dedicated Networks
- C. Multiplexing
- D. Multi-tenancy
正解:D
質問 # 102
Match the description with the VPN technology.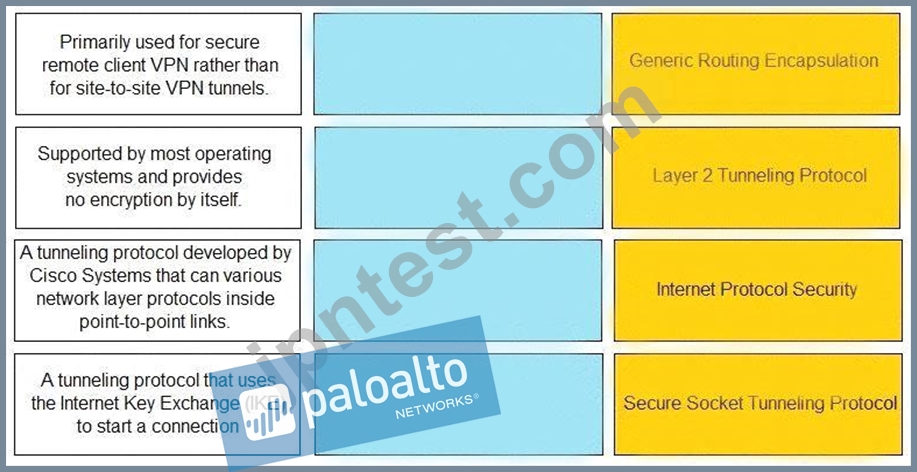
正解:
解説:
質問 # 103
Which option describes the "selective network security virtualization" phase of incrementally transforming data centers?
- A. during the selective network security virtualization phase, all intra-host traffic is encapsulated and encrypted using the IPSEC protocol
- B. during the selective network security virtualization phase, all intra-host communication paths are strictly controlled
- C. during the selective network security virtualization phase, all intra-host traffic is forwarded to a Web proxy server
- D. during the selective network security virtualization phase, all intra-host traffic is load balanced
正解:B
解説:
Selective network security virtualization: Intra-host communications and live migrations are architected at this phase. All intra-host communication paths are strictly controlled to ensure that traffic between VMs at different trust levels is intermediated either by an on-box, virtual security appliance or by an off-box, physical security appliance.
質問 # 104
What are the two most prominent characteristics of the malware type rootkit? (Choose two.)
- A. It takes control of the operating system.
- B. It steals personal information.
- C. It encrypts user data.
- D. It cannot be detected by antivirus because of its masking techniques.
正解:A、D
質問 # 105
......
無料PCCET試験問題PCCET実際の無料試験問題:https://www.jpntest.com/shiken/PCCET-mondaishu
