[2023年11月]更新のFortinet NSE6_FAC-6.4テストエンジンとPDFで完全版無料問題集を無料提供
最新版を今すぐ試そうNSE6_FAC-6.4認定有効な試験問題集
質問 # 19
Which interface services must be enabled for the SCEP client to connect to Authenticator?
- A. OCSP
- B. HTTP/HTTPS
- C. REST API
- D. SSH
正解:B
解説:
HTTP/HTTPS are the interface services that must be enabled for the SCEP client to connect to FortiAuthenticator. SCEP stands for Simple Certificate Enrollment Protocol, which is a method of requesting and issuing digital certificates over HTTP or HTTPS. FortiAuthenticator supports SCEP as a certificate authority (CA) and can process SCEP requests from SCEP clients. To enable SCEP on FortiAuthenticator, the HTTP or HTTPS service must be enabled on the interface that receives the SCEP requests.
質問 # 20
Which two statements about the self-service portal are true? (Choose two)
- A. Self-registration information can be sent to the user through email or SMS
- B. Authenticating users must specify domain name along with username
- C. Realms can be used to configure which seld-registered users or groups can authenticate on the network
- D. Administrator approval is required for all self-registration
正解:A、C
解説:
Two statements about the self-service portal are true:
Self-registration information can be sent to the user through email or SMS using the notification templates feature. This feature allows administrators to customize the messages that are sent to users when they register or perform other actions on the self-service portal.
Realms can be used to configure which self-registered users or groups can authenticate on the network using the realm-based authentication feature. This feature allows administrators to apply different authentication policies and settings to different groups of users based on their realm membership.
質問 # 21
Which behaviors exist for certificate revocation lists (CRLs) on FortiAuthenticator? (Choose two)
- A. CRLs can be exported only through the SCEP server
- B. CRLs contain the serial number of the certificate that has been revoked
- C. All local CAs share the same CRLs
- D. Revoked certificates are automaticlly placed on the CRL
正解:B、D
解説:
CRLs are lists of certificates that have been revoked by the issuing CA and should not be trusted by any entity. CRLs contain the serial number of the certificate that has been revoked, the date and time of revocation, and the reason for revocation. Revoked certificates are automatically placed on the CRL by the CA and the CRL is updated periodically. CRLs can be exported through various methods, such as HTTP, LDAP, or SCEP. Each local CA has its own CRL that is specific to its issued certificates. Reference: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372408/certificate-management/372413/certificate-revocation-lists
質問 # 22
Which statement about the assignment of permissions for sponsor and administrator accounts is true?
- A. Both sponsor and administrator account permissions are assigned using admin profiles.
- B. Only administrator accounts permissions are assigned using admin profiles.
- C. Sponsor permissions are assigned using group settings.
- D. Administrator capabilities are assigned by applying permission sets to admin groups.
正解:A
解説:
Both sponsor and administrator account permissions are assigned using admin profiles. An admin profile is a set of permissions that defines what actions an administrator or a sponsor can perform on FortiAuthenticator. An admin profile can be assigned to an admin group or an individual admin user. A sponsor is a special type of admin user who can create and manage guest accounts on behalf of other users.
質問 # 23
Which two protocols are the default management access protocols for administrative access for FortiAuthenticator? (Choose two)
- A. SNMP
- B. Telnet
- C. SSH
- D. HTTPS
正解:C、D
解説:
HTTPS and SSH are the default management access protocols for administrative access for FortiAuthenticator. HTTPS allows administrators to access the web-based GUI of FortiAuthenticator using a web browser and a secure connection. SSH allows administrators to access the CLI of FortiAuthenticator using an SSH client and an encrypted connection. Both protocols require the administrator to enter a valid username and password to log in.
質問 # 24
What capability does the inbound proxy setting provide?
- A. It allows FortiAuthenticator to determine the origin source IP address after traffic passes through a proxy for system access,
- B. It allows FortiAuthenticator the ability to round robin load balance remote authentication servers.
- C. It allows FortiAuthenticator system access to authenticating users, based on a geo IP address designation.
- D. It allows FortiAuthenticator to act as a proxy for remote authentication servers.
正解:A
解説:
The inbound proxy setting provides the ability for FortiAuthenticator to determine the origin source IP address after traffic passes through a proxy for system access. The inbound proxy setting allows FortiAuthenticator to use the X-Forwarded-For header in the HTTP request to identify the original client IP address. This can help FortiAuthenticator apply the correct authentication policy or portal policy based on the source IP address.
質問 # 25
Which two capabilities does FortiAuthenticator offer when acting as a self-signed or local CA? (Choose two)
- A. Validating other CA CRLs using OSCP
- B. Creating, signing, and revoking of X.509 certificates
- C. Merging local and remote CRLs using SCEP
- D. Importing other CA certificates and CRLs
正解:B、D
解説:
FortiAuthenticator can act as a self-signed or local CA that can issue certificates to users, devices, or other CAs. It can also import other CA certificates and CRLs to trust them and validate their certificates. It can also create, sign, and revoke X.509 certificates for various purposes, such as VPN authentication, web server encryption, or wireless security. It cannot validate other CA CRLs using OCSP or merge local and remote CRLs using SCEP because these are protocols that require communication with external CAs. Reference: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372408/certificate-management
質問 # 26
At a minimum, which two configurations are required to enable guest portal services on FortiAuthenticator? (Choose two)
- A. Configuring a RADIUS client
- B. Configuring a portal policy
- C. Configuring at least on post-login service
- D. Configuring an external authentication portal
正解:B、C
解説:
To enable guest portal services on FortiAuthenticator, you need to configure a portal policy that defines the conditions for presenting the guest portal to users and the authentication methods to use. You also need to configure at least one post-login service that defines what actions to take after a user logs in successfully, such as sending an email confirmation, assigning a VLAN, or creating a user account. Configuring a RADIUS client or an external authentication portal are optional steps that depend on your network setup and requirements. Reference: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372404/guest-management
質問 # 27
Which method is the most secure way of delivering FortiToken data once the token has been seeded?
- A. Automatic token generation using FortiAuthenticator
- B. Online activation of the tokens through the FortiGuard network
- C. Shipment of the seed files on a CD using a tamper-evident envelope
- D. Using the in-house token provisioning tool
正解:B
解説:
Online activation of the tokens through the FortiGuard network is the most secure way of delivering FortiToken data once the token has been seeded because it eliminates the risk of seed files being compromised during transit or storage. The other methods involve physical or manual delivery of seed files which can be intercepted, lost, or stolen. Reference: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372403/fortitoken
質問 # 28
You want to monitor FortiAuthenticator system information and receive FortiAuthenticator traps through SNMP.
Which two configurations must be performed after enabling SNMP access on the FortiAuthenticator interface? (Choose two)
- A. Upload management information base (MIB) files to SNMP server
- B. Set the tresholds to trigger SNMP traps
- C. Associate an ASN, 1 mapping rule to the receiving host
- D. Enable logging services
正解:A、B
解説:
To monitor FortiAuthenticator system information and receive FortiAuthenticator traps through SNMP, two configurations must be performed after enabling SNMP access on the FortiAuthenticator interface:
Set the thresholds to trigger SNMP traps for various system events, such as CPU usage, disk usage, memory usage, or temperature.
Upload management information base (MIB) files to SNMP server to enable the server to interpret the SNMP traps sent by FortiAuthenticator.
質問 # 29
You are a FortiAuthenticator administrator for a large organization. Users who are configured to use FortiToken 200 for two-factor authentication can no longer authenticate. You have verified that only the users with two-factor authentication are experiencing the issue.
What can cause this issue?
- A. Time drift between FortiAuthenticator and hardware tokens
- B. FortiAuthenticator has lost contact with the FortiToken Cloud servers
- C. FortiToken 200 license has expired
- D. One of the FortiAuthenticator devices in the active-active cluster has failed
正解:A
解説:
One possible cause of the issue is time drift between FortiAuthenticator and hardware tokens. Time drift occurs when the internal clocks of FortiAuthenticator and hardware tokens are not synchronized. This can result in mismatched one-time passwords (OTPs) generated by the hardware tokens and expected by FortiAuthenticator. To prevent this issue, FortiAuthenticator provides a time drift tolerance option that allows a certain number of seconds of difference between the clocks.
質問 # 30
Which option correctly describes an SP-initiated SSO SAML packet flow for a host without a SAML assertion?
- A. Principal contacts idendity provider and is redirected to service provider, principal establishes connection with service provider, service provider validates authentication with identify provider
- B. Service provider contacts idendity provider, idendity provider validates principal for service provider, service provider establishes communication with principal
- C. Principal contacts idendity provider and authenticates, identity provider relays principal to service provider after valid authentication
- D. Principal contacts service provider, service provider redirects principal to idendity provider, after succesfull authentication identify provider redirects principal to service provider
正解:D
解説:
SP-initiated SSO SAML packet flow for a host without a SAML assertion is as follows:
Principal contacts service provider, requesting access to a protected resource.
Service provider redirects principal to identity provider, sending a SAML authentication request.
Principal authenticates with identity provider using their credentials.
After successful authentication, identity provider redirects principal back to service provider, sending a SAML response with a SAML assertion containing the principal's attributes.
Service provider validates the SAML response and assertion, and grants access to the principal.
質問 # 31
Examine the screenshot shown in the exhibit.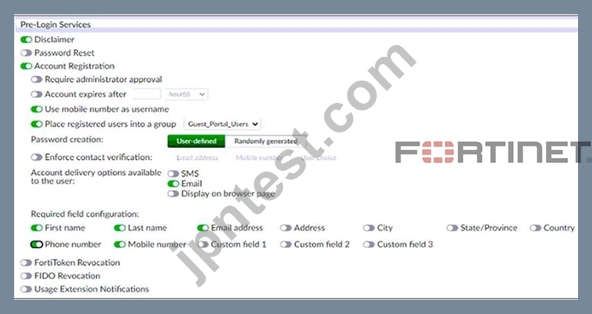
Which two statements regarding the configuration are true? (Choose two.)
- A. All accounts registered through the guest portal must be validated through email
- B. Guest user account will expire after eight hours
- C. All guest accounts created using the account registration feature will be placed under the Guest_Portal_Users group
- D. Guest users must fill in all the fields on the registration form
正解:A、C
解説:
The screenshot shows that the account registration feature is enabled for the guest portal and that the guest group is set to Guest_Portal_Users. This means that all guest accounts created using this feature will be placed under that group1. The screenshot also shows that email validation is enabled for the guest portal and that the email validation link expires after 24 hours. This means that all accounts registered through the guest portal must be validated through email within that time frame1.
質問 # 32
Which EAP method is known as the outer authentication method?
- A. EAP-GTC
- B. MSCHAPV2
- C. EAP-TLS
- D. PEAP
正解:D
解説:
PEAP is known as the outer authentication method because it establishes a secure tunnel between the client and the server using TLS. The inner authentication method, such as EAP-GTC, EAP-TLS, or MSCHAPV2, is then used to authenticate the client within the tunnel.
質問 # 33
You are the administrator of a global enterprise with three FortiAuthenticator devices. You would like to deploy them to provide active-passive HA at headquarters, with geographically distributed load balancing.
What would the role settings be?
- A. One standalone and two load balancers
- B. One standalone primary, one cluster member, and one load balancer
- C. Two cluster members and one load balancer
- D. Two cluster members and one backup
正解:B
解説:
To deploy three FortiAuthenticator devices to provide active-passive HA at headquarters, with geographically distributed load balancing, the role settings would be:
One standalone primary, which acts as the master device for HA and load balancing One cluster member, which acts as the backup device for HA and load balancing One load balancer, which acts as a remote device that forwards authentication requests to the primary or cluster member device
質問 # 34
Which two types of digital certificates can you create in Fortiauthenticator? (Choose two)
- A. Third-party root certificate
- B. User certificate
- C. Local service certificate
- D. Organization validation certificate
正解:B、C
解説:
FortiAuthenticator can create two types of digital certificates: user certificates and local service certificates. User certificates are issued to users or devices for authentication purposes, such as VPN, wireless, or web access. Local service certificates are issued to FortiAuthenticator itself for securing its own services, such as HTTPS, RADIUS, or LDAP.
質問 # 35
Which two features of FortiAuthenticator are used for EAP deployment? (Choose two)
- A. RADIUS server
- B. LDAP server
- C. Certificate authority
- D. MAC authentication bypass
正解:A、C
解説:
Two features of FortiAuthenticator that are used for EAP deployment are certificate authority and RADIUS server. Certificate authority allows FortiAuthenticator to issue and manage digital certificates for EAP methods that require certificate-based authentication, such as EAP-TLS or PEAP-EAP-TLS. RADIUS server allows FortiAuthenticator to act as an authentication server for EAP methods that use RADIUS as a transport protocol, such as EAP-GTC or PEAP-MSCHAPV2.
質問 # 36
An administrator has an active directory (AD) server integrated with FortiAuthenticator. They want members of only specific AD groups to participate in FSSO with their corporate FortiGate firewalls.
How does the administrator accomplish this goal?
- A. Configure a FortiGate filter on FortiAuthenticatoc
- B. Configure fine-grained controls on FortiAuthenticator to designate AD groups.
- C. Configure SSO groups and assign them to FortiGate groups.
- D. Configure a domain groupings list to identify the desired AD groups.
正解:C
解説:
To allow members of only specific AD groups to participate in FSSO with their corporate FortiGate firewalls, the administrator can configure SSO groups and assign them to FortiGate groups. SSO groups are groups of users or devices that are defined on FortiAuthenticator based on various criteria, such as user group membership, source IP address, MAC address, or device type. FortiGate groups are groups of users or devices that are defined on FortiGate based on various criteria, such as user group membership, firewall policy, or authentication method. By mapping SSO groups to FortiGate groups, the administrator can control which users or devices can access the network resources protected by FortiGate.
質問 # 37
When you are setting up two FortiAuthenticator devices in active-passive HA, which HA role must you select on the master FortiAuthenticator?
- A. Load balancing master
- B. Cluster member
- C. Standalone master
- D. Active-passive master
正解:D
解説:
When you are setting up two FortiAuthenticator devices in active-passive HA, you need to select the active-passive master role on the master FortiAuthenticator device. This role means that the device will handle all requests and synchronize data with the slave device until a failover occurs. The slave device must be configured as an active-passive slave role. The other roles are used for different HA modes, such as standalone (no HA), cluster (active-active), or load balancing (active-active with load balancing). Reference: https://docs.fortinet.com/document/fortiauthenticator/6.4/administration-guide/372411/high-availability
質問 # 38
......
100%合格保証付きの素晴らしいNSE6_FAC-6.4試験問題PDF:https://www.jpntest.com/shiken/NSE6_FAC-6.4-mondaishu
