[2024年最新] 最高の5V0-41.21試験問題集を使って- 実際の試験問題と解答を解こう
テストエンジンを練習して5V0-41.21テスト問題
質問 # 16
An administrator needs to send FW connections logs to a remote server.
Which sequence of commands does the administrator need to apply on their ESXi Host?
A)
B)
C)
D)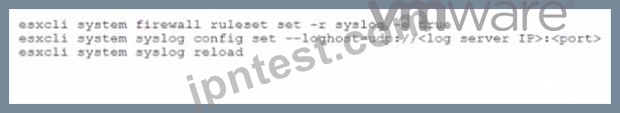
- A. Option B
- B. Option A
- C. Option C
- D. Option D
正解:C
質問 # 17
Which two statements are true about IDS/IPS signatures? (Choose two.)
- A. Users can upload their own IDS signature definitions from the NSX UI.
- B. An IDS signature contains data used to identify known exploits and vulnerabilities.
- C. Users can create their own IDS signature definitions from the NSX UI.
- D. IDS Signatures can be High Risk, Suspicious, Low Risk and Trustworthy.
- E. An IDS signature contains a set of instructions that determine which traffic is analyzed.
正解:B、C
質問 # 18
Which dot color indicates an on-going attack of medium severity in the IDS/IPS events tab of NSX-T Data Center'
- A. blinking orange dot
- B. blinking yellow dot
- C. solid red dot
- D. solid orange dot
正解:C
質問 # 19
Refer to the exhibit.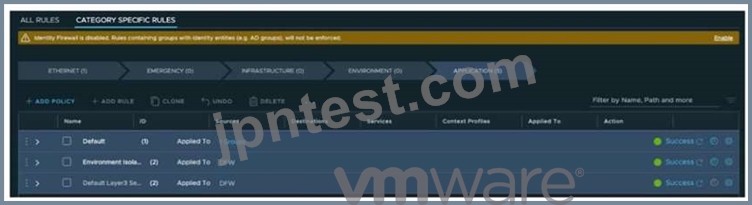
An administrator needs to configure a security policy with a firewall rule allowing a group of applications to retrieve the correct time from an NTP server. Which is the category to configure this security policy and firewall rule?
- A. Infrastructure
- B. Environment
- C. Application
- D. Emergency
正解:A
質問 # 20
An NSX administrator has been tasked with deploying a NSX Edge Virtual machine through an ISO image.
Which virtual network interface card (vNIC) type must be selected while creating the NSX Edge VM allow participation in overlay and VLAN transport zones?
- A. VMXNET3
- B. Flexible
- C. VMXNET2
- D. e1000
正解:A
質問 # 21
Which three security objects are provided as an output in a recommendation session in NSX Intelligence?
(Choose three.)
- A. gateway firewall rules
- B. security groups
- C. distributed firewall rules
- D. security service
- E. context profiles
正解:B、D、E
質問 # 22
What is the NSX feature that allows a user to block ICMP between 192.168.1.100 and 192.168.1.101?
- A. NSX Distributed Switch Agent
- B. NSX Distributed Routing
- C. NSX Distributed Firewall
- D. NSX Distributed IDS/IPS
正解:B
質問 # 23
Refer to the exhibit.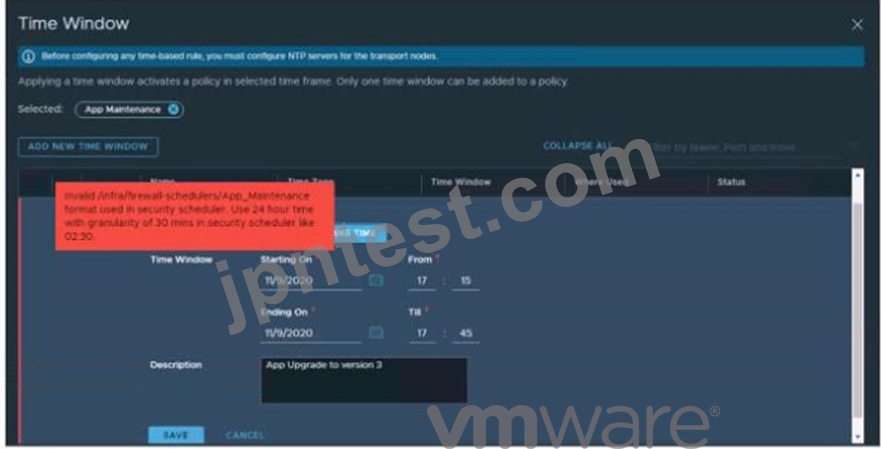
A security administrator is configuring a time window to create a time-based distributed firewall rule. While configuring the time window, an error displayed as shown in the exhibit. Which action will resolve the problem?
- A. Change the time windows frequency
- B. Restart me NTP service on the ESXl host.
- C. Configure the ESXl host to use a remote NTP server.
- D. Change the time window interval.
正解:C
解説:
The most likely action to resolve the problem is to configure the ESXi host to use a remote NTP server. The time window requires the ESXi host to be synchronized to a time source in order to properly calculate the time window, and the error is likely due to the ESXi host not being synchronized. Configuring the ESXi host to use a remote NTP server should ensure that the host is properly synchronized, and allow the time window to be configured correctly. Reference: [1] https://docs.vmware.com/en/VMware-NSX-T/3.0/vmware-nsx-t-30-administration-guide/GUID-DD7F38A3-3D3B-47F1-92D7-9A4D4F3C44E1.html [2] https://www.vmware.com/support/vsphere/doc/vsphere-esxi-vcenter-server-601-configuration-maximums.html
質問 # 24
When configuring members of a Security Group, which membership criteria art permitted?
- A. Virtual Interface, Segment, Physical Machine, and IP Set
- B. Virtual Interface, Segment, Cloud Native Service Instance, and IP Set.
- C. Segment Port, Segment, Virtual Machine, and IP Set
- D. Virtual Machine, Physical Machine, Cloud Native Service Instance, and IP Set
正解:A
質問 # 25
Which two are true of the NSX Gateway Firewall? (Choose two.)
- A. Security Groups can be used in Applied-To column.
- B. Firewall rules in System category cannot be edited.
- C. Applied-To can be configured at Firewall Policy level.
- D. NAT service can be configured in NSX Gateway Firewall policy.
- E. Firewall rules in Pre Rule category are applied to all gateways.
正解:C、E
質問 # 26
Which of the following are the local user accounts used to administer NSX-T Data Center?
- A. admin, super, read-only
- B. admin, audit, root
- C. operator, admin, root
- D. operator, admin, audit
正解:D
解説:
For further reading, see the VMware NSX-T Data Center Administration Guide (https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/com.vmware.nsxt.admin.doc/GUID-4A4E9FBE-50B3-4F8F-B6C4-8527E7A08A67.html) for more information on user accounts and permissions in NSX-T Data Center.
質問 # 27
What is the default action of the Default Layer 3 distributed firewall rule?
- A. Forward
- B. Allow
- C. Reject
- D. Drop
正解:D
解説:
The Default Layer 3 distributed firewall rule is a system-defined rule in NSX-T Data Center that applies to all distributed firewall sections. By default, this rule is set to drop all traffic, meaning that any traffic that does not match a specific rule will be dropped.
For more information on the Default Layer 3 distributed firewall rule and how to configure it, please refer to the NSX-T Data Center documentation: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.0/nsx-t-3.0-firewall/GUID-B6B835F2-B6F2-4468-8F8E-6F7B9B9D6E91.html
質問 # 28
Which two Guest OS drivers are required for the Identity Firewall to operate? (Choose two.)
- A. NSX Network Introspection
- B. e1000e
- C. Guest Introspection
- D. NSX File Introspection
- E. vmxnet3
正解:A、C
解説:
The two Guest OS drivers that are required for the Identity Firewall to operate are NSX Network Introspection and Guest Introspection. NSX Network Introspection provides network-level visibility and control, while Guest Introspection provides kernel-level visibility and control. The other drivers listed, vmxnet3, NSX File Introspection, and e1000e, are not required for the Identity Firewall to operate.
質問 # 29
Which two are requirements for URL Analysis? (Choose two.)
- A. The NSX Edge nodes require access to the Internet to download category and reputation definitions.
- B. A layer 7 gateway firewall rule must be configured on the tier-0 gateway uplink to capture DNS traffic.
- C. The ESXi hosts require access to the Internet to download category and reputation definitions.
- D. A layer 7 gateway firewall rule must be configured on the tier-1 gateway uplink to capture DNS traffic,
- E. The NSX Manager requires access to the Internet to download category and reputation definitions.
正解:A、D
解説:
The NSX Edge nodes require access to the Internet to download category and reputation definitions, and a layer 7 gateway firewall rule must be configured on the tier-1 gateway uplink to capture DNS traffic. This will allow the URL Analysis service to analyze incoming DNS traffic and block malicious requests. For more information, please see this VMware Documentation article[1], which explains how to configure URL Analysis on NSX.
[1] https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/nsxt_31_url_analysis/GUID-46BC65F3-7A45-4A9F-B444-E4A1A7E0AC4A.html
質問 # 30
An administrator is creating the first distributed firewall rules for a company's salts department. What is the first object that must be created in the distributed firewall'
- A. firewall service
- B. firewall folder
- C. firewall policy
- D. firewall file
正解:C
解説:
The first object that must be created in the distributed firewall is a firewall policy. A firewall policy is a set of rules that define what traffic is allowed or blocked on a given network. When creating a policy, the administrator must specify the source and destination address and port, as well as the type of traffic that is allowed or blocked. The policy will then be applied to the distributed firewall, allowing it to enforce the rules specified in the policy. Reference: [1] https://docs.vmware.com/en/VMware-NSX-T/3.0/vmware-nsx-t-30-administration-guide/GUID-4CAF59C8-13F3-4F3E-B53E-D8F1E03FBE7B.html [2] https://www.vmware.com/content/dam/digitalmarketing/vmware/en/pdf/techpaper/vmware-nsx-data-center-for-vsphere-distributed-firewall-deployment-guide.pdf
質問 # 31
An organization wants to add security controls for contractor virtual desktops. Which statement Is true when configuring an NSX Identity firewall rule?
- A. User Identity can only be used in the Source section of the firewall rule.
- B. User Identity can only be used in the Destination Section of the firewall rule.
- C. User Identity can be used in the both the Source and the Destination sections of the firewall rule.
- D. User Identity cannot be used in Source or Destination sections of the firewall rule.
正解:A
解説:
In NSX-T, Identity firewall rules allow you to specify security controls based on the identity of the user, rather than the IP address or other network-based attributes. User identity can be used as a source in the firewall rule.
質問 # 32
Which two are the insertion points for North-South service insertion? (Choose two.)
- A. Transport Node NIC
- B. Uplink of tier-1 gateway
- C. Uplink of tier-0 gateway
- D. Guest VM vNIC
- E. Partner Service VM
正解:C、E
質問 # 33
Which three are required to configure a firewall rule on a getaway to allow traffic from the internal to web servers? (Choose three.)
- A. Enable Firewall Service for gateway.
- B. Disable the firewall rule in Default category.
- C. Create a firewall rule in System category.
- D. Add a firewall rule in Local Gateway category.
- E. Create a firewall policy in Local Gateway category.
- F. Create a URL analysis profile for web hosting category.
正解:A、D、E
解説:
In order to configure a firewall rule on a gateway to allow traffic from the internal to web servers, the administrator needs to enable the Firewall Service for the gateway, create a firewall policy in the Local Gateway category, and add a firewall rule in the Local Gateway category. This firewall rule should specify the web servers as the destination and the internal network as the source.
For more information on how to configure firewall rules on a gateway, please refer to the NSX-T Data Center documentation: https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.0/nsx-t-3.0-firewall/GUID-3A79CA7A-9D5E-4F2B-8F75-4EA298E4A4D5.html
質問 # 34
Which dot color indicates an on-going attack of medium severity in the IDS/IPS events tab of NSX-T Data Center?
- A. solid red dot
- B. blinking orange dot
- C. solid orange dot
- D. blinking yellow dot
正解:C
解説:
The dot color that indicates an on-going attack of medium severity in the IDS/IPS events tab of NSX-T Data Center is a solid orange dot. This indicates that the attack has been detected and is ongoing at a medium severity level.
Reference:
In the IDS/IPS events tab of NSX-T Data Center, different colors of dots are used to indicate the severity of an attack.
A solid red dot indicates a critical attack, which is the highest severity level.
A solid orange dot indicates a medium attack, which is a moderate severity level.
A solid yellow dot indicates a low attack, which is the lowest severity level.
In this case, a solid orange dot is used to indicate an on-going attack of medium severity in the IDS/IPS events tab of NSX-T Data Center.
It's worth noting that there is no blinking dots in this context, all the dots are solid.
VMware NSX-T Data Center documentation https://docs.vmware.com/en/VMware-NSX-T-Data-Center/index.html VMware NSX-T Data Center Intrusion Detection and Prevention documentation https://docs.vmware.com/en/VMware-NSX-T-Data-Center/3.1/com.vmware.nsxt.ids.doc/GUID-C4ED1F4D-4E4B-4A9C-9F5C-7AC081A5C5D5.html
質問 # 35
A security administrator has configured NSX Intelligence for discovery. They would like to get recommendations based on the changes in the scope of the input entities every hour.
What needs to be configured to achieve the requirement?
- A. Publish the recommendations.
- B. Start a new recommendation.
- C. Adjust the time range to 1 hour.
- D. Toggle the monitoring option on.
正解:D
質問 # 36
To which network operations does a user with the Security Engineer role have full access permission?
- A. Networking Load Balancing, Networking DNS, Networking Forwarding Policies
- B. Networking Forwarding Policies, Networking NAT, Networking VPN
- C. Networking DHCP, Networking NAT, Networking Segments
- D. Networking IP Address Pools, Networking NAT, Networking DHCP
正解:C
質問 # 37
Which vCenter component is used by the NSX Manager to deploy the Partner Service VM on every host of a cluster configured for guest introspection?
- A. Update Manager (VUM)
- B. Component Manager
- C. Auto Deploy
- D. ESXi Agent Manager (EAM)
正解:B
質問 # 38
Which is an insertion point for East-West service insertion?
- A. Partner SVM
- B. transport node
- C. Guest VM vNlC
- D. tier-1 gateway
正解:D
質問 # 39
......
VMware 5V0-41.21 試験は、105分以内に完了する必要がある45の多肢選択問題から構成されています。この試験は英語と日本語で提供され、オンライン、またはテストセンターで受験することができます。試験料金は$250で、受験者は500点満点中300点以上を取得する必要があります。
5V0-41.21実際の問題アンサーPDFには100%カバー率リアルな試験問題:https://www.jpntest.com/shiken/5V0-41.21-mondaishu
