あなたのNSE4_FGT-7.0試験100%合格問題集はここJPNTestで一発合格
突破上級者がシミュレーションされたNSE4_FGT-7.0試験問題集PDF
質問 # 12
Examine the network diagram shown in the exhibit, then answer the following question: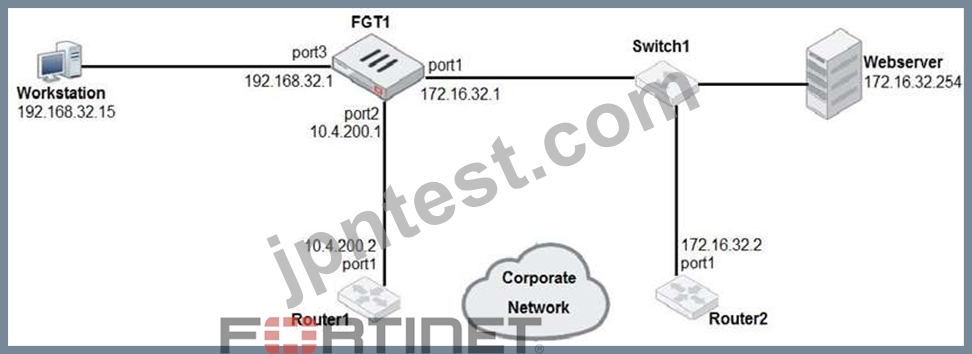
Which one of the following routes is the best candidate route for FGT1 to route traffic from the Workstation to the Web server?
- A. 172.16.32.0/24 is directly connected, port1
- B. 172.16.0.0/16 [50/0] via 10.4.200.2, port2 [5/0]
- C. 0.0.0.0/0 [20/0] via 10.4.200.2, port2
- D. 10.4.200.0/30 is directly connected, port2
正解:A
質問 # 13
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
- A. The collector agent uses a Windows API to query DCs for user logins.
- B. The collector agent must search security event logs.
- C. The NetSession Enum function is used to track user logouts.
- D. NetAPI polling can increase bandwidth usage in large networks.
正解:C
解説:
Reference:
https://kb.fortinet.com/kb/microsites/search.do?cmd=displayKC&docType=kc&externalId=FD34906&sliceId=1&docTypeID=DT_KCARTICLE_1_1&dialogID=210966035&stateId=1%200%20210968009%27)
質問 # 14
Refer to the exhibit.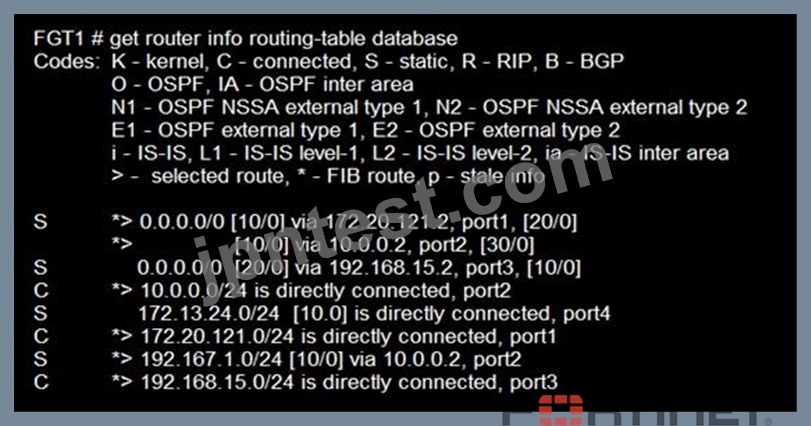
Given the routing database shown in the exhibit, which two statements are correct? (Choose two.)
- A. The port1 and port2 default routes are active in the routing table.
- B. The port3 default route has the highest distance.
- C. There will be eight routes active in the routing table.
- D. The port3 default route has the lowest metric.
正解:A、B
質問 # 15
A network administrator is configuring a new IPsec VPN tunnel on FortiGate. The remote peer IP address is dynamic. In addition, the remote peer does not support a dynamic DNS update service.
What type of remote gateway should the administrator configure on FortiGate for the new IPsec VPN tunnel to work?
- A. Pre-shared Key
- B. Static IP Address
- C. Dynamic DNS
- D. Dialup User
正解:D
解説:
Dialup user is used when the remote peer's IP address is unknown. The remote peer whose IP address is unknown acts as the dialup clien and this is often the case for branch offices and mobile VPN clients that use dynamic IP address and no dynamic DNS
質問 # 16
Refer to the exhibit.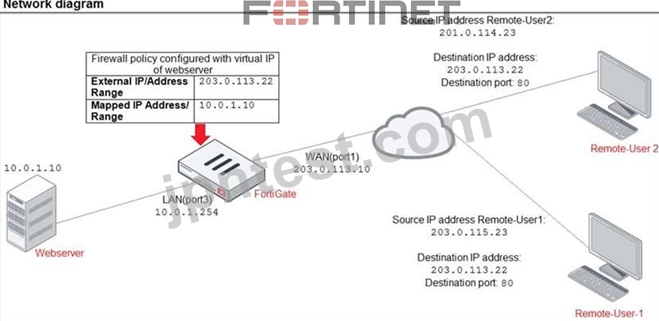
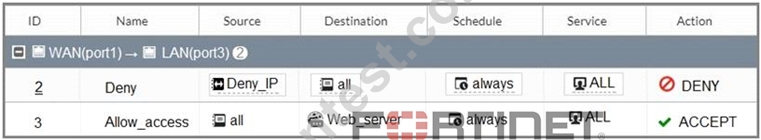
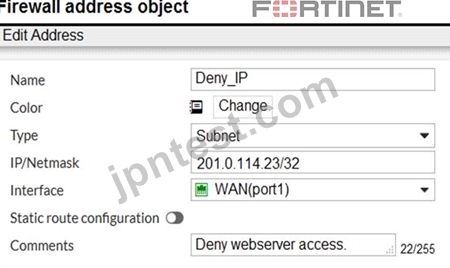
The exhibit contains a network diagram, firewall policies, and a firewall address object configuration.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-user2. Remote-user2 is still able to access Webserver.
Which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
- A. Set the Destination address as Deny_IP in the Allow-access policy.
- B. Enable match vip in the Deny policy.
- C. Disable match-vip in the Deny policy.
- D. Set the Destination address as Web_server in the Deny policy.
正解:B、D
質問 # 17
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
- A. get system arp
- B. diagnose sys top
- C. get system performance status
- D. get system status
正解:A
解説:
Explanation
"If you suspect that there is an IP address conflict, or that an IP has been assigned to the wrong device, you may need to look at the ARP table."
質問 # 18
Refer to the web filter raw logs.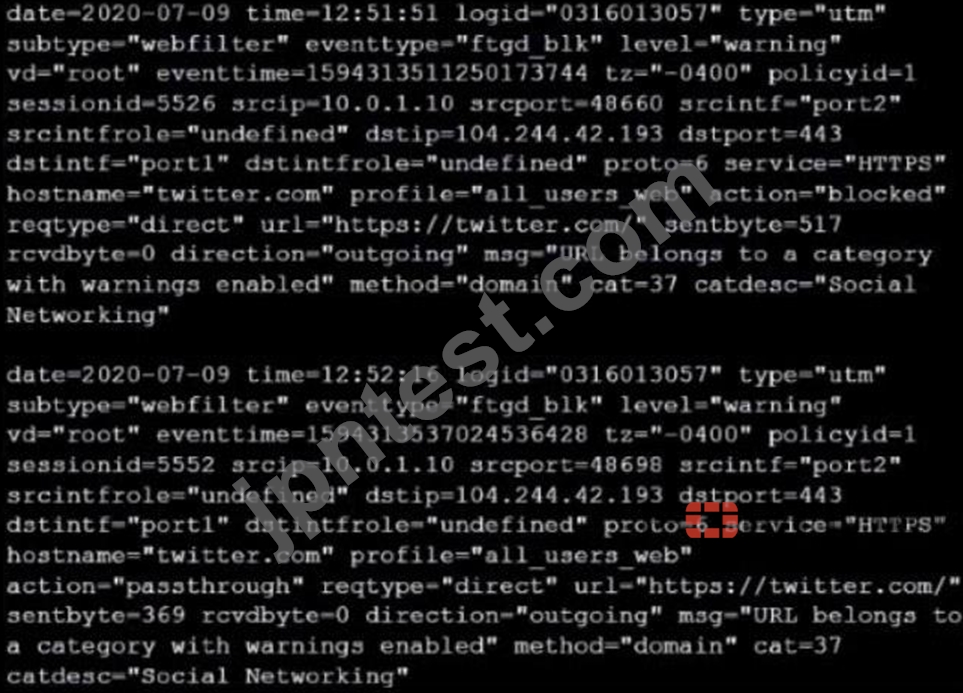
Based on the raw logs shown in the exhibit, which statement is correct?
- A. Access to the social networking web filter category was explicitly blocked to all users.
- B. The action on firewall policy ID 1 is set to warning.
- C. Social networking web filter category is configured with the action set to authenticate.
- D. The name of the firewall policy is all_users_web.
正解:C
質問 # 19
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
- A. Certificate inspection
- B. Full Content inspection
- C. Flow-based inspection
- D. Proxy-based inspection
正解:C、D
質問 # 20
View the exhibit.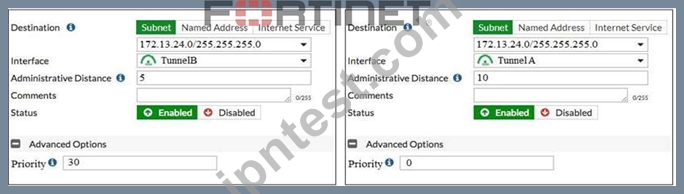
Which of the following statements are correct? (Choose two.)
- A. The TunnelB route is the primary route for reaching the remote site. The TunnelA route is used only if the TunnelB VPN is down.
- B. Dead peer detection must be disabled to support this type of IPsec setup.
- C. This setup requires at least two firewall policies with the action set to IPsec.
- D. This is a redundant IPsec setup.
正解:A、D
質問 # 21
View the exhibit.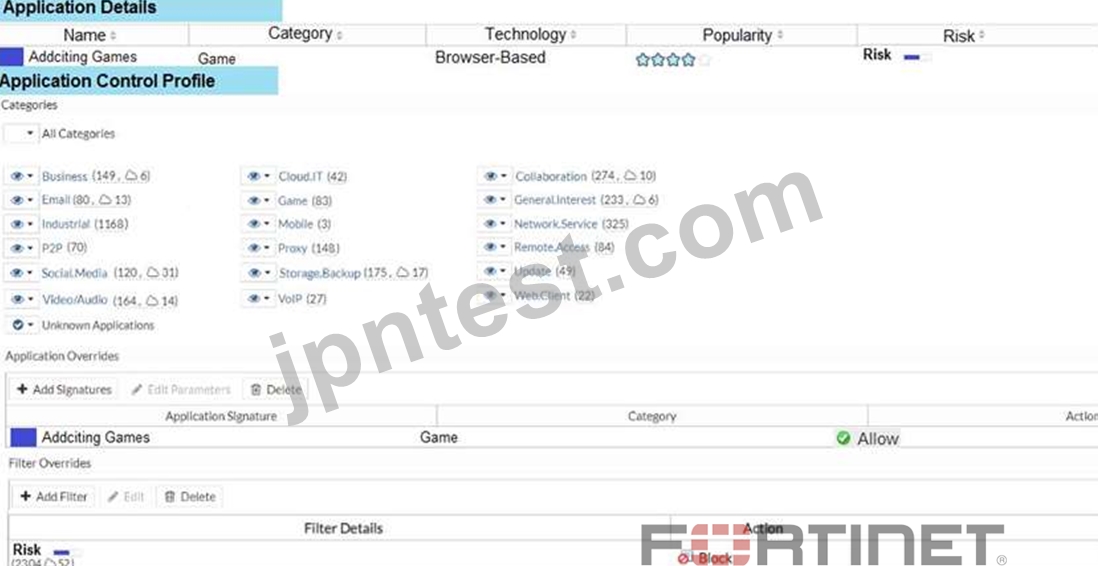
A user behind the FortiGate is trying to go to http://www.addictinggames.com (Addicting Games). Based on this configuration, which statement is true?
- A. Addicting.Games is blocked on the Filter Overrides configuration.
- B. Addcting.Games is allowed based on the Categories configuration.
- C. Addicting.Games is allowed based on the Application Overrides configuration.
- D. Addicting.Games can be allowed only if the Filter Overrides actions is set to Exempt.
正解:C
質問 # 22
Which type of logs on FortiGate record information about traffic directly to and from the FortiGate management IP addresses?
- A. Forward traffic logs
- B. Security logs
- C. System event logs
- D. Local traffic logs
正解:D
質問 # 23
An administrator wants to configure timeouts for users. Regardless of the useres behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
- A. soft-timeout
- B. idle-timeout
- C. new-session
- D. auth-on-demand
- E. hard-timeout
正解:E
解説:
Reference:
https://kb.fortinet.com/kb/documentLink.do?externalID=FD37221#:~:text=Hard%20timeout%3A%20User%20e
質問 # 24
An organization's employee needs to connect to the office through a high-latency internet connection.
Which SSL VPN setting should the administrator adjust to prevent the SSL VPN negotiation failure?
- A. Change the login timeout.
- B. Change the idle-timeout.
- C. Change the session-ttl.
- D. Change the udp idle timer.
正解:A
解説:
FortiGate_Security_7.0 page 607
質問 # 25
Which two statements are true about the RPF check? (Choose two.)
- A. The RPF check is run on the first sent and reply packet of any new session.
- B. The RPF check is run on the first reply packet of any new session.
- C. RPF is a mechanism that protects FortiGate and your network from IP spoofing attacks.
- D. The RPF check is run on the first sent packet of any new session.
正解:C、D
質問 # 26
A network administrator has enabled SSL certificate inspection and antivirus on FortiGate. When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the virus and the file can be downloaded.
What is the reason for the failed virus detection by FortiGate?
- A. SSL/SSH Inspection profile is incorrect
- B. Antivirus definitions are not up to date
- C. Antivirus profile configuration is incorrect
- D. Application control is not enabled
正解:A
解説:
https traffic requires SSL decryption. Check the ssh inspection profile
質問 # 27
Exhibit: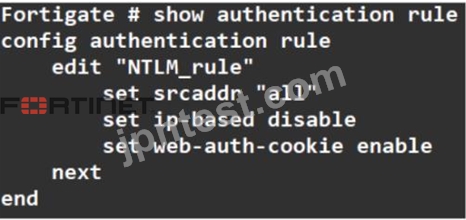
Refer to the exhibit to view the authentication rule configuration In this scenario, which statement is true?
- A. Policy-based authentication is enabled
- B. Session-based authentication is enabled.
- C. IP-based authentication is enabled
- D. Route-based authentication is enabled
正解:B
質問 # 28
Which three criteria can a FortiGate use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Lowest to highest policy ID number.
- B. Destination defined as Internet Services in the firewall policy.
- C. Services defined in the firewall policy.
- D. Source defined as Internet Services in the firewall policy.
- E. Highest to lowest priority defined in the firewall policy.
正解:B、C、D
質問 # 29
When a firewall policy is created, which attribute is added to the policy to support recording logs to a FortiAnalyzer or a FortiManager and improves functionality when a FortiGate is integrated with these devices?
- A. Universally Unique Identifier
- B. Sequence ID
- C. Log ID
- D. Policy ID
正解:A
解説:
Reference: https://docs.fortinet.com/document/fortigate/6.0.0/handbook/554066/firewall-policies
"Universally Unique Identifier (UUID) attributes have been added to policies to improve functionality when working with FortiManager or FortiAnalyzer units"
質問 # 30
Refer to the exhibit.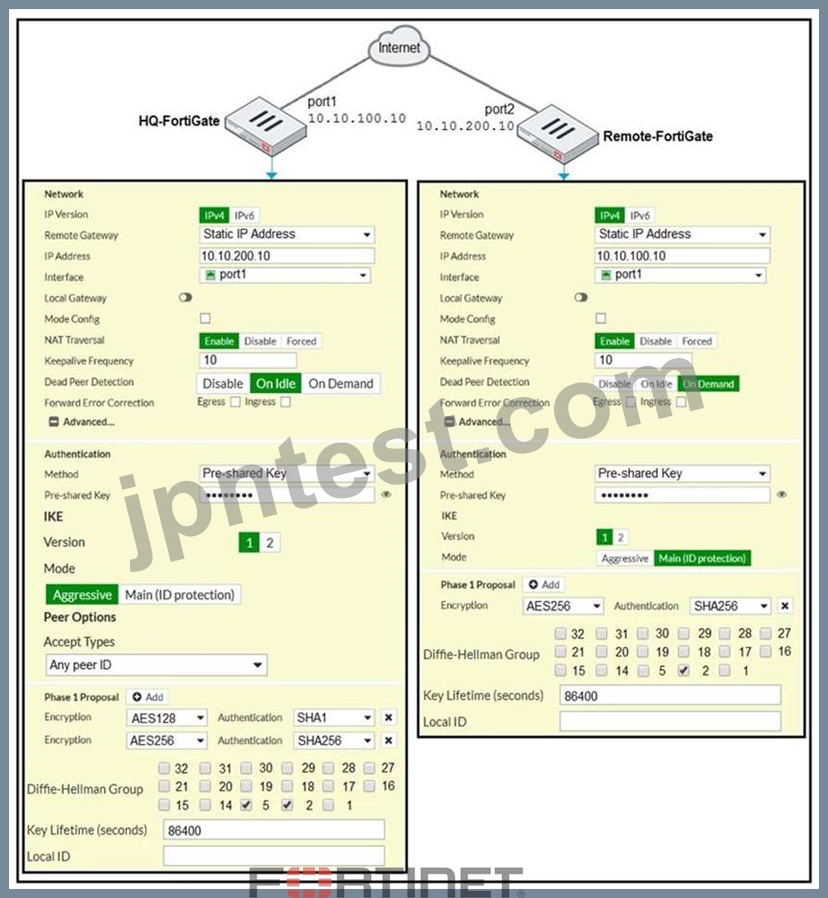
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
- A. On HQ-FortiGate, disable Diffie-Helman group 2
- B. On HQ-FortiGate, set IKE mode to
- C. On both FortiGate devices, set
- D. On Remote-FortiGate, set port2
正解:B、D
解説:
Explanation
FortiGate Infrastructure 7.0 Study Guide p. 222 FortiGate Infrastructure 7.0 Study Guide p. 208
質問 # 31
Refer to the exhibit.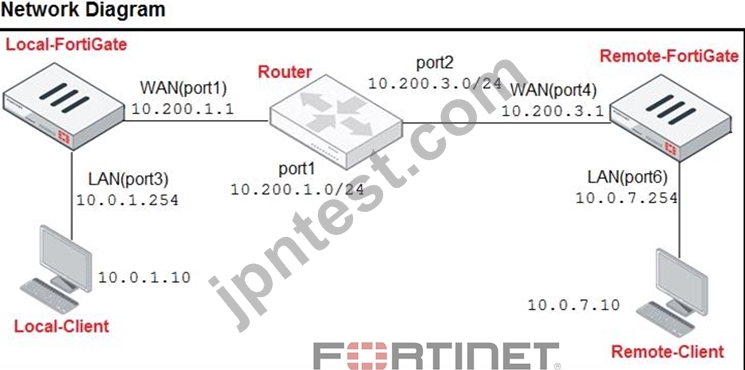
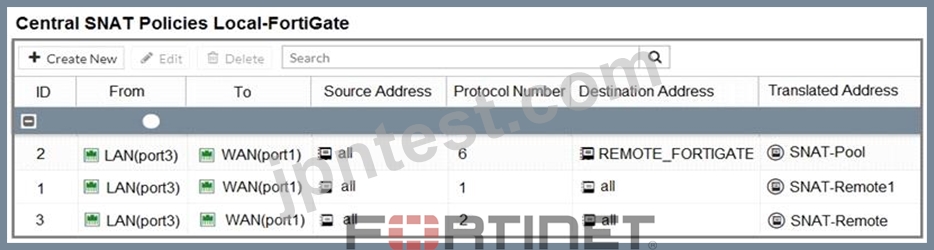
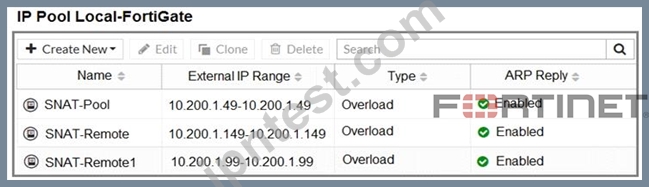
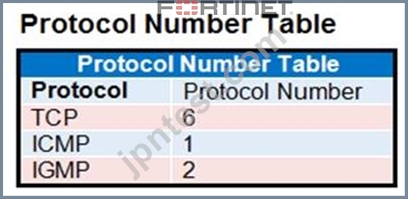
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0.1.10) pings the IP address of Remote-FortiGate (10.200.3.1)?
- A. 10.200.1.1
- B. 10.200.1.49
- C. 10.200.1.149
- D. 10.200.1.99
正解:D
質問 # 32
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A. FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
- B. FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
- C. FortiGate automatically negotiates a new security association after the existing security association expires.
- D. FortiGate automatically negotiates different local and remote addresses with the remote peer.
正解:A
解説:
https://kb.fortinet.com/kb/documentLink.do?externalID=12069
質問 # 33
What is the primary FortiGate election process when the HA override setting is disabled?
- A. Connected monitored ports > HA uptime > Priority > FortiGate Serial number
- B. Connected monitored ports > Priority > System uptime > FortiGate Serial number
- C. Connected monitored ports > System uptime > Priority > FortiGate Serial number
- D. Connected monitored ports > Priority > HA uptime > FortiGate Serial number
正解:A
解説:
Reference: http://myitmicroblog.blogspot.com/2018/11/what-should-you-know-about-ha-override.html FortiGate_Infrastructure_7.0 page 304 PUPS - Ports/Uptime/Priority/Serial
質問 # 34
Refer to the exhibit to view the firewall policy.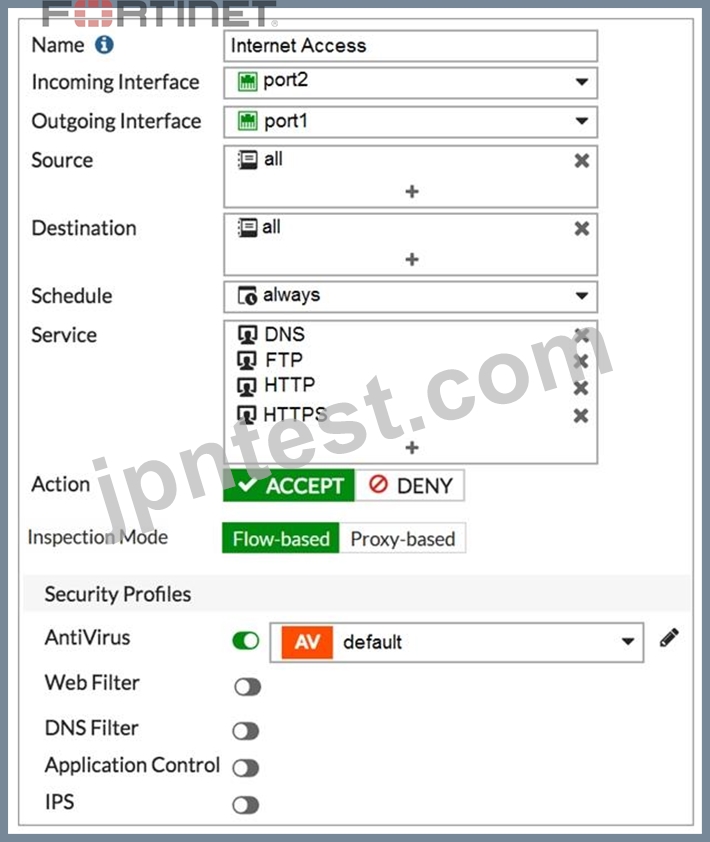
Which statement is correct if well-known viruses are not being blocked?
- A. The firewall policy does not apply deep content inspection.
- B. The firewall policy must be configured in proxy-based inspection mode.
- C. The action on the firewall policy must be set to deny.
- D. Web filter should be enabled on the firewall policy to complement the antivirus profile.
正解:A
解説:
Explanation
Without deep inspection, you would never find a virus in HTTPS traffic. You will only catch a virus when it is send to you via HTTP or FTP with these settings.
質問 # 35
......
Fortinet NSE4_FGT-7.0 認定試験は、FortinetのFortiOS 7.0プラットフォームを使用してセキュリティソリューションを展開、設定、管理する知識と専門知識を検証したい専門家向けに設計されています。この認定は、サイバーセキュリティソリューションの主要なプロバイダーであるFortinetが提供するネットワークセキュリティエキスパート(NSE)プログラムの一部です。NSE4_FGT-7.0試験に合格した候補者は、Fortinet NSE 4認定プロフェッショナルとして認められ、ネットワークセキュリティおよびFortiOS 7.0技術の熟練度を示すことができます。
NSE4_FGT-7.0問題集トレーニングコース完全版:https://www.jpntest.com/shiken/NSE4_FGT-7.0-mondaishu
