最新 [2023年01月23日]Fortinet NSE4_FGT-7.0試験練習でテストの素晴らしい結果を出そう
あなたのキャリアーを稼いで飛躍せよFortinet NSE4_FGT-7.0
質問 81
Which CLI command allows administrators to troubleshoot Layer 2 issues, such as an IP address conflict?
- A. get system status
- B. diagnose sys top
- C. get system performance status
- D. get system arp
正解: D
解説:
"If you suspect that there is an IP address conflict, or that an IP has been assigned to the wrong device, you may need to look at the ARP table."
質問 82
Which two statements ate true about the Security Fabric rating? (Choose two.)
- A. Many of the security issues can be fixed immediately by clicking Apply where available.
- B. The Security Fabric rating must be run on the root FortiGate device in the Security Fabric.
- C. It provides executive summaries of the four largest areas of security focus.
- D. The Security Fabric rating is a free service that comes bundled with alt FortiGate devices.
正解: A,B
質問 83
What inspection mode does FortiGate use if it is configured as a policy-based next-generation firewall (NGFW)?
- A. Full Content inspection
- B. Proxy-based inspection
- C. Certificate inspection
- D. Flow-based inspection
正解: D
解説:
Explanation
The default mode is flow based for the policies. NGFW mode does not change the inspection mode.
質問 84
Which of the following statements about central NAT are true? (Choose two.)
- A. Destination NAT, using central NAT, requires a VIP object as the destination address in a firewall.
- B. IP tool references must be removed from existing firewall policies before enabling central NAT.
- C. Central NAT can be enabled or disabled from the CLI only.
- D. Source NAT, using central NAT, requires at least one central SNAT policy.
正解: B,C
質問 85
Which two statements about antivirus scanning mode are true? (Choose two.)
- A. In flow-based inspection mode, FortiGate buffers the file, but also simultaneously transmits it to the client.
- B. In proxy-based inspection mode, files bigger than the buffer size are scanned.
- C. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
- D. In flow-based inspection mode, files bigger than the buffer size are scanned.
正解: A,C
解説:
An antivirus profile in full scan mode buffers up to your specified file size limit. The default is 10 MB. That is large enough for most files, except video files. If your FortiGate model has more RAM, you may be able to increase this threshold. Without a limit, very large files could exhaust the scan memory. So, this threshold balances risk and performance. Is this tradeoff unique to FortiGate, or to a specific model? No. Regardless of vendor or model, you must make a choice. This is because of the difference between scans in theory, that have no limits, and scans on real-world devices, that have finite RAM. In order to detect 100% of malware regardless of file size, a firewall would need infinitely large RAM-something that no device has in the real world. Most viruses are very small. This table shows a typical tradeoff. You can see that with the default 10 MB threshold, only 0.01% of viruses pass through.
質問 86
Which of the following are purposes of NAT traversal in IPsec? (Choose two.)
- A. To force a new DH exchange with each phase 2 rekey.
- B. To encapsulation ESP packets in UDP packets using port 4500.
- C. To detect intermediary NAT devices in the tunnel path.
- D. To dynamically change phase 1 negotiation mode aggressive mode.
正解: B,C
質問 87
Refer to the exhibit showing a debug flow output.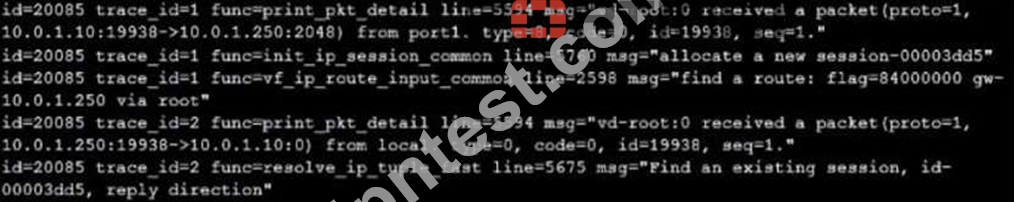
Which two statements about the debug flow output are correct? (Choose two.)
- A. The debug flow is of ICMP traffic.
- B. A firewall policy allowed the connection.
- C. A new traffic session is created.
- D. The default route is required to receive a reply.
正解: A,C
質問 88
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
- A. FortiGate does not support full SSL inspection when web filtering is enabled.
- B. The browser requires a software update.
- C. There are network connectivity issues.
- D. The CA certificate set on the SSL/SSH inspection profile has not been imported into the browser.
正解: D
解説:
Reference: https://kb.fortinet.com/kb/documentLink.do?externalID=FD41394
質問 89
Which three statements about a flow-based antivirus profile are correct? (Choose three.)
- A. Flow-based inspection uses a hybrid of scanning modes available in proxy-based inspection.
- B. If the virus is detected, the last packet is delivered to the client.
- C. IPS engine handles the process as a standalone.
- D. FortiGate buffers the whole file but transmits to the client simultaneously.
- E. Optimized performance compared to proxy-based inspection.
正解: A,D,E
解説:
Reference: https://forum.fortinet.com/tm.aspx?m=192309
質問 90
What is the effect of enabling auto-negotiate on the phase 2 configuration of an IPsec tunnel?
- A. FortiGate automatically brings up the IPsec tunnel and keeps it up, regardless of activity on the IPsec tunnel.
- B. FortiGate automatically negotiates a new security association after the existing security association expires.
- C. FortiGate automatically negotiates different local and remote addresses with the remote peer.
- D. FortiGate automatically negotiates different encryption and authentication algorithms with the remote peer.
正解: A
解説:
https://kb.fortinet.com/kb/documentLink.do?externalID=12069
質問 91
Which two statements about IPsec authentication on FortiGate are correct? (Choose two.)
- A. A certificate is not required on the remote peer when you set the signature as the authentication method.
- B. For a stronger authentication, you can also enable extended authentication (XAuth) to request the remote peer to provide a username and password
- C. FortiGate supports pre-shared key and signature as authentication methods.
- D. Enabling XAuth results in a faster authentication because fewer packets are exchanged.
正解: B,C
解説:
Reference:
https://docs.fortinet.com/document/fortigate/6.2.0/cookbook/913287/ipsec-vpn-authenticating-aremote-fortigate-
質問 92
Which two policies must be configured to allow traffic on a policy-based next-generation firewall (NGFW) FortiGate? (Choose two.)
- A. SSL inspection and authentication policy
- B. Firewall policy
- C. Security policy
- D. Policy rule
正解: A,C
質問 93
Which downstream FortiGate VDOM is used to join the Security Fabric when split-task VDOM is enabled on all FortiGate devices?
- A. Global VDOM
- B. FG-traffic VDOM
- C. Customer VDOM
- D. Root VDOM
正解: D
質問 94
Refer to the exhibit.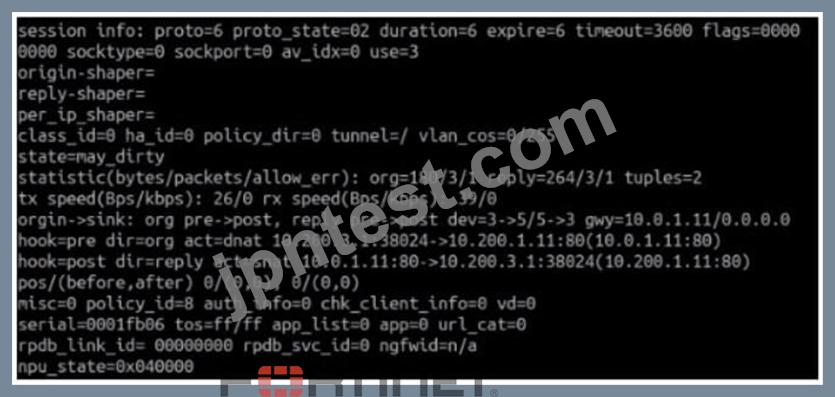
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
- A. The session is in FTN_WAIT state.
- B. The session is in FIN_ACK state.
- C. The session is in ESTABLISHED state.
- D. The session is in SYN_SENT state.
正解: D
解説:
Explanation
Indicates TCP (proto=6) session in SYN_SENT state (proto=state=2)
https://kb.fortinet.com/kb/viewContent.do?externalId=FD30042
質問 95
Which Security rating scorecard helps identify configuration weakness and best practice violations in your network?
- A. Security Posture
- B. Automated Response
- C. Optimization
- D. Fabric Coverage
正解: A
解説:
Reference:
https://www.fortinet.com/content/dam/fortinet/assets/support/fortinet-recommended-security-bestpractices.pdf Description of the three major scorecards is seen in Security fabric > Security rating>Security posture.
Security Posture Identify configuration weaknesses and best practice violations in your deployment. Fabric Coverage Identify in your overall network, where Security Fabric can enhance visibility and control.
Optimization Optimize your fabric deployment.
質問 96
Refer to the exhibit, which contains a radius server configuration.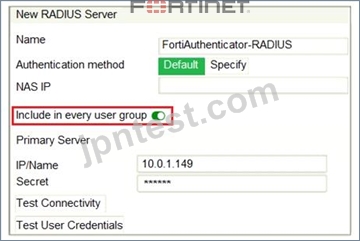
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
What will be the impact of using Include in every user group option in a RADIUS configuration?
- A. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
- B. This option places the RADIUS server, and all users who can authenticate against that server, into every FortiGate user group.
- C. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
- D. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
正解: B
質問 97
An administrator is configuring an IPsec VPN between site A and site B.
The Remote Gateway setting in both sites has been configured as Static IP Address. For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
- A. 192.168.1.0/24
- B. 192.168.2.0/24
- C. 192.168.3.0/24
- D. 192.168.0.0/24
正解: B
質問 98
......
Fortinet NSE4_FGT-7.0 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
正真正銘のベスト資料NSE4_FGT-7.0オンライン練習試験:https://www.jpntest.com/shiken/NSE4_FGT-7.0-mondaishu
