あなたを合格させるCBSP試験問題集で使おう(更新された92問があります)
CBSP試験問題集でBlockchain練習テスト問題
Blockchain CBSP 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
質問 47
The List hack demonstrated that biockchains using short addresses are exploitable
- A. True
- B. False
正解: A
質問 48
In which blockchain consensus algorithm does a user pay (give up coin forever) to participate in consensus?
- A. Proof of Activity
- B. Proof of Work
- C. None of the above
- D. Proof of Stake
- E. Proof of Burn
正解: E
質問 49
Which of the following attacks only requires a single account and performs only normal blockchain operations?
- A. Eclipse Attack
- B. Replay Attack
- C. Routing Attack
- D. 51% Attack
正解: B
質問 50
A major advantage of a stale channel is that it provides a permanent means of transferring value between two parties
- A. True
- B. False
正解: A
質問 51
This sample code is vulnerable to which of the following attacks? Select all that apply.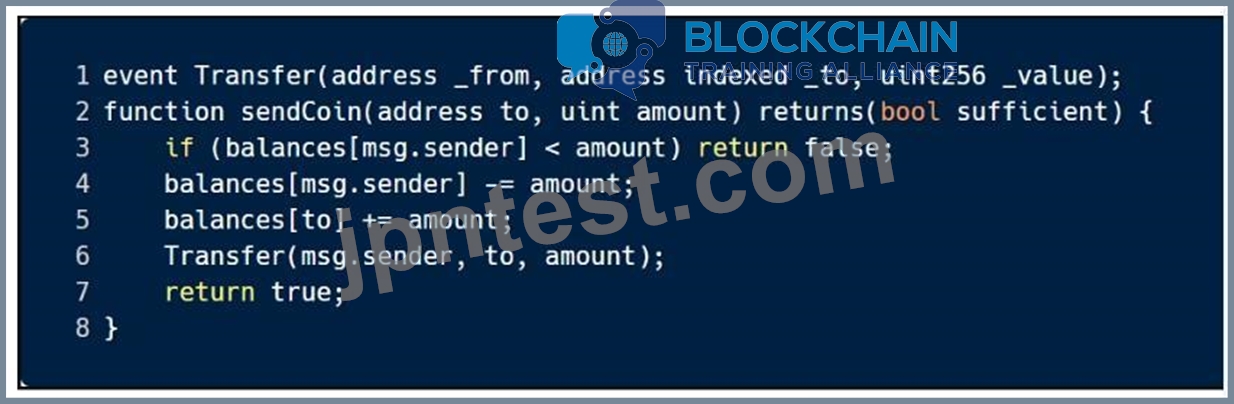
- A. Short Address
- B. Arithmetic
- C. Unchecked Return Values
- D. Reentrancy
正解: A
質問 52
In which of the following attacks targeting Proof of Stake does an attacker create a divergent chain and race to make their chain longer than the real chain?
- A. Long-Range Attack
- B. Double-Spend Attack
- C. 51% Attack
- D. Selfish Mining Attack
正解: A
質問 53
From a regulatory perspective, which of the following may be the most complicated issue around demonstrating proper data management?
- A. Lack of access controls
- B. Decentralized control of blockchain
- C. Use of distributed storage
- D. Lack of blockchain support for encryption
正解: C
質問 54
Which of the following is NOT a common regulatory requirement tor businesses?
- A. Personal data protection
- B. Data encryption
- C. Data control
- D. Data transparency
正解: D
質問 55
From a business perspective, which of me following is the major consideration regarding the use of smart contract technology?
- A. Public Accessibility
- B. Decentralization
- C. Hosting Requirements
- D. Code as Law" Arbitration
正解: D
質問 56
Which of the following does NOT rely on the security of public key cryptography?
- A. Ring Signature
- B. Zero-Knowledge Proof
- C. Confidential Transaction
- D. Stealth Address
正解: B
質問 57
For which of the following regulatory requirements is blockchain technology best suited?
- A. Data Retention
- B. Data Deletion
- C. Transparency
- D. Data Control
正解: C
質問 58
Poorly designed smart contracts can only be disabled on the blockchain if this functionality was built in from the beginning
- A. True
- B. False
正解: A
質問 59
All smart contracts are audited for correctness and checked for malicious code before being uploaded to the blockchain.
- A. False
- B. True
正解: A
質問 60
The decentralization of the blockchain makes it immune to traditional Denial of Service attacks
- A. False
- B. True
正解: A
質問 61
Spinning up a large number of temporary mining servers is likely part of what type of attack?
- A. Sybil
- B. Eclipse
- C. Routing
- D. Denial of Service
正解: A
質問 62
Checkpointing is designed to protect against an attacker exploiting the mechanism by which blockchain resolves divergent chains
- A. True
- B. False
正解: A
質問 63
Which of the following are necessary properties for a cryptographic hash function to be secure? Select all that apply
- A. Non-Locality
- B. Randomness
- C. Large State Space
- D. One-Way
正解: A,C,D
質問 64
Which of the following is NOT an essential part of Confidential Transactions?
- A. Ring Signature
- B. Pederson Commitment
- C. Zero-Knowledge Proof
- D. Elliptic Curve Cryptography
正解: C
質問 65
Using public keys tor identity management helps blockchain technology achieve which of the following?
- A. Decentralization
- B. Immutability
- C. Anonymity
- D. Trustlessness
正解: C
質問 66
Multisignatures are designed to allow a set of users to make a valid transaction only if a set minimum number of them consent
- A. True
- B. False
正解: A
質問 67
Stealth addresses are designed to do which of the following?
- A. Conceal transaction recipient
- B. Conceal transaction sender
- C. Conceal shared secret
- D. Conceal transaction amount
正解: A
質問 68
......
あなたをお手軽に合格させるCBSP試験正確なPDF問題:https://www.jpntest.com/shiken/CBSP-mondaishu
