お手軽に合格させる 最新CheckPoint 156-315.81問題集には616問があります
最新の156-315.81学習ガイド2024年最新の- 提供するのはテストエンジンとPDF
Check Point Certified Security Expert(CCSE)R81は、チェックポイントセキュリティソリューションの管理、構成、展開を担当するセキュリティ専門家のスキルと知識をテストするために設計された認定試験です。この試験は、チェックポイント認定セキュリティ管理者(CCSA)R81認定を既に完了し、サイバーセキュリティの分野でのキャリアを促進しようとしている個人を対象としています。
質問 # 206
Hit Count is a feature to track the number of connections that each rule matches, which one is not benefit of Hit Count.
- A. Analyze a Rule Base - You can delete rules that have no matching connections
- B. Improve Firewall performance - You can move a rule that has hot count to a higher position in the Rule Base
- C. Automatically rearrange Access Control Policy based on Hit Count Analysis
- D. Better understand the behavior of the Access Control Policy
正解:C
解説:
Explanation
Hit Count is a feature to track the number of connections that each rule matches, which can help to optimize the Rule Base efficiency and analyze the network traffic behavior. The benefit that is not provided by Hit Count is automatically rearrange Access Control Policy based on Hit Count Analysis. Hit Count does not change the order of the rules automatically, but it allows the administrator to manually move the rules up or down based on the hit count statistics. The administrator can also use the SmartOptimize feature to get suggestions for improving the Rule Base order and performance. References: R81 Security Management Administration Guide, page 97.
質問 # 207
What command is used to manually failover a Multi-Version Cluster during the upgrade?
- A. clusterXL_admin down in Clish
- B. set cluster member state down in Clish
- C. set cluster down in Expert Mode
- D. clusterXL_admin down in Expert Mode
正解:A
質問 # 208
What is the minimum amount of RAM needed for a Threat Prevention Appliance?
- A. 6 GB
- B. 8GB with Gaia in 64-bit mode
- C. It depends on the number of software blades enabled
- D. 4 GB
正解:D
解説:
Explanation
According to the Check Point Resource Library, the minimum amount of RAM needed for a Threat Prevention Appliance is 4 GB. This applies to both physical and virtual appliances. The other options are either incorrect or irrelevant. References: Check Point Resource Library
質問 # 209
On R81.10 the IPS Blade is managed by:
- A. Layers on Firewall policy
- B. Threat Protection policy
- C. Threat Prevention policy
- D. Anti-Bot Blade
正解:C
質問 # 210
Due to high CPU workload on the Security Gateway, the security administrator decided to purchase a new multicore CPU to replace the existing single core CPU. After installation, is the administrator required to perform any additional tasks?
- A. After upgrading the hardware, increase the number of kernel instances using cpconfig
- B. Administrator does not need to perform any task. Check Point will make use of the newly installed CPU and Cores
- C. Hyperthreading must be enabled in the bios to use CoreXL
- D. Run cprestart from clish
正解:A
質問 # 211
What ports are used for SmartConsole to connect to the Security Management Server?
- A. CPMI (18190)
- B. CPM (19009), CPMI (18190) CPD (18191)
- C. CPM (19009), CPMI (18190) https (443)
- D. ICA_Pull (18210), CPMI (18190) https (443)
正解:C
解説:
Explanation
The correct answer is C. CPM (19009), CPMI (18190) https (443).
SmartConsole is a client application that connects to the Security Management Server to manage and configure the security policy and objects. SmartConsole uses three ports to communicate with the Security Management Server1:
CPM (19009): This port is used for the communication between the SmartConsole client and the Check Point Management (CPM) process on the Security Management Server. The CPM process handles the database operations and the policy installation.
CPMI (18190): This port is used for the communication between the SmartConsole client and the Check Point Management Interface (CPMI) process on the Security Management Server. The CPMI process handles the authentication and encryption of the SmartConsole sessions.
https (443): This port is used for the communication between the SmartConsole client and the web server on the Security Management Server. The web server provides the SmartConsole GUI and the SmartConsole extensions.
The other options are incorrect because they either include ports that are not used by SmartConsole or omit ports that are used by SmartConsole.
References:
SmartConsole R81.20 - Check Point Software1
質問 # 212
Native Applications require a thin client under which circumstances?
- A. If you want to use a VPN Client that is not officially supported by the underlying operating system
- B. If you want to have assigned a particular Office Mode IP address.
- C. If you want to use a legacy 32-Bit Windows OS
- D. If you are about to use a client (FTP. RDP, ...) that is installed on the endpoint.
正解:D
解説:
Explanation
Native Applications require a thin client under the circumstance that you are about to use a client (FTP, RDP, etc.) that is installed on the endpoint. A thin client is a lightweight software component that enables secure connectivity for native applications without requiring additional configuration or user intervention. A thin client is automatically downloaded and installed on the endpoint when a user initiates a native application session through Mobile Access Portal or SNX Portal. References: [Check Point Security Expert R81 Mobile Access Administration Guide], page 16.
質問 # 213
What are the correct steps upgrading a HA cluster (M1 is active, M2 is passive) using Multi-Version Cluster(MVC)Upgrade?
- A. 1) Enable the MVC mechanism on both cluster members #cphaprob mvc on
2) Upgrade the passive node M2 to R81.10
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism - B. 1) Enable the MVC mechanism on both cluster members #cphaprob mvc on
2) Upgrade the passive node M2 to R81.10
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy - C. 1) Upgrade the passive node M2 to R81.10
2) Enable the MVC mechanism on the upgraded R81.10 Cluster Member M2 #cphaconf mvc on
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy upgrade the passive node M2 to R81.10 - D. 1) In SmartConsole, change the version of the cluster object
2) Upgrade the passive node M2 to R81.10
3) Enable the MVC mechanism on the upgraded R81.10 Cluster Member M2 #cphaconf mvc on
4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy SmartConsole, change the version of the cluster object
正解:D
解説:
Explanation
The correct steps upgrading a HA cluster (M1 is active, M2 is passive) using Multi-Version Cluster (MVC) Upgrade are:
In SmartConsole, change the version of the cluster object to R81.10.
Upgrade the passive node M2 to R81.10 using CPUSE or CLI.
Enable the MVC mechanism on the upgraded R81.10 Cluster Member M2 using the command cphaconf mvc on.
Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails by selecting in the Policy Installation Settings dialog box.
After examining the cluster states using cphaprob stat and verifying that both members are synchronized, upgrade node M1 to R81.10 using CPUSE or CLI.
On each Cluster Member, disable the MVC mechanism using the command cphaconf mvc off and Install the Access Control Policy3.
References: Check Point R81 Installation and Upgrade Guide
質問 # 214
You want to gather data and analyze threats to your mobile device. It has to be a lightweight app. Which application would you use?
- A. Check Point Capsule Cloud
- B. Sandblast Mobile Protect
- C. SmartEvent Client Info
- D. SecuRemote
正解:B
解説:
Explanation
SandBlast Mobile Protect is a lightweight app for iOS and Android that gathers data and helps analyze threats to devices in your environment.
https://www.checkpoint.com/downloads/products/how-sandblast-mobile-works-solution-brief.pdf
質問 # 215
What is true about the IPS-Blade?
- A. In R81, IPS is managed by the Threat Prevention Policy
- B. In R81, IPS Exceptions cannot be attached to "all rules"
- C. In R81, in the IPS Layer, the only three possible actions are Basic, Optimized and Strict
- D. In R81, the GeoPolicy Exceptions and the Threat Prevention Exceptions are the same
正解:A
質問 # 216
What is the best method to upgrade a Security Management Server to R81.x when it is not connected to the Internet?
- A. CPUSE offline upgrade only
- B. Advanced upgrade or CPUSE offline upgrade
- C. Advanced Upgrade only
- D. SmartUpdate offline upgrade
正解:B
解説:
Explanation
The best method to upgrade a Security Management Server to R81.x when it is not connected to the Internet is either Advanced upgrade or CPUSE offline upgrade. Advanced upgrade is a manual procedure that involves backing up the current configuration, installing the new version from an ISO image, and restoring the configuration. CPUSE offline upgrade is an automated procedure that involves downloading the upgrade package from the Check Point User Center, transferring it to the Security Management Server, and installing it using CPUSE. SmartUpdate offline upgrade is not a valid option, as SmartUpdate is a tool for managing licenses and software packages on multiple gateways and servers1. References: 1: Check Point Software, Getting Started, Upgrading Security Management Servers.
質問 # 217
With Mobile Access enabled, administrators select the web-based and native applications that can be accessed by remote users and define the actions that users can perform the applications. Mobile Access encrypts all traffic using:
- A. HTTPS for web-based applications and AES or RSA algorithm for native applications. For end users to access the native application, they need to install the SSL Network Extender.
- B. HTTPS for web-based applications and 3DES or RC4 algorithm for native applications. For end users to access the native applications, they need to install the SSL Network Extender.
- C. HTTPS for web-based applications and 3DES or RC4 algorithm for native applications. For end users to access the native applications, no additional software is required.
- D. HTTPS for web-based applications and AES or RSA algorithm for native applications. For end users to access the native application, no additional software is required.
正解:B
質問 # 218
If there are two administration logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available or other administrators? (Choose the BEST answer.)
- A. Revert the session.
- B. Publish or discard the session.
- C. Save and install the Policy.
- D. Delete older versions of database.
正解:B
解説:
Explanation
The only way to make objects locked for editing available for other administrators is to publish or discard the session that contains the changes. Publishing the session will save and share the changes with other administrators, while discarding the session will undo and discard the changes. Saving the session will only save the changes locally, but not share them with others or release the locks. Reverting the session will restore a previous version of the session, but not affect the locks. Saving and installing the policy will only install the policy on the gateways, but not share or discard the changes in SmartConsole. Deleting older versions of database will only free up disk space, but not affect the locks.
質問 # 219
You notice that your firewall is under a DDoS attack and would like to enable the Penalty Box feature, which command you use?
- A. sim erdos -x 1
- B. sim erdos - m 1
- C. sim erdos -v 1
- D. sim erdos -e 1
正解:D
解説:
Explanation
The command that would be used to enable the Penalty Box feature is sim erdos -e 1. Penalty Box is a feature that protects the Security Gateway from DDoS attacks by dropping packets from sources that send excessive traffic. Sim erdos is a command that allows administrators to configure and manage the Penalty Box feature.
Sim erdos -e 1 enables the Penalty Box feature on the Security Gateway. The other options are either invalid or perform different functions.
質問 # 220
Vanessa is firewall administrator in her company. Her company is using Check Point firewall on a central and several remote locations which are managed centrally by R77.30 Security Management Server. On central location is installed R77.30 Gateway on Open server. Remote locations are using Check Point UTM-1570 series appliances with R75.30 and some of them are using a UTM-1-Edge-X or Edge-W with latest available firmware. She is in process of migrating to R81.
What can cause Vanessa unnecessary problems, if she didn't check all requirements for migration to R81?
- A. Unsupported appliances on remote locations
- B. Unsupported version on UTM-1 570 series appliance
- C. Missing an installed R77.20 Add-on on Security Management Server
- D. Unsupported firmware on UTM-1 Edge-W appliance
正解:C
解説:
Explanation
What can cause Vanessa unnecessary problems, if she didn't check all requirements for migration to R81, is missing an installed R77.20 Add-on on Security Management Server. R77.20 Add-on is a package that adds new features and enhancements to R77 Security Management Server, such as support for new appliances, Gaia OS features, VPN features, etc. One of the requirements for migrating to R81 from R77 Security Management Server is to have R77.20 Add-on installed on the server. If Vanessa did not check this requirement and tried to migrate without R77.20 Add-on, she would encounter errors and failures during the migration process. The other options are either not relevant or not problematic for migration to R81.
質問 # 221
What are possible Automatic Reactions in SmartEvent?
- A. Web Mail, Forward to SandBlast Appliance, SNMP Trap, External Script
- B. Web Mail. Block Destination, SNMP Trap. SmartTask
- C. Mail. SNMP Trap, Block Source. Block Event Activity, External Script
- D. Web Mail, Block Service. SNMP Trap. SmartTask, Geo Protection
正解:D
質問 # 222
Which pre-defined Permission Profile should be assigned to an administrator that requires full access to audit all configurations without modifying them?
- A. Read Only All
- B. Auditor
- C. Full Access
- D. Super User
正解:A
質問 # 223
SandBlast Mobile identifies threats in mobile devices by using on-device, network, and cloud-based algorithms and has four dedicated components that constantly work together to protect mobile devices and their data. Which component is NOT part of the SandBlast Mobile solution?
- A. Management Dashboard
- B. Gateway
- C. Behavior Risk Engine
- D. Personal User Storage
正解:D
解説:
Explanation
SandBlast Mobile has four components: Management Dashboard, Gateway, Behavior Risk Engine, and On-Device Network Protection. Personal User Storage is not part of the SandBlast Mobile solution.
References: SandBlast Mobile Architecture
質問 # 224
In the Check Point Firewall Kernel Module, each Kernel is associated with a key, which specifies the type of traffic applicable to the chain module. For Wire Mode configuration, chain modules marked with
____________ will not apply.
- A. 0
- B. 1
- C. ffff
- D. 2
正解:D
解説:
Explanation
In the Check Point Firewall Kernel Module, each kernel is associated with a key, which specifies the type of traffic applicable to the chain module. For Wire Mode configuration, chain modules marked with 1 will not apply, as they are related to NAT, VPN, or other features that are not supported in Wire Mode. Wire Mode is a mode of operation that allows transparent traffic forwarding without any inspection or modification by the firewall. References: Check Point Security Expert R81 Course, Wire Mode Configuration Guide
質問 # 225
Which of the following will NOT affect acceleration?
- A. Multicast packets
- B. Connections destined to or originated from the Security gateway
- C. A 5-tuple match
- D. Connections that have a Handler (ICMP, FTP, H.323, etc.)
正解:C
解説:
Explanation
Check Point's SecureXL technology, which is responsible for acceleration, has certain limitations and conditions under which acceleration may not occur. In this context, the question is asking about factors that will NOT affect acceleration.
Option B, "A 5-tuple match," will not affect acceleration. A 5-tuple match refers to the matching of source IP, source port, destination IP, destination port, and protocol. SecureXL can accelerate traffic that matches these criteria, but it's not a factor that hinders acceleration.
Options A, C, and D can all affect acceleration:
Option A mentions "Connections destined to or originated from the Security gateway," which implies that SecureXL acceleration can apply to these connections.
Option C mentions "Multicast packets," and SecureXL may have limitations in handling multicast traffic efficiently.
Option D mentions "Connections that have a Handler (ICMP, FTP, H.323, etc.)," and certain protocols (such as FTP) may require special handling and might not be fully accelerated by SecureXL.
References: Check Point Certified Security Expert R81 Study Guide
質問 # 226
What is the command to see cluster status in cli expert mode?
- A. fw ctl stat
- B. clusterXL stat
- C. cphaprob stat
- D. clusterXL status
正解:C
質問 # 227
What does it mean if Deyra sees the gateway status? (Choose the BEST answer.)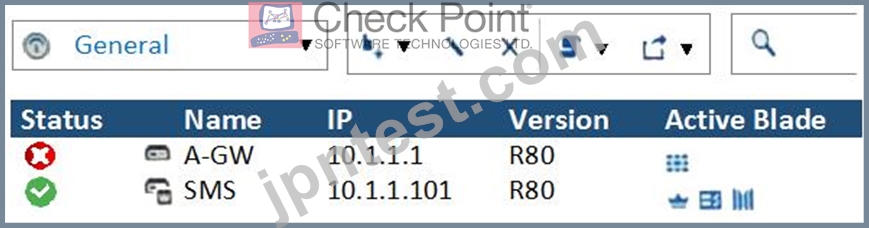
- A. Security Gateway's MGNT NIC card is disconnected.
- B. There is a blade reporting a problem.
- C. SmartCenter Server cannot reach this Security Gateway.
- D. VPN software blade is reporting a malfunction.
正解:B
質問 # 228
......
チェックポイント認定セキュリティの専門家R81は、セキュリティの専門家にとって最も人気のある認定の1つです。この認定は、高度なセキュリティソリューションの管理、トラブルシューティング、チェックポイントセキュリティアーキテクチャの最適化に必要な専門知識を検証します。チェックポイント156-315.81試験は、チェックポイントセキュリティシステムを構成、管理、およびトラブルシューティングする候補者の知識とスキルを評価するように設計されています。
チェックポイント認定セキュリティの専門家R81試験に合格することは、サイバーセキュリティ業界で大きな成果です。候補者はチェックポイントのセキュリティソリューションを深く理解しており、効果的に実装するスキルと知識を持っていることを示しています。この認定は業界で非常に尊敬されており、世界的に認識されています。
156-315.81問題集と試験テストエンジン:https://www.jpntest.com/shiken/156-315.81-mondaishu
