156-315.81練習試験テスト最新問題2023年11月
156-315.81試験を一発合格保証問題集!
質問 # 116
Your manager asked you to check the status of SecureXL, and its enabled templates and features. What command will you use to provide such information to manager?
- A. fwaccel stat
- B. fwaccel stats
- C. fw acces stats
- D. fw accel stat
正解:A
解説:
Explanation
References:
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_PerformanceTuning_AdminGuide/T
質問 # 117
Which one of the following is true about Threat Emulation?
- A. Works on MS Office and PDF files only
- B. Takes less than a second to complete
- C. Always delivers a file
- D. Takes minutes to complete (less than 3 minutes)
正解:D
解説:
Explanation
Threat Emulation is a software blade that takes minutes to complete (less than 3 minutes). Threat Emulation analyzes files for malicious behavior by running them in a virtual sandbox. Threat Emulation works on MS Office, PDF, executables, and archive files. Threat Emulation does not always deliver a file, but only if no threats are found or if the user chooses to download the original file after seeing a warning message.
References: Check Point Security Expert R81 Course, Threat Emulation Administration Guide
質問 # 118
Which of the following statements about SecureXL NAT Templates is true?
- A. NAT Templates are generated to achieve high session rate for NAT. These templates store the NAT attributes of connections matched by rulebase so that similar new connections can take advantage of this information and do NAT without the expensive rulebase lookup. These are enabled by default and work only if Accept Templates are enabled.
- B. DROP Templates are generated to achieve high session rate for NAT. These templates store the NAT attributes of connections matched by rulebase so that similar new connections can take advantage of this information and do NAT without the expensive rulebase lookup. These are disabled by default and work only if NAT Templates are disabled.
- C. ACCEPT Templates are generated to achieve high session rate for NAT. These templates store the NAT attributes of connections matched by rulebase so that similar new connections can take advantage of this information and do NAT without the expensive rulebase lookup. These are disabled by default and work only if NAT Templates are disabled.
- D. NAT Templates are generated to achieve high session rate for NAT. These templates store the NAT attributes of connections matched by rulebase so that similar new connections can take advantage of this information and do NAT without the expensive rulebase lookup. These are disabled by default and work only if Accept Templates are disabled.
正解:A
質問 # 119
In what way is Secure Network Distributor (SND) a relevant feature of the Security Gateway?
- A. SND is a feature to accelerate multiple SSL VPN connections
- B. SND is an alternative to IPSec Main Mode, using only 3 packets
- C. SND is a feature of fw monitor to capture accelerated packets
- D. SND is used to distribute packets among Firewall instances
正解:D
解説:
Explanation
Secure Network Distributor (SND) is a relevant feature of the Security Gateway because it is used to distribute packets among Firewall instances. SND is a technology that improves the performance and scalability of the Security Gateway by using multiple cores to handle concurrent connections. SND consists of two components:
SND driver and Firewall instances. SND driver is responsible for receiving packets from network interfaces and distributing them to Firewall instances based on a load balancing algorithm. Firewall instances are responsible for inspecting packets according to security policies and forwarding them to their destinations. The other options are either incorrect or not related to SND.
質問 # 120
Which CLI command will reset the IPS pattern matcher statistics?
- A. ips pmstats refresh
- B. ips reset pmstat
- C. ips pmstats reset
- D. ips pstats reset
正解:C
解説:
Explanation
The CLI command to reset the IPS (Intrusion Prevention System) pattern matcher statistics is option D: ips pmstats reset. This command will reset the statistics related to the IPS pattern matcher.
Options A, B, and C are not the correct syntax for resetting the IPS pattern matcher statistics.
References: Check Point Certified Security Expert (CCSE) R81 documentation and learning resources.
質問 # 121
SecureXL is able to accelerate the Connection Rate using templates. Which attnbutes are used in the template to identify the connection?
- A. Source address . Destination address. Destination port
- B. Source address . Destination address. Source Port, Destination port
- C. Source address . Destination address. Source Port, Destination port. Protocol
- D. Source address . Destination address. Destination port. Pro^col
正解:C
質問 # 122
Which command shows detailed information about VPN tunnels?
- A. vpn tu
- B. cpview
- C. vpn tu tlist
- D. cat $FWDIR/conf/vpn.conf
正解:C
解説:
Explanation
The command vpn tu tlist shows detailed information about VPN tunnels, such as the peer IP address, encryption domain, IKE phase 1 and phase 2 status, encryption algorithm, and tunnel uptime. The command vpn tu is an interactive tool that allows users to list, delete, or reconnect VPN tunnels. The command cpview is a real-time performance monitoring tool that shows various statistics about the system and network.
References: VPN Administration Guide, SK97638 - What is cpview Utility and How to Use it
質問 # 123
What are the two high availability modes?
- A. Active and Standby
- B. New and Legacy
- C. Traditional and New
- D. Load Sharing and Legacy
正解:B
解説:
Explanation
ClusterXL has four working modes. This section briefly describes each mode and its relative advantages and disadvantages.
質問 # 124
What should the admin do in case the Primary Management Server is temporary down?
- A. Logon with SmartConsole to the Secondary Management Server and choose "Make Active' under Actions in the HA Management Menu
- B. The Secondary will take over automatically Change the IP in SmartConsole to logon to the private IP of the Secondary Management Server.
- C. Use the VIP in SmartConsole you always reach the active Management Server.
- D. Run the 'promote_util' to activate the Secondary Management server
正解:C
解説:
Explanation
High Availability (HA) is a deployment scenario where two or more Security Management Servers are configured to work together as a cluster. One server acts as the Primary server and handles all management operations, while another server acts as the Secondary server and serves as a backup. If the Primary server fails, the Secondary server takes over and becomes active. The cluster members communicate using a Virtual IP (VIP) address, which is used by SmartConsole to connect to the active server. If the Primary server is temporarily down, the administrator does not need to do anything, as SmartConsole will automatically connect to the VIP address and reach the Secondary server that has become active. Therefore, the correct answer is A.
References: 6: High Availability Administration Guide
質問 # 125
On the following picture an administrator configures Identity Awareness: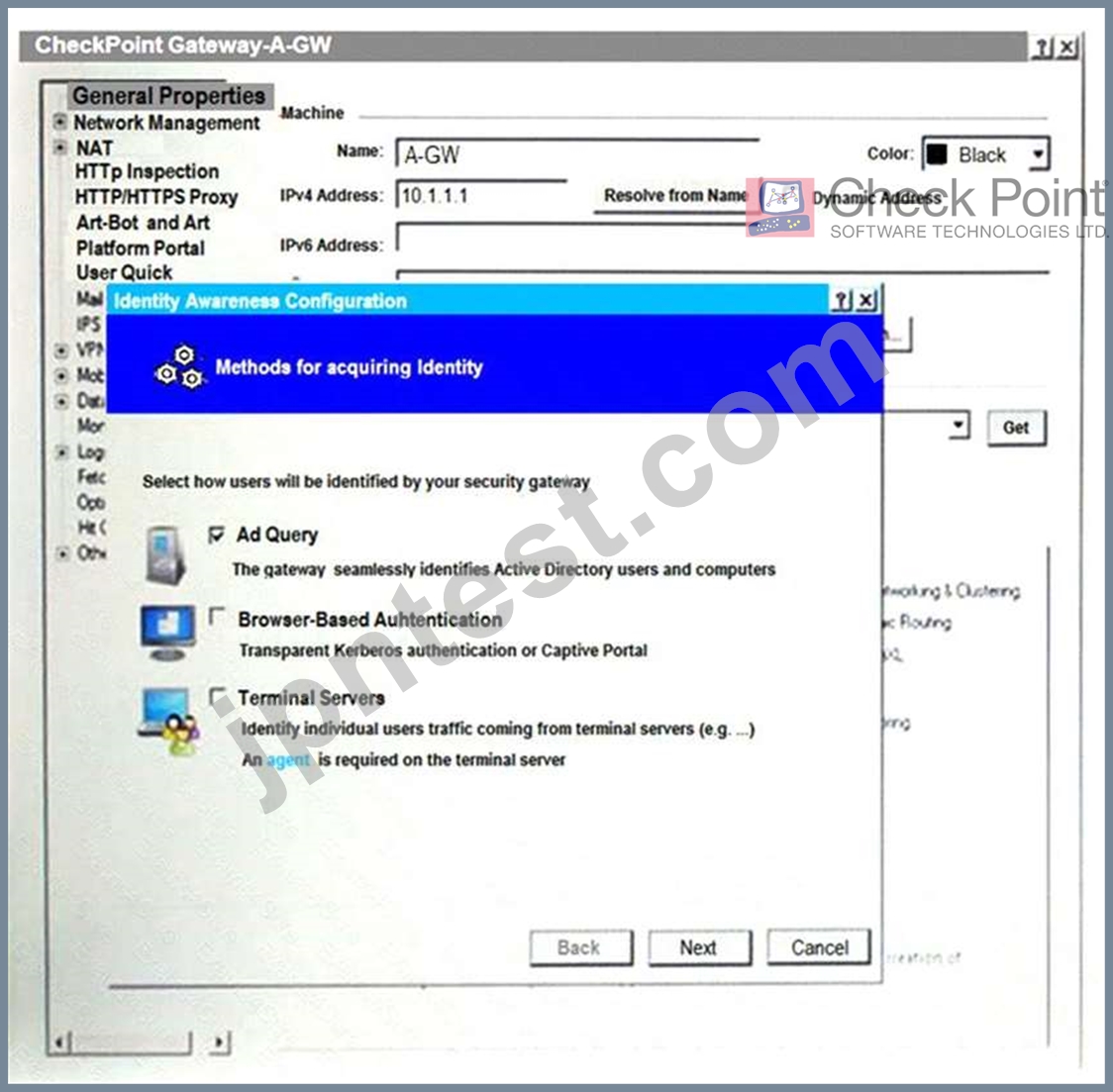
After clicking "Next" the above configuration is supported by:
- A. Kerberos SSO which will be working for Active Directory integration
- B. Obligatory usage of Captive Portal.
- C. Based on Active Directory integration which allows the Security Gateway to correlate Active Directory users and machines to IP addresses in a method that is completely transparent to the user.
- D. The ports 443 or 80 what will be used by Browser-Based and configured Authentication.
正解:C
解説:
Explanation
After clicking "Next", the above configuration is supported by Active Directory integration which allows the Security Gateway to correlate Active Directory users and machines to IP addresses in a method that is completely transparent to the user. This is a feature of Identity Awareness that allows the Security Gateway to identify users and machines on the network and enforce security policies based on their identity. The administrator can configure Identity Awareness to use various methods for acquiring identity, including Active Directory integration, browser-based authentication, terminal servers, and transparent authentication1.
References: Check Point Resource Library, page 3.
質問 # 126
Fill in the blank: The R81 SmartConsole, SmartEvent GUI client, and _______ consolidate billions of logs and shows then as prioritized security events.
- A. SmartView Web Application
- B. SmartMonitor
- C. SmartTracker
- D. SmartReporter
正解:A
質問 # 127
Which of the following process pulls application monitoring status?
- A. cpwd
- B. cpd
- C. fwm
- D. fwd
正解:B
解説:
Explanation
The process that pulls application monitoring status is cpd. cpd is a daemon that runs on Check Point products and performs various tasks related to management communication, policy installation, license verification, logging, etc. cpd also monitors the status of other processes and applications on the system and reports it to the management server. cpd uses SNMP to collect information from various sources, such as blades, gateways, servers, etc. You can view the application monitoring status in SmartConsole by using the Gateways & Servers tab in the Logs & Monitor view. References: Check Point Processes and Daemons
質問 # 128
What are the correct steps upgrading a HA cluster (M1 is active, M2 is passive) using Multi-Version Cluster(MVC)Upgrade?
- A. 1) In SmartConsole, change the version of the cluster object
2) Upgrade the passive node M2 to R81.10
3) Enable the MVC mechanism on the upgraded R81.10 Cluster Member M2 #cphaconf mvc on
4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy SmartConsole, change the version of the cluster object - B. 1) Enable the MVC mechanism on both cluster members #cphaprob mvc on
2) Upgrade the passive node M2 to R81.10
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy - C. 1) Enable the MVC mechanism on both cluster members #cphaprob mvc on
2) Upgrade the passive node M2 to R81.10
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy and make sure that the installation will not stop if installation on one cluster member fails
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism - D. 1) Upgrade the passive node M2 to R81.10
2) Enable the MVC mechanism on the upgraded R81.10 Cluster Member M2 #cphaconf mvc on
3) In SmartConsole, change the version of the cluster object
4) Install the Access Control Policy
5) After examine the cluster states upgrade node M1 to R81.10
6) On each Cluster Member, disable the MVC mechanism and Install the Access Control Policy upgrade the passive node M2 to R81.10
正解:A
解説:
Explanation
https://sc1.checkpoint.com/documents/R81/WebAdminGuides/EN/CP_R81_Installation_and_Upgrade_Guide/T
質問 # 129
Which components allow you to reset a VPN tunnel?
- A. vpn tunnelutil or delete vpn ike sa command
- B. delete vpn ike sa or vpn she11 command
- C. vpn tu command or SmartView monitor
- D. SmartView monitor only
正解:C
解説:
Explanation
The vpn tu command and the SmartView Monitor are two components that allow you to reset a VPN tunnel.
The vpn tu command is a command-line tool that lets you view and manage the status of VPN tunnels on a Security Gateway or cluster member. The SmartView Monitor is a graphical tool that lets you monitor the network and security performance, view VPN tunnel status, and reset VPN tunnels. Both components can be used to reset a VPN tunnel by selecting the option to delete IKE SA or IPsec SA for a specific peer or all peers. References: R81 VPN Administration Guide, page 29-30; R81 SmartConsole R81 Resolved Issues, sk170114
質問 # 130
With MTA (Mail Transfer Agent) enabled the gateways manages SMTP traffic and holds external email with potentially malicious attachments. What is required in order to enable MTA (Mail Transfer Agent) functionality in the Security Gateway?
- A. Threat Cloud Intelligence
- B. Traffic on port 25
- C. Endpoint Total Protection
- D. Threat Prevention Software Blade Package
正解:D
質問 # 131
You pushed a policy to your gateway and you cannot access the gateway remotely any more. What command should you use to remove the policy from the gateway by logging in through console access?
- A. "fw unloadlocal"
- B. "fwundo"
- C. "fw cpstop"
- D. "fw unloadpolicy''
正解:D
質問 # 132
......
Check Point Certified Security Expert無料認定試験材料はJPNTestが提供された582問題:https://www.jpntest.com/shiken/156-315.81-mondaishu
