別格で売上ナンバーワン156-215.80試験にはは2022年最新のCheckPoint練習問試験合格させます
CCSA R80問題集で156-215.80試験完全版問題で試験学習ガイド
CheckPoint 156-215.80 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
| トピック 9 |
|
質問 13
Which of the following is NOT a valid application navigation tab in the R80 SmartConsole?
- A. Security Policies
- B. Gateway and Servers
- C. Manage and Command Line
- D. Logs and Monitor
正解: C
解説:
Explanation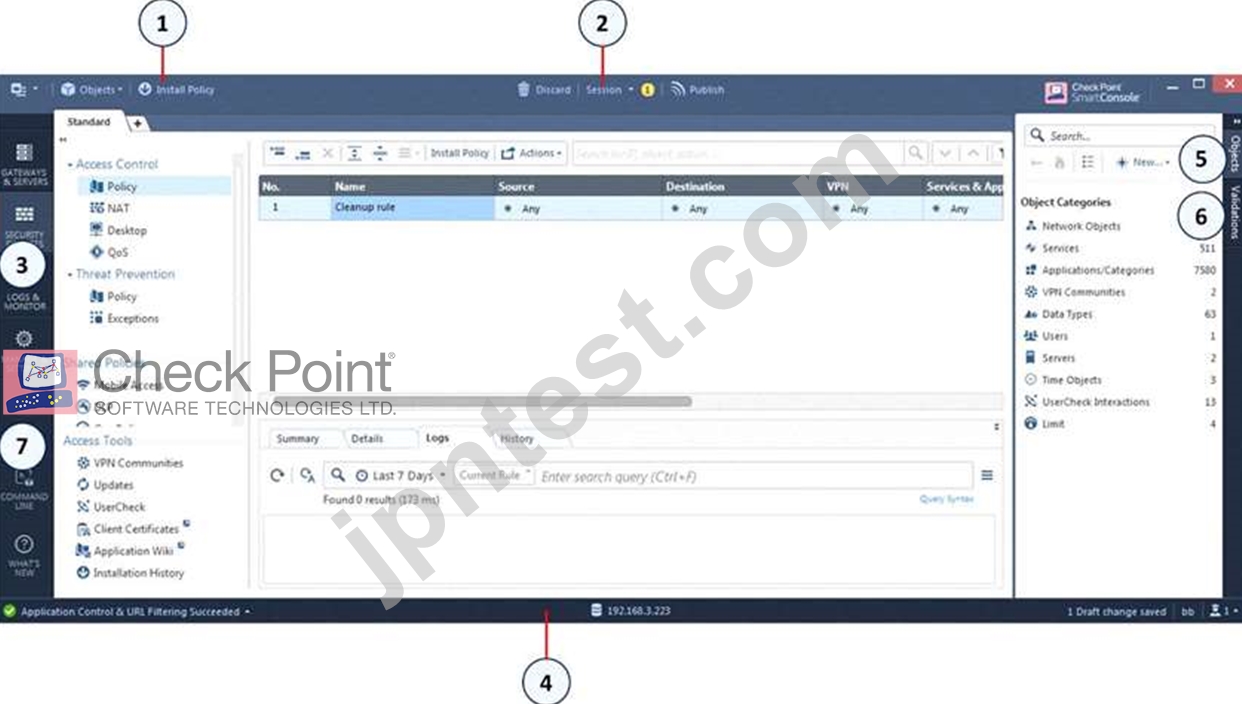
質問 14
Which utility allows you to configure the DHCP service on GAIA from the command line?
- A. ifconfig
- B. dhcp_cfg
- C. sysconfig
- D. cpconfig
正解: C
解説:
Sysconfig Configuration Options
Menu Item
Purpose
7
DHCP Server Configuration
Configure SecurePlatform DHCP Server.
8
DHCP Relay Configuration
Setup DHCP Relay.
Refrence:https://sc1.checkpoint.com/documents/R76/CP_R76_Splat_AdminGuide/51548.h tm
NOTE:Question must be wrong because no answer is possible for GAIA system, this must be SPLAT version.
DHCP CLI configuration for GAIA
reference:https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/73181.ht m#o80096
質問 15
Which of these statements describes the Check Point ThreatCloud?
- A. Blocks or limits usage of web applications
- B. Prevents Cloud vulnerability exploits
- C. A worldwide collaborative security network
- D. Prevents or controls access to web sites based on category
正解: C
解説:
Explanation
References:
質問 16
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.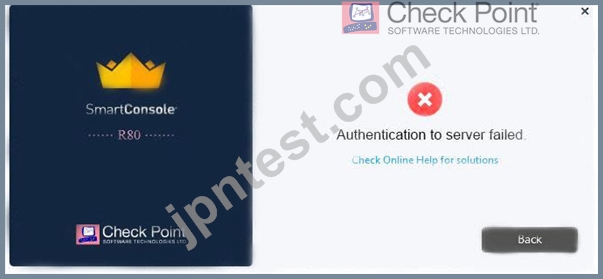
What is the most likely reason?
- A. Check Point R80 SmartConsole authentication is more secure than in previous versions and Vanessa requires a special authentication key for R80 SmartConsole. Check that the correct key details are used.
- B. Check Point Management software authentication details are not automatically the same as the Operating System authentication details. Check that she is using the correct details.
- C. Authentication failed because Vanessa's username is not allowed in the new Threat Prevention console update checks even though these checks passed with Gaia.
- D. SmartConsole Authentication is not allowed for Vanessa until a Super administrator has logged in first and cleared any other administrator sessions.
正解: B
質問 17
You are using SmartView Tracker to troubleshoot NAT entries. Which column do you check to view the NAT'd source port if you are using Source NAT?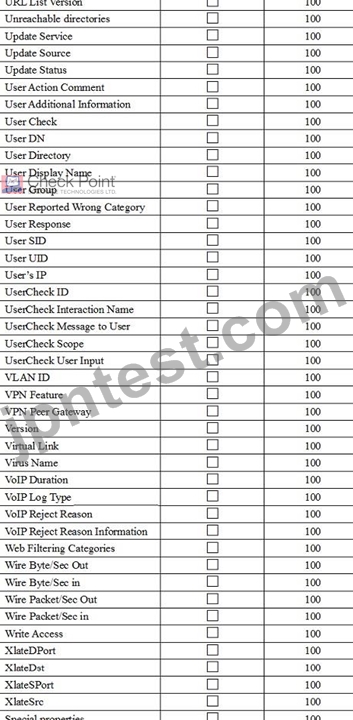
- A. XlateSrc
- B. XlateSPort
- C. XlateDPort
- D. XlateDst
正解: B
質問 18
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations.
Select accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
- A. Have the security administrator reboot the firewall.
- B. Have the security administrator select Any for the Machines tab in the appropriate Access Role.
- C. Install the Identity Awareness agent on her iPad.
- D. Have the security administrator select the Action field of the Firewall Rule "Redirect HTTP connections to an authentication (captive) portal".
正解: D
質問 19
As you review this Security Policy, what changes could you make to accommodate Rule 4?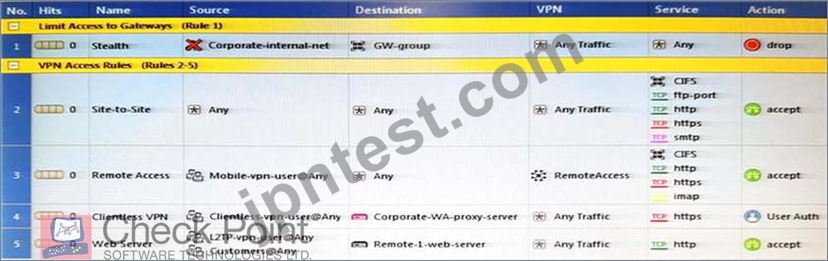
- A. Modify the column VPN in Rule 2 to limit access to specific traffic.
- B. Modify the columns Source or Destination in Rule 4
- C. Nothing at all
- D. Remove the service HTTP from the column Service in Rule 4.
正解: A
質問 20
In Unified SmartConsole Gateways and Servers tab you can perform the following functions EXCEPT
- A. Open SSH
- B. Open WebUI
- C. Open service request with Check Point Technical Support
- D. Upgrade the software version
正解: A
質問 21
What port is used for communication to the User Center with SmartUpdate?
- A. TCP 8080
- B. CPMI 200
- C. HTTPS 443
- D. HTTP 80
正解: C
質問 22
Which of the following is the most secure means of authentication?
- A. Pre-shared secret
- B. Password
- C. Certificate
- D. Token
正解: C
質問 23
All R77 Security Servers can perform authentication with the exception of one. Which of the Security Servers
can NOT perform authentication?
- A. HTTP
- B. SMTP
- C. RLOGIN
- D. FTP
正解: B
質問 24
Which of the following technologies extracts detailed information from packets and stores that information in state tables?
- A. Packet Filtering
- B. Application Layer Firewall
- C. Stateful Inspection
- D. INSPECT Engine
正解: C
解説:
Explanation/Reference:
Reference: https://www.checkpoint.com/smb/help/utm1/8.2/7080.htm
質問 25
Fill in the blank: To build an effective Security Policy, use a ________ and _______ rule.
- A. Cleanup; default
- B. Implicit; explicit
- C. Stealth; implicit
- D. Cleanup; stealth
正解: D
質問 26
ALPHA Corp has a new administrator who logs into the Gaia Portal to make some changes. He realizes that
even though he has logged in as an administrator, he is unable to make any changes because all configuration
options are greyed out as shown in the screenshot image below. What is the likely cause for this?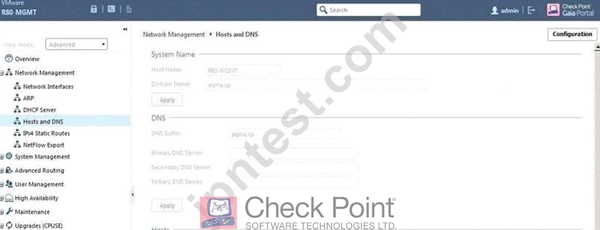
- A. The IP address of his computer is not in the allowed hosts.
- B. The Gaia /bin/confd is locked by another administrator from a SmartConsole session.
- C. The database is locked by another administrator SSH session.
- D. The Network address of his computer is in the blocked hosts.
正解: C
解説:
Explanation
There is a lock on top left side of the screen. B is the logical answer.
質問 27
What port is used for delivering logs from the gateway to the management server?
- A. Port 257
- B. Port 981
- C. Port 18209
- D. Port 258
正解: A
質問 28
The "Hit count" feature allows tracking the number of connections that each rule matches. Will the Hit count
feature work independently from logging and Track the hits even if the Track option is set to "None"?
- A. No, it will not work independently. Hit Count will be shown only for rules with Track options set as Log
or alert - B. Yes, it will work independently as long as "analyze all rules" tick box is enabled on the Security
Gateway - C. No, it will not work independently because hit count requires all rules to be logged
- D. Yes, it will work independently because when you enable Hit Count, the SMS collects the data from
supported Security Gateways
正解: D
質問 29
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to
access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she
cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal
and then get the same access as on her office computer. Her access to resources is based on rules in the R77
Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is
selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select
accept as the Action.
4) Install policy.
Ms McHanry tries to access the resource but is unable. What should she do?
- A. Have the security administrator reboot the firewall.
- B. Have the security administrator select Any for the Machines tab in the appropriate Access Role.
- C. Install the Identity Awareness agent on her iPad.
- D. Have the security administrator select the Action field of the Firewall Rule "Redirect HTTP connections
to an authentication (captive) portal".
正解: D
質問 30
What are the two types of address translation rules?
- A. Manipulated packet and original packet
- B. Original packet and translated packet
- C. Untranslated packet and manipulated packet
- D. Translated packet and untranslated packet
正解: B
解説:
Explanation
NAT Rule Base
The NAT Rule Base has two sections that specify how the IP addresses are translated:
質問 31
Fill in the blank: RADIUS protocol uses ______ to communicate with the gateway.
- A. UDP
- B. HTTP
- C. CCP
- D. TDP
正解: A
解説:
Explanation/Reference:
Explanation: Parameters: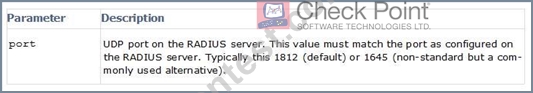
Reference: https://sc1.checkpoint.com/documents/R76SP/
CP_R76SP_Security_System_WebAdminGuide/105209.htm
質問 32
Which two Identity Awareness commands are used to support identity sharing?
- A. Policy Decision Point (PDP) and Policy Enforcement Point (PEP)
- B. Policy Manipulation Point (PMP) and Policy Activation Point (PAP)
- C. Policy Enforcement Point (PEP) and Policy Manipulation Point (PMP)
- D. Policy Activation Point (PAP) and Policy Decision Point (PDP)
正解: A
解説:
Explanation/Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/66477.htm
質問 33
While enabling the Identity Awareness blade the Identity Awareness wizard does not automatically detect the
windows domain. Why does it not detect the windows domain?
- A. SMS is not part of the domain
- B. SmartConsole machine is not part of the domain
- C. Identity Awareness is not enabled on Global properties
- D. Security Gateways is not part of the Domain
正解: B
解説:
Explanation
To enable Identity Awareness:
The Identity Awareness Configuration wizard opens.
See Choosing Identity Sources.
Note - When you enable Browser-Based Authentication on a Security Gateway that is on an IP Series
appliance, make sure to set the Voyager management application port to a port other than 443 or 80.
The Integration With Active Directory window opens.
When SmartDashboard is part of the domain, SmartDashboard suggests this domain automatically. If you
select this domain, the system creates an LDAP Account Unit with all of the domain controllers in the
organization's Active Directory.
質問 34
Which firewall daemon is responsible for the FW CLI commands?
- A. cpd
- B. fwd
- C. fwm
- D. cpm
正解: B
解説:
Explanation/Reference:
質問 35
ABC Corp., and have recently returned from a training course on Check Point's new advanced R80
management platform. You are presenting an in-house R80 Management to the other administrators in ABC
Corp.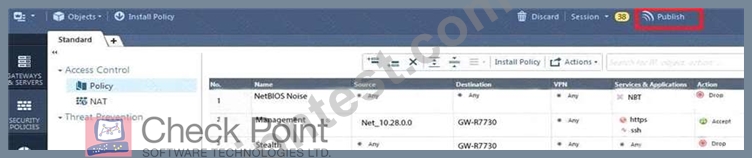
How will you describe the new "Publish" button in R80 Management Console?
- A. The Publish button makes any changes an administrator has made in their management session visible to
all other administrator sessions and saves it to the Database. - B. The Publish button takes any changes an administrator has made in their management session, publishes
a copy to the Check Point of R80, and then saves it to the R80 database. - C. The Publish button takes any changes an administrator has made in their management session and
publishes a copy to the Check Point Cloud of R80 and but does not save it to the R80 - D. The Publish button makes any changes an administrator has made in their management session visible to
the new Unified Policy session and saves it to the Database.
正解: A
解説:
Explanation
To make your changes available to other administrators, and to save the database before installing a policy,
you must publish the session. When you publish a session, a new database version is created.
質問 36
......
最適な道は練習テストCheckPoint 156-215.80問題集:https://www.jpntest.com/shiken/156-215.80-mondaishu
