正真正銘の156-215.80問題集には100%合格率練習テスト問題集
CheckPoint 156-215.80リアル試験問題保証付き 更新された問題集
質問 189
Consider the Global Properties following settings: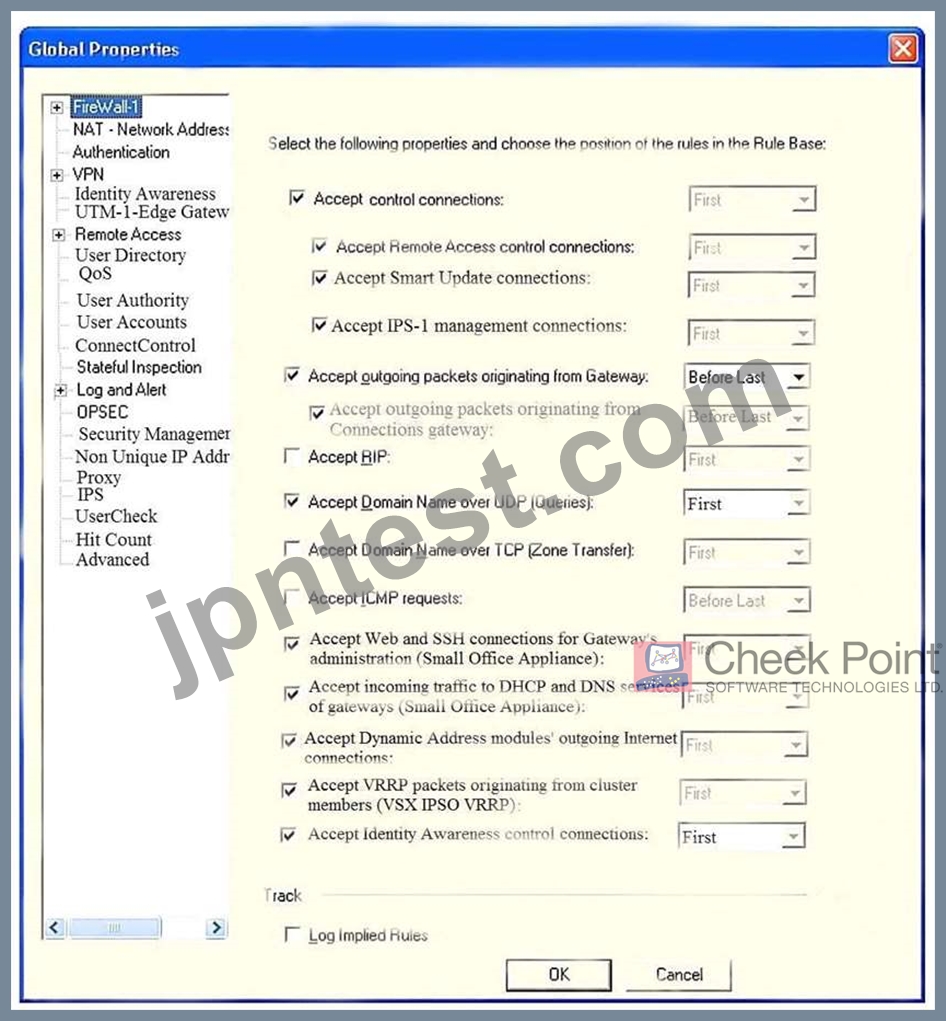
The selected option "Accept Domain Name over UDP (Queries)" means:
- A. UDP Queries will be accepted by the traffic allowed only through interfaces with external anti-spoofing topology and this will be done before first explicit rule written by Administrator in a Security Policy.
- B. All UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
- C. All UDP Queries will be accepted by the traffic allowed by first explicit rule written by Administrator in a Security Policy.
- D. No UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
正解: A
質問 190
Which command can you use to verify the number of active concurrent connections?
- A. fw conn all
- B. show connections
- C. fw ctl pst pstat
- D. show all connections
正解: C
解説:
Explanation/Reference: https://supportcenter.checkpoint.com/supportcenter/portal?
eventSubmit_doGoviewsolutiondetails=&solutionid=sk103496
質問 191
Fill in the blank: In Security Gateways R75 and above, SIC uses ______________ for encryption.
- A. 3DES
- B. AES-256
- C. AES-128
- D. DES
正解: C
解説:
Explanation/Reference: https://sc1.checkpoint.com/documents/R80/CP_R80_SecMGMT/html_frameset.htm?
topic=documents/R80/CP_R80_SecMGMT/125443
質問 192
What is the purpose of the Clean-up Rule?
- A. To log all traffic that is not explicitly allowed or denied in the Rule Base
- B. To eliminate duplicate log entries in the Security Gateway
- C. To remove all rules that could have a conflict with other rules in the database
- D. To clean up policies found inconsistent with the compliance blade reports
正解: A
解説:
Explanation
Explanation:
These are basic access control rules we recommend for all Rule Bases:
* Stealth rule that prevents direct access to the Security Gateway.
* Cleanup rule that drops all traffic that is not allowed by the earlier rules.
There is also an implied rule that drops all traffic, but you can use the Cleanup rule to log the traffic.
Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Firewall_WebAdmin/92703.htm
質問 193
Which Check Point supported authentication scheme typically requires a user to possess a token?
- A. Check Point password
- B. RADIUS
- C. SecurID
- D. TACACS
正解: C
解説:
SecurID
SecurID requires users to both possess a token authenticator and to supply a PIN or password Reference: https://sc1.checkpoint.com/documents/R77/CP_R77_SecurityGatewayTech_WebAdmin/6721.htm
質問 194
You want to define a selected administrator's permission to edit a layer. However, when you click the + sign in the "Select additional profile that will be able edit this layer" you do not see anything. What is the most likely cause of this problem? Select the BEST answer.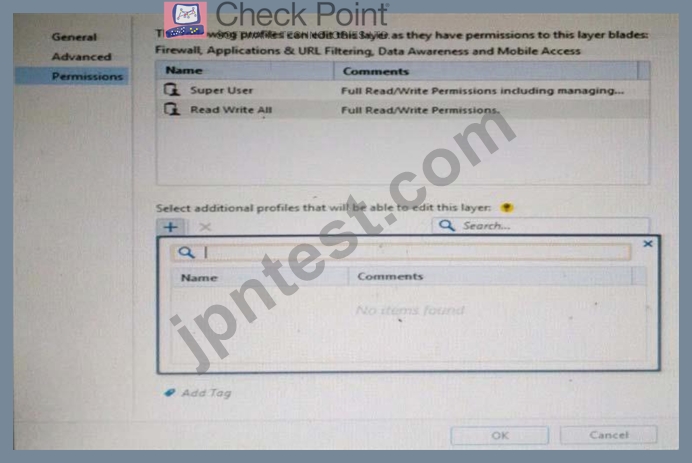
- A. "Edit layers by selected profiles in a layer editor" is unselected in the Permission profile.
- B. All permission profiles are in use.
- C. "Edit layers by Software Blades" is unselected in the Permission Profile
- D. There are no permission profiles available and you need to create one first.
正解: D
質問 195
What command would show the API server status?
- A. api status
- B. api restart
- C. show api status
- D. cpm status
正解: A
質問 196
The following graphic shows: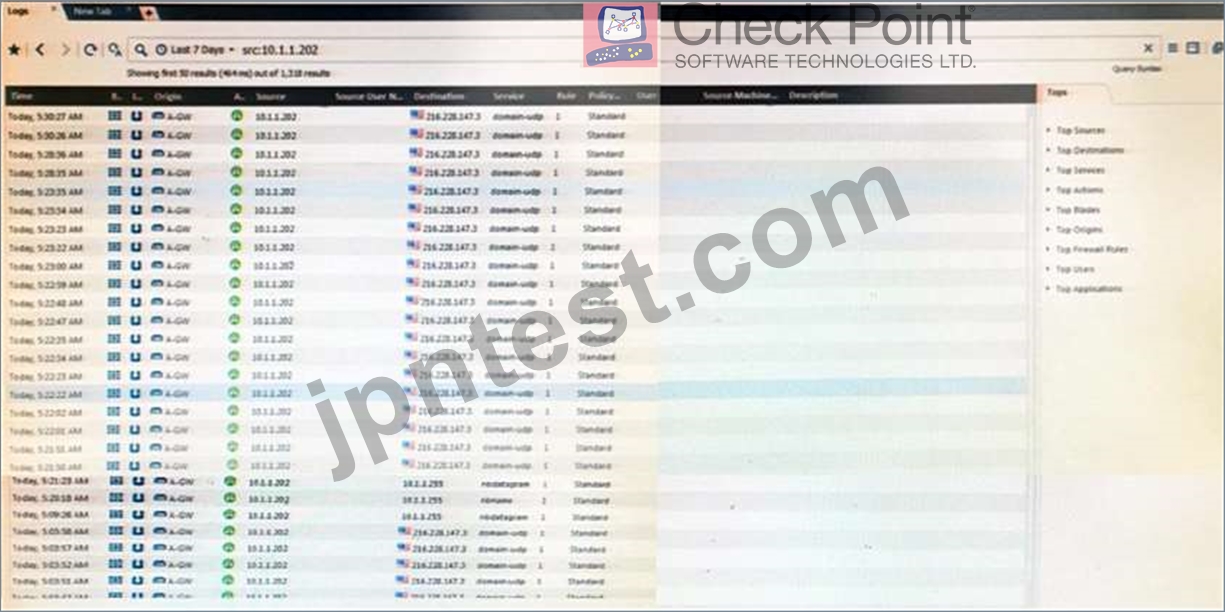
- A. View from SmartView Monitor for logs initiated from source address 10.1.1.202
- B. View from SmartView Tracker for logs of destination address 10.1.1.202
- C. View from SmartView Tracker for logs initiated from source address 10.1.1.202
- D. View from SmartLog for logs initiated from source address 10.1.1.202
正解: C
質問 197
Each cluster has __________ interfaces.
- A. Three
- B. Five
- C. Two
- D. Four
正解: A
解説:
Each cluster member has three interfaces: one external interface, one internal interface, and one for synchronization. Cluster member interfaces facing in each direction are connected via a switch, router, or VLAN switch.
質問 198
Which method below is NOT one of the ways to communicate using the Management API's?
- A. Typing API commands from a dialog box inside the SmartConsole GUI application
- B. Sending API commands over an http connection using web-services
- C. Typing API commands using the "mgmt_cli" command
- D. Typing API commands using Gaia's secure shell (clash)19+
正解: B
解説:
Explanation
References:
質問 199
What Identity Agent allows packet tagging and computer authentication?
- A. System Agent
- B. Light Agent
- C. Full Agent
- D. Endpoint Security Client
正解: C
解説:
Explanation/Reference:
Reference: https://sc1.checkpoint.com/documents/R77/CP_R77_IdentityAwareness_WebAdminGuide/ html_frameset.htm?topic=documents/R77/CP_R77_IdentityAwareness_WebAdminGuide/62838
質問 200
Fill in the blank: An identity server uses a ___________ for user authentication.
- A. One-time password
- B. Token
- C. Certificate
- D. Shared secret
正解: D
解説:
Explanation/Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_IdentityAwareness_AdminGuide/62050.htm
質問 201
What is UserCheck?
- A. Messaging tool user to verify a user's credentials
- B. Administrator tool used to monitor users on their network
- C. Communication tool used to inform a user about a website or application they are trying to access
- D. Communication tool used to notify an administrator when a new user is created
正解: C
解説:
Explanation/Reference:
質問 202
At what point is the Internal Certificate Authority (ICA) created?
- A. When an administrator decides to create one.
- B. When an administrator initially logs into SmartConsole.
- C. Upon creation of a certificate
- D. During the primary Security Management Server installation process.
正解: D
解説:
Explanation/Reference:
Explanation: Introduction to the ICA
The ICA is a Certificate Authority which is an integral part of the Check Point product suite. It is fully compliant with X.509 standards for both certificates and CRLs. See the relevant X.509 and PKI documentation, as well as RFC 2459 standards for more information. You can read more about Check Point and PKI in the R76 VPN Administration Guide.
The ICA is located on the Security Management server. It is created during the installation process, when the Security Management server is configured.
Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_SecMan_WebAdmin/html_frameset.htm?
topic=documents/R76/CP_R76_SecMan_WebAdmin/13118
質問 203
Office mode means that:
- A. Users authenticate with an Internet browser and use secure HTTPS connection.
- B. Allows a security gateway to assign a remote client an IP address. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
- C. Local ISP (Internet service Provider) assigns a non-routable IP address to the remote user.
- D. SecureID client assigns a routable MAC address. After the user authenticates for a tunnel, the VPN gateway assigns a routable IP address to the remote client.
正解: B
解説:
Office Mode enables a Security Gateway to assign internal IP addresses to SecureClient users. This IP address will not be exposed to the public network, but is encapsulated inside the VPN tunnel between the client and the Gateway. The IP to be used externally should be assigned to the client in the usual way by the Internet Service provider used for the Internet connection. This mode allows a Security Administrator to control which addresses are used by remote clients inside the local network and makes them part of the local network. The mechanism is based on an IKE protocol extension through which the Security Gateway can send an internal IP address to the client.
質問 204
Gaia can be configured using the _______ or ______ .
- A. Gaia Interface; GaiaUI
- B. WebUI; Gaia Interface
- C. Gaia; command line interface
- D. Command line interface; WebUI
正解: D
解説:
Configuring Gaia for the First Time
In This Section:
Running the First Time Configuration Wizard in WebUI
Running the First Time Configuration Wizard in CLI
After you install Gaia for the first time, use the First Time Configuration Wizard to configure the system and the Check Point products on it.
質問 205
Which repositories are installed on the Security Management Server by SmartUpdate?
- A. Package Repository and Licenses
- B. Update and License & Contract
- C. License & Contract and Package Repository
- D. License and Update
正解: C
解説:
Explanation
Explanation/Reference: https://sc1.checkpoint.com/documents/R76/CP_R76_Installation_and_Upgrade_Guide- webAdmin/13128.htm
質問 206
......
CheckPoint 156-215.80 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
| トピック 7 |
|
| トピック 8 |
|
| トピック 9 |
|
| トピック 10 |
|
検証済み!合格できる156-215.80試験一発合格保証付き:https://www.jpntest.com/shiken/156-215.80-mondaishu
