合格させるNSE 7 Network Security Architect NSE7_OTS-6.4テスト問題集で[2023年08月01日] 更新された37問あります
Fortinet NSE7_OTS-6.4実際の問題と100%カバー率でリアル試験問題
Fortinet NSE7_OTS-6.4は、オペレーショナル・テクノロジー(OT)セキュリティの分野におけるネットワークセキュリティ専門家のスキルと知識を検証する認定試験です。この試験は、産業制御システム(ICS)や監視制御およびデータ収集(SCADA)システムのセキュリティを担当する個人を対象としています。Fortinet NSE7_OTS-6.4試験は、Fortinetのネットワークセキュリティ専門家(NSE)プログラムの一部であり、Fortinetの製品やソリューションに関する詳細な知識を提供する包括的なトレーニングと認定プログラムです。
Fortinet NSE7_OTS-6.4 Examは、OTネットワークのセキュリティを確保し、キャリアの展望を向上させたい専門家に最適です。この認定は、エネルギー、交通、製造などの重要なインフラセクターで運営する組織によって世界的に認められ、高く評価されています。この認定を取得することで、専門家はOTネットワークをセキュリティ保護し、サイバー脅威を軽減するためにその組織を支援できます。
Fortinet NSE7_OTS-6.4 試験は、IT プロフェッショナルの OT(運用技術)セキュリティ分野におけるスキルと知識を試験する認定です。この試験は、産業制御システム(ICS)、監視制御及びデータ収集(SCADA)システム、その他の重要なインフラストラクチャを確保する候補者の専門知識を認定するために設計されています。この認定は、ネットワークセキュリティ、クラウドセキュリティ、エンドポイント保護ソリューションを提供する主要なサイバーセキュリティ企業である Fortinet によって提供されています。
質問 # 12
Which three common breach points can be found in a typical OT environment? (Choose three.)
- A. Hard hat
- B. Black hat
- C. RTU exploits
- D. VLAN exploits
- E. Global hat
正解:B、C、D
質問 # 13
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. You cannot use Windows and Linux hosts security events with FortiSoC.
- B. Each playbook can include multiple triggers.
- C. You must set correct operator in event handler to trigger an event.
- D. You can automate SOC tasks through playbooks.
正解:B、D
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 # 14
Refer to the exhibit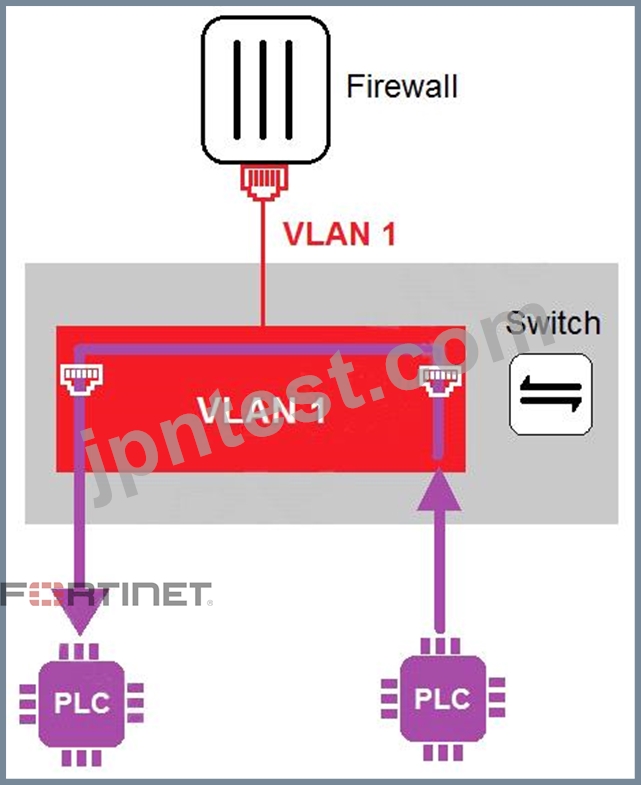
In the topology shown in the exhibit, both PLCs can communicate directly with each other, without going through the firewall.
Which statement about the topology is true?
- A. There is no micro-segmentation in this topology.
- B. An administrator can create firewall policies in the switch to secure between PLCs.
- C. This integration solution expands VLAN capabilities from Layer 2 to Layer 3.
- D. PLCs use IEEE802.1Q protocol to communicate each other.
正解:A
質問 # 15
An OT administrator deployed many devices to secure the OT network. However, the SOC team is reporting that there are too many alerts, and that many of the alerts are false positive. The OT administrator would like to find a solution that eliminates repetitive tasks, improves efficiency, saves time, and saves resources.
Which products should the administrator deploy to address these issues and automate most of the manual tasks done by the SOC team?
- A. A syslog server and FortiSIEM
- B. FortiSandbox and FortiSIEM
- C. FortiSOAR and FortiSIEM
- D. FortiSIEM and FortiManager
正解:C
質問 # 16
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
- A. Under config user settings configure set auth-on-demand implicit.
- B. Enable two-factor authentication with FSSO.
- C. Configure a firewall policy with LDAP users and place it on the top of list of firewall policies.
- D. Configure a firewall policy with FSSO users and place it on the top of list of firewall policies.
正解:A
質問 # 17
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
- A. Destination defined as internet services in the firewall policy
- B. Source defined as internet services in the firewall policy
- C. Highest to lowest priority defined in the firewall policy
- D. Services defined in the firewall policy.
- E. Lowest to highest policy ID number
正解:A、C、D
解説:
The three criteria that a FortiGate device can use to look for a matching firewall policy to process traffic are:
1. Services defined in the firewall policy - FortiGate devices can match firewall policies based on the services defined in the policy, such as HTTP, FTP, or DNS.
2. Destination defined as internet services in the firewall policy - FortiGate devices can also match firewall policies based on the destination of the traffic, including destination IP address, interface, or internet services.
3. Highest to lowest priority defined in the firewall policy - FortiGate devices can prioritize firewall policies based on the priority defined in the policy. The device will process traffic against the policy with the highest priority first and move down the list until it finds a matching policy.
Reference:
Fortinet NSE 7 - Enterprise Firewall 6.4 Study Guide, Chapter 4: Policy Implementation, page 4-18.
質問 # 18
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
- A. FortiAnalyzer
- B. FortiManager
- C. FortiSIEM
- D. FortiNAC
- E. FortiGate
正解:A、C、D
質問 # 19
Which three Fortinet products can be used for device identification in an OT industrial control system (ICS)? (Choose three.)
- A. FortiManager
- B. FortiGate
- C. FortiSIEM
- D. FortiNAC
- E. FortiAnalyzer
正解:B、C、D
解説:
1. FortiNAC - FortiNAC is a network access control solution that provides visibility and control over network devices. It can identify devices, enforce access policies, and automate threat response.
2. FortiSIEM - FortiSIEM is a security information and event management solution that can collect and analyze data from multiple sources, including network devices and servers. It can help identify potential security threats, as well as monitor compliance with security policies and regulations.
3. FortiAnalyzer - FortiAnalyzer is a central logging and reporting solution that collects and analyzes data from multiple sources, including FortiNAC and FortiSIEM. It can provide insights into network activity and help identify anomalies or security threats.
Reference:
Fortinet NSE 7 - OT Security 6.4 Study Guide, Chapter 4: OT Security Devices, page 4-20.
質問 # 20
What two advantages does FortiNAC provide in the OT network? (Choose two.)
- A. It can be used for network micro-segmentation.
- B. It can be used for IoT device detection.
- C. It can be used for industrial intrusion detection and prevention.
- D. It can be used for device profiling.
正解:B、D
解説:
Typically, in a microsegmented network, NGFWs are used in conjunction with VLANs to implement security policies and to inspect and filter network communications. Fortinet FortiSwitch and FortiGate NGFW offer an integrated approach to microsegmentation.
質問 # 21
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Local authentication on FortiGate
- B. Two-factor authentication on FortiAuthenticator
- C. FSSO authentication on FortiGate
- D. Role-based authentication on FortiNAC
正解:A、B
質問 # 22
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
- A. TACACS
- B. RADIUS
- C. ICMP
- D. API
- E. SNMP
正解:B、D、E
質問 # 23
Refer to the exhibit.
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric? (Choose three.)
- A. FortiNAC for network access control
- B. FortiGate for SD-WAN
- C. FortiGate for application control and IPS
- D. FortiSIEM for security incident and event management
- E. FortiEDR for endpoint detection
正解:A、C、D
質問 # 24
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
- A. You cannot use Windows and Linux hosts security events with FortiSoC.
- B. You must set correct operator in event handler to trigger an event.
- C. Each playbook can include multiple triggers.
- D. You can automate SOC tasks through playbooks.
正解:B、D
解説:
Ref: https://docs.fortinet.com/document/fortianalyzer/7.0.0/administration-guide/268882/fortisoc
質問 # 25
An OT network architect needs to secure control area zones with a single network access policy to provision devices to any number of different networks.
On which device can this be accomplished?
- A. FortiNAC
- B. FortiSwitch
- C. FortiGate
- D. FortiEDR
正解:C
解説:
An OT network architect can accomplish the goal of securing control area zones with a single network access policy to provision devices to any number of different networks on a FortiGate device.
質問 # 26
What triggers Layer 2 polling of infrastructure devices connected in the network?
- A. A matched profiling rule
- B. A matched security policy
- C. A linkup or linkdown trap
- D. A failed Layer 3 poll
正解:C
質問 # 27
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
- A. FortiGate determined the user by passive authentication
- B. FortiNAC determined the user by DHCP fingerprint method
- C. The user was determined by Security Fabric
- D. Two-factor authentication is not configured with RADIUS authentication method
正解:B
質問 # 28
In a wireless network integration, how does FortiNAC obtain connecting MAC address information?
- A. End station traffic monitoring
- B. RADIUS
- C. MAC notification traps
- D. Link traps
正解:B
質問 # 29
Refer to the exhibit, which shows a non-protected OT environment.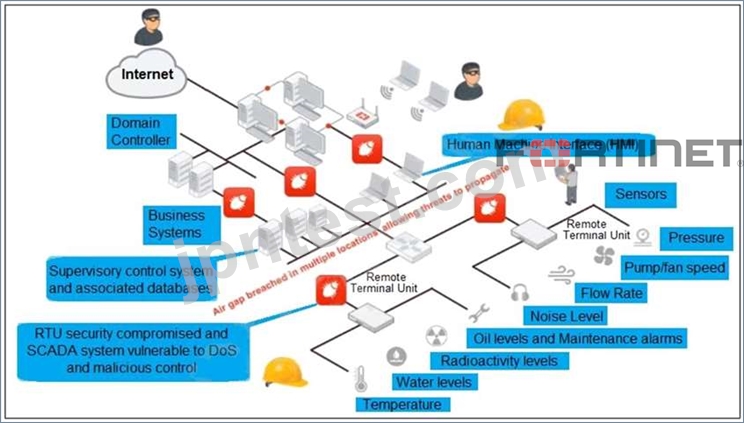
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
- A. Deploy a FortiGate device within each ICS network.
- B. Deploy an edge FortiGate between the internet and an OT network as a one-arm sniffer.
- C. Use segmentation
- D. Configure firewall policies with industrial protocol sensors
- E. Configure firewall policies with web filter to protect the different ICS networks.
正解:B、D、E
質問 # 30
An OT network administrator is trying to implement active authentication.
Which two methods should the administrator use to achieve this? (Choose two.)
- A. Local authentication on FortiGate
- B. Role-based authentication on FortiNAC
- C. Two-factor authentication on FortiAuthenticator
- D. FSSO authentication on FortiGate
正解:B、C
質問 # 31
......
Fortinet NSE7_OTS-6.4リアル2023年最新のブレーン問題集で模擬試験問題集:https://www.jpntest.com/shiken/NSE7_OTS-6.4-mondaishu
