本日更新された312-50v11練習テスト2023年最新の無料問題集を無料登録!
最新のJPNTest 312-50v11のPDF問題集をダウンロード(525問題と解答)
EC-COUNCIL 312-50v11 (Certified Ethical Hacker Exam (CEH v11)) 認定試験は、倫理的ハッキング分野における候補者の知識とスキルを検証する広く認知された認定資格です。この試験は、脆弱性の特定と悪用、リスクの評価と軽減、およびシステムやネットワークをサイバー攻撃から保護する方法についての候補者の理解をテストするように設計されています。試験は、最新の業界動向に基づいており、ネットワークセキュリティ、Webアプリケーションセキュリティ、暗号化、倫理的ハッキング技術など、包括的なトピックをカバーしています。
質問 # 99
George, an employee of an organization, is attempting to access restricted websites from an official computer. For this purpose, he used an anonymizer that masked his real IP address and ensured complete and continuous anonymity for all his online activities. Which of the following anonymizers helps George hide his activities?
- A. https://www.wolframalpha.com
- B. https://www.baidu.com
- C. https://karmadecay.com
- D. https://www.guardster.com
正解:D
質問 # 100
Lewis, a professional hacker, targeted the loT cameras and devices used by a target venture-capital firm. He used an information-gathering tool to collect information about the loT devices connected to a network, open ports and services, and the attack surface are a. Using this tool, he also generated statistical reports on broad usage patterns and trends. This tool helped Lewis continually monitor every reachable server and device on the Internet, further allowing him to exploit these devices in the network. Which of the following tools was employed by Lewis in the above scenario?
- A. Wapiti
- B. NeuVector
- C. Censys
- D. Lacework
正解:C
解説:
Censys scans help the scientific community accurately study the Internet. The data is sometimes used to detect security problems and to inform operators of vulnerable systems so that they can fixed
質問 # 101
During the enumeration phase. Lawrence performs banner grabbing to obtain information such as OS details and versions of services running. The service that he enumerated runs directly on TCP port 445.
Which of the following services is enumerated by Lawrence in this scenario?
- A. Telnet
- B. Server Message Block (SMB)
- C. Network File System (NFS)
- D. Remote procedure call (RPC)
正解:B
解説:
Explanation
Worker Message Block (SMB) is an organization document sharing and information texture convention. SMB is utilized by billions of gadgets in a different arrangement of working frameworks, including Windows, MacOS, iOS , Linux, and Android. Customers use SMB to get to information on workers. This permits sharing of records, unified information the board, and brought down capacity limit needs for cell phones. Workers additionally use SMB as a feature of the Software-characterized Data Center for outstanding burdens like grouping and replication.
Since SMB is a far off record framework, it requires security from assaults where a Windows PC may be fooled into reaching a pernicious worker running inside a confided in organization or to a far off worker outside the organization edge. Firewall best practices and arrangements can upgrade security keeping malevolent traffic from leaving the PC or its organization.
For Windows customers and workers that don't have SMB shares, you can obstruct all inbound SMB traffic utilizing the Windows Defender Firewall to keep far off associations from malignant or bargained gadgets. In the Windows Defender Firewall, this incorporates the accompanying inbound principles.
You should also create a new blocking rule to override any other inbound firewall rules. Use the following suggested settings for any Windows clients or servers that do not host SMB Shares:
* Name: Block all inbound SMB 445
* Description: Blocks all inbound SMB TCP 445 traffic. Not to be applied to domain controllers or computers that host SMB shares.
* Action: Block the connection
* Programs: All
* Remote Computers: Any
* Protocol Type: TCP
* Local Port: 445
* Remote Port: Any
* Profiles: All
* Scope (Local IP Address): Any
* Scope (Remote IP Address): Any
* Edge Traversal: Block edge traversal
You must not globally block inbound SMB traffic to domain controllers or file servers. However, you can restrict access to them from trusted IP ranges and devices to lower their attack surface. They should also be restricted to Domain or Private firewall profiles and not allow Guest/Public traffic.
質問 # 102
George is a security professional working for iTech Solutions. He was tasked with securely transferring sensitive data of the organization between industrial systems. In this process, he used a short-range communication protocol based on the IEEE 203.15.4 standard. This protocol is used in devices that transfer data infrequently at a low rate in a restricted area, within a range of 10-100 m. What is the short-range wireless communication technology George employed in the above scenario?
- A. MQTT
- B. LPWAN
- C. NB-IOT
- D. Zigbee
正解:B
解説:
Low-power WAN (LPWAN) could be a wireless wide space network technology that interconnects low-bandwidth, powered devices with low bit rates over long ranges.
Created for machine-to-machine (M2M) and net of things (IoT) networks, LPWANs operate at a lower value with bigger power potency than ancient mobile networks. they're additionally ready to support a greater range of connected devices over a bigger space.
LPWANs will accommodate packet sizes from ten to 1,000 bytes at transmission speeds up to two hundred Kbps. LPWAN's long vary varies from a pair of kilometre to one,000 km, counting on the technology.
Most LPWANs have a star wherever, like Wi-Fi, every end point connects on to common central access points.
Types of LPWANs
LPWAN isn't one technology, however a bunch of assorted low-power, wide space network technologies that take several shapes and forms. LPWANs will use licenced or unauthorised frequencies and embody proprietary or open normal choices.
The proprietary, unauthorised Sigfox is one among the foremost wide deployed LPWANs these days. Running over a public network within the 868 MHz or 902 MHz bands, the ultra-narrowband technology solely permits one operator per country. whereas it will deliver messages over distances of 30-50 kilometre in rural areas, 3-10 kilometre in urban settings and up to one,000 kilometre in line-of-site applications, its packet size is restricted to a hundred and fifty messages of twelve bytes per day. Downlink packets area unit smaller, restricted to four messages of eight bytes per day. causation information back to endpoints may also be vulnerable to interference.
Random part multiple access, or RPMA, could be a proprietary LPWAN from Ingenu INC. tho' it's a shorter vary (up to fifty kilometre line of sight and with 5-10 kilometre nonline of sight), it offers higher duplex communication than Sigfox. However, as a result of it runs within the a pair of.4 gigahertz spectrum, it's vulnerable to interference from Wi-Fi, Bluetooth and physical structures. It additionally usually has higher power consumption than different LPWAN choices.
The unauthorised LoRa, nominative and backed by the LoRa Alliance, transmits in many sub-gigahertz frequencies, creating it less vulnerable to interference. A spinoff of chirp unfold spectrum (CSS) modulation, LoRa permits users to outline packet size. whereas open supply, the underlying transceiver chip accustomed implement LoRa is barely offered from Semtech Corporation, the corporate behind the technology. LoRaWAN is that the media access management (MAC) layer protocol that manages communication between LPWAN devices and gateways.
Weightless SIG has developed 3 LPWAN standards: The unifacial weightless-N, duplex Weightless-P and Weightless-W, that is additionally duplex and runs off of unused TV spectrum. Weightless-N and Weightless-P area unit usually a lot of in style choices because of Weightless-W's shorter battery life. Weightless-N and Weightless-P run within the sub-1 gigahertz unauthorised spectrum however additionally support licenced spectrum operation mistreatment twelve.5 kilohertz narrowband technology.
Narrowband-IoT (NB-IoT) and LTE-M area unit each third Generation Partnership Project (3GPP) standards that treat the licenced spectrum. whereas they need similar performance to different standards, they treat existing cellular infrastructure, permitting service suppliers to quickly add cellular IoT property to their service portfolios.
NB-IoT, additionally referred to as CAT-NB1, operates on existing LTE and international System for Mobile (GSM) infrastructure. It offers transmission and downlink rates of around two hundred Kbps, mistreatment solely two hundred kilohertz of accessible information measure.
LTE-M, additionally referred to as CAT-M1, offers higher information measure than NB-IoT, and therefore the highest information measure of any LPWAN technology.
Some vendors, as well as Orange and SK medium, area unit deploying each licenced and unauthorised technologies to capture each markets.
Other LPWAN technologies include:
GreenOFDM from GreenWaves Technologies
DASH7 from hayrick Technologies INC.
Symphony Link from Link Labs INC.
ThingPark Wireless from Actility
Ultra slim Band from numerous corporations as well as Telensa, Nwave and Sigfox WAVIoT
質問 # 103
Stella, a professional hacker, performs an attack on web services by exploiting a vulnerability that provides additional routing information in the SOAP header to support asynchronous communication. This further allows the transmission of web-service requests and response messages using different TCP connections. Which of the following attack techniques is used by Stella to compromise the web services?
- A. Web services parsing attacks
- B. SOAPAction spoofing
- C. WS-Address spoofing
- D. XML injection
正解:C
解説:
WS-Address provides additional routing information in the SOAP header to support asynchronous communication. This technique allows the transmission of web service requests and response messages using different TCP connections
https://www.google.com/search?client=firefox-b-d&q=WS-Address+spoofing
CEH V11 Module 14 Page 1896
質問 # 104
Kevin, an encryption specialist, implemented a technique that enhances the security of keys used for encryption and authentication. Using this technique, Kevin input an initial key to an algorithm that generated an enhanced key that is resistant to brute-force attacks. What is the technique employed by Kevin to improve the security of encryption keys?
- A. Key derivation function
- B. A Public key infrastructure
- C. Key stretching
- D. Key reinstallation
正解:B
質問 # 105
Firewalls are the software or hardware systems that are able to control and monitor the traffic coming in and out the target network based on pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
- A. Web application firewall
- B. Stateful firewall
- C. Data-driven firewall
- D. Packet firewall
正解:A
質問 # 106
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.
What is this attack?
- A. Cross-site-scripting attack
- B. SQL Injection
- C. URL Traversal attack
- D. Buffer Overflow attack
正解:A
質問 # 107
On performing a risk assessment, you need to determine the potential impacts when some of the critical business processes of the company interrupt its service.
What is the name of the process by which you can determine those critical businesses?
- A. Emergency Plan Response (EPR)
- B. Business Impact Analysis (BIA)
- C. Risk Mitigation
- D. Disaster Recovery Planning (DRP)
正解:B
質問 # 108
Annie, a cloud security engineer, uses the Docker architecture to employ a client/server model in the application she is working on. She utilizes a component that can process API requests and handle various Docker objects, such as containers, volumes. Images, and networks. What is the component of the Docker architecture used by Annie in the above scenario?
- A. Docker registries
- B. Docker objects
- C. Docker client
- D. Docker daemon
正解:D
解説:
Docker uses a client-server design. The docker client talks to the docker daemon, that will the work of building, running, and distributing your docker containers. The docker client and daemon will run on the same system, otherwise you will connect a docker consumer to a remote docker daemon. The docker consumer and daemon communicate using a REST API, over OS sockets or a network interface.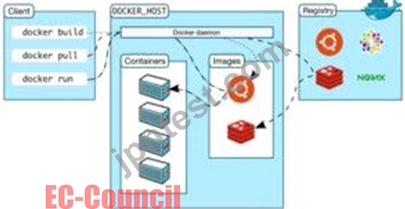
The docker daemon (dockerd) listens for docker API requests and manages docker objects like pictures, containers, networks, and volumes. A daemon may communicate with other daemons to manage docker services.
質問 # 109
Bob was recently hired by a medical company after it experienced a major cyber security breach. Many patients are complaining that their personal medical records are fully exposed on the Internet and someone can find them with a simple Google search. Bob's boss is very worried because of regulations that protect those data. Which of the following regulations is mostly violated?
- A. PCIDSS
- B. ISO 2002
- C. HIPPA/PHl
- D. Pll
正解:C
解説:
Explanation
PHI stands for Protected Health info. The HIPAA Privacy Rule provides federal protections for private health info held by lined entities and provides patients an array of rights with regard to that info. under HIPAA phi is considered to be any identifiable health info that's used, maintained, stored, or transmitted by a HIPAA-covered entity - a healthcare provider, health plan or health insurer, or a aid clearinghouse - or a business associate of a HIPAA-covered entity, in relation to the availability of aid or payment for aid services.
It is not only past and current medical info that's considered letter under HIPAA Rules, however also future info concerning medical conditions or physical and mental health related to the provision of care or payment for care. phi is health info in any kind, together with physical records, electronic records, or spoken info.
Therefore, letter includes health records, medical histories, lab check results, and medical bills. basically, all health info is considered letter once it includes individual identifiers. Demographic info is additionally thought of phi underneath HIPAA Rules, as square measure several common identifiers like patient names, Social Security numbers, Driver's license numbers, insurance details, and birth dates, once they square measure connected with health info.
The eighteen identifiers that create health info letter are:
* Names
* Dates, except year
* phonephone numbers
* Geographic information
* FAX numbers
* Social Security numbers
* Email addresses
* case history numbers
* Account numbers
* Health arrange beneficiary numbers
* Certificate/license numbers
* Vehicle identifiers and serial numbers together with license plates
* Web URLs
* Device identifiers and serial numbers
* net protocol addresses
* Full face photos and comparable pictures
* Biometric identifiers (i.e. retinal scan, fingerprints)
* Any distinctive identifying variety or code
One or a lot of of those identifiers turns health info into letter, and phi HIPAA Privacy Rule restrictions can then apply that limit uses and disclosures of the data. HIPAA lined entities and their business associates will ought to guarantee applicable technical, physical, and body safeguards are enforced to make sure the confidentiality, integrity, and availability of phi as stipulated within the HIPAA Security Rule.
質問 # 110
Gilbert, a web developer, uses a centralized web API to reduce complexity and increase the Integrity of updating and changing dat a. For this purpose, he uses a web service that uses HTTP methods such as PUT. POST. GET. and DELETE and can improve the overall performance, visibility, scalability, reliability, and portability of an application. What is the type of web-service API mentioned in the above scenario?
- A. SOAP API
- B. JSON-RPC
- C. RESTful API
- D. REST API
正解:C
質問 # 111
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
- A. [info:]
- B. [inurl:]
- C. [related:]
- D. [site:]
正解:C
解説:
related:This operator displays websites that are similar or related to the URL specified.
質問 # 112
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
- A. Broadcast ping
- B. Traceroute
- C. TCP ping
- D. Hping
正解:D
解説:
https://tools.kali.org/information-gathering/hping3
質問 # 113
Susan, a software developer, wants her web API to update other applications with the latest information. For this purpose, she uses a user-defined HTTP tailback or push APIs that are raised based on trigger events: when invoked, this feature supplies data to other applications so that users can instantly receive real-time Information.
Which of the following techniques is employed by Susan?
- A. Webhooks
- B. web shells
- C. SOAP API
- D. REST API
正解:A
解説:
Webhooks are one of a few ways internet applications will communicate with one another.
It allows you to send real-time data from one application to another whenever a given event happens.
For example, let's say you've created an application using the Foursquare API that tracks when people check into your restaurant. You ideally wish to be able to greet customers by name and provide a complimentary drink when they check in.
What a webhook will is notify you any time someone checks in, therefore you'd be able to run any processes that you simply had in your application once this event is triggered.
The data is then sent over the web from the application wherever the event originally occurred, to the receiving application that handles the data.
Here's a visual representation of what that looks like:
A webhook url is provided by the receiving application, and acts as a phone number that the other application will call once an event happens.
Only it's more complicated than a phone number, because data about the event is shipped to the webhook url in either JSON or XML format. this is known as the "payload." Here's an example of what a webhook url looks like with the payload it's carrying:
What are Webhooks? Webhooks are user-defined HTTP callback or push APIs that are raised based on events triggered, such as comment received on a post and pushing code to the registry. A webhook allows an application to update other applications with the latest information. Once invoked, it supplies data to the other applications, which means that users instantly receive real-time information. Webhooks are sometimes called "Reverse APIs" as they provide what is required for API specification, and the developer should create an API to use a webhook. A webhook is an API concept that is also used to send text messages and notifications to mobile numbers or email addresses from an application when a specific event is triggered. For instance, if you search for something in the online store and the required item is out of stock, you click on the "Notify me" bar to get an alert from the application when that item is available for purchase. These notifications from the applications are usually sent through webhooks.
質問 # 114
Vlady works in a fishing company where the majority of the employees have very little understanding of IT let alone IT Security. Several information security issues that Vlady often found includes, employees sharing password, writing his/her password on a post it note and stick it to his/her desk, leaving the computer unlocked, didn't log out from emails or other social media accounts, and etc.
After discussing with his boss, Vlady decided to make some changes to improve the security environment in his company. The first thing that Vlady wanted to do is to make the employees understand the importance of keeping confidential information, such as password, a secret and they should not share it with other persons.
Which of the following steps should be the first thing that Vlady should do to make the employees in his company understand to importance of keeping confidential information a secret?
- A. Conducting a one to one discussion with the other employees about the importance of information security
- B. Developing a strict information security policy
- C. Information security awareness training
- D. Warning to those who write password on a post it note and put it on his/her desk
正解:D
質問 # 115
Ricardo has discovered the username for an application in his targets environment. As he has a limited amount of time, he decides to attempt to use a list of common passwords he found on the Internet. He compiles them into a list and then feeds that list as an argument into his password-cracking application, what type of attack is Ricardo performing?
- A. Brute force
- B. Dictionary
- C. Known plaintext
- D. Password spraying
正解:A
解説:
A brute force attack could be a popular cracking method: by some accounts, brute force attacks accounted for five% has a of confirmed security breaches. A brute force attack involves 'guessing' username and passwords to achieve unauthorized access to a system. Brute force could be a easy attack methodology and encompasses a high success rate. Some attackers use applications and scripts as brute force tools. These tools attempt various parole combos to bypass authentication processes. In different cases, attackers try and access net applications by sorting out the correct session ID. offender motivation might embody stealing data, infecting sites with malware, or disrupting service. While some attackers still perform brute force attacks manually, nowadays most brute force attacks nowadays area unit performed by bots. Attackers have lists of ordinarily used credentials, or real user credentials, obtained via security breaches or the dark net. Bots consistently attack websites and take a look at these lists of credentials, and apprize the offender after they gain access.
Types of Brute Force Attacks
* Simple brute force attack-uses a scientific approach to 'guess' that doesn't believe outside logic. * Hybrid brute force attacks-starts from external logic to see that parole variation could also be presumably to succeed, then continues with the easy approach to undertake several potential variations. * Dictionary attacks-guesses username or passwords employing a wordbook of potential strings or phrases. * Rainbow table attacks-a rainbow table could be a precomputed table for reversing cryptologic hash functions. It may be wont to guess a perform up to a precise length consisting of a restricted set of characters. * Reverse brute force attack-uses a typical parole or assortment of passwords against several potential username . Targets a network of users that the attackers have antecedently obtained knowledge. * Credential stuffing-uses previously-known password-username pairs, attempting them against multiple websites. Exploits the actual fact that several users have an equivalent username and parole across totally different systems.
Hydra and different widespread Brute Force Attack Tools
Security analysts use the THC-Hydra tool to spot vulnerabilities in shopper systems. Hydra quickly runs through an outsized range of parole combos, either easy brute force or dictionary-based. It will attack quite fifty protocols and multiple operational systems. Hydra is an open platform; the safety community and attackers perpetually develop new modules.
Other high brute force tools are: * Aircrack-ng-can be used on Windows, Linux, iOS, and golem. It uses a wordbook of wide used passwords to breach wireless networks. * John the Ripper-runs on fifteen totally different platforms as well as UNIX operating system, Windows, and OpenVMS. Tries all potential combos employing a dictionary of potential passwords. * L0phtCrack-a tool for cracking Windows passwords. It uses rainbow tables, dictionaries, and digital computer algorithms. * Hashcat-works on Windows, Linux, and Mac OS. will perform easy brute force, rule-based, and hybrid attacks. * DaveGrohl-an open-source tool for cracking mac OS. may be distributed across multiple computers. * Ncrack-a tool for cracking network authentication. It may be used on Windows, Linux, and BSD.
質問 # 116
Morris, a professional hacker, performed a vulnerability scan on a target organization by sniffing the traffic on the network lo identify the active systems, network services, applications, and vulnerabilities. He also obtained the list of the users who are currently accessing the network. What is the type of vulnerability assessment that Morris performed on the target organization?
- A. Credentialed assessment
- B. External assessment
- C. Passive assessment
- D. internal assessment
正解:A
解説:
Explanation
Detached weakness evaluation adopts an interesting strategy: In checking network traffic, it endeavors to order a hub's working framework, ports and benefits, and to find weaknesses a functioning scan like Nessus or Qualys probably won't discover on the grounds that ports are hindered or another host has come on the web.
The information may then give setting to security occasions, for example, relating with IDS alarms to lessen bogus positives.
Uninvolved investigation offers two key points of interest. The first is perceivability. There's regularly a wide hole between the thing you believe is running on your organization and what really is. Both organization and host scan report just what they see. Scan are obstructed by organization and host firewalls. In any event, when a host is live, the data accumulated is here and there restricted to flag checks and some noninvasive setup checks. In the event that your scan has the host certifications, it can question for more data, however bogus positives are an immense issue, you actually may not see everything. Further, rootkits that introduce themselves may run on a nonscanned port or, on account of UDP, may not react to an irregular test. On the off chance that a functioning weakness appraisal scan doesn't see it, it doesn't exist to the scan.
Host firewalls are regular even on worker PCs, so how would you identify a rebel worker or PC with a functioning output? An inactive sensor may see mavericks on the off chance that they're visiting on the organization; that is perceivability a scanner won't give you. A detached sensor likewise will recognize action to and from a port that isn't generally filtered, and may identify nonstandard port utilization, given the sensor can interpret and order the traffic. For instance, basic stream examination won't distinguish SSH or telnet on Port 80, however convention investigation may.
The subsequent significant favorable position of inactive investigation is that it's noninvasive- - it doesn't intrude on organization tasks. Dynamic weakness evaluation scanners are obtrusive and can disturb administrations, regardless of their designers' endeavors to limit the potential for blackouts. In any event, utilizing alleged safe sweeps, we've taken out switches, our NTP administration and a large group of other basic framework segments. Quite a long while prior, we even bobbed our center switch twice with a nmap port output.
質問 # 117
Kate dropped her phone and subsequently encountered an issue with the phone's internal speaker. Thus, she is using the phone's loudspeaker for phone calls and other activities. Bob, an attacker, takes advantage of this vulnerability and secretly exploits the hardware of Kate's phone so that he can monitor the loudspeaker's output from data sources such as voice assistants, multimedia messages, and audio files by using a malicious app to breach speech privacy. What is the type of attack Bob performed on Kate in the above scenario?
- A. Man-in-the-disk attack
- B. Spearphone attack
- C. aLTEr attack
- D. SIM card attack
正解:B
質問 # 118
Andrew is an Ethical Hacker who was assigned the task of discovering all the active devices hidden by a restrictive firewall in the IPv4 range in a given target network.
Which of the following host discovery techniques must he use to perform the given task?
- A. TCP Maimon scan
- B. arp ping scan
- C. ACK flag probe scan
- D. UDP scan
正解:B
解説:
Explanation
One of the most common Nmap usage scenarios is scanning an Ethernet LAN. Most LANs, especially those that use the private address range granted by RFC 1918, do not always use the overwhelming majority of IP addresses. When Nmap attempts to send a raw IP packet, such as an ICMP echo request, the OS must determine a destination hardware (ARP) address, such as the target IP, so that the Ethernet frame can be properly addressed. .. This is required to issue a series of ARP requests. This is best illustrated by an example where a ping scan is attempted against an Area Ethernet host. The -send-ip option tells Nmap to send IP-level packets (rather than raw Ethernet), even on area networks. The Wireshark output of the three ARP requests and their timing have been pasted into the session.
Raw IP ping scan example for offline targetsThis example took quite a couple of seconds to finish because the (Linux) OS sent three ARP requests at 1 second intervals before abandoning the host. Waiting for a few seconds is excessive, as long as the ARP response usually arrives within a few milliseconds. Reducing this timeout period is not a priority for OS vendors, as the overwhelming majority of packets are sent to the host that actually exists. Nmap, on the other hand, needs to send packets to 16 million IP s given a target like
10.0.0.0/8. Many targets are pinged in parallel, but waiting 2 seconds each is very delayed.
There is another problem with raw IP ping scans on the LAN. If the destination host turns out to be unresponsive, as in the previous example, the source host usually adds an incomplete entry for that destination IP to the kernel ARP table. ARP tablespaces are finite and some operating systems become unresponsive when full. If Nmap is used in rawIP mode (-send-ip), Nmap may have to wait a few minutes for the ARP cache entry to expire before continuing host discovery.
ARP scans solve both problems by giving Nmap the highest priority. Nmap issues raw ARP requests and handles retransmissions and timeout periods in its sole discretion. The system ARP cache is bypassed. The example shows the difference. This ARP scan takes just over a tenth of the time it takes for an equivalent IP.
Example b ARP ping scan of offline target
In example b, neither the -PR option nor the -send-eth option has any effect. This is often because ARP has a default scan type on the Area Ethernet network when scanning Ethernet hosts that Nmap discovers. This includes traditional wired Ethernet as 802.11 wireless networks. As mentioned above, ARP scanning is not only more efficient, but also more accurate. Hosts frequently block IP-based ping packets, but usually cannot block ARP requests or responses and communicate over the network.Nmap uses ARP instead of all targets on equivalent targets, even if different ping types (such as -PE and -PS) are specified. LAN.. If you do not need to attempt an ARP scan at all, specify -send-ip as shown in Example a "Raw IP Ping Scan for Offline Targets".
If you give Nmap control to send raw Ethernet frames, Nmap can also adjust the source MAC address. If you have the only PowerBook in your security conference room and a large ARP scan is initiated from an Apple-registered MAC address, your head may turn to you. Use the -spoof-mac option to spoof the MAC address as described in the MAC Address Spoofing section.
質問 # 119
The establishment of a TCP connection involves a negotiation called three-way handshake. What type of message does the client send to the server in order to begin this negotiation?
- A. RST
- B. SYN-ACK
- C. ACK
- D. SYN
正解:D
質問 # 120
An attacker has installed a RAT on a host. The attacker wants to ensure that when a user attempts to go to "www.MyPersonalBank.com", the user is directed to a phishing site.
Which file does the attacker need to modify?
- A. Sudoers
- B. Networks
- C. Hosts
- D. Boot.ini
正解:C
質問 # 121
......
EC-COUNCIL 312-50v11(Certified Ethical Hacker Exam(CEH v11))認定試験の準備をするために、受験者は試験に必要なトピックとスキルをカバーするトレーニングコースに参加することをお勧めします。CEH v11のトレーニングをオンラインおよび対面で提供するトレーニングプロバイダーは多数あり、受験者はEC-COUNCILによって認定されたプロバイダーを選択することで、最高品質のトレーニングを受けることができます。
2023年04月最新312-50v11試験問題集PDFと試験エンジン:https://www.jpntest.com/shiken/312-50v11-mondaishu
