312-50v11問題集を掴み取れ![最新2023]EC-COUNCIL試験合格させます
312-50v11試験問題集PDF正確率保証と更新された問題
質問 100
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking the hashed passwords?
- A. netcat
- B. John the Ripper
- C. THC-Hydra
- D. Hashcat
正解: B
質問 101
Which among the following is the best example of the hacking concept called "clearing tracks"?
- A. After a system is breached, a hacker creates a backdoor to allow re-entry into a system.
- B. During a cyberattack, a hacker injects a rootkit into a server.
- C. During a cyberattack, a hacker corrupts the event logs on all machines.
- D. An attacker gains access to a server through an exploitable vulnerability.
正解: C
質問 102
Attacker Steve targeted an organization's network with the aim of redirecting the company's web traffic to another malicious website. To achieve this goal, Steve performed DNS cache poisoning by exploiting the vulnerabilities in the DNS server software and modified the original IP address of the target website to that of a fake website.
What is the technique employed by Steve to gather information for identity theft?
- A. Skimming
- B. Pharming
- C. Wardriving
- D. Pretexting
正解: B
質問 103
A DDOS attack is performed at layer 7 to take down web infrastructure. Partial HTTP requests are sent to the web infrastructure or applications. Upon receiving a partial request, the target servers opens multiple connections and keeps waiting for the requests to complete.
Which attack is being described here?
- A. Slowloris attack
- B. Session splicing
- C. Desynchronization
- D. Phlashing
正解: A
解説:
Explanation
Developed by Robert "RSnake" Hansen, Slowloris is DDoS attack software that permits one computer to require down an internet server. Due the straightforward yet elegant nature of this attack, it requires minimal bandwidth to implement and affects the target server's web server only, with almost no side effects on other services and ports.Slowloris has proven highly-effective against many popular sorts of web server software, including Apache 1.x and 2.x.Over the years, Slowloris has been credited with variety of high-profile server takedowns. Notably, it had been used extensively by Iranian 'hackivists' following the 2009 Iranian presidential election to attack Iranian government internet sites .Slowloris works by opening multiple connections to the targeted web server and keeping them open as long as possible. It does this by continuously sending partial HTTP requests, none of which are ever completed. The attacked servers open more and connections open, expecting each of the attack requests to be completed.Periodically, the Slowloris sends subsequent HTTP headers for every request, but never actually completes the request. Ultimately, the targeted server's maximum concurrent connection pool is filled, and extra (legitimate) connection attempts are denied.By sending partial, as against malformed, packets, Slowloris can easily elapse traditional Intrusion Detection systems.Named after a kind of slow-moving Asian primate, Slowloris really does win the race by moving slowly and steadily. A Slowloris attack must await sockets to be released by legitimate requests before consuming them one by one.For a high-volume internet site , this will take a while . the method are often further slowed if legitimate sessions are reinitiated. But within the end, if the attack is unmitigated, Slowloris-like the tortoise-wins the race.If undetected or unmitigated, Slowloris attacks also can last for long periods of your time . When attacked sockets outing , Slowloris simply reinitiates the connections, continuing to reach the online server until mitigated.Designed for stealth also as efficacy, Slowloris are often modified to send different host headers within the event that a virtual host is targeted, and logs are stored separately for every virtual host.More importantly, within the course of an attack, Slowloris are often set to suppress log file creation. this suggests the attack can catch unmonitored servers off-guard, with none red flags appearing in log file entries.Methods of mitigationImperva's security services are enabled by reverse proxy technology, used for inspection of all incoming requests on their thanks to the clients' servers.Imperva's secured proxy won't forward any partial connection requests-rendering all Slowloris DDoS attack attempts completely and utterly useless.
質問 104
You are logged in as a local admin on a Windows 7 system and you need to launch the Computer Management Console from command line.
Which command would you use?
- A. c:\gpedit
- B. c:\ncpa.cp
- C. c:\services.msc
- D. c:\compmgmt.msc
正解: D
解説:
To start the Computer Management Console from command line just type compmgmt.msc /computer:computername in your run box or at the command line and it should automatically open the Computer Management console.
References: http://www.waynezim.com/tag/compmgmtmsc/
質問 105
The network users are complaining because their system are slowing down. Further, every time they attempt to go a website, they receive a series of pop-ups with advertisements. What types of malware have the system been infected with?
- A. Spyware
- B. Adware
- C. Trojan
- D. Virus
正解: B
解説:
Explanation
Adware, or advertising supported computer code, is computer code that displays unwanted advertisements on your pc. Adware programs can tend to serve you pop-up ads, will modification your browser's homepage, add spyware and simply bombard your device with advertisements. Adware may be a additional summary name for doubtless unwanted programs. It's roughly a virulent disease and it's going to not be as clearly malicious as a great deal of different problematic code floating around on the net. create no mistake concerning it, though, that adware has to return off of no matter machine it's on. Not solely will adware be extremely annoying whenever you utilize your machine, it might additionally cause semipermanent problems for your device.
Adware a network users the browser to gather your internet browsing history so as to 'target' advertisements that appear tailored to your interests. At their most innocuous, adware infections square measure simply annoying. as an example, adware barrages you with pop-up ads that may create your net expertise markedly slower and additional labor intensive.
質問 106
Ricardo has discovered the username for an application in his target's environment. As he has a limited amount of time, he decides to attempt to use a list of common passwords he found on the Internet. He compiles them into a list and then feeds that list as an argument into his password-cracking application.
What type of attack is Ricardo performing?
- A. Brute force
- B. Dictionary
- C. Password spraying
- D. Known plaintext
正解: B
質問 107
You are trying to break into a highly classified top-secret mainframe computer with highest security system in place at Merclyn Barley Bank located in Los Angeles.
You know that conventional hacking doesn't work in this case, because organizations such as banks are generally tight and secure when it comes to protecting their systems.
In other words, you are trying to penetrate an otherwise impenetrable system.
How would you proceed?
- A. Look for "zero-day" exploits at various underground hacker websites in Russia and China and buy the necessary exploits from these hackers and target the bank's network
- B. Try to conduct Man-in-the-Middle (MiTM) attack and divert the network traffic going to the Merclyn Barley Bank's Webserver to that of your machine using DNS Cache Poisoning techniques
- C. Launch DDOS attacks against Merclyn Barley Bank's routers and firewall systems using 100, 000 or more "zombies" and "bots"
- D. Try to hang around the local pubs or restaurants near the bank, get talking to a poorly-paid or disgruntled employee, and offer them money if they'll abuse their access privileges by providing you with sensitive information
正解: D
質問 108
Which of the following allows attackers to draw a map or outline the target organization's network infrastructure to know about the actual environment that they are going to hack.
- A. Enumeration
- B. Scanning networks
- C. Vulnerability analysis
- D. Malware analysis
正解: A
質問 109
Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications. He installed a fake communication tower between two authentic endpoints to mislead the victim. Bobby used this virtual tower to interrupt the data transmission between the user and real tower, attempting to hijack an active session, upon receiving the users request. Bobby manipulated the traffic with the virtual tower and redirected the victim to a malicious website. What is the attack performed by Bobby in the above scenario?
- A. jamming signal attack
- B. KRACK attack
- C. Wardriving
- D. aLTEr attack
正解: D
質問 110
An organization is performing a vulnerability assessment tor mitigating threats. James, a pen tester, scanned the organization by building an inventory of the protocols found on the organization's machines to detect which ports are attached to services such as an email server, a web server or a database server. After identifying the services, he selected the vulnerabilities on each machine and started executing only the relevant tests. What is the type of vulnerability assessment solution that James employed in the above scenario?
- A. Service-based solutions
- B. Product-based solutions
- C. Tree-based assessment
- D. inference-based assessment
正解: A
解説:
Explanation
As systems approaches to the event of biological models become more mature, attention is increasingly that specialize in the matter of inferring parameter values within those models from experimental data. However, particularly for nonlinear models, it's not obvious, either from inspection of the model or from the experimental data, that the inverse problem of parameter fitting will have a singular solution, or maybe a non-unique solution that constrains the parameters to lie within a plausible physiological range. Where parameters can't be constrained they're termed 'unidentifiable'. We specialise in gaining insight into the causes of unidentifiability using inference-based methods, and compare a recently developed measure-theoretic approach to inverse sensitivity analysis to the favored Markov chain Monte Carlo and approximate Bayesian computation techniques for Bayesian inference. All three approaches map the uncertainty in quantities of interest within the output space to the probability of sets of parameters within the input space. The geometry of those sets demonstrates how unidentifiability are often caused by parameter compensation and provides an intuitive approach to inference-based experimental design.
質問 111
Which of the following is the BEST way to defend against network sniffing?
- A. Using encryption protocols to secure network communications
- B. Restrict Physical Access to Server Rooms hosting Critical Servers
- C. Register all machines MAC Address in a Centralized Database
- D. Use Static IP Address
正解: A
質問 112
These hackers have limited or no training and know how to use only basic techniques or tools.
What kind of hackers are we talking about?
- A. White-Hat Hackers
- B. Script Kiddies
- C. Black-Hat Hackers A
- D. Gray-Hat Hacker
正解: B
解説:
Explanation
Script Kiddies: These hackers have limited or no training and know how to use only basictechniques or tools.
Even then they may not understand any or all of what they are doing.
質問 113
Which of the following is the least-likely physical characteristic to be used in biometric control that supports a large company?
- A. Iris patterns
- B. Fingerprints
- C. Height and Weight
- D. Voice
正解: C
質問 114
In Trojan terminology, what is a covert channel?
- A. It is Reverse tunneling technique that uses HTTPS protocol instead of HTTP protocol to establish connections
- B. A channel that transfers information within a computer system or network in a way that violates the security policy
- C. It is a kernel operation that hides boot processes and services to mask detection
- D. A legitimate communication path within a computer system or network for transfer of data
正解: B
質問 115
which of the following protocols can be used to secure an LDAP service against anonymous queries?
- A. SSO
- B. WPA
- C. RADIUS
- D. NTLM
正解: C
解説:
Explanation
Remote Authentication Dial-In User Service (RADIUS) could be a networking protocols, in operation on ports
1812 and 1813, that gives centralized Authentication, Authorization, and Accounting (AAA or Triple A) management for users who connect and use a network service. RADIUS was developed by American Revolutionary leader Enterprises, Inc. in 1991 as an access server authentication and accounting protocol and later brought into the net Engineering Task Force (IETF) standards.
RADIUS could be a client/server protocol that runs within the application layer, and might use either protocol or UDP as transport. Network access servers, the gateways that management access to a network, sometimes contain a RADIUS consumer element that communicates with the RADIUS server . RADIUS is commonly the back-end of alternative for 802.1X authentication moreover.
The RADIUS server is sometimes a background method running on a UNIX system or Microsoft Windows server.
質問 116
The Heartbleed bug was discovered in 2014 and is widely referred to under MITRE's Common Vulnerabilities and Exposures (CVE) as CVE-2014-0160. This bug affects the OpenSSL implementation of the Transport Layer Security (TLS) protocols defined in RFC6520.
What type of key does this bug leave exposed to the Internet making exploitation of any compromised system very easy?
- A. Root
- B. Shared
- C. Public
- D. Private
正解: D
質問 117
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
- A. Broadcast ping
- B. TCP ping
- C. Hping
- D. Traceroute
正解: C
解説:
Explanation
https://tools.kali.org/information-gathering/hping3
質問 118
An attacker is trying to redirect the traffic of a small office. That office is using their own mail server, DNS server and NTP server because of the importance of their job. The attacker gain access to the DNS server and redirect the direction www.google.com to his own IP address. Now when the employees of the office want to go to Google they are being redirected to the attacker machine. What is the name of this kind of attack?
- A. DNS spoofing
- B. MAC Flooding
- C. Smurf Attack
- D. ARP Poisoning
正解: A
質問 119
Richard, an attacker, targets an MNC. In this process, he uses a footprinting technique to gather as much information as possible. Using this technique, he gathers domain information such as the target domain name, contact details of its owner, expiry date, and creation date. With this information, he creates a map of the organization's network and misleads domain owners with social engineering to obtain internal details of its network.
What type of footprinting technique is employed by Richard?
- A. Email footprinting
- B. Whois footprinting
- C. VoIP footprinting
- D. VPN footprinting
正解: B
質問 120
What did the following commands determine?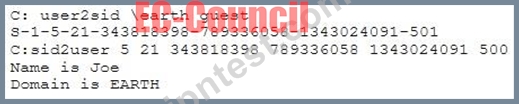
- A. That the Joe account has a SID of 500
- B. That the true administrator is Joe
- C. These commands demonstrate that the guest account has NOT been disabled
- D. Issued alone, these commands prove nothing
- E. These commands demonstrate that the guest account has been disabled
正解: B
質問 121
......
EC-COUNCIL 312-50v11 認定試験の出題範囲:
| トピック | 出題範囲 |
|---|---|
| トピック 1 |
|
| トピック 2 |
|
| トピック 3 |
|
| トピック 4 |
|
| トピック 5 |
|
| トピック 6 |
|
最新をゲットせよ!312-50v11認定練習テスト問題 試験問題集:https://www.jpntest.com/shiken/312-50v11-mondaishu
