2024年最新の認定サンプル問題Secret-Sen問題集と練習試験合格させます
Secret-Sen豪華セット学習ガイドにはオンライン試験エンジン
Cyberark Secret-Sen認定試験は、複数選択の質問で構成され、オンラインで実施されます。試験期間は2時間で、候補者は認定を受けるために70%の合格スコアを達成する必要があります。試験に失敗した候補者は、14日間の待機期間後にそれを再試行できます。認定は2年間有効であり、その後、候補者は認証ステータスを維持するために再認定する必要があります。
CyberArk Secrets Managerソリューションは、アプリケーション、サービス、およびマシンが使用する資格情報およびシークレットを保護、管理、およびローテーションするために設計されたエンタープライズグレードのプラットフォームです。CyberArk Secret-Sen認定試験に合格することで、候補者は特権アカウントとシークレットを管理する専門知識を証明し、それはサイバーセキュリティの専門家にとって重要なスキルです。
質問 # 13
When working with Credential Providers in a Privileged Cloud setting, what is a special consideration?
- A. If there are installation issues, troubleshooting may need to involve the Privileged Cloud support team.
- B. Debug logging for Credential Providers deployed in a Privileged Cloud setting can inadvertently exhaust available disk space.
- C. The AWS Cloud account number must be defined in the file main appprovider.conf.
<platform>.<version> found in the AppProviderConf Safe. - D. Credential Providers are not supported in a Privileged Cloud setting.
正解:A
解説:
Explanation
Credential Providers are tools that enable applications to securely retrieve credentials from CyberArk Secrets Manager without hard-coding or storing them in files. Credential Providers can be installed on application servers or on a central server that acts as a proxy for multiple applications. Credential Providers can integrate with Privileged Cloud, which is a cloud-based solution that provides privileged access management as a service. Privileged Cloud integrates with Secrets Manager Credential Providers to manage application credentials as privileged accounts within Privileged Cloud.
When working with Credential Providers in a Privileged Cloud setting, a special consideration is that if there are installation issues, troubleshooting may need to involve the Privileged Cloud support team. This is because the installation of Credential Providers in a Privileged Cloud setting requires some additional steps and configurations that are performed by the Privileged Cloud support team. For example, the Privileged Cloud support team needs to configure the connection between Privileged Cloud and Credential Providers, and provide the necessary certificates and keys for secure communication. Therefore, if there are any problems or errors during the installation process, the Privileged Cloud support team may need to assist with the troubleshooting and resolution.
The other options are not correct. Credential Providers are supported in a Privileged Cloud setting, as described in the Secrets Manager Credential Providers integration documentation1. The AWS Cloud account number does not need to be defined in the file main appprovider.conf.<platform>.<version> found in the AppProviderConf Safe. This file is used to configure the Credential Provider settings, such as the Privileged Cloud URL, the application ID, and the SSL options. The AWS Cloud account number is not relevant for this file. Debug logging for Credential Providers deployed in a Privileged Cloud setting can be enabled or disabled by the Privileged Cloud support team, as described in the Credential Provider installation documentation2.
Debug logging can help with troubleshooting and diagnostics, but it does not necessarily exhaust available disk space, as the log files can be rotated and archived.
References = Secrets Manager Credential Providers integration; Credential Provider installation
質問 # 14
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
- A. The application ID or Application Provider does not have the correct permissions on the safe.
- B. The OS user does not have the correct permissions on the safe
- C. The client certificate fingerprint is not trusted.
- D. The service account running the application does not have the correct permissions on the safe.
正解:A
解説:
Explanation
The most likely cause for this issue is A. The application ID or Application Provider does not have the correct permissions on the safe. The CyberArk Central Credential Provider (CCP) is a web service that enables applications to retrieve secrets from the CyberArk Vault using REST API calls. The CCP requires an application ID or an Application Provider to authenticate and authorize the application before returning the requested secret. The application ID or Application Provider must have the Retrieve and List permissions on the safe where the secret is stored, otherwise the CCP will not be able to find the matching secret and will return an error.
To resolve this issue, you should verify that the application ID or Application Provider has the correct permissions on the safe, and that the safe name and object name are correctly specified in the REST API call.
You can use the CyberArk Privileged Access Security Web Access (PVWA) or the PrivateArk Client to check and modify the permissions on the safe. You can also use the CyberArk REST API Tester or a tool like Postman to test the REST API call and see the response from the CCP. For more information, refer to the following resources:
Credential Providers - Centralized Credential Management | CyberArk, Section "Central Credential Provider" Credential Provider - CyberArk, Section "Using the Credential Provider" How to Build Your Secrets Management REST API's into Postman, Section "How to Build Your Secrets Management REST API's into Postman"
質問 # 15
Where can all the self-signed/imported certificates be found in Conjur?
- A. /opt/conjur/etc/ssl from the Conjur containers
- B. /opt/conjur/certificates from the Conjur containers
- C. Log in to the Conjur UI > Conjur Cluster > Certificates > view.
- D. /opt/cyberark/dap/certs from the Conjur containers
正解:A
解説:
Explanation
Conjur uses TLS certificates for authentication between nodes and clients. These certificates are either self-signed by Conjur or imported from a third-party CA. All the certificates are stored in the
/opt/conjur/etc/ssl directory from the Conjur containers. This directory contains the following files:
ca.crt: The CA certificate used to verify all Conjur node certificates. This is either the self-signed Conjur CA certificate or the imported third-party CA certificate.
server.crt: The server certificate used by the Conjur node for HTTPS and mTLS connections. This certificate contains the DNS names of the node and the load balancer in the CN and SAN fields.
server.key: The private key corresponding to the server certificate.
cert.pem: A symbolic link to the server certificate file.
key.pem: A symbolic link to the server key file.
References: Certificate architecture, Certificate requirements, Rotate certificates Learn more:
質問 # 16
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
- A. one Follower in each AZ. load balancer for the region
- B. two Followers in each region, load balanced across all regions
- C. two Followers in each region, load balanced for the region
- D. two Followers in each AZ. load balanced for the region
正解:A
解説:
Explanation
According to the CyberArk Sentry Secrets Manager documentation, Conjur is a secrets management solution that consists of a leader node and one or more follower nodes. The leader node is responsible for managing the secrets, policies, and audit records, while the follower nodes are read-only replicas that can serve secrets requests from applications. To achieve high availability in AWS cloud infrastructure, the minimally viable Conjur deployment architecture is to have one follower in each availability zone (AZ) and a load balancer for the region. This way, if one AZ fails, the applications can still access secrets from another AZ through the load balancer. Having two followers in each region, load balanced for the region, is not enough to ensure high availability, as a regional outage can affect both followers. Having two followers in each AZ, load balanced for the region, is more than necessary, as one follower per AZ can handle the secrets requests. Having two followers in each region, load balanced across all regions, is not feasible, as Conjur does not support cross-region replication. References: 1: Conjur Architecture 2: Deploying Conjur on AWS
質問 # 17
If you rename an account or Safe, the Vault Conjur Synchronizer recreates these accounts and safes with their new name and deletes the old accounts or safes.
What does this mean?
- A. Their permissions in Coniur must also be recreated to access them.
- B. You can not rename an account or safe.
- C. Their permissions in Coniur remain the same.
- D. The Vault-Conjur Synchronizer will recreate these accounts and safes with their exact same names.
正解:A
解説:
Explanation
When an account or Safe is renamed in the Vault, the Vault Conjur Synchronizer will create new variables in Conjur with the new name and delete the old variables with the old name. This means that the permissions that were granted to the old variables in Conjur will not apply to the new variables, and they will need to be recreated using delegation policies. Otherwise, the users or hosts that had access to the old variables will not be able to access the new ones. References: Manage Accounts and Safes During Synchronization; Vault Synchronizer full policy guide
質問 # 18
Arrange the steps of a Conjur authentication flow in the correct sequence.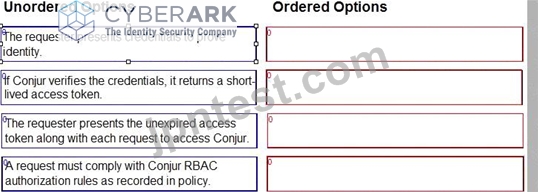
正解:
解説: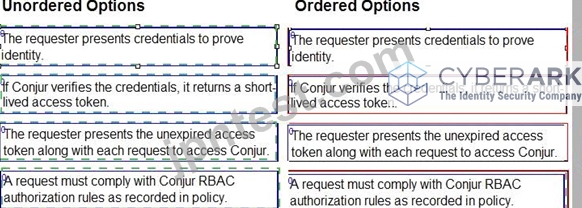
Explanation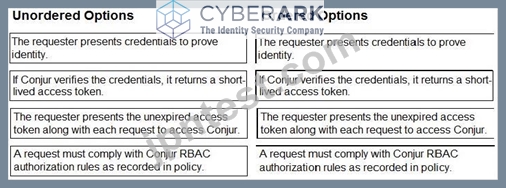
References:
CyberArk Sentry Secrets Manager
documentation: https://docs.cyberark.com/Portal/Content/Resources/_TopNav/cc_Portal.htm CyberArk Sentry Secrets Manager course materials: https://training.cyberark.com/learn CyberArk whitepapers and technical resources: https://www.cyberark.com/resources/home/cyberark-secrets-manager The authentication flow begins with the requester presenting their credentials to Conjur. This can be in the form of a username and password, an API key, or another supported method.
Conjur verifies the presented credentials against its internal database. If the credentials are valid, Conjur generates and returns a short-lived access token to the requester.
The requester includes the access token with every subsequent request to access Conjur resources. This allows Conjur to identify the requester and authorize their access to specific secrets and functionalities based on configured policies.
Finally, each request is evaluated against the Conjur RBAC (Role-Based Access Control) rules defined in its policy. These rules determine which users and roles have access to specific resources and what actions they can perform. Only requests that comply with these rules are granted access.
質問 # 19
When attempting to retrieve a credential managed by the Synchronizer, you receive this error:
What is the cause of the issue?
- A. The path to the credential was not properly encoded.
- B. The Vault Conjur Synchronizer has crashed and needs to be restarted.
- C. The Conjur Leader has lost upstream connectivity to the Vault Conjur Synchronizer.
- D. The host does not have access to the credential.
正解:D
解説:
Explanation
The cause of the issue is that the host does not have access to the credential. This can happen if the host does not have the correct permissions or if the credential is not properly configured in the Vault Conjur Synchronizer.
The Vault Conjur Synchronizer is a tool that enables the integration between CyberArk Vault and Conjur Secrets Manager Enterprise. The Synchronizer synchronizes secrets that are stored and managed in the CyberArk Vault with Conjur Enterprise, and allows them to be used via Conjur clients, APIs, and SDKs. The Synchronizer creates and updates Conjur policies and variables based on the Vault accounts and safes, and assigns permissions to Conjur hosts based on the Vault allowed machines.
To fix this issue, the host needs to have the permission to access the credential in Conjur. This can be done by adding the host to the allowed machines list of the Vault account that corresponds to the credential, and synchronizing the changes with Conjur. Alternatively, the host can be granted the permission to access the credential in Conjur by modifying the Conjur policy that corresponds to the Vault safe that contains the credential, and loading the policy to Conjur. However, this may cause conflicts or inconsistencies with the Synchronizer, and is not recommended.
For more information, see the CyberArk Vault Synchronizer docs1 and the Synchronizer Troubleshooting guide2.
質問 # 20
You start up a Follower and try to connect to it with a REST call using the server certificate, but you get an SSL connection refused error.
What could be the problem and how should you fix it?
- A. The certificate is unnecessary. Use the command option to suppress SSL certificate checking.
- B. Port 443 is blocked; open that port.
- C. One of the PostgreSQL ports (5432. 1999) is blocked by the firewall Open those ports.
- D. The certificate does not contain the Follower hostname as a Subject Alternative Name (SAN). Generate a new certificate for the Follower.
正解:D
解説:
Explanation
The correct answer is A. The certificate does not contain the Follower hostname as a Subject Alternative Name (SAN). Generate a new certificate for the Follower.
A possible explanation is:
A Follower is a read-only node that replicates data from the Leader node in a Secrets Manager cluster. A Follower can serve requests from clients and applications that need to retrieve secrets or perform other read-only operations. To connect to a Follower with a REST call, the client or application needs to use the server certificate that was generated for the Follower during the installation process. The server certificate is used to establish a secure and trusted connection between the client or application and the Follower.
However, if the server certificate does not contain the Follower hostname as a Subject Alternative Name (SAN), the connection will fail with an SSL connection refused error. This is because the SAN is an extension of the X.509 certificate standard that allows the certificate to specify multiple hostnames or IP addresses that the certificate is valid for. If the Follower hostname is not included in the SAN, the client or application will not be able to verify the identity of the Follower, and will reject the connection.
To fix this problem, a new server certificate needs to be generated for the Follower, with the Follower hostname added to the SAN. The new certificate can be generated using the openssl command or another tool that supports the SAN extension. The new certificate also needs to be signed by the same certificate authority (CA) that signed the original certificate, and the CA certificate needs to be trusted by the client or application.
The new certificate then needs to be copied to the Follower node and configured in the nginx.conf file. The Follower node also needs to be restarted for the changes to take effect.
References = Secrets Manager Cluster Installation; Secrets Manager Cluster Configuration; Subject Alternative Name - Wikipedia
質問 # 21
What does "Line of business (LOB)" represent?
- A. the services that Conjur offers and typically refers to a group of application identities in Conjur
- B. the services that Conjur offers and typically refers to the list of configured and enabled authenticators in Conjur
- C. a business group that meets a certain set of Conjur policies for entitlements and policy management
- D. a business group requiring access to secrets from the Vault/Privilege Claud to facilitate syncing accounts to Conjur
正解:A
解説:
Explanation
Line of business (LOB) is a term used by CyberArk Secrets Manager to describe the services that Conjur offers and typically refers to a group of application identities in Conjur. A LOB can be defined by a Conjur policy that grants permissions and access to secrets for a specific set of applications. For example, a LOB can represent a business unit, a project, a product, or a team within an organization. A LOB can also have sub-LOBs that inherit the permissions and secrets from the parent LOB, but can also have their own specific policies and secrets. A LOB can help organize and manage secrets for different applications in a hierarchical and scalable way. References: CyberArk Secrets Manager - Line of Business; CyberArk Secrets Manager - Policy Management; CyberArk Secrets Manager - Application Identity Management
質問 # 22
You are installing a Credential Provider on a Linux host. Arrange the installation steps in the correct sequence.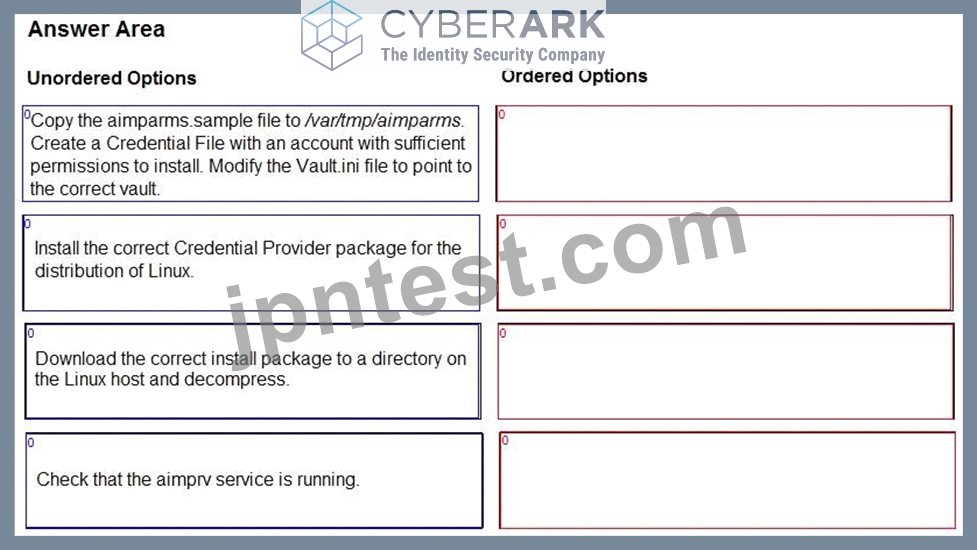
正解:
解説: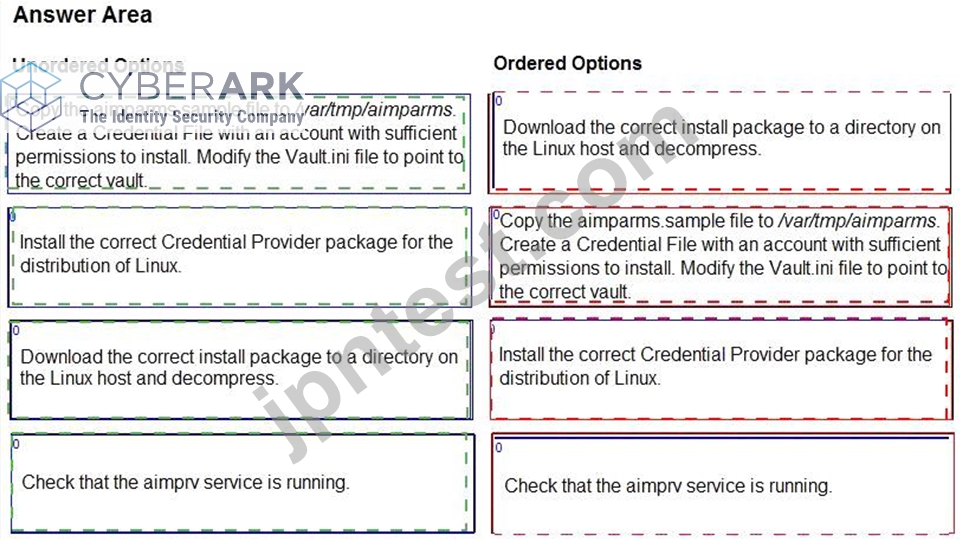
Explanation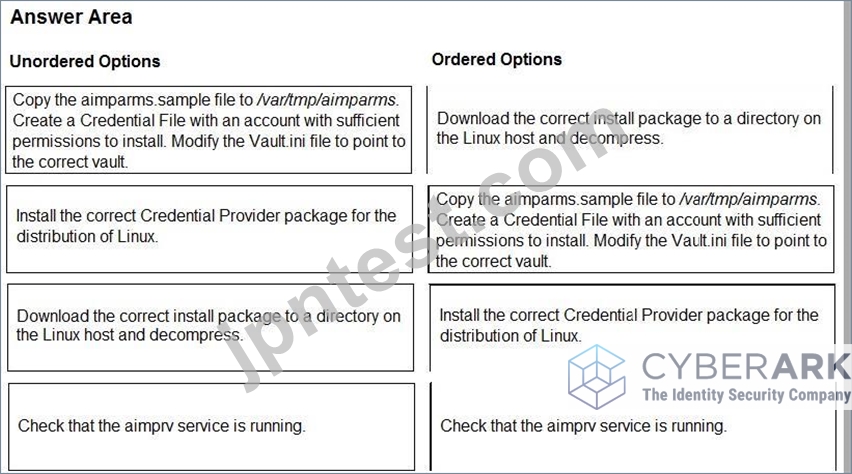
The correct sequence of installation steps for a Credential Provider on a Linux host is as follows:
Download the correct install package to a directory on the Linux host and decompress1.
Copy the aimparms.sample file to /var/tmp/aimparms. Create a Credential File with an account with sufficient permissions to install. Modify the Vault.ini file to point to the correct vault2.
Install the correct Credential Provider package for the distribution of Linux using the command: rpm
-ivh CARKaim-<version+build number>.<distribution>.rpm2.
Check that the aimprv service is running using the command: service aimprv status2.
References: 1: Download the Credential Provider 2: Install Credential Provider on Linux / AIX
質問 # 23
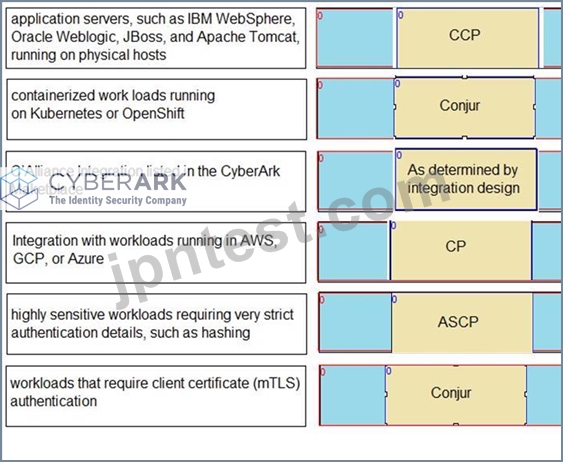
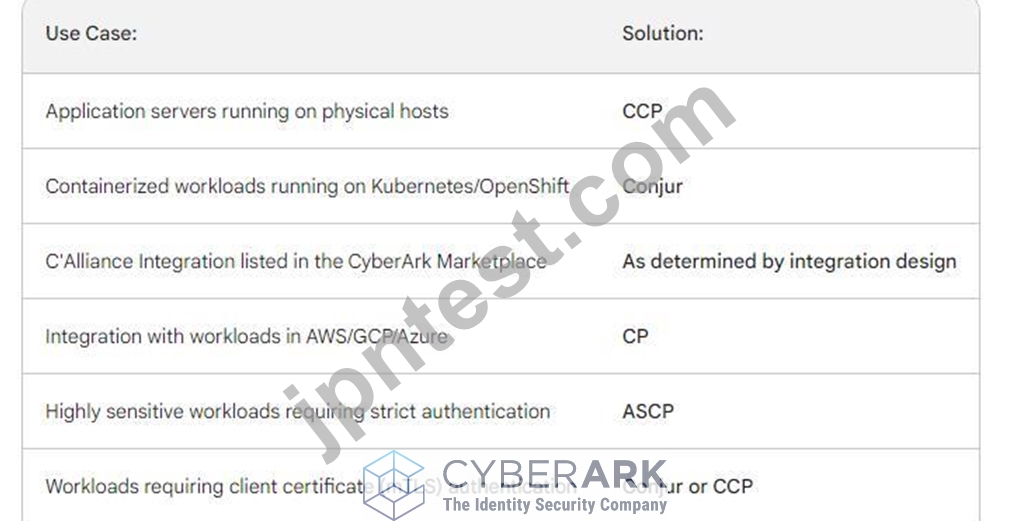
Match each use case to the appropriate Secrets Manager Solution.
正解:
解説: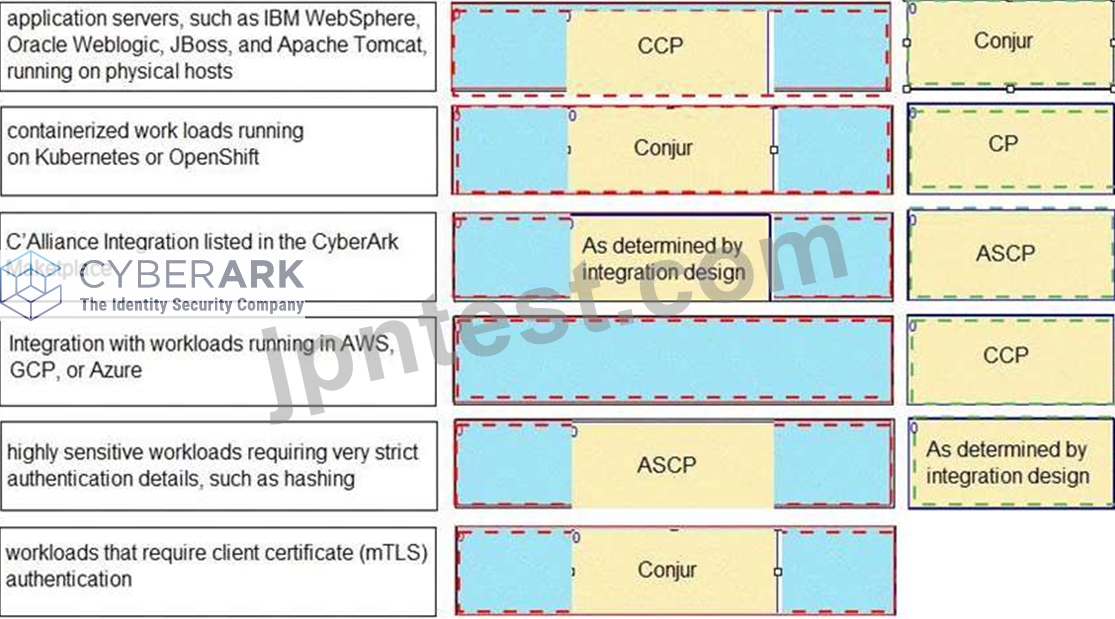
質問 # 24
A customer wants to minimize the Kubernetes application code developers must change to adopt Conjur for secrets access.
Which solutions can meet this requirement? (Choose two.)
- A. Application Server Credential Provider
- B. CPM Push-to-File
- C. Secretless
- D. Secrets Provider
- E. authn-Azure
正解:C、D
解説:
Explanation
Secrets Provider and Secretless are two solutions that can minimize the Kubernetes application code changes required to adopt Conjur for secrets access. Secrets Provider is a Kubernetes Job or Deployment that runs as an init container or application container alongside the application pod. It retrieves secrets from Conjur and writes them to one or more files in a shared, mounted volume. The application can then consume the secrets from the files without any code changes, as reading local files is a common and platform-agnostic method. Secretless is a sidecar proxy that runs as a separate container in the same pod as the application. It intercepts the application's requests to protected resources, such as databases or web services, and injects the secrets from Conjur into the requests. The application does not need to handle any secrets in its code, as Secretless handles the authentication and authorization for it. References: CyberArk Secrets Provider for Kubernetes, Secretless Broker
質問 # 25
A Kubernetes application attempting to authenticate to the Follower load balancer receives this error:
ERROR: 2024/10/30 06:07:08 authenticator.go:139: CAKC029E Received invalid response to certificate signing request. Reason: status code 401 When checking the logs, you see this message:
authn-k8s/prd-cluster-01 is not enabled
How do you remediate the issue?
- A. Enable the authenticator in the Ul > Webservices > Authenticators > Enable and enable the appropriate authenticator webservice.
- B. A network issue is preventing the application from reaching the Follower; correct the issue and verity that it is resolved.
- C. Modify conjur.conf in /opt/conjur/etc/authenticators addinqthe authenticator webservice.
- D. Check the info endpoint on each Follower behind the load balancer and enable the authenticator on the Follower.
正解:C
解説:
Explanation
The error message indicates that the authenticator webservice is not enabled on the Conjur server. To enable the authenticator, you need to modify the conjur.conf file in the /opt/conjur/etc directory and add the authenticator webservice ID to the CONJUR_AUTHENTICATORS environment variable. For example, if the authenticator webservice ID is authn-k8s/prd-cluster-01, you need to add it to the existing value of CONJUR_AUTHENTICATORS, separated by a comma. Then, you need to restart the Conjur service for the changes to take effect. This will enable the authenticator on the Conjur server and allow the Kubernetes application to authenticate to the Follower load balancer. References: Enable the Authenticator Webservice, Configure the Authenticator Webservice
質問 # 26
Which statement is correct about this message?
Message: "[number-of-deleted-rows] rows has successfully deleted "CEADBR009D Finished vacuum"?
- A. When audit retention was performed, the query on the Ul audit database (audit.db) generated an error.
- B. The Vault Conjur Synchronizer successfully deleted the password objects that were marked for deletion in the PVWA.
- C. It notes the number of records deleted from the database and does not require any action.
- D. The user specified for Conjur does not have the appropriate permissions to retrieve the audit database (audit .db).
正解:C
解説:
Explanation
This is the correct answer because the message indicates that the audit retention process has successfully completed and deleted the specified number of rows from the audit database (audit.db). The audit retention process is a scheduled task that runs periodically to delete old audit records from the audit database based on the retention period configured in the Conjur UI. The audit retention process also performs a vacuum operation to reclaim the disk space and optimize the database performance. The message does not require any action from the user, as it is a normal and expected outcome of the audit retention process. This answer is based on the CyberArk Secrets Manager documentation1 and the CyberArk Secrets Manager training course2.
The other options are not correct statements about the message. The message does not imply that the user specified for Conjur does not have the appropriate permissions to retrieve the audit database, as the message is not an error or a warning, but a confirmation of the audit retention process. The user specified for Conjur is the user that is used to connect to the Conjur server and perform operations on the Conjur resources, such as roles, policies, secrets, and audit records. The user specified for Conjur needs to have the appropriate permissions to access the audit database, but the message does not indicate any problem with the user permissions.
The message does not imply that when audit retention was performed, the query on the UI audit database generated an error, as the message is not an error or a warning, but a confirmation of the audit retention process. The query on the UI audit database is the query that is used to display the audit records in the Conjur UI. The query on the UI audit database is not related to the audit retention process, which is a background task that runs on the Conjur server and deletes the old audit records from the audit database. The message does not indicate any problem with the query on the UI audit database.
The message does not imply that the Vault Conjur Synchronizer successfully deleted the password objects that were marked for deletion in the PVWA, as the message is not related to the Vault Conjur Synchronizer or the password objects. The Vault Conjur Synchronizer is a service that synchronizes secrets from the CyberArk Vault to the Conjur database. The password objects are the accounts in the CyberArk Vault that store the credentials for various platforms and devices. The message is related to the audit retention process, which deletes the old audit records from the audit database. The message does not indicate any problem or action with the Vault Conjur Synchronizer or the password objects.
質問 # 27
When working with Summon, what is the purpose of the secrets.yml file?
- A. It is where you store the Conjur URL and host API key.
- B. It is where Summon outputs the secret value after retrieval.
- C. It is where you define which secrets to retrieve.
- D. It is the log file for Summon.
正解:C
解説:
Explanation
= Summon is a command-line tool that provides on-demand secrets access for common DevOps tools. It reads a file in secrets.yml format and injects secrets as environment variables into any process. The secrets.yml file is where you define which secrets to retrieve from a trusted store, such as CyberArk Secrets Manager. The secrets.yml file specifies the name and location of each secret, as well as the environment variable to assign it to. For example, a secrets.yml file could look like this:
DB_USERNAME: !var dev/my-app/db-username DB_PASSWORD: !var dev/my-app/db-password This means that Summon will fetch the values of dev/my-app/db-username and dev/my-app/db-password from the trusted store, and assign them to the environment variables DB_USERNAME and DB_PASSWORD, respectively. Then, Summon will run the specified process with these environment variables set, and remove them once the process exits. This way, Summon enables secure and convenient access to secrets without exposing them in plain text or storing them in files.
References = Summon by cyberark - GitHub Pages; Using Summon to Manage Secrets as You Move From Dev to Prod
質問 # 28
Arrange the steps to configure authenticators in the correct the sequence.
正解:
解説:
Explanation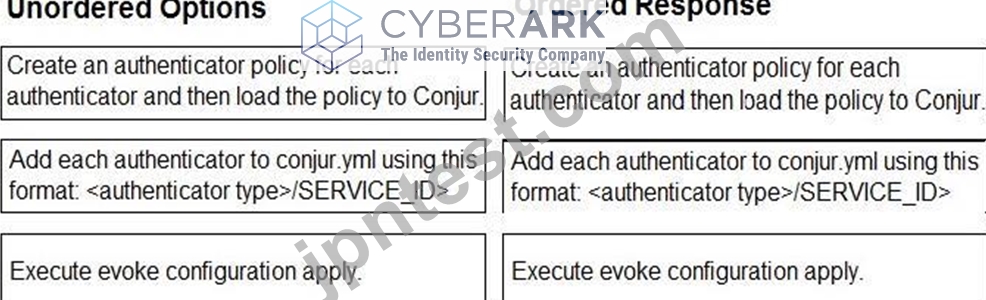
Create an authenticator policy for each authenticator and then load the policy to Conjur.
Add each authenticator to conjur.yml using this format: <authenticator type> <SERVICE_ID>.
Execute evoke configuration apply.
Comprehensive Explanation: Authenticators are plugins that enable Conjur to authenticate requests from different types of clients, such as Kubernetes, Azure, or LDAP. To configure authenticators, you need to follow these steps:
Create an authenticator policy for each authenticator and then load the policy to Conjur. This step defines the authenticator as a resource in Conjur and grants permissions to the users or hosts that can use it. You can use the policy templates provided by Conjur for each authenticator type, or create your own custom policy. For more information, see Define Authenticator Policy.
Add each authenticator to conjur.yml using this format: <authenticator type> <SERVICE_ID>. This step enables the authenticator service on the Conjur server and specifies the service ID that identifies the authenticator instance. The service ID must match the one used in the policy. For more information, see Enable Authenticators.
Execute evoke configuration apply. This step applies the changes made to the conjur.yml file and restarts the Conjur service. This is necessary for the authenticator configuration to take effect. For more information, see Apply Configuration Changes.
References: The steps to configure authenticators are explained in detail in the Configure Authenticators section of the CyberArk Conjur Enterprise documentation. The image in the question is taken from the same source.
質問 # 29
In the event of a failover of the Vault server from the primary to the DR, which configuration option ensures that a CP will continue being able to refresh its cache?
- A. In the Conjur UI, add the IP address of the DR Vault in the Disaster Recovery section under Cluster Config > Credential Provider > Options.
- B. Add the IP address of the DR vault to the "Address" parameter in the file Vault.ini.file on the machine on which the CP is installed.
- C. In the Password Vault Web Access UI, add the IP address of the DR Vault in the Disaster Recovery section under Applications > Options.
- D. Add the DR Vault IP address to the "Address" parameter in the file main_appprovider.conf.
<platform>.<version> found in the AppProviderConf safe.
正解:B
解説:
Explanation
This is the correct answer because the Vault.ini file on the CP machine contains the configuration settings for the CP to connect to the Vault server. The Address parameter specifies the IP address or hostname of the Vault server that the CP will use to communicate with the Vault. In the event of a failover of the Vault server from the primary to the DR, the CP needs to update the Address parameter with the IP address of the DR Vault server in order to continue being able to refresh its cache. The cache is a local storage of credentials that the CP retrieves from the Vault and provides to the applications. The cache is refreshed periodically based on the RefreshInterval parameter in the Vault.ini file. This answer is based on the CyberArk Secrets Manager documentation1 and the CyberArk Secrets Manager training course2.
The other options are not correct because they do not ensure that the CP will continue being able to refresh its cache in the event of a failover of the Vault server from the primary to the DR. Adding the DR Vault IP address to the Address parameter in the main_appprovider.conf.<platform>.<version> file in the AppProviderConf safe is not a valid option, as this file does not contain the Address parameter. The main_appprovider.conf file contains the configuration settings for the basic provider, such as the AppProviderVaultParmsFile, the AppProviderPort, and the AppProviderCacheMode. The Address parameter is only found in the Vault.ini file on the CP machine.
In the Password Vault Web Access (PVWA) UI, adding the IP address of the DR Vault in the Disaster Recovery section under Applications > Options is not a valid option, as this section does not exist in the PVWA UI. The PVWA UI does not have a Disaster Recovery section under Applications > Options. The PVWA UI has a Disaster Recovery section under Administration > Options, but this section is used to configure the DR Vault settings, such as the DR Vault IP address, the DR Vault user, and the DR Vault password. These settings are not related to the CP configuration or cache refresh.
In the Conjur UI, adding the IP address of the DR Vault in the Disaster Recovery section under Cluster Config
> Credential Provider > Options is not a valid option, as this section does not exist in the Conjur UI. The Conjur UI does not have a Cluster Config, Credential Provider, or Options section. The Conjur UI has a Cluster Config section under Settings, but this section is used to configure the Conjur cluster settings, such as the master IP address, the follower IP address, and the seed fetcher IP address. These settings are not related to the CP configuration or cache refresh.
質問 # 30
Refer to the exhibit.
In which example will auto-failover occur?
- A.

- B.

- C.
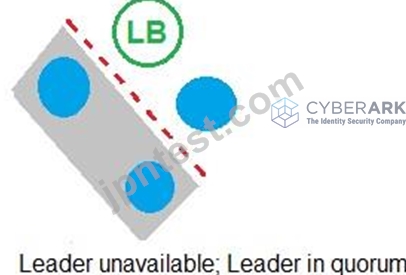
- D.

正解:C
解説:
Explanation
According to the CyberArk Sentry Secrets Manager documentation, auto-failover is a feature that enables the automatic promotion of a standby node to a leader node in case of a leader failure. Auto-failover requires a quorum, which is a majority of nodes in the cluster that are available and synchronized. A quorum ensures that only one node can be promoted to a leader at a time and prevents split-brain scenarios. In the exhibit, each option shows a network diagram of a load balancer and four nodes, one of which is crossed out with a red X, indicating a leader failure. The text below each diagram indicates whether there is a quorum or not. Option C is the only example where auto-failover will occur, because there is a quorum of three out of four nodes, and one of the standby nodes can be promoted to a leader. Option A will not have auto-failover, because there is no quorum, as only two out of four nodes are available. Option B will not have auto-failover, because there is no quorum, as only one out of four nodes is available. Option D will not have auto-failover, because there is no quorum, as none of the nodes are available. References: 1: Auto-failover 2: Configure auto-failover
質問 # 31
A customer has 100 .NET applications and wants to use Summon to invoke the application and inject secrets at run time.
Which change to the NET application code might be necessary to enable this?
- A. It must be changed to access secrets from a configuration file or environment variable.
- B. No changes are needed as Summon brokers the connection between the application and the backend data source through impersonation.
- C. It must be changed to include the REST API calls necessary to retrieve the needed secrets from the CCP.
- D. It must be changed to include the host API key necessary for Summon to retrieve the needed secrets from a Follower
正解:A
解説:
Explanation
Summon is a utility that allows applications to access secrets from a variety of trusted stores and export them as environment variables to a sub-process environment. Summon does not require any changes to the application code to retrieve secrets from the CyberArk Central Credential Provider (CCP), as it uses a provider plugin that handles the communication with the CCP. However, the application code must be able to access secrets from a configuration file or environment variable, as these are the methods that Summon uses to inject secrets into the application. Summon reads a secrets.yml file that defines the secrets that the application needs and maps them to environment variables. Then, Summon fetches the secrets from the CCP using the provider plugin and exports them as environment variables to the application sub-process. The application can then read the secrets from the environment variables as if they were hard-coded in the configuration file. References: Summon-inject secrets, .NET Application Password SDK
質問 # 32
Refer to the exhibit.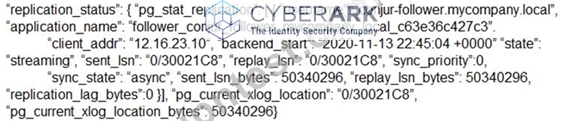
How can you confirm that the Follower has a current copy of the database?
- A. Compare the pgcurrentxlog_locationlocation from the Leader to the Follower you need to validate against.
- B. Retrieve the credential from a test application on the Leader cluster; then retrieve against the Follower and compare if they are accurate.
- C. Validate that the Follower container ID matches the node in the info endpoint on the Leader.
- D. Count the number of components in pgstartreplication and compare this to the total number of Followers in the deployment.
正解:A
解説:
Explanation
The exhibit shows a JSON object that contains the replication status of a database in a Secrets Manager cluster. Secrets Manager is a secrets management solution that securely stores and manages secrets and credentials used by applications, DevOps tools, and other systems. Secrets Manager can be deployed in a cluster mode, which consists of a Leader node and one or more Follower nodes. The Leader node is the primary node that handles all write operations and coordinates the replication of data to the Follower nodes.
The Follower nodes are read-only nodes that replicate data from the Leader node and serve requests from clients and applications that need to retrieve secrets or perform other read-only operations.
To confirm that the Follower has a current copy of the database, you can compare the pgcurrentxlog_locationlocation from the Leader to the Follower you need to validate against. The pgcurrentxlog_locationlocation is a property that indicates the current position of the write-ahead log (WAL) in the database. The WAL is a mechanism that records all changes made to the database in a sequential log file, before they are applied to the actual data files. The WAL ensures the durability and consistency of the database in case of a crash or a power failure. The WAL also enables the replication of data from the Leader node to the Follower nodes, by streaming the WAL records to the Follower nodes and applying them to their local databases.
By comparing the pgcurrentxlog_locationlocation from the Leader to the Follower, you can determine how far behind the Follower is from the Leader in terms of the WAL records. If the pgcurrentxlog_locationlocation values are identical or very close, it means that the Follower has a current copy of the database, and that the replication is working properly. If the pgcurrentxlog_locationlocation values are different or far apart, it means that the Follower has an outdated copy of the database, and that there is a replication lag or a replication failure. In that case, you may need to troubleshoot the replication issue and resolve it as soon as possible.
References = Secrets Manager Cluster Installation; Secrets Manager Cluster Configuration; Write-Ahead Logging - PostgreSQL Documentation
質問 # 33
You are diagnosing this log entry:
From Conjur logs: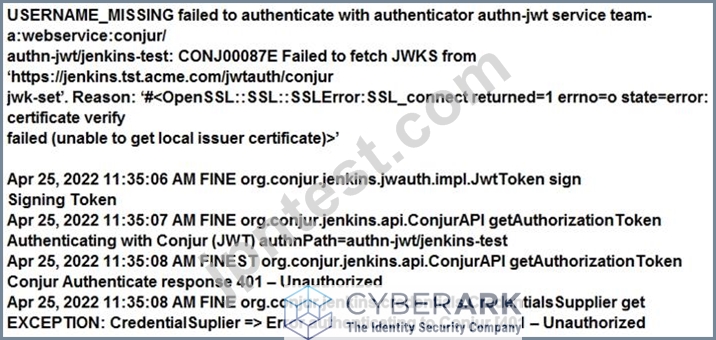
Given these errors, which problem is causing the breakdown?
- A. The Jenkins certificate is malformed and will not be trusted by Conjur.
- B. The Conjur certificate chain is not trusted by Jenkins.
- C. The Jenkins certificate chain is not trusted by Conjur.
- D. The JWT sent by Jenkins does not match the Conjur host annotations.
正解:C
解説:
Explanation
The log entry shows a failed authentication attempt with Conjur using the authn-jwt method. This method allows applications to authenticate with Conjur using JSON Web Tokens (JWTs) that are signed by a trusted identity provider. In this case, the application is Jenkins, which is a CI/CD tool that can integrate with Conjur using the Conjur Jenkins plugin. The plugin allows Jenkins to securely retrieve secrets from Conjur and inject them as environment variables into Jenkins pipelines or projects.
The log entry indicates that the JWT sent by Jenkins was rejected by Conjur because of an SSL connection error. The error message says that the certificate chain of Jenkins could not be verified by Conjur, and that the certificate authority (CA) that signed the Jenkins certificate was unknown to Conjur. This means that the Jenkins certificate chain is not trusted by Conjur, and that Conjur does not have the CA certificate of Jenkins in its trust store. Therefore, Conjur cannot establish a secure and trusted connection with Jenkins, and cannot validate the JWT signature.
To fix this problem, the Jenkins certificate chain needs to be trusted by Conjur. This can be done by copying the CA certificate of Jenkins to the Conjur server, and adding it to the Conjur trust store. The Conjur trust store is a directory that contains the CA certificates of the trusted identity providers for the authn-jwt method. The Conjur server also needs to be restarted for the changes to take effect.
References = Conjur Jenkins Plugin; Conjur JWT Authentication; Conjur Trust Store
質問 # 34
During the configuration of Conjur, what is a possible deployment scenario?
- A. The Conjur Leader cluster is deployed outside of a Kubernetes environment; Followers can run inside or outside the environment.
- B. The Leader cluster is deployed outside a Kubernetes environment; Followers and Standbys can run inside or outside the environment.
- C. The Conjur Leader cluster and Followers are deployed inside a Kubernetes environment.
- D. The Leader and Followers are deployed outside of a Kubernetes environment; Slandbys can run inside a Kubernetes environment.
正解:B
質問 # 35
You are setting up a Kubernetes integration with Conjur. With performance as the key deciding factor, namespace and service account will be used as identity characteristics.
Which authentication method should you choose?
- A. Certificate-based authentication
- B. API key authentication
- C. JWT-based authentication
- D. Connect (OIDC) authentication
正解:C
解説:
Explanation
According to the CyberArk Sentry Secrets Manager documentation, JWT-based authentication is the recommended method for authenticating Kubernetes pods with Conjur. JWT-based authentication uses JSON Web Tokens (JWTs) that are issued by the Kubernetes API server and signed by its private key. The JWTs contain the pod's namespace and service account as identity characteristics, which are verified by Conjur against a policy that defines the allowed namespaces and service accounts. JWT-based authentication is fast, scalable, and secure, as it does not require any additional certificates, secrets, or sidecars to be deployed on the pods. JWT-based authentication also supports rotation and revocation of the Kubernetes API server's private key, which enhances the security and resilience of the authentication process.
Certificate-based authentication is another method for authenticating Kubernetes pods with Conjur, but it is not the best option for performance. Certificate-based authentication uses X.509 certificates that are generated by a Conjur CA service and injected into the pods as Kubernetes secrets. The certificates contain the pod's namespace and service account as identity characteristics, which are verified by Conjur against a policy that defines the allowed namespaces and service accounts. Certificate-based authentication is secure and reliable, but it requires more resources and steps to generate, inject, and manage the certificates and secrets.
Certificate-based authentication also does not support rotation and revocation of the certificates, which may pose a security risk if the certificates are compromised or expired.
API key authentication and Connect (OIDC) authentication are not valid methods for authenticating Kubernetes pods with Conjur. API key authentication is used for authenticating hosts, users, and applications that have a Conjur identity and an API key. Connect (OIDC) authentication is used for authenticating users and applications that have an OpenID Connect identity and a token. These methods are not suitable for Kubernetes pods, as they do not use the pod's namespace and service account as identity characteristics, and they require additional secrets or tokens to be stored and managed on the pods. References: = JWT Authenticator | CyberArk Docs; Certificate Authenticator | CyberArk Docs; API Key Authenticator | CyberArk Docs; Connect Authenticator | CyberArk Docs
質問 # 36
When attempting to configure a Follower, you receive the error:
Which port is the problem?
- A. 0
- B. 1
- C. 2
- D. 3
正解:B
解説:
Explanation
The error message "psql: server closed the connection unexpectedly" means that the server terminated abnormally before or while processing the request. This is likely due to the Leader Load Balancer not being available on the port and replication cannot be established. The port that is the problem is 5432, which is the default port for PostgreSQL database connections. The Follower needs to connect to the Leader Load Balancer on this port to receive the replication data from the Leader. If the port is blocked or unreachable, the Follower will fail to sync with the Leader and display the error message. References: [Set up Follower], [Troubleshoot Follower]
質問 # 37
An application is having authentication issues when trying to securely retrieve credential's from the Vault using the CCP webservices RESTAPI. CyberArk Support advised that further debugging should be enabled on the CCP server to output a trace file to review detailed logs to help isolate the problem.
What best describes how to enable debug for CCP?
- A. In the PVWA, go to the Applications tab, select the Application in question, go to Options > Logging and choose Debug.
- B. Edit web.config. change the "AIMWebServiceTrace" value, restart Windows Web Server (IIS)
- C. Edit the basic_appprovider.conf, change the "AIMWebServiceTrace" value, and restart the provider.
- D. From the command line, run appprvmgr.exe update_config logging=debug.
正解:B
解説:
Explanation
The best way to enable debug for CCP is to edit the web.config file in the AIMWebService folder and change the value of the AIMWebServiceTrace parameter to 4, which is the verbose level. This will generate detailed logs in the AIMWSTrace.log file in the logs folder. The logs folder may need to be created manually and given the appropriate permissions for the IIS_IUSRS group. After changing the web.config file, the Windows Web Server (IIS) service needs to be restarted to apply the changes. This method is recommended by CyberArk Support and documented in the CyberArk Knowledge Base1.
Editing the basic_appprovider.conf file and changing the AIMWebServiceTrace value is not a valid option, as this parameter does not exist in this file. The basic_appprovider.conf file is used to configure the basic provider settings, such as the AppProviderVaultParmsFile, the AppProviderPort, and the AppProviderCacheMode. The AIMWebServiceTrace parameter is only found in the web.config file of the AIMWebService.
In the PVWA, going to the Applications tab, selecting the Application in question, and going to Options > Logging and choosing Debug is not a valid option, as this will only enable debug for the Application Identity Manager (AIM) component, not the CCP component. The AIM component is used to manage the application identities and their access to the Vault. The CCP component is used to provide secure retrieval of credentials from the Vault using web services. Enabling debug for AIM will generate logs in the APPconsole.log, APPtrace.log, and APPaudit.log files in the ApplicationPasswordProvider\Logs folder, but these logs will not help to troubleshoot the CCP authentication issues.
From the command line, running appprvmgr.exe update_config logging=debug is not a valid option, as this will only enable debug for the Application Provider Manager (APM) component, not the CCP component. The APM component is used to manage the configuration and operation of the providers, such as the basic provider, the LDAP provider, and the ENE provider. Running appprvmgr.exe update_config logging=debug will generate logs in the appprvmgr.log file in the ApplicationPasswordProvider\Logs folder, but these logs will not help to troubleshoot the CCP authentication issues. References:
Enable Debugging and Gather Logs - Central Credential Provider1
質問 # 38
......
Secret-Sen問題集レビュー専門クイズで学習材料:https://www.jpntest.com/shiken/Secret-Sen-mondaishu
