2024年04月 CyberArk Secret-Sen実際にある問題と100%カバー率リアル試験問題
Secret-Sen無料試験問題と解答PDF最新問題2024年04月
質問 # 20
When attempting to retrieve a credential, you receive an error 401 - Malformed Authorization Token.
What is the cause of the issue?
- A. The credential has not been initialized.
- B. The host does not have access to the credential with the current token.
- C. The token you are trying to retrieve does not exist.
- D. The token is not correctly encoded.
正解:D
解説:
Explanation
= The cause of the issue is that the token is not correctly encoded. A token is a string of characters that represents a credential or an authorization grant for accessing a resource. A token must be encoded according to a specific format and standard, such as Base64, JSON Web Token (JWT), or OAuth 2.0. If the token is malformed, meaning that it does not follow the expected format or standard, the server will reject the token and return an error 401 - Malformed Authorization Token. This error indicates that the token is invalid or expired, and the request is unauthorized. To resolve the issue, the token must be regenerated or refreshed using the correct encoding method and parameters12. References: = CyberArk Identity: Getting 401 unauthorized Error when using API calls with OAuth2 Client 2, Resolution 1 Troubleshoot CyberArk Vault Synchronizer 1, Error: Forbidden Logon Token is Empty - Cannot logon Unauthorized
質問 # 21
Refer to the exhibit.
In which example will auto-failover occur?
- A.

- B.

- C.
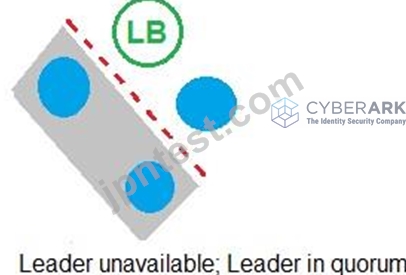
- D.

正解:C
解説:
Explanation
According to the CyberArk Sentry Secrets Manager documentation, auto-failover is a feature that enables the automatic promotion of a standby node to a leader node in case of a leader failure. Auto-failover requires a quorum, which is a majority of nodes in the cluster that are available and synchronized. A quorum ensures that only one node can be promoted to a leader at a time and prevents split-brain scenarios. In the exhibit, each option shows a network diagram of a load balancer and four nodes, one of which is crossed out with a red X, indicating a leader failure. The text below each diagram indicates whether there is a quorum or not. Option C is the only example where auto-failover will occur, because there is a quorum of three out of four nodes, and one of the standby nodes can be promoted to a leader. Option A will not have auto-failover, because there is no quorum, as only two out of four nodes are available. Option B will not have auto-failover, because there is no quorum, as only one out of four nodes is available. Option D will not have auto-failover, because there is no quorum, as none of the nodes are available. References: 1: Auto-failover 2: Configure auto-failover
質問 # 22
You are setting up the Secrets Provider for Kubernetes to support rotation with Push-to-File mode.
Which deployment option should be used?
- A. Application container
- B. Init container
- C. Service Broker
- D. Sidecar
正解:D
解説:
Explanation
According to the CyberArk Sentry Secrets Manager documentation, the Secrets Provider for Kubernetes can be deployed as an init container or a sidecar in Push-to-File mode. In Push-to-File mode, the Secrets Provider pushes Conjur secrets to one or more secrets files in a shared volume in the same Pod as the application container. The application container can then consume the secrets files from the shared volume. The deployment option that should be used to support rotation with Push-to-File mode is the sidecar, because the sidecar can run continuously and check for updates to the secrets in Conjur. If changes are detected, the sidecar can update the secrets files in the shared volume. The init container, on the other hand, runs to completion and does not support rotation. The application container and the service broker are not valid deployment options for the Secrets Provider for Kubernetes in Push-to-File mode. References: 1: Secrets Provider - Init container/Sidecar - Push-to-File mode 2: Secrets Provider - init container/sidecar - Push-to-File mode
質問 # 23
Which statement is correct about this message?
Message: "[number-of-deleted-rows] rows has successfully deleted "CEADBR009D Finished vacuum"?
- A. The user specified for Conjur does not have the appropriate permissions to retrieve the audit database (audit .db).
- B. When audit retention was performed, the query on the Ul audit database (audit.db) generated an error.
- C. The Vault Conjur Synchronizer successfully deleted the password objects that were marked for deletion in the PVWA.
- D. It notes the number of records deleted from the database and does not require any action.
正解:D
解説:
Explanation
This is the correct answer because the message indicates that the audit retention process has successfully completed and deleted the specified number of rows from the audit database (audit.db). The audit retention process is a scheduled task that runs periodically to delete old audit records from the audit database based on the retention period configured in the Conjur UI. The audit retention process also performs a vacuum operation to reclaim the disk space and optimize the database performance. The message does not require any action from the user, as it is a normal and expected outcome of the audit retention process. This answer is based on the CyberArk Secrets Manager documentation1 and the CyberArk Secrets Manager training course2.
The other options are not correct statements about the message. The message does not imply that the user specified for Conjur does not have the appropriate permissions to retrieve the audit database, as the message is not an error or a warning, but a confirmation of the audit retention process. The user specified for Conjur is the user that is used to connect to the Conjur server and perform operations on the Conjur resources, such as roles, policies, secrets, and audit records. The user specified for Conjur needs to have the appropriate permissions to access the audit database, but the message does not indicate any problem with the user permissions.
The message does not imply that when audit retention was performed, the query on the UI audit database generated an error, as the message is not an error or a warning, but a confirmation of the audit retention process. The query on the UI audit database is the query that is used to display the audit records in the Conjur UI. The query on the UI audit database is not related to the audit retention process, which is a background task that runs on the Conjur server and deletes the old audit records from the audit database. The message does not indicate any problem with the query on the UI audit database.
The message does not imply that the Vault Conjur Synchronizer successfully deleted the password objects that were marked for deletion in the PVWA, as the message is not related to the Vault Conjur Synchronizer or the password objects. The Vault Conjur Synchronizer is a service that synchronizes secrets from the CyberArk Vault to the Conjur database. The password objects are the accounts in the CyberArk Vault that store the credentials for various platforms and devices. The message is related to the audit retention process, which deletes the old audit records from the audit database. The message does not indicate any problem or action with the Vault Conjur Synchronizer or the password objects.
質問 # 24
What is a main advantage of using dual accounts in password management?
- A. Since there are two active accounts, it doubles the probability that a system, database, or application will successfully authenticate.
- B. It ensures passwords are rotated every 90 days, which respects the expected downtime for a system, database, or application
- C. It ensures no delays are incurred when the application needs credentials because a password that is currently used by an application will never be changed
- D. Since passwords are cached for both rotation accounts, it ensures the password for an application will not be changed, reducing the amount of blackout dates when a password expires.
正解:C
解説:
Explanation
Dual accounts is a password management method that uses two accounts with identical privileges to access a system, database, or application. One account is active and the other is inactive at any given time. The active account remains untouched during password rotation, while the inactive account has its password changed after a grace period. This way, the application can always use the active account without experiencing any delays or errors due to password expiration or change. The advantage of using dual accounts is that it ensures business continuity and seamless access to the target resource, especially for high load and critical applications. References: Manage Dual Accounts, Configure dual accounts
質問 # 25
In the event of a failover of the Vault server from the primary to the DR, which configuration option ensures that a CP will continue being able to refresh its cache?
- A. Add the DR Vault IP address to the "Address" parameter in the file main_appprovider.conf.
<platform>.<version> found in the AppProviderConf safe. - B. In the Conjur UI, add the IP address of the DR Vault in the Disaster Recovery section under Cluster Config > Credential Provider > Options.
- C. In the Password Vault Web Access UI, add the IP address of the DR Vault in the Disaster Recovery section under Applications > Options.
- D. Add the IP address of the DR vault to the "Address" parameter in the file Vault.ini.file on the machine on which the CP is installed.
正解:D
解説:
Explanation
This is the correct answer because the Vault.ini file on the CP machine contains the configuration settings for the CP to connect to the Vault server. The Address parameter specifies the IP address or hostname of the Vault server that the CP will use to communicate with the Vault. In the event of a failover of the Vault server from the primary to the DR, the CP needs to update the Address parameter with the IP address of the DR Vault server in order to continue being able to refresh its cache. The cache is a local storage of credentials that the CP retrieves from the Vault and provides to the applications. The cache is refreshed periodically based on the RefreshInterval parameter in the Vault.ini file. This answer is based on the CyberArk Secrets Manager documentation1 and the CyberArk Secrets Manager training course2.
The other options are not correct because they do not ensure that the CP will continue being able to refresh its cache in the event of a failover of the Vault server from the primary to the DR. Adding the DR Vault IP address to the Address parameter in the main_appprovider.conf.<platform>.<version> file in the AppProviderConf safe is not a valid option, as this file does not contain the Address parameter. The main_appprovider.conf file contains the configuration settings for the basic provider, such as the AppProviderVaultParmsFile, the AppProviderPort, and the AppProviderCacheMode. The Address parameter is only found in the Vault.ini file on the CP machine.
In the Password Vault Web Access (PVWA) UI, adding the IP address of the DR Vault in the Disaster Recovery section under Applications > Options is not a valid option, as this section does not exist in the PVWA UI. The PVWA UI does not have a Disaster Recovery section under Applications > Options. The PVWA UI has a Disaster Recovery section under Administration > Options, but this section is used to configure the DR Vault settings, such as the DR Vault IP address, the DR Vault user, and the DR Vault password. These settings are not related to the CP configuration or cache refresh.
In the Conjur UI, adding the IP address of the DR Vault in the Disaster Recovery section under Cluster Config
> Credential Provider > Options is not a valid option, as this section does not exist in the Conjur UI. The Conjur UI does not have a Cluster Config, Credential Provider, or Options section. The Conjur UI has a Cluster Config section under Settings, but this section is used to configure the Conjur cluster settings, such as the master IP address, the follower IP address, and the seed fetcher IP address. These settings are not related to the CP configuration or cache refresh.
質問 # 26
When loading policy, you receive a 422 Response from Conjur with a message.
What could cause this issue?
- A. malformed Policy file
- B. misconfigured Load Balancer health check
- C. incorrect Vault Conjur Synchronizer URL
- D. incorrect Leader URL
正解:A
解説:
Explanation
The most likely cause for this issue is A. malformed Policy file. A 422 Response from Conjur indicates that the request was well-formed but was unable to be followed due to semantic errors. A common semantic error when loading policy is having a malformed Policy file, which means that the Policy file does not follow the correct syntax, structure, or logic of the Conjur Policy language. A malformed Policy file can result from typos, missing or extra characters, incorrect indentation, invalid references, or other mistakes that prevent Conjur from parsing and applying the Policy file. The message that accompanies the 422 Response will usually provide more details about the error and the location of the problem in the Policy file.
To resolve this issue, you should review the Policy file and check for any errors or inconsistencies. You can use a YAML validator or a text editor with syntax highlighting to help you identify and correct any syntax errors. You can also use the Conjur Policy Simulator to test and debug your Policy file before loading it to Conjur. The Conjur Policy Simulator is a web-based tool that allows you to upload your Policy file and see how it will affect the Conjur data model, without actually loading it to Conjur. You can also use the Conjur Policy Simulator to compare different versions of your Policy file and see the changes and conflicts between them. For more information, refer to the following resources:
Policy - CyberArk, Section "Policy"
Policy Language - CyberArk, Section "Policy Language"
Conjur Policy Simulator - CyberArk, Section "Conjur Policy Simulator"
質問 # 27
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
- A. The service account running the application does not have the correct permissions on the safe.
- B. The OS user does not have the correct permissions on the safe
- C. The client certificate fingerprint is not trusted.
- D. The application ID or Application Provider does not have the correct permissions on the safe.
正解:D
解説:
Explanation
The most likely cause for this issue is A. The application ID or Application Provider does not have the correct permissions on the safe. The CyberArk Central Credential Provider (CCP) is a web service that enables applications to retrieve secrets from the CyberArk Vault using REST API calls. The CCP requires an application ID or an Application Provider to authenticate and authorize the application before returning the requested secret. The application ID or Application Provider must have the Retrieve and List permissions on the safe where the secret is stored, otherwise the CCP will not be able to find the matching secret and will return an error.
To resolve this issue, you should verify that the application ID or Application Provider has the correct permissions on the safe, and that the safe name and object name are correctly specified in the REST API call.
You can use the CyberArk Privileged Access Security Web Access (PVWA) or the PrivateArk Client to check and modify the permissions on the safe. You can also use the CyberArk REST API Tester or a tool like Postman to test the REST API call and see the response from the CCP. For more information, refer to the following resources:
Credential Providers - Centralized Credential Management | CyberArk, Section "Central Credential Provider" Credential Provider - CyberArk, Section "Using the Credential Provider" How to Build Your Secrets Management REST API's into Postman, Section "How to Build Your Secrets Management REST API's into Postman"
質問 # 28
While installing the first CP in an environment, errors that occurred when the environment was created are displayed; however, the installation procedure continued and finished successfully.
What should you do?
- A. Run setup.exe again and select 'Recreate Vault Environment'. Provide the details of a user with more privileges when prompted by the installer.
- B. Continue configuring the application to use the CP. No further action is needed since the successful installation makes the error message benign.
- C. Review the PV WA lags to determine which REST API call used during the installation failed.
- D. Review the lag file 'CreateEnv.loq' and investigate any error messages it contains.
正解:D
解説:
Explanation
B: Review the log file 'CreateEnv.log' and investigate any error messages it contains.
This is the best option because the CreateEnv.log file records the steps and results of creating the CP environment in the Vault during the installation. The CP environment includes the safe, the provider user, the application user, and the application identity. If any errors occurred when creating the CP environment, they will be logged in this file and may indicate a problem with the Vault connection, the credential file, the permissions, or the configuration. Reviewing the log file can help to identify and resolve the root cause of the errors and ensure the CP environment is properly set up.
Continuing configuring the application to use the CP without further action is not a good option because it may lead to unexpected or inconsistent behavior of the CP or the application. The errors that occurred when creating the CP environment may affect the security, availability, or integrity of the credentials or the application. Ignoring the errors may also make it harder to troubleshoot or fix them later.
Running setup.exe again and selecting 'Recreate Vault Environment' is not a good option because it may overwrite or delete the existing CP environment and cause more errors or conflicts. Recreating the Vault environment should only be done after reviewing the log file and understanding the cause of the errors.
Moreover, recreating the Vault environment may require more privileges than creating it for the first time, as some objects may be already in use or locked.
Reviewing the PVWA logs to determine which REST API call used during the installation failed is not a good option because it may not provide enough information or context to understand or resolve the errors. The PVWA logs may show the HTTP status codes or messages of the REST API calls, but they may not show the details or parameters of the calls or the responses. The PVWA logs may also contain other unrelated or irrelevant entries that may confuse or distract from the errors. The CreateEnv.log file is a more specific and reliable source of information for the errors that occurred when creating the CP environment.
質問 # 29
When installing the CCP and configuring it for use behind a load balancer, which authentication methods may be affected? (Choose two.)
- A. Allowed Machines authentication
- B. Path
- C. Hash
- D. [Client Certificate authentication
- E. OS User
正解:A、D
解説:
Explanation
The CCP (Central Credential Provider) is a tool that enables applications to securely retrieve credentials from CyberArk Secrets Manager without hard-coding or storing them in files. The CCP can be installed on a single server or on multiple servers behind a load balancer for high availability and scalability. The load balancer is a device or service that distributes the network traffic among the CCP servers based on predefined rules and criteria.
The CCP supports multiple methods to authenticate applications, such as Allowed Machines, Client Certificate, OS User, Path, and Hash. These methods are based on registering information in the Vault with the unique application ID. For more information about the supported authentication methods, see Application authentication methods1.
When installing the CCP and configuring it for use behind a load balancer, some authentication methods may be affected by the load balancer's behavior and settings. Specifically, the following authentication methods may be affected:
Allowed Machines authentication: This method authenticates applications based on their IP address or hostname. If the load balancer replaces the source IP or hostname of the routed packets with its own IP or hostname, the CCP will not be able to authenticate the application that initiated the credential request.
To enable the CCP to resolve the IP or hostname of the application, the load balancer needs to be configured as a transparent proxy or to attach the X-Forwarded-For header to the routed packets. For more information, see Load balance the Central Credential Provider2.
Client Certificate authentication: This method authenticates applications based on their client certificate that is signed by a trusted certificate authority (CA). The client certificate is used to establish a secure and trusted connection between the application and the CCP. If the load balancer terminates the SSL connection before proxying the traffic to the CCP, the CCP will not be able to verify the client certificate of the application. To enable the CCP to validate the client certificate, the load balancer needs to be configured as a pass-through proxy or to forward the client certificate to the CCP. For more information, see Load balance the Central Credential Provider2.
The other authentication methods are not affected by the load balancer, as they do not rely on the IP, hostname, or certificate of the application. For example, the OS User method authenticates applications based on their Windows domain user, the Path method authenticates applications based on their URL path, and the Hash method authenticates applications based on a hash value that is generated from the application ID and a shared secret. These methods do not require any special configuration on the load balancer or the CCP.
質問 # 30
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
- A. two Followers in each region, load balanced for the region
- B. two Followers in each region, load balanced across all regions
- C. one Follower in each AZ. load balancer for the region
- D. two Followers in each AZ. load balanced for the region
正解:C
質問 # 31
Findings were obtained after cataloging pending Secrets Manager use cases.
Arrange the findings in the correct order for prioritization.
正解:
解説:
Explanation
The correct order for prioritization of the findings is as follows:
A new vulnerability scanner project is nearing completion and is expected to go into production soon.
This scanner is owned by the Security Team that owns CyberArk. This finding should be prioritized first because it has the highest urgency, feasibility, and alignment with the Security Team's goals. The vulnerability scanner is a critical security tool that needs to protect its credentials from unauthorized access. The Security Team can leverage their own expertise and authority to implement the Secrets Manager solution for this project without much delay or dependency.
A large, high performance application under PCI DSS regulation will require many CPs. This will require a license purchase. The procurement process can take 6-12 months. The development team is eager to work with Security on this project. This finding should be prioritized second because it has a high impact, compliance requirement, and stakeholder support. The application handles sensitive payment card data that needs to be secured by the Secrets Manager solution. The development team is willing to collaborate with the Security Team on this project and can help with the technical aspects of the implementation. However, this finding also has a high cost and a long lead time due to the license purchase and the procurement process.
A small, internally developed application under HIPPA regulation needs updates to the application code to retrieve secrets from a Secrets Manager solution. The development team stated they cannot accommodate this work before next quarter. This finding should be prioritized third because it has a moderate impact, compliance requirement, and feasibility. The application handles protected health information that needs to be secured by the Secrets Manager solution. The development team is aware of the need to update the application code to integrate with the Secrets Manager solution, but they have other priorities and constraints that prevent them from doing so in the near term.
Here's the reasoning behind this order:
1. New vulnerability scanner project:
This project directly impacts CyberArk's Security Team, making it a high priority due to potential internal security concerns. Additionally, its near-completion state suggests a quicker implementation timeframe.
2. Large application under PCI DSS:
While this application requires significant resources and time investment due to license purchase and development, its high performance and PCI DSS regulation compliance mandate prioritization. Delaying this project could potentially lead to security vulnerabilities and compliance issues.
3. Small application under HIPAA:
Although HIPAA regulation necessitates compliance, the application's size and development team's delay request suggest a lower priority compared to the previous two projects. However, it should still be addressed within the next quarter as mandated by the development team.
質問 # 32
When working with Credential Providers in a Privileged Cloud setting, what is a special consideration?
- A. Debug logging for Credential Providers deployed in a Privileged Cloud setting can inadvertently exhaust available disk space.
- B. The AWS Cloud account number must be defined in the file main appprovider.conf.
<platform>.<version> found in the AppProviderConf Safe. - C. Credential Providers are not supported in a Privileged Cloud setting.
- D. If there are installation issues, troubleshooting may need to involve the Privileged Cloud support team.
正解:D
解説:
Explanation
Credential Providers are tools that enable applications to securely retrieve credentials from CyberArk Secrets Manager without hard-coding or storing them in files. Credential Providers can be installed on application servers or on a central server that acts as a proxy for multiple applications. Credential Providers can integrate with Privileged Cloud, which is a cloud-based solution that provides privileged access management as a service. Privileged Cloud integrates with Secrets Manager Credential Providers to manage application credentials as privileged accounts within Privileged Cloud.
When working with Credential Providers in a Privileged Cloud setting, a special consideration is that if there are installation issues, troubleshooting may need to involve the Privileged Cloud support team. This is because the installation of Credential Providers in a Privileged Cloud setting requires some additional steps and configurations that are performed by the Privileged Cloud support team. For example, the Privileged Cloud support team needs to configure the connection between Privileged Cloud and Credential Providers, and provide the necessary certificates and keys for secure communication. Therefore, if there are any problems or errors during the installation process, the Privileged Cloud support team may need to assist with the troubleshooting and resolution.
The other options are not correct. Credential Providers are supported in a Privileged Cloud setting, as described in the Secrets Manager Credential Providers integration documentation1. The AWS Cloud account number does not need to be defined in the file main appprovider.conf.<platform>.<version> found in the AppProviderConf Safe. This file is used to configure the Credential Provider settings, such as the Privileged Cloud URL, the application ID, and the SSL options. The AWS Cloud account number is not relevant for this file. Debug logging for Credential Providers deployed in a Privileged Cloud setting can be enabled or disabled by the Privileged Cloud support team, as described in the Credential Provider installation documentation2.
Debug logging can help with troubleshooting and diagnostics, but it does not necessarily exhaust available disk space, as the log files can be rotated and archived.
References = Secrets Manager Credential Providers integration; Credential Provider installation
質問 # 33
A customer wants to minimize the Kubernetes application code developers must change to adopt Conjur for secrets access.
Which solutions can meet this requirement? (Choose two.)
- A. authn-Azure
- B. Secrets Provider
- C. Secretless
- D. CPM Push-to-File
- E. Application Server Credential Provider
正解:B、C
解説:
Explanation
Secrets Provider and Secretless are two solutions that can minimize the Kubernetes application code changes required to adopt Conjur for secrets access. Secrets Provider is a Kubernetes Job or Deployment that runs as an init container or application container alongside the application pod. It retrieves secrets from Conjur and writes them to one or more files in a shared, mounted volume. The application can then consume the secrets from the files without any code changes, as reading local files is a common and platform-agnostic method. Secretless is a sidecar proxy that runs as a separate container in the same pod as the application. It intercepts the application's requests to protected resources, such as databases or web services, and injects the secrets from Conjur into the requests. The application does not need to handle any secrets in its code, as Secretless handles the authentication and authorization for it. References: CyberArk Secrets Provider for Kubernetes, Secretless Broker
質問 # 34
An application is having authentication issues when trying to securely retrieve credential's from the Vault using the CCP webservices RESTAPI. CyberArk Support advised that further debugging should be enabled on the CCP server to output a trace file to review detailed logs to help isolate the problem.
What best describes how to enable debug for CCP?
- A. Edit the basic_appprovider.conf, change the "AIMWebServiceTrace" value, and restart the provider.
- B. Edit web.config. change the "AIMWebServiceTrace" value, restart Windows Web Server (IIS)
- C. From the command line, run appprvmgr.exe update_config logging=debug.
- D. In the PVWA, go to the Applications tab, select the Application in question, go to Options > Logging and choose Debug.
正解:B
解説:
Explanation
The best way to enable debug for CCP is to edit the web.config file in the AIMWebService folder and change the value of the AIMWebServiceTrace parameter to 4, which is the verbose level. This will generate detailed logs in the AIMWSTrace.log file in the logs folder. The logs folder may need to be created manually and given the appropriate permissions for the IIS_IUSRS group. After changing the web.config file, the Windows Web Server (IIS) service needs to be restarted to apply the changes. This method is recommended by CyberArk Support and documented in the CyberArk Knowledge Base1.
Editing the basic_appprovider.conf file and changing the AIMWebServiceTrace value is not a valid option, as this parameter does not exist in this file. The basic_appprovider.conf file is used to configure the basic provider settings, such as the AppProviderVaultParmsFile, the AppProviderPort, and the AppProviderCacheMode. The AIMWebServiceTrace parameter is only found in the web.config file of the AIMWebService.
In the PVWA, going to the Applications tab, selecting the Application in question, and going to Options > Logging and choosing Debug is not a valid option, as this will only enable debug for the Application Identity Manager (AIM) component, not the CCP component. The AIM component is used to manage the application identities and their access to the Vault. The CCP component is used to provide secure retrieval of credentials from the Vault using web services. Enabling debug for AIM will generate logs in the APPconsole.log, APPtrace.log, and APPaudit.log files in the ApplicationPasswordProvider\Logs folder, but these logs will not help to troubleshoot the CCP authentication issues.
From the command line, running appprvmgr.exe update_config logging=debug is not a valid option, as this will only enable debug for the Application Provider Manager (APM) component, not the CCP component. The APM component is used to manage the configuration and operation of the providers, such as the basic provider, the LDAP provider, and the ENE provider. Running appprvmgr.exe update_config logging=debug will generate logs in the appprvmgr.log file in the ApplicationPasswordProvider\Logs folder, but these logs will not help to troubleshoot the CCP authentication issues. References:
Enable Debugging and Gather Logs - Central Credential Provider1
質問 # 35
A Kubernetes application attempting to authenticate to the Follower load balancer receives this error:
ERROR: 2024/10/30 06:07:08 authenticator.go:139: CAKC029E Received invalid response to certificate signing request. Reason: status code 401 When checking the logs, you see this message:
authn-k8s/prd-cluster-01 is not enabled
How do you remediate the issue?
- A. Enable the authenticator in the Ul > Webservices > Authenticators > Enable and enable the appropriate authenticator webservice.
- B. Modify conjur.conf in /opt/conjur/etc/authenticators addinqthe authenticator webservice.
- C. A network issue is preventing the application from reaching the Follower; correct the issue and verity that it is resolved.
- D. Check the info endpoint on each Follower behind the load balancer and enable the authenticator on the Follower.
正解:B
解説:
Explanation
The error message indicates that the authenticator webservice is not enabled on the Conjur server. To enable the authenticator, you need to modify the conjur.conf file in the /opt/conjur/etc directory and add the authenticator webservice ID to the CONJUR_AUTHENTICATORS environment variable. For example, if the authenticator webservice ID is authn-k8s/prd-cluster-01, you need to add it to the existing value of CONJUR_AUTHENTICATORS, separated by a comma. Then, you need to restart the Conjur service for the changes to take effect. This will enable the authenticator on the Conjur server and allow the Kubernetes application to authenticate to the Follower load balancer. References: Enable the Authenticator Webservice, Configure the Authenticator Webservice
質問 # 36
......
CyberArk Secret-Senリアル2024年最新のブレーン問題集模擬試験問題集:https://www.jpntest.com/shiken/Secret-Sen-mondaishu
