更新された2023年12月テストエンジン練習PCCSE問題集と練習試験合格させます
問題集お試しセットPCCSEテストエンジンで問題集トレーニングには200問あります
PCCSE認定試験は、クラウドセキュリティとPrisma Cloudプラットフォームに特化したセキュリティ専門家にとって不可欠な資格です。この認定は、クラウドの採用が拡大し続ける中、クラウドセキュリティにPrisma Cloudプラットフォームを必要とする組織が増加することが予想されるため、セキュリティ専門家にとって優れたキャリア機会です。
Palo Alto Networks PCCSE(Prisma Certified Cloud Security Engineer)認定試験は、Prisma Cloudプラットフォームを使用してクラウド環境を保護する専門家のスキルを検証する高く評価されている認定です。PCCSE認定試験は、クラウドセキュリティアーキテクト、クラウドセキュリティエンジニア、クラウドセキュリティオペレーション担当者など、クラウド環境を保護する責任を持つプロフェッショナルを対象としています。認定試験は、Prisma Cloudプラットフォームを使用してクラウドセキュリティソリューションを設計、展開、管理する能力を測定することを目的としています。
PCCSE 認定プロフェッショナルになることは、キャリアの見通しを向上させる優れた方法であり、クラウドセキュリティの分野におけるあなたの貢献を示すことができます。PCCSE 認定は、世界的に認められており、分野の他のプロフェッショナルから差別化することができます。この認定を取得することで、プリズマプラットフォームを使用して効果的なソリューションを設計および実装する能力、クラウドセキュリティに関する専門知識を証明することができます。
質問 # 41
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
- A. To retrieve Prisma Cloud Console images using URL auth:
1. Access registry-auth.twistlock.com, and authenticate using the user certificate.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - B. To retrieve Prisma Cloud Console images using basic auth:
1. Access registry.twistlock.com, and authenticate using 'docker login'.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - C. To retrieve Prisma Cloud Console images using basic auth:
1. Access registry.paloaltonetworks.com, and authenticate using 'docker login'.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - D. To retrieve Prisma Cloud Console images using URL auth:
1. Access registry-url-auth.twistlock.com, and authenticate using the user certificate.
2. Retrieve the Prisma Cloud Console images using 'docker pull'.
正解:B
解説:
Section: (none)
Explanation
質問 # 42
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)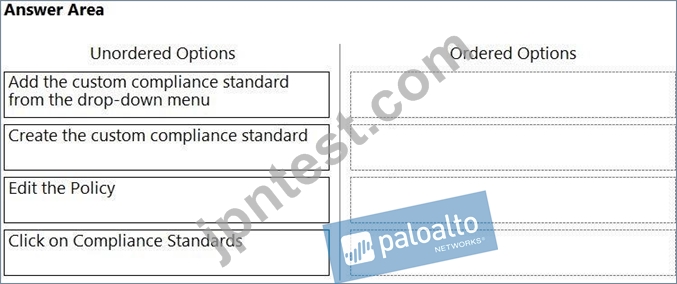
正解:
解説: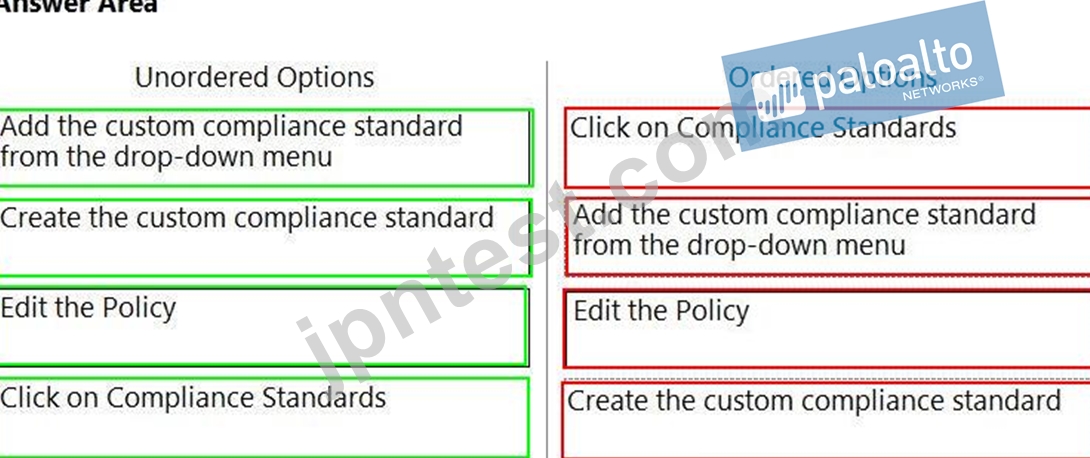
質問 # 43
A customer has a requirement to scan serverless functions for vulnerabilities.
Which three settings are required to configure serverless scanning? (Choose three.)
- A. Console Address
- B. Defender Name
- C. Region
- D. Provider
- E. Credential
正解:C、D、E
質問 # 44
A customer is deploying Defenders to a Fargate environment It wants to understand the vulnerabilities in the images it is deploying. How should the customer automate vulnerability scanning for images deployed to Fargate?
- A. Embed a Fargate Defender to automatically scan for vulnerabilities
- B. Set up a vulnerability scanner on the registry
- C. Designate a Fargate Defender to serve a dedicated image scanner
- D. Use Cloud Compliance to identify misconfigured AWS accounts
正解:A
質問 # 45
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
- A. 0
- B. 1
- C. 2
- D. 3
正解:C
質問 # 46
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster.
Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
- A. From the deployment page in Console, choose pod name for Console identifier, generate DaemonSet file, and apply the DaemonSet to twistlock namespace.
- B. From the deployment page in Console, choose twistlock-console for Console identifier, generate DaemonSet file, and apply DaemonSet to the twistlock namespace.
- C. From the deployment page configure the cloud credential in Console and allow cloud discovery to auto-protect the Kubernetes nodes.
- D. From the deployment page in Console, choose twistlock-console for Console identifier, and run the curl | bash script on the master Kubernetes node.
正解:B
質問 # 47
The attempted bytes count displays?
- A. traffic that is either denied by the firewall rules or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
- B. traffic that is either denied by the security group or firewall rules.
- C. traffic that is either denied by the security group or firewall rules or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
- D. traffic denied by the security group or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
正解:A
質問 # 48
You are an existing customer of Prisma Cloud Enterprise. You want to onboard a public cloud account and immediately see all of the alerts associated with this account based off ALL of your tenant's existing enabled policies. There is no requirement to send alerts from this account to a downstream application at this time.
Which options shows the steps required during the alert rule creation process to achieve this objective?
- A. Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select one or more policies checkbox as part of the alert rule
Confirm the alert rule - B. Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select "select all policies" checkbox as part of the alert rule
Add alert notifications
Confirm the alert rule - C. Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select "select all policies" checkbox as part of the alert rule
Confirm the alert rule - D. Ensure the public cloud account is assigned to an account group
Assign the confirmed account group to alert rule
Select one or more policies as part of the alert rule
Add alert notifications
Confirm the alert rule
正解:D
質問 # 49
A customer has configured the JIT, and the user created by the process is trying to log in to the Prisma Cloud console. The user encounters the following error message:
What is the reason for the error message?
- A. The attribute name is not set correctly in JIT settings.
- B. The role is not assigned for the user.
- C. The user does not exist.
- D. The user entered an incorrect password
正解:A
質問 # 50
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two )
- A. add a new policy
- B. disable an out-of-the-box policy
- C. clone an existing policy
- D. edit the query in the out-of-the-box policy
正解:B、C
質問 # 51
Which three types of bucket exposure are available in the Data Security module? (Choose three.)
- A. Private
- B. Public
- C. International
- D. Conditional
- E. Differential
正解:C、D、E
質問 # 52
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.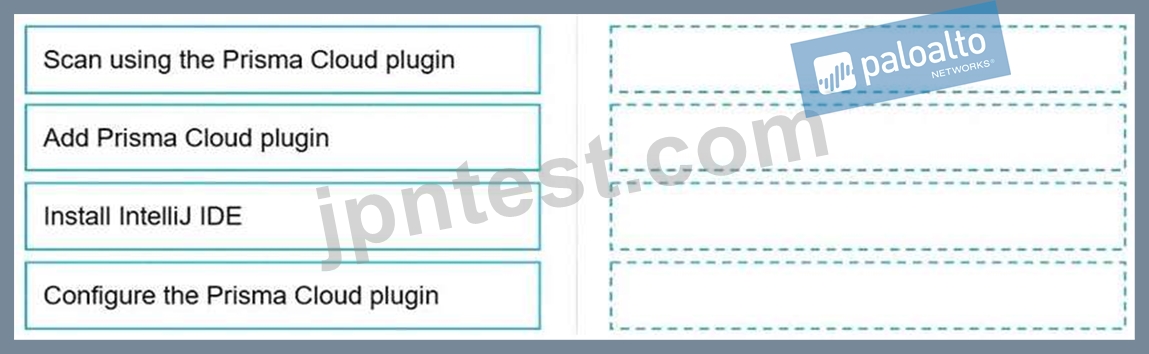
正解:
解説: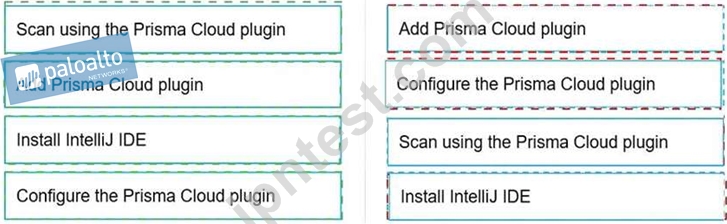
Explanation
Graphical user interface, text, application, chat or text message Description automatically generated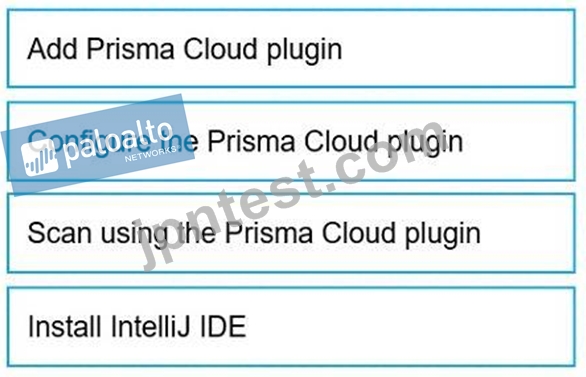
質問 # 53
Which three actions are available for the container image scanning compliance rule? (Choose three.)
- A. Snooze
- B. Allow
- C. Block
- D. Ignore
- E. Alert
正解:A、B、C
質問 # 54
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
- A. Set the specific CVE exception as an option using the magic string in the Console.
- B. Set the specific CVE exception in Console's CI policy.
- C. Set the specific CVE exception as an option in Defender running the scan.
- D. Set the specific CVE exception as an option in Jenkins or twistcli.
正解:B
解説:
Explanation
Reference tech docs:
https://docs.paloaltonetworks.com/prisma/prisma-cloud/prisma-cloud-admin-compute/continuous_integration/se Vulnerability rules that target the build tool can allow specific vulnerabilities by creating an exception and setting the effect to 'ignore'. Block them by creating an exception and setting hte effect to 'fail'. For example, you could create a vulnerability rule that explicitly allows CVE-2018-1234 to suppress warnings in the scan results.
質問 # 55
Which three public cloud providers are supported for VM image scanning? (Choose three.)
- A. Oracle
- B. Azure
- C. GCP
- D. Alibaba
- E. AWS
正解:B、C、E
質問 # 56
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
- A. Asset Name
- B. Tags
- C. Prisma Cloud API URL
- D. Access Key
- E. Secret Key
正解:C、D、E
質問 # 57
Given the following RQL:
Which audit event snippet is identified by the RQL?
A)
B)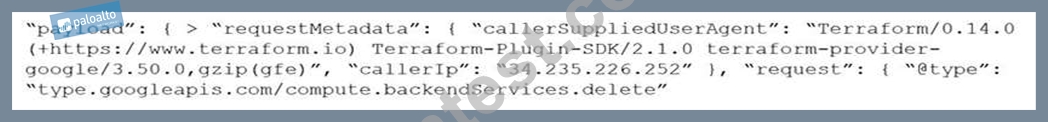
C)
D)
- A. Option A
- B. Option D
- C. Option C
- D. Option B
正解:B
質問 # 58
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application.
The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
- A. 0
- B. 1
- C. 2
- D. 3
正解:C
質問 # 59
The development team wants to block Cross Site Scripting attacks from pods its environment How should the team construct the CNAF policy to protect against this attack?
- A. create a Container CNAF policy, targeted at a specific resource, check the box for XSS attack protection and set the action to prevent
- B. create a Host CNAF policy targeted at a specific resource, check the box for XSS attack protection and set the action to "prevent"
- C. create a Container CNAF policy, targeted at a specific resource, check the box for XSS attack protection and set the action to alert
- D. create a Container CNAF policy, targeted at a specific resource, and they should set "Explicitly allowed inbound IP sources" to the IP address of the pod.
正解:B
質問 # 60
Which categories does the Adoption Advisor use to measure adoption progress for Cloud Security Posture Management?
- A. Visibility, Security, and Compliance
- B. Visibility, Compliance, Governance, and Threat Detection and Response
- C. Foundations, Advanced, and Optimize
- D. Network, Anomaly, and Audit Event
正解:B
解説:
The Adoption Advisor uses four categories to measure adoption progress for Cloud Security Posture Management: Visibility, Compliance, Governance, and Threat Detection and Response. Visibility helps to identify the resources in the environment and to ensure that security controls are in place. Compliance helps to ensure that the environment is meeting regulatory and industry standards. Governance helps to ensure that the environment is secure and managed according to policy. Threat Detection and Response helps to detect and respond to threats quickly and effectively.
質問 # 61
......
Palo Alto Networks PCCSE問題集カバー率リアル試験問題:https://www.jpntest.com/shiken/PCCSE-mondaishu
