PCCSE試験問題集合格できるには更新された2023年04月テスト問題集
PCCSEテスト問題練習は2023年最新のに更新された200問あります
質問 69
Given this information:
The Console is located at https://prisma-console.mydomain.local The username is: cluster The password is: password123 The image to scan is: myimage:latest Which twistcli command should be used to scan a Container for vulnerabilities and display the details about each vulnerability?
- A. twistcli images scan --console-address https://prisma-console.mydomain.local -u cluster -p password123 -- details myimage:latest
- B. twistcli images scan --console-address prisma-console.mydomain.local -u cluster -p password123 -- vulnerability-details myimage:latest
- C. twistcli images scan --address prisma-console.mydomain.local -u cluster -p password123 --vulnerability- details myimage:latest
- D. twistcli images scan --address https://prisma-console.mydomain.local -u cluster -p password123 --details myimage:latest
正解: D
質問 70
A customer is deploying Defenders to a Fargate environment It wants to understand the vulnerabilities in the images it is deploying. How should the customer automate vulnerability scanning for images deployed to Fargate?
- A. Use Cloud Compliance to identify misconfigured AWS accounts
- B. Set up a vulnerability scanner on the registry
- C. Embed a Fargate Defender to automatically scan for vulnerabilities
- D. Designate a Fargate Defender to serve a dedicated image scanner
正解: C
質問 71
Which component(s), if any, will Palo Alto Networks host and run when a customer purchases Prisma Cloud Enterprise Edition?
- A. twistcli
- B. Console
- C. Jenkins
- D. Defenders
正解: B
質問 72
A customer wants to monitor the company's AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
- A. Active Directory ID
- B. External ID
- C. Role ARN
- D. Subscription ID
- E. Cloudtrail
正解: C,E
質問 73
Which three types of runtime rules can be created? (Choose three.)
- A. Filesystem
- B. Waas-request
- C. Kubernetes-audit
- D. Processes
- E. Network-outgoing
正解: A,C,D
質問 74
An administrator has added a Cloud account on Prisma Cloud and then deleted it.
What will happen if the deleted account is added back on Prisma Cloud within a 24-hour period?
- A. Existing alerts will be marked as resolved.
- B. Existing alerts will be displayed again.
- C. New alerts will be generated.
- D. No alerts will be displayed.
正解: B
質問 75
One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet: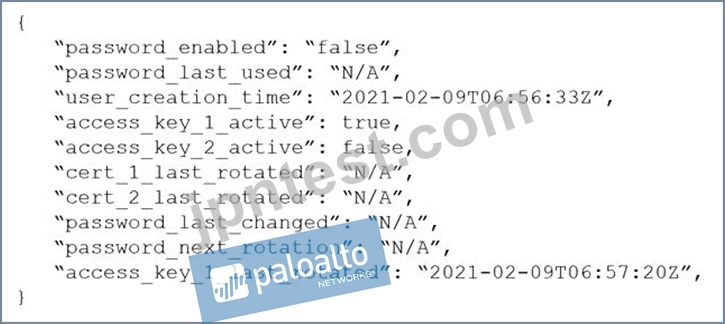
Which RQL detected the vulnerability?
- A.

- B.

- C.

- D.

正解: C
質問 76
Which data security default policy is able to scan for vulnerabilities?
- A. Objects containing Threats
- B. Objects containing Vulnerabilities
- C. Objects containing Exploits
- D. Objects containing Malware
正解: B
質問 77
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
- A. Search engine crawlers
- B. Web scrapers
- C. HTTP libraries
- D. News bots
正解: A,B
質問 78
The Unusual protocol activity (Internal) network anomaly is generating too many alerts An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
- A. Change the Training Threshold to Low
- B. Set Alert Disposition to Aggressive
- C. Set the Alert Disposition to Conservative
- D. Disable the policy
正解: A
質問 79
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
- A. The mined currency is associated with a user token.
- B. The value of the mined currency exceeds $100.
- C. Common cryptominer process name was found.
- D. High CPU usage over time for the container is detected.
- E. Common cryptominer port usage was found.
正解: A,C,D
質問 80
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine.
Which configuration step is needed first to accomplish this task?
- A. Set Defender's listener type to TCP.
- B. Configure Defender's authentication sequence to first use an identity provider and then Console.
- C. Set Docker's listener type to TCP.
- D. Configure Docker's authentication sequence to first use an identity provider and then Console.
正解: B
質問 81
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
正解:
解説: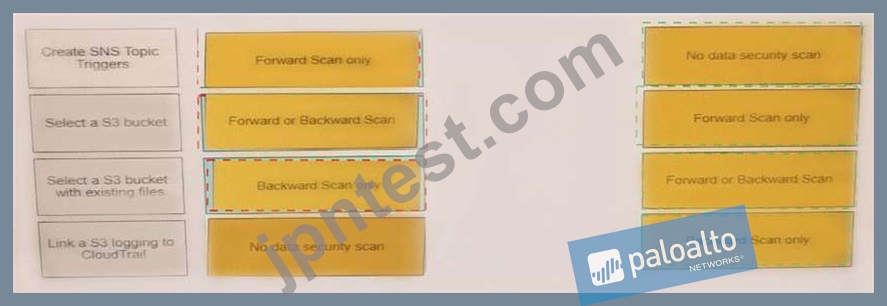
質問 82
Which three types of classifications are available in the Data Security module? (Choose three. )
- A. Malicious IP
- B. Compliance standard
- C. Financial information
- D. Personally identifiable information
- E. Malware
正解: B,D,E
質問 83
What is the most reliable and extensive source for documentation on Prisma Cloud APIs?
- A. Prisma Cloud Administrator's Guide
- B. docs.paloaltonetworks.com
- C. prisma.pan.dev
- D. Live Community
正解: A
質問 84
Which statement is true about obtaining Console images for Prisma Cloud Compute Edition?
- A. To retrieve Prisma Cloud Console images using URL auth:
1. Access registry-auth.twistlock.com, and authenticate using the user certificate.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - B. To retrieve Prisma Cloud Console images using basic auth:
1. Access registry.paloaltonetworks.com, and authenticate using 'docker login'.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - C. To retrieve Prisma Cloud Console images using basic auth:
1. Access registry.twistlock.com, and authenticate using 'docker login'.
2. Retrieve the Prisma Cloud Console images using 'docker pull'. - D. To retrieve Prisma Cloud Console images using URL auth:
1. Access registry-url-auth.twistlock.com, and authenticate using the user certificate.
2. Retrieve the Prisma Cloud Console images using 'docker pull'.
正解: C
解説:
Section: (none)
Explanation
質問 85
What is the order of steps to create a custom network policy?
(Drag the steps into the correct order of occurrence, from the first step to the last.)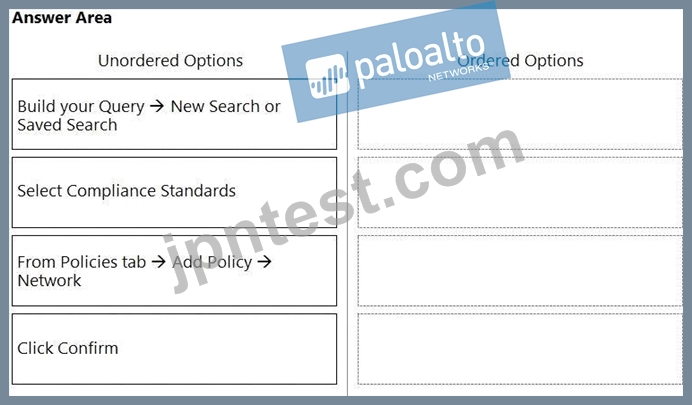
正解:
解説: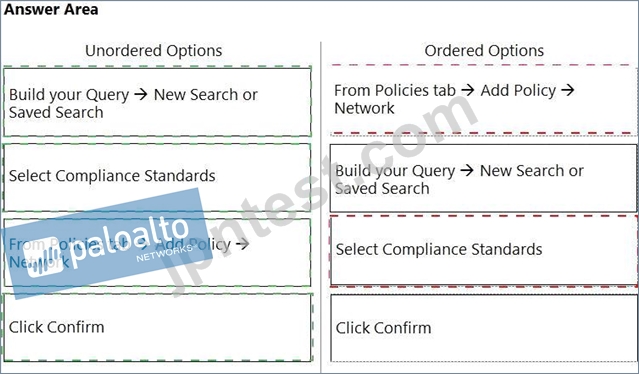
Explanation
A picture containing table Description automatically generated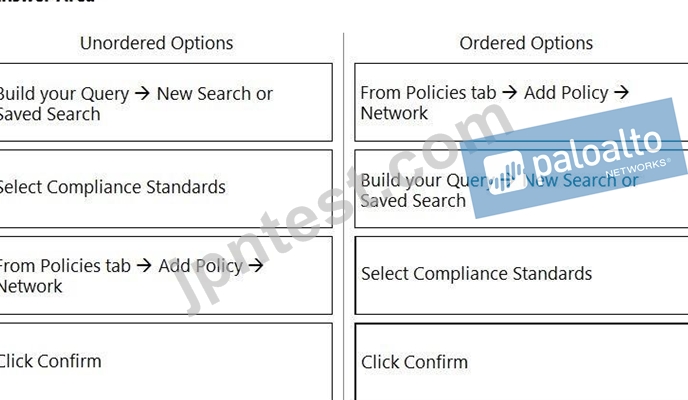
質問 86
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud?
(Choose two.)
- A. SSO Certificate
- B. SP (Service Provider) Entity ID
- C. Assertion Consumer Service (ACS) URL
- D. Username
正解: A,B
質問 87
Which three public cloud providers are supported for VM image scanning? (Choose three.)
- A. GCP
- B. Oracle
- C. Azure
- D. Alibaba
- E. AWS
正解: A,C,E
質問 88
......
正真正銘のPCCSE問題集には100%合格率練習テスト問題集:https://www.jpntest.com/shiken/PCCSE-mondaishu
