無料提供されるPCCSE問題集とPCCSEリアル試験問題
Palo Alto Networks PCCSE実際の問題とブレーン問題集
PCCSE認証は、サイバーセキュリティ業界で高く評価され、クラウドセキュリティにおける専門知識を持つプロフェッショナルを示すものです。また、クラウドセキュリティにおけるキャリアアップの機会を求めるプロフェッショナルにとって、競争力のあるアドバンテージを提供します。さらに、クラウドコンピューティングがますます人気を集める中、PCCSE認定プロフェッショナルの需要は増加することが予想され、この認証はさらに価値があるものになります。
PCCSE試験は、クラウドセキュリティに関連する幅広いトピックをカバーしています。これには、クラウドインフラセキュリティ、クラウドアプリケーションセキュリティ、クラウドデータセキュリティ、クラウドにおけるコンプライアンスとガバナンスが含まれます。試験は、これらの分野における知識とスキルをテストするように設計されており、合格した候補者は、Prismaプラットフォームを使用して効果的なクラウドセキュリティソリューションを開発、実装、管理できる能力を証明することができます。
質問 # 27
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)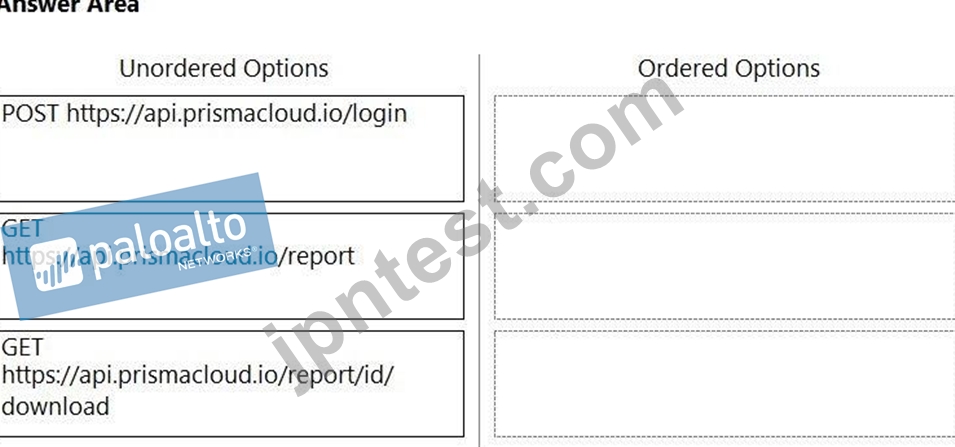
正解:
解説:
質問 # 28
Which component of a Kubernetes setup can approve, modify, or reject administrative requests?
- A. Kube Controller
- B. Terraform Controller
- C. Admission Controller
- D. Control plane
正解:C
質問 # 29
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
正解:
解説: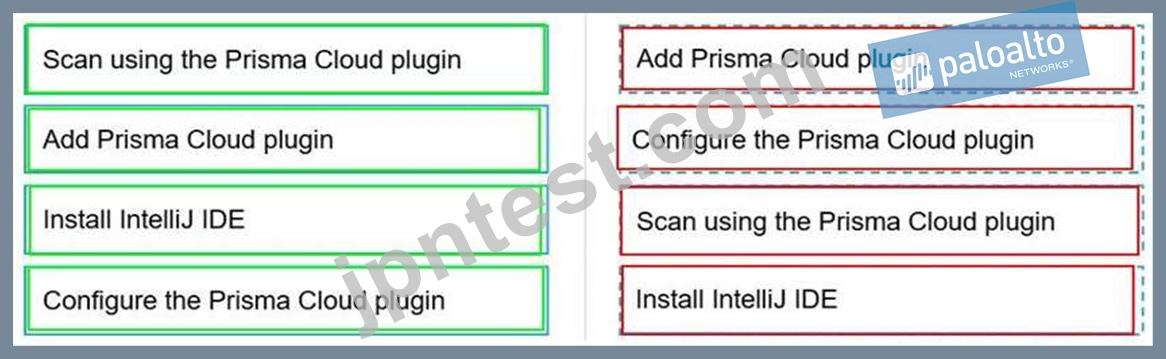
質問 # 30
The security team wants to protect a web application container from an SQLi attack? Which type of policy should the administrator create to protect the container?
- A. Runtime
- B. Compliance
- C. CNAF
- D. CNNF
正解:D
質問 # 31
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud?
(Choose two.)
- A. SSO Certificate
- B. Assertion Consumer Service (ACS) URL
- C. Username
- D. SP (Service Provider) Entity ID
正解:A、D
質問 # 32
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application.
The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
- A. 0
- B. 1
- C. 2
- D. 3
正解:C
質問 # 33
During an initial deployment of Prisma Cloud Compute, the customer sees vulnerabilities in their environment.
Which statement correctly describes the default vulnerability policy?
- A. It blocks all containers that contain a vulnerability.
- B. It alerts on any container with more than three critical vulnerabilities.
- C. It alerts on all vulnerabilities, regardless of severity.
- D. It blocks containers after 30 days if they contain a critical vulnerability.
正解:C
質問 # 34
A Prisma Cloud administrator is onboarding a single GCP project to Prisma Cloud. Which two steps can be performed by the Terraform script? (Choose two.)
- A. publish the flow log to a storage bucket.
- B. enable the required APIs for Prisma Cloud.
- C. enable flow logs for Prisma Cloud.
- D. create the Prisma Cloud role.
正解:B、C
質問 # 35
What is the order of steps in a Jenkins pipeline scan?
(Drag the steps into the correct order of occurrence, from the first step to the last.)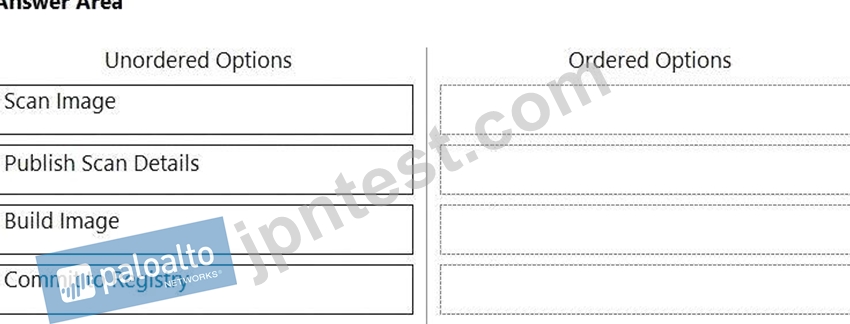
正解:
解説: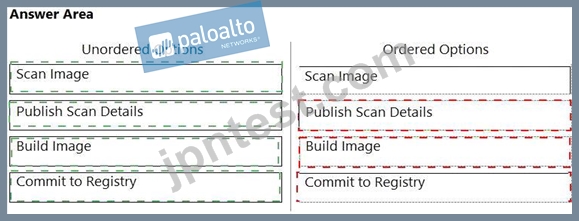
Explanation
Table Description automatically generated with medium confidence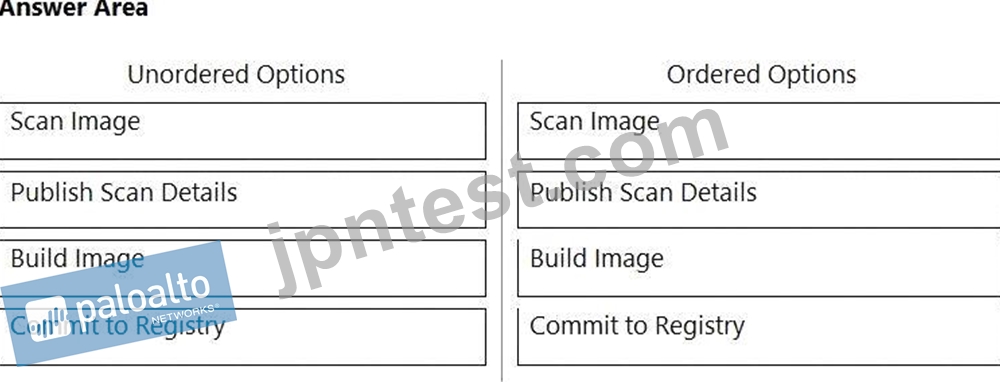
質問 # 36
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
- A. Anomaly
- B. Audit Event
- C. Config
- D. Network
正解:C
質問 # 37
Which of the below actions would indicate - "The timestamp on the compliance dashboard?
- A. indicates when the data was ingested
- B. indicates when the data was aggregated for the results displayed
- C. indicates the most recent alert generated
- D. indicates the most recent data
正解:A
質問 # 38
Which order of steps map a policy to a custom compliance standard?
(Drag the steps into the correct order of occurrence, from the first step to the last.)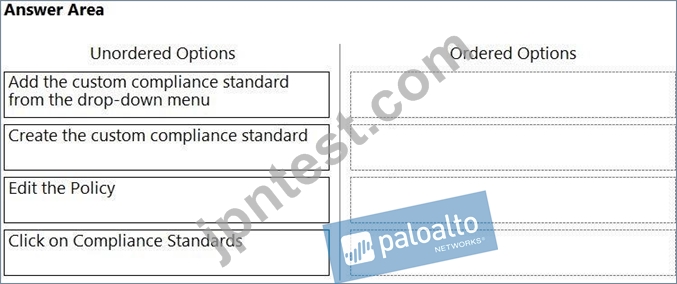
正解:
解説: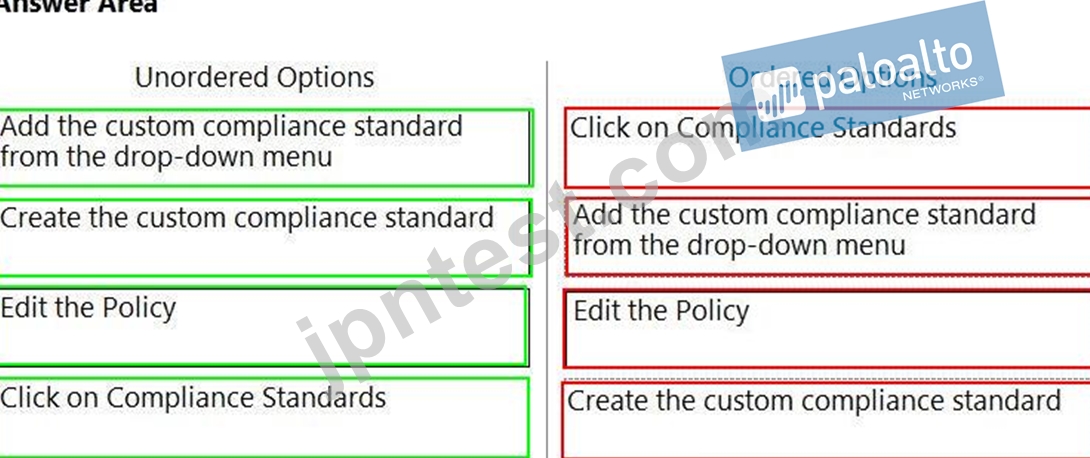
質問 # 39
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)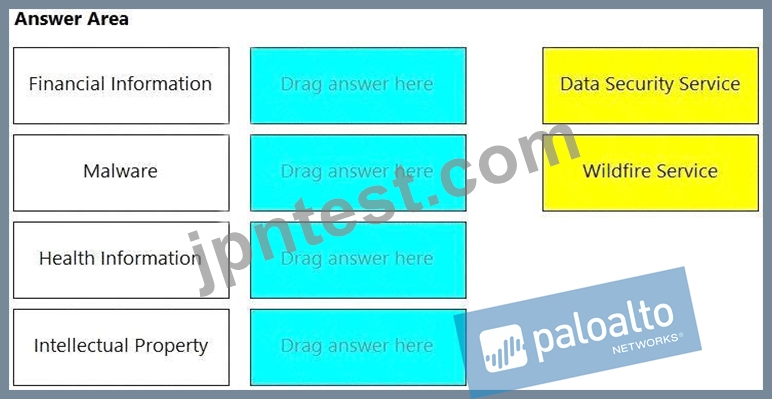
正解:
解説: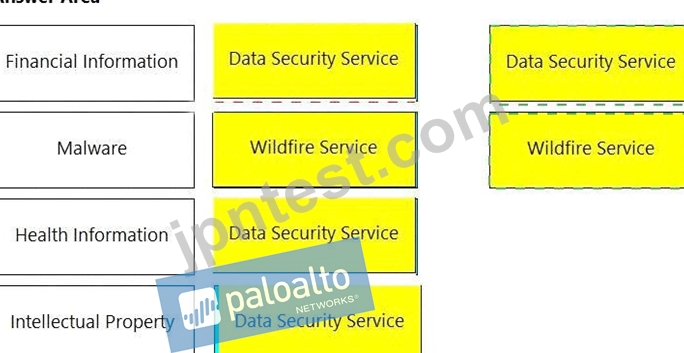
Explanation
Diagram Description automatically generated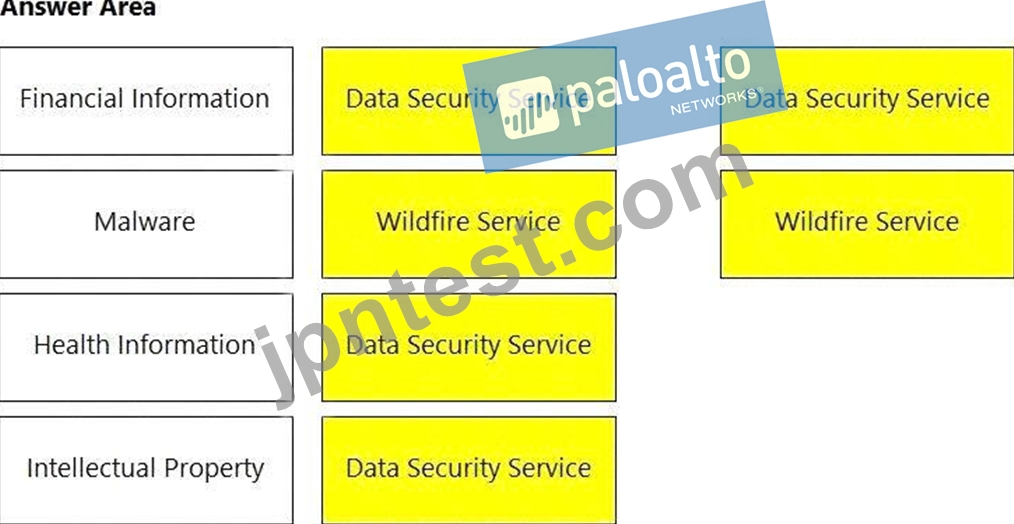
質問 # 40
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer's request?
- A. Enterprise Alert Disposition
- B. Anomaly Trusted List
- C. Trusted Login IP Addresses
- D. Trusted Alert IP Addresses
正解:D
解説:
Section: (none)
Explanation
質問 # 41
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
- A. Change the Training Threshold to Low
- B. Disable the policy
- C. Set Alert Disposition to Aggressive
- D. Set the Alert Disposition to Conservative
正解:A
解説:
Section: (none)
Explanation
質問 # 42
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)
- A. Configure IAM AWS remediation script.
- B. Integrate with Azure Service Bus.
- C. Install boto3 & requests library.
- D. Configure IAM Azure remediation script.
正解:A、C
質問 # 43
A customer has Defenders connected to Prisma Cloud Enterprise. The Defenders are deployed as a DaemonSet in OpenShift.
How should the administrator get a report of vulnerabilities on hosts?
- A. Navigate to Monitor > Vulnerabilities > Hosts
- B. Navigate to Defend > Vulnerabilities > VM Images
- C. Navigate to Monitor > Vulnerabilities > CVE Viewer
- D. Navigate to Defend > Vulnerabilities > Hosts
正解:A
質問 # 44
A security team is deploying Cloud Native Application Firewall (CNAF) on a containerized web application. The application is running an NGINX container. The container is listening on port 8080 and is mapped to host port 80.
Which port should the team specify in the CNAF rule to protect the application?
- A. 0
- B. 1
- C. 2
- D. 3
正解:B
質問 # 45
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
- A. Common cryptominer port usage was found.
- B. High CPU usage over time for the container is detected.
- C. The mined currency is associated with a user token.
- D. The value of the mined currency exceeds $100.
- E. Common cryptominer process name was found.
正解:A、B、E
質問 # 46
Which RQL query type is invalid?
- A. IAM
- B. Config
- C. Event
- D. Incident
正解:A
解説:
RQL (Real-time Query Language) is a query language used to search, filter and analyze data in Prisma Cloud. The valid RQL query types are:
Event: This type of query is used to search, filter and analyze events in Prisma Cloud.
Incident: This type of query is used to search, filter and analyze security incidents in Prisma Cloud.
Config: This type of query is used to search, filter and analyze configurations in Prisma Cloud.
IAM (Identity and Access Management) is not a valid RQL query type as it doesn't fall in the above three categories. IAM is used to manage user access to Prisma Cloud and other cloud services, and it is not used to search or analyze data in Prisma Cloud.
Top of Form
Bottom of Form
質問 # 47
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
- A. Search engine crawlers
- B. Web scrapers
- C. HTTP libraries
- D. News bots
正解:A、B
質問 # 48
How often do Defenders share logs with Console?
- A. Every 30 minutes
- B. Every 1 hour
- C. Real time
- D. Every 10 minutes
正解:B
質問 # 49
Which alerts are fixed by enablement of automated remediation?
- A. All applicable open alerts regardless of when they were generated, with alert status updated to "resolved"
- B. Only the open alerts that were generated before the enablement of remediation, with alert status updated to "resolved"
- C. All applicable open alerts regardless of when they were generated, with alert status updated to "dismissed"
- D. Only the open alerts that were generated after the enablement of remediation, with alert status updated to "resolved"
正解:D
質問 # 50
......
PCCSE試験は、クラウドセキュリティに精通した個人の専門知識を証明する価値のある認定プログラムです。クラウドサービスプロバイダと協力するプロフェッショナルに適しており、クラウド環境をセキュアに保つために必要なさまざまなトピックをカバーしています。PCCSE試験に合格することで、個人は自身のスキルと知識を検証し、キャリアの見通しを向上させ、効果的なクラウドセキュリティソリューションの開発に貢献することができます。
PCCSE合格させる問題集でPalo Alto Networks24時間で試験合格できます:https://www.jpntest.com/shiken/PCCSE-mondaishu
