[2023年10月] 問題集簡単概要PCNSE試験問題JPNTest
PCNSEトレーニング認証最新版をゲットPCNSE PAN-OS
PCNSE 認定プログラムは、次世代ファイアウォール、Panorama 管理、およびその他の関連技術を含む Palo Alto Networks セキュリティプラットフォームの深い理解を持つことを候補者が保証するために設計されています。プログラムは、ファイアウォールの構成、ネットワークセキュリティ、VPN の設定、ユーザー識別、およびアプリケーション制御など、幅広いトピックをカバーしています。候補者は、これらの領域での熟練度を証明して試験に合格し、認定を取得する必要があります。
Palo Alto Networks PCNSE認定を取得することは、個人がPalo Alto Networksファイアウォールを設計、展開、および管理するために必要なスキルと知識を持っていることを示すものです。これは、個人のキャリアの展望を向上させ、収入を増やすことができる貴重な資格です。全体的に、PCNSE認定は、Palo Alto Networksファイアウォールの専門知識を示し、ITセキュリティ業界でキャリアを進めたい人にとって必須の資格です。
質問 # 14
When an engineer configures an active/active high availability pair, which two links can they use? (Choose two)
- A. Console Backup
- B. HA2 backup
- C. HA3
- D. HSCI-C
正解:B、C
解説:
Explanation
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/high-availability/set-up-activeactive-ha/prerequisit According to the Palo Alto Networks documentation1, an active/active high availability pair requires four links to communicate and synchronize state information: HA1, HA2, HA3, and HSCI. HA1 and HA2 are the same as in active/passive mode, where HA1 is used for control plane synchronization and HA2 is used for data plane synchronization. However, in active/active mode, there are two additional links:
HA3: This link is used for session setup synchronization between the two firewalls. It allows the firewalls to share information about new sessions that they create, so that they can forward packets for the same session if needed.
HSCI: This link is used for session owner synchronization between the two firewalls. It allows the firewalls to determine which firewall is responsible for processing packets for a given session.
Both HA3 and HSCI links can use either a dedicated interface or a subinterface. Therefore, the correct answer is C and D.
The other options are not valid links for an active/active high availability pair:
HSCI-C: This option is not a valid link name. HSCI stands for High-Speed Chassis Interconnect, which is a physical cable that connects two firewalls in a chassis-based system. It is not related to active/active high availability.
Console Backup: This option is not a valid link name. Console backup is a feature that allows accessing the console port of a firewall remotely through another firewall in an HA pair. It is not related to active/active high availability.
References: 1:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/high-availability/set-up-activeactive-ha/configure-ac
質問 # 15
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?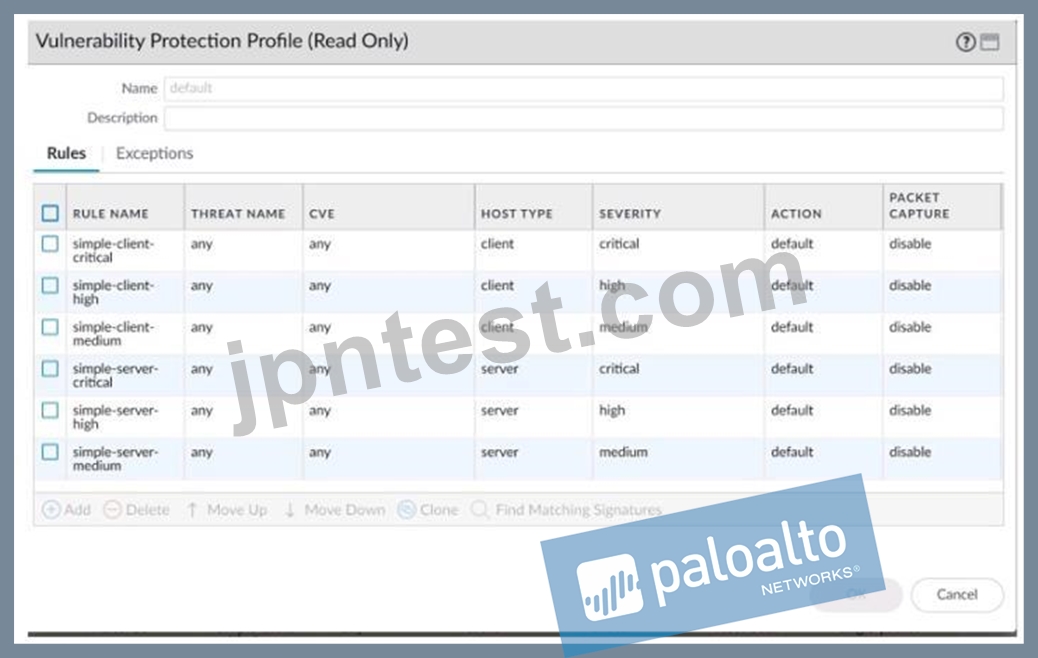
- A. The profile rule action
- B. The profile rule threat name
- C. Exceptions lab
- D. CVE column
正解:A
質問 # 16
A firewall administrator is troubleshooting problems with traffic passing through the Palo Alto Networks firewall. Which method shows the global counters associated with the traffic after configuring the appropriate packet filters?
- A. From the GUI, select show global counters under the monitor tab.
- B. From the CLI, issue the show counter interface command for the ingress interface.
- C. From the CLI, issue the show counter global filter pcap yes command.
- D. From the CLI, issue the show counter global filter packet-filter yes command.
正解:D
解説:
You can check global counters for a specific source and destination IP addresses by setting a packet filter. We recommend that you use the global counter command with a packet filter to get specific traffic outputs. These outputs will help isolate the issue between two peers.
Use the following CLI command to show when traffic is passing through the Palo Alto Networks firewall from that source to destination.
> show counter global filter packet-filter yes delta yes
Global counters:
Elapsed time since last sampling: 20.220 seconds
name value rate severity category aspect description
-------------------------------------------------------------------------------- pkt_recv 6387398 4 info packet pktproc Packets received pkt_recv_zero 370391 0 info packet pktproc Packets received from QoS 0 Etc.
https://live.paloaltonetworks.com/t5/Management-Articles/How-to-check-global-counters-for-a- specific-source-and/ta-p/65794
質問 # 17
The SSL Forward Proxy decryption policy is configured. The following four certificate authority (CA) certificates are installed on the firewall.
An end-user visits the untrusted website https //www firewall-do-not-trust-website com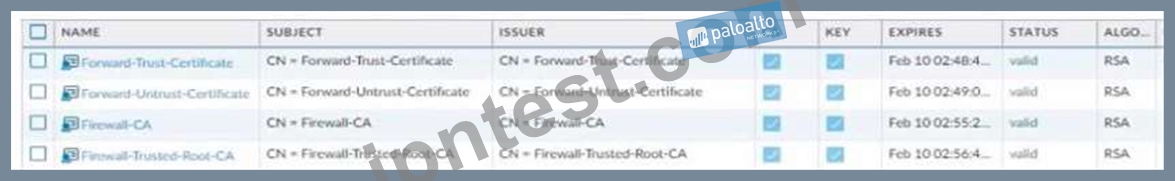
Which certificate authority (CA) certificate will be used to sign the untrusted webserver certificate?
- A. Forward-Trust-Certificate
- B. Forward-Untrust-Certificate
- C. Firewall-CA
- D. Firewall-Trusted-Root-CA
正解:A
質問 # 18
Which benefit do policy rule UUlDs provide?
- A. The use of user IP mapping and groups in policies
- B. Functionality for scheduling policy actions
- C. Cloning of policies between device-groups
- D. An audit trail across a policy's lifespan
正解:D
質問 # 19
An existing NGFW customer requires direct interne! access offload locally at each site and iPSec connectivity to all branches over public internet. One requirement is mat no new SD-WAN hardware be introduced to the environment.
What is the best solution for the customer?
- A. Upgrade to a PAN-OS SD-WAN subscription
- B. Deploy Prisma SD-WAN with Prisma Access
- C. Configure policy-based forwarding
- D. Configure a remote network on PAN-OS
正解:A
質問 # 20
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0." How should the administrator identify the root cause of this error message?
- A. In the IKE Gateway configuration, verify that the IP address for each VPN peer is accurate
- B. In the IPSec Crypto profile configuration, verify that PFS is either enabled on both VPN peers or disabled on both VPN peers.
- C. Check whether the VPN peer on one end is set up correctly using policy-based VPN
- D. Verify that the IP addresses can be pinged and that routing issues are not causing the connection failure
正解:C
解説:
Explanation
According to the Palo Alto Networks documentation , the error message "IKE phase-2 negotiation failed when processing Proxy ID" indicates that there is a mismatch between the Proxy ID settings on the two VPN peers. Proxy ID is used to identify the traffic that needs to be encrypted and tunneled. It consists of the local and remote IP addresses, protocols, and ports. If the Proxy ID settings do not match on both VPN peers, the phase-2 negotiation will fail. Therefore, the administrator should check whether the VPN peer on one end is set up correctly using policy-based VPN, which allows specifying the Proxy ID settings manually2. Therefore, the correct answer is C.
The other options are not relevant or helpful for identifying the root cause of this error message:
In the IKE Gateway configuration, verify that the IP address for each VPN peer is accurate: This option would help to identify the root cause of a phase-1 negotiation failure, not a phase-2 negotiation failure.
The IP address for each VPN peer is used to establish the IKE gateway, which is part of the phase-1 negotiation. If the IP address is inaccurate, the phase-1 negotiation will fail and the error message will be different.
Verify that the IP addresses can be pinged and that routing issues are not causing the connection failure:
This option would also help to identify the root cause of a phase-1 negotiation failure, not a phase-2 negotiation failure. The ability to ping and route between the IP addresses of the VPN peers is a prerequisite for establishing the IKE gateway, which is part of the phase-1 negotiation. If there are routing issues or connectivity problems, the phase-1 negotiation will fail and the error message will be different.
In the IPSec Crypto profile configuration, verify that PFS is either enabled on both VPN peers or disabled on both VPN peers: This option would help to identify the root cause of a different phase-2 negotiation failure, not the one related to Proxy ID mismatch. PFS stands for Perfect Forward Secrecy, which is an option to generate a new encryption key for each IPSec session. If PFS is enabled on one VPN peer but disabled on another, the phase-2 negotiation will fail and the error message will be
"IKEv2 IPSec SA negotiation failed. Invalid syntax."3.
References: 1: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClbXCAS 2:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/vpn/site-to-site-vpn/set-up-a-site-to-site-vpn-betwee
3: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClZSCA0
質問 # 21
A customer is replacing their legacy remote access VPN solution. The current solution is in place to secure only internet egress for the connected clients.
Prisma Access has been selected to replace the current remote access VPN solution.
During onboarding the following options and licenses were selected and enabled:
- Prisma Access for Remote Networks 300Mbps
- Prisma Access for Mobile Users 1500 Users
- Cortex Data Lake 2TB
- Trusted Zones trust
- Untrusted Zones untrust
- Parent Device Group shared
How can you configure Prisma Access to provide the same level of access as the current VPN solution?
- A. Configure mobile users with a service connection and trust-to-trust Security policy rules to allow the desired traffic outbound to the internet
- B. Configure remote networks with a service connection and trust-to-untrust Security policy rules to allow the desired traffic outbound to the internet
- C. Configure mobile users with trust-to-untrust Security policy rules to allow the desired traffic outbound to the internet
- D. Configure remote networks with trust-to-trust Security policy rules to allow the desired traffic outbound to the internet
正解:D
質問 # 22
Which Captive Portal mode must be configured to support MFA authentication?
- A. Redirect
- B. Transparent
- C. NTLM
- D. Single Sign-On
正解:A
質問 # 23
Refer to the diagram.
An administrator needs to create an address object that will be useable by the NYC. MA, CA and WA device groups
Where will the object need to be created within the device-group hierarchy?
- A. East
- B. West
- C. US
- D. Americas
正解:D
質問 # 24
What type of address object would be useful for internal devices where the addressing structure assigns meaning to certain bits in the address, as illustrated in the diagram?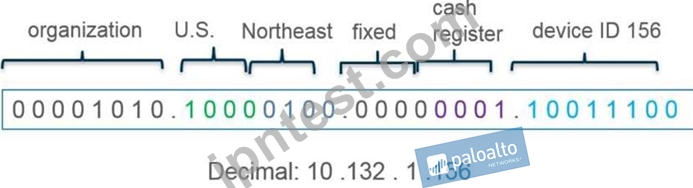
- A. IP Range
- B. IP Wildcard Mask
- C. IP Netmask
- D. IP Address
正解:B
質問 # 25
Which of the following are valid Subscriptions for the Next Generation Platform? [Select All that apply]
- A. App ID
- B. User ID
- C. URL Filtering
- D. SSL Decryption
- E. Threat Prevention
- F. Support
- G. Content ID
正解:C、E、F
質問 # 26
What happens when an A/P firewall cluster synchronizes IPsec tunnel security associations (SAs)?
- A. Phase 1 and Phase 2 SAs are synchronized over HA3 links.
- B. Phase 1 SAs are synchronized over HA1 links.
- C. Phase 1 and Phase 2 SAs are synchronized over HA2 links.
- D. Phase 2 SAs are synchronized over HA2 links.
正解:D
解説:
Reference:
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA14u000000HAuZCAW&lang
=en_US%E2%80%A9&refURL=http%3A%2F%2Fknowledgebase.paloaltonetworks.com%2FKCS ArticleDetail
質問 # 27
A network security administrator has been tasked with deploying User-ID in their organization.
What are three valid methods of collecting User-ID information in a network? (Choose three.)
- A. XMLAPI
- B. External dynamic list
- C. Dynamic user groups
- D. GlobalProtect
- E. Windows User-ID agent
正解:A、D、E
解説:
Explanation
User-ID is a feature that enables the firewall to identify users and groups based on their IP addresses, usernames, or other attributes.
There are three valid methods of collecting User-ID information in a network:
* Windows User-ID agent: This is a software agent that runs on a Windows server and collects user mapping information from Active Directory, Exchange servers, or other sources.
* GlobalProtect: This is a VPN solution that provides secure remote access for users and devices. It also collects user mapping information from endpoints that connect to the firewall using GlobalProtect.
* XMLAPI: This is an application programming interface that allows third-party applications or scripts to send user mapping information to the firewall using XML format.
質問 # 28
Which three file types can be forwarded to WildFire for analysis as a part of the basic WildFire service?
(Choose three.)
- A. .exe
- B. .pdf
- C. .apk
- D. .src
- E. .dll
- F. .jar
正解:A、D、E
解説:
Explanation
https://docs.paloaltonetworks.com/pan-os/7-1/pan-os-admin/getting-started/enable-basic-wildfire-forwarding
質問 # 29
In a Panorama template which three types of objects are configurable? (Choose three)
- A. interface management profiles
- B. HIP objects
- C. security profiles
- D. QoS profiles
- E. certificate profiles
正解:A、B、C
質問 # 30
PAS-OS 7.0 introduced an automated correlation engine that analyzes log patterns and generates correlation events visible in the new Application Command Center (ACC).
Which license must the firewall have to obtain new correlation objectives?
- A. URL Filtering
- B. GlobalProtect
- C. Application Center
- D. Threat Prevention
正解:D
解説:
https://www.paloaltonetworks.com/documentation/70/pan-os/pan-os/monitoring/automated- correlation-engine-concepts
質問 # 31
What best describes the HA Promotion Hold Time?
- A. the time that is recommended to avoid a failover when both firewalls experience the same link/path monitor failure simultaneously
- B. the time that the passive firewall will wait before taking over as the active firewall after communications with the HA peer have been lost
- C. the time that a passive firewall with a low device priority will wait before taking over as the active firewall if the firewall is operational again
- D. the time that is recommended to avoid an HA failover due to the occasional flapping of neighboring devices
正解:B
解説:
HA Promotion Hold Time is the time that the passive firewall will wait before taking over as the active firewall after communications with the HA peer have been lost 2. Reference: 2: PAN-OS New Features Guide
質問 # 32
PBF can address which two scenarios? (Select Two)
- A. enabling the firewall to bypass Layer 7 inspection
- B. routing FTP to a backup ISP link to save bandwidth on the primary ISP link
- C. forwarding all traffic by using source port 78249 to a specific egress interface
- D. providing application connectivity the primary circuit fails
正解:B、D
解説:
Explanation
https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/policy/policy-based-forwarding/use-case-pbf-for-o
質問 # 33
Which PAN-OS® policy must you configure to force a user to provide additional credentials before he is allowed to access an internal application that contains highly-sensitive business data?
- A. Security policy
- B. Decryption policy
- C. Authentication policy
- D. Application Override policy
正解:C
質問 # 34
An administrator wants multiple web servers in the DMZ to receive connections initiated from the internet.
Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10.1.1.22
Based on the information shown in the image, which NAT rule will forward web-browsing traffic correctly?
A)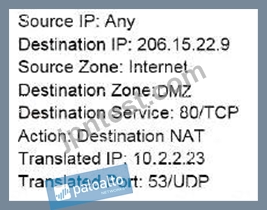
B)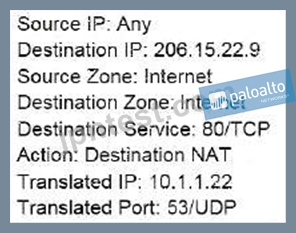
C)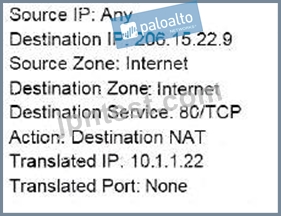
D)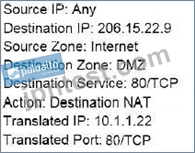
- A. Option B
- B. Option A
- C. Option D
- D. Option C
正解:D
質問 # 35
What will be the egress interface if the traffic's ingress interface is ethernet1/6 sourcing from 192.168.111.3 and to the destination 10.46.41.113 during the time shown in the image?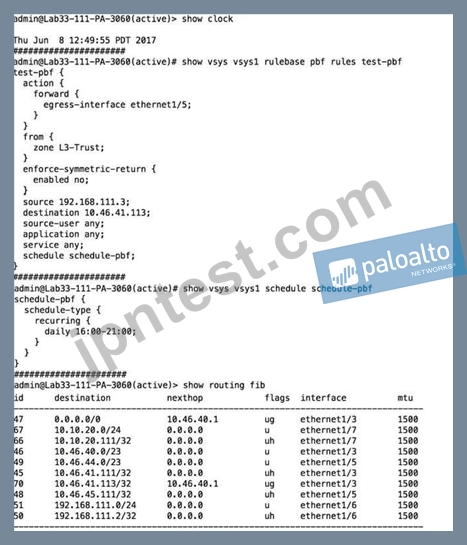
- A. ethernet1/5
- B. ethernet1/6
- C. ethernet1/7
- D. ethernet1/3
正解:D
質問 # 36
What is exchanged through the HA2 link?
- A. session synchronization
- B. hello heartbeats
- C. HA state information
- D. User-ID information
正解:A
解説:
Reference:
"Data Link-The HA2 link is used to synchronize sessions, forwarding tables, IPSec security associations and ARP tables between devices in an HA pair. Data flow on the HA2 link is always unidirectional (except for the HA2 keep-alive); it flows from the active device to the passive device." https://docs.paloaltonetworks.com/vm-series/9-0/vm-series-deployment/set-up-the-vm-series-firewall-on-aws/high-availability-for-vm-series-firewall-on-aws/ha-links#:~:text=%E2%80%94The%20HA1%20link%20is%20used,port%20is%20used%20for%20HA1
質問 # 37
......
Palo Alto NetworksのPCNSE認定試験は、最新バージョンのPAN-OS 10.0に基づいています。この試験では、ファイアウォールアーキテクチャ、展開シナリオ、ネットワークセキュリティコンセプト、およびトラブルシューティング手法に関する候補者の知識をテストします。また、新しいセキュリティ強化機能、ポリシー管理、およびデバイス管理機能を含むPAN-OS 10.0の最新機能もカバーしています。
認証トレーニングPCNSE試験問題集テストエンジン:https://www.jpntest.com/shiken/PCNSE-mondaishu
