PCNSE別格な問題集をダウンロードして無料で最新の(PCNSEテスト問題集をゲット2023年12月04日)
PCNSE問題集は合格保証します合格できるPCNSE試験問題2023年更新
PCNSE認定試験に備えるために、候補者はパロアルトネットワークスのトレーニングコース、オンラインリソース、および学習資料を活用することができます。試験は厳しいものであり、試験に挑戦する前に、候補者はパロアルトネットワークスの製品や技術に対して実践的な経験を持っていることが推奨されています。
質問 # 52
An administrator deploys PA-500 NGFWs as an active/passive high availability pair. The devices are not participating in dynamic routing, and preemption is disabled.
What must be verified to upgrade the firewalls to the most recent version of PAN-OS software?
- A. User-ID agent.
- B. Antivirus update package.
- C. WildFire update package.
- D. Applications and Threats update package.
正解:D
解説:
Explanation/Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/newfeaturesguide/upgrade-to-pan-os-
80/upgrade-the-firewall-to-pan-os-80/upgrade-an-ha-firewall-pair-to-pan-os-80
質問 # 53
A users traffic traversing a Palo Alto networks NGFW sometimes can reach http //www company com At other times the session times out. At other times the session times out The NGFW has been configured with a PBF rule that the user traffic matches when it goes to
http://www.company.com goes to http://www company com
How can the firewall be configured to automatically disable the PBF rule if the next hop goes down?
- A. Configure path monitoring for the next hop gateway on the default route in the virtual router
- B. Enable and configure a link monitoring profile for the external interface of the firewall
- C. Create and add a monitor profile with an action of wait recover in the PBF rule in question
- D. Create and add a monitor profile with an action of fail over in the PBF rule in question
正解:D
質問 # 54
Several offices are connected with VPNs using static IPV4 routes. An administrator has been tasked with implementing OSPF to replace static routing.
Which step is required to accoumplish this goal?
- A. Create new VPN zones at each site to terminate each VPN connection
- B. Assign OSPF Area ID 0.0.0.0 to all Ethernet and tunnel interfaces
- C. Assign an IP address on each tunnel interface at each site
- D. Enable OSPFv3 on each tunnel interface and use Area ID 0.0.0.0
正解:B
質問 # 55
An engineer troubleshooting a VPN issue needs to manually initiate a VPN tunnel from the CLI.
Which CLI command can the engineer use?
- A. test vpn flow
- B. test vpn tunnel
- C. test vpn gateway
- D. test vpn Ike-sa
正解:C
解説:
Explanation
The engineer can use the test vpn gateway CLI command to manually initiate a VPN tunnel from the CLI.
This command allows the engineer to specify the name of the VPN gateway and the IP address of the peer to initiate an IKE negotiation and establish a VPN tunnel. Option A is incorrect because test vpn flow is not a valid CLI command. Option B is incorrect because test vpn ike-sa is a CLI command that displays information about the IKE security associations, not initiates a VPN tunnel. Option C is incorrect because test vpn tunnel is a CLI command that displays information about the IPSec security associations, not initiates a VPN tunnel.
質問 # 56
A user at an internal system queries the DNS server for their web server with a private IP of 10 250 241 131 in the. The DNS server returns an address of the web server's public address, 200.1.1.10.
In order to reach the web server, which security rule and U-Turn NAT rule must be configured on the firewall?
- A.
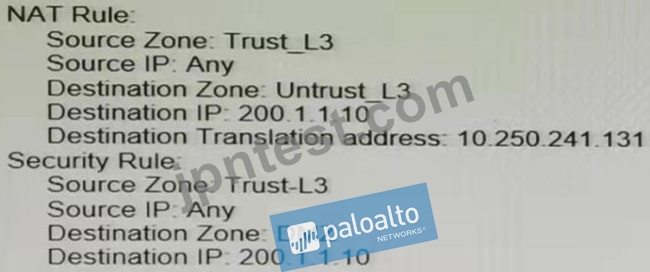
- B.

- C.

- D.
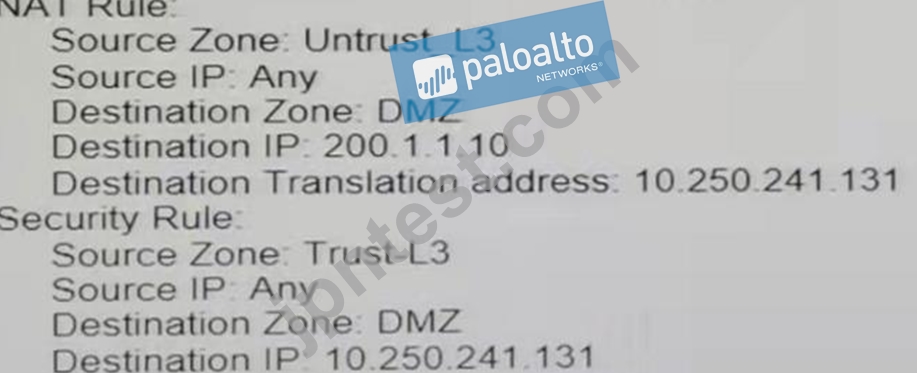
正解:A
解説:
Explanation
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClEiCAK
質問 # 57
Refer to the exhibit.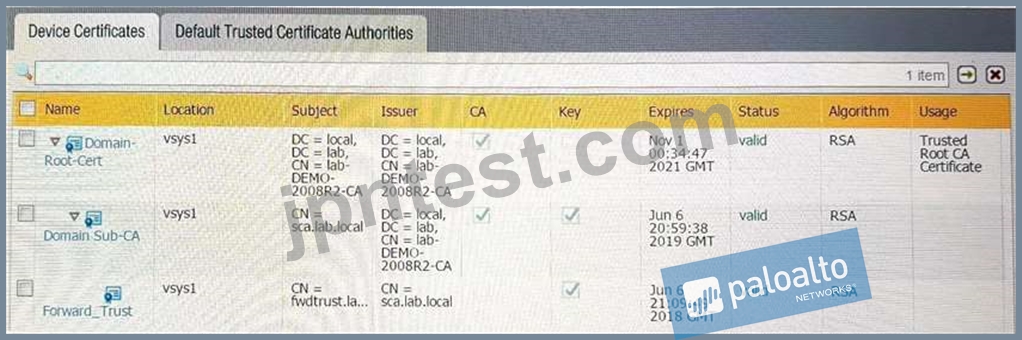
Which certificates can be used as a Forwarded Trust certificate?
- A. Domain Sub-CA
- B. Domain-Root-Cert
- C. Certificate from Default Trust Certificate Authorities
- D. Forward_Trust
正解:A
質問 # 58
Which log type will help the engineer verify whether packet buffer protection was activated?
- A. Threat
- B. Traffic
- C. Data Filtering
- D. Configuration
正解:A
解説:
The log type that will help the engineer verify whether packet buffer protection was activated is Threat Logs. Threat Logs are logs generated by the Palo Alto Networks firewall when it detects a malicious activity on the network. These logs contain information about the source, destination, and type of threat detected. They also contain information about the packet buffer protection that was activated in response to the detected threat. This information can help the engineer verify that packet buffer protection was activated and determine which actions were taken in response to the detected threat.
Packet buffer protection is a feature that prevents packet buffer exhaustion by dropping packets, discarding sessions, or blocking source IP addresses when the packet buffer utilization exceeds a certain threshold. The firewall records these events in the threat log with different threat IDs and names1. The system log also records an alert event when the packet buffer congestion reaches the alert threshold2. The other types of logs do not show packet buffer protection events. Reference: 1: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/zone-protection-and-dos-protection/zone-defense/packet-buffer-protection 2: https://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/monitoring/use-syslog-for-monitoring/syslog-field-descriptions/system-log-fields
質問 # 59
A network administrator configured a site-to-site VPN tunnel where the peer device will act as initiator None of the peer addresses are known What can the administrator configure to establish the VPN connection?
- A. Enable Passive Mode
- B. Configure the peer address as an FQDN.
- C. Use the Dynamic IP address type.
- D. Set up certificate authentication.
正解:B
解説:
Explanation
According to the documentation, if the peer device has a dynamic IP address, the administrator can configure the peer address as an FQDN and use tunnel monitoring to establish the VPN connection. Tunnel monitoring is a feature that sends periodic ICMP pings to a specified destination IP address across the VPN tunnel and brings down the tunnel interface if the pings fail. This way, the firewall can detect when the peer device changes its IP address and re-establish the VPN connection. References: IPSec VPN Tunnel with Peer Having Dynamic IP Address - Palo Alto Networks Dual ISP VPN site to site Tunnel Failover with Tunnel Monitoring - Palo Alto Networks
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClIGCA0
質問 # 60
The UDP-4501 protocol-port is used between which two GlobalProtect components?
- A. GlobalProtect app and GlobalProtect portal
- B. GlobalProtect portal and GlobalProtect gateway
- C. GlobalProtect app and GlobalProtect satellite
- D. GlobalProtect app and GlobalProtect gateway
正解:D
解説:
UDP 4501 Used for IPSec tunnel connections between GlobalProtect apps and gateways. https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/firewall-administration/reference-port-number-usage/ports-used-for-globalprotect.html
質問 # 61
Which three authentication factors does PAN-OS® software support for MFA (Choose three.)
- A. Push
- B. Voice
- C. Pull
- D. Okta Adaptive
- E. SMS
正解:A、B、E
解説:
Reference:
https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/authentication/configure-multi-factor-authentication
質問 # 62
An engineer is configuring SSL Inbound Inspection for public access to a company's application. Which certificate(s) need to be installed on the firewall to ensure that inspection is performed successfully?
- A. Self-signed certificate with exportable private key
- B. Self-signed CA and End-entity certificate
- C. Intermediate CA (s) and End-entity certificate
- D. Root CA and Intermediate CA(s)
正解:C
解説:
https://docs.paloaltonetworks.com/pan-os/10-1/pan-os-admin/decryption/configure-ssl-inbound-inspection We recommend uploading a certificate chain (a single file) to the firewall if your end-entity (leaf) certificate is signed by one or more intermediate certificates and your web server supports TLS 1.2 and Rivest, Shamir, Adleman (RSA) or Perfect Forward Secrecy (PFS) key exchange algorithms. Uploading the chain avoids client-side server certificate authentication issues. You should arrange the certificates in the file as follows: End-entity (leaf) certificate Intermediate certificates (in issuing order) (Optional) Root certificate
質問 # 63
Which value in the Application column indicates UDP traffic that did not match an App-ID signature?
- A. not-applicable
- B. unknown-ip
- C. unknown-udp
- D. incomplete
正解:C
解説:
Explanation
To safely enable applications you must classify all traffic, across all ports, all the time. With App-ID, the only applications that are typically classified as unknown traffic-tcp, udp or non-syn-tcp-in the ACC and the Traffic logs are commercially available applications that have not yet been added to App-ID, internal or custom applications on your network, or potential threats.
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/app-id/use-application-objects-in-policy/create-a-cu
質問 # 64
SD-WAN is designed to support which two network topology types? (Choose two.)
- A. full-mesh
- B. ring
- C. hub-and-spoke
- D. point-to-point
正解:A、C
質問 # 65
Click the Exhibit button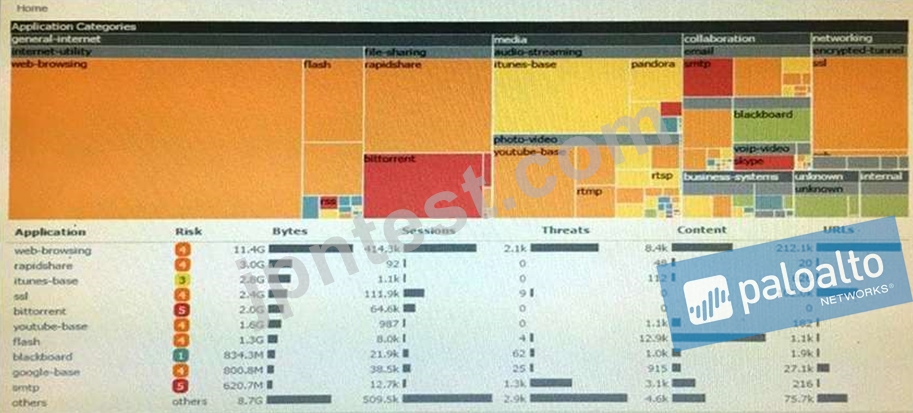
An administrator has noticed a large increase in bittorrent activity. The administrator wants to determine where the traffic is going on the company.
What would be the administrator's next step?
- A. Create local filter for bittorrent traffic and then view Traffic logs.
- B. Create a global filter for bittorrent traffic and then view Traffic logs.
- C. Click on the bittorrent application link to view network activity
- D. Right-Click on the bittorrent link and select Value from the context menu
正解:C
質問 # 66
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
- A. Powershell scripts
- B. VBscripts
- C. ELF
- D. MS Office
- E. APK
正解:A、C、D
解説:
"The WildFire inline ML option present in the Antivirus profile enables the firewall dataplane to apply machine learning on PE (portable executable), ELF (executable and linked format) and MS Office files, and PowerShell and shell scripts in real-time." fromhttps://docs.paloaltonetworks.com/pan-os/10-2/pan-os-admin/threat-prevention/wildfire-inline-ml
質問 # 67
Please match the terms to their corresponding definitions.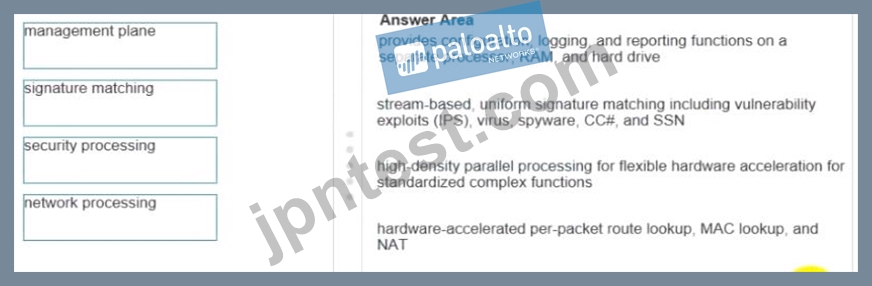
正解:
解説:
質問 # 68
Which two statements are true about DoS Protection and Zone Protection Profiles? (Choose two).
- A. DoS Protection Profiles are linked to Security policy rules
- B. Zone Protection Profiles protect ingress zones
- C. DoS Protection Profiles are packet-based, not signature-based
- D. Zone Protection Profiles protect egress zones
正解:A、B
解説:
https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/zone-protection-and-dos-protection/zone-defense/zone-protection-profiles
質問 # 69
Which administrative authentication method supports authorization by an external service?
- A. LDAP
- B. SSH keys
- C. Certificates
- D. RADIUS
正解:D
解説:
Explanation/Reference: https://www.paloaltonetworks.com/documentation/80/pan-os/pan-os/firewall-administration/ manage-firewall-administrators/administrative-authentication
質問 # 70
Which option describes the operation of the automatic commit recovery feature?
- A. It enables a firewall to revert to the previous configuration if a commit causes HA partner connectivity failure.
- B. It enables a firewall to revert to the previous configuration if application dependency errors are found.
- C. It enables a firewall to revert to the previous configuration if a commit causes Panorama connectivity failure.
- D. It enables a firewall to revert to the previous configuration if rule shadowing is detected.
正解:C
解説:
Explanation/Reference: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-new-features/panorama-features/automatic- panorama-connection-recovery.html
質問 # 71
An administrator wants multiple web servers in the DMZ to receive connections initiated from the internet.
Traffic destined for 206.15.22.9 port 80/TCP needs to be forwarded to the server at 10.1.1.22 Based on the information shown in the image, which NAT rule will forward web-browsing traffic correctly?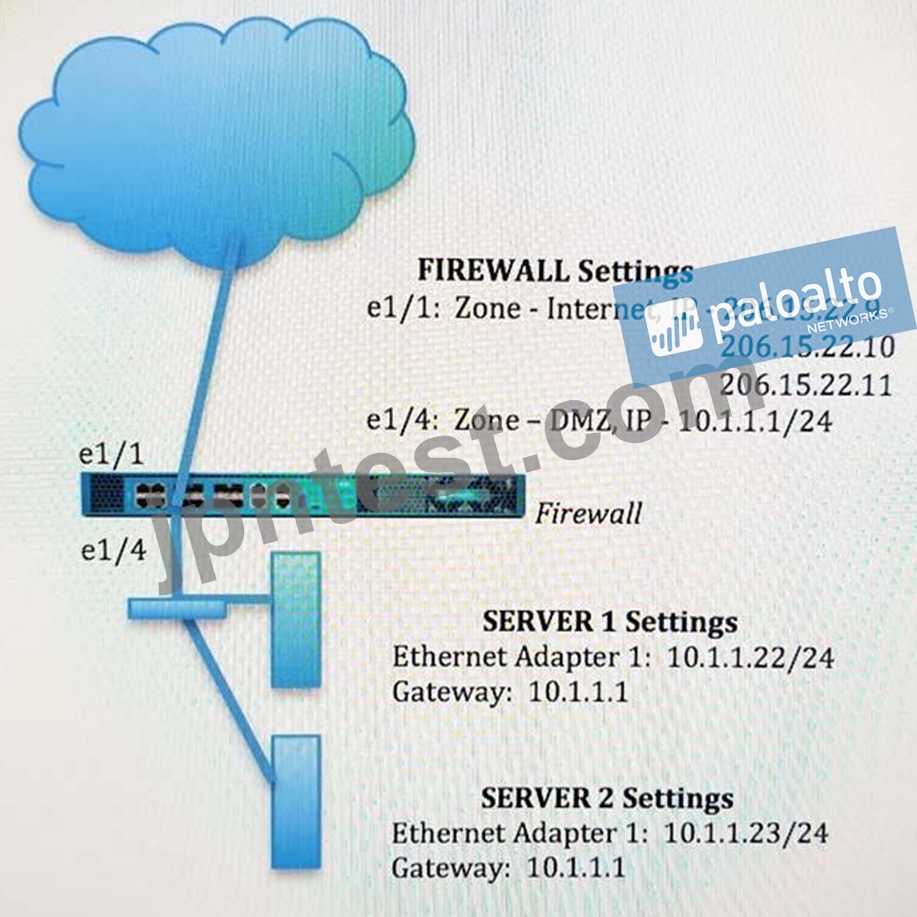
A: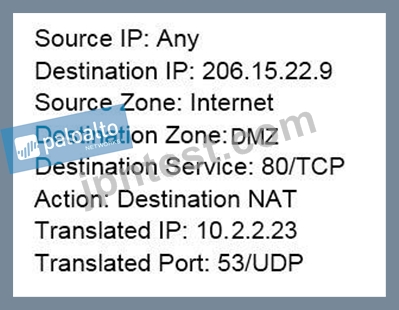
B: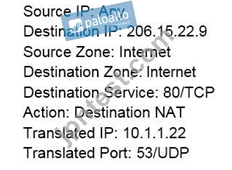
C: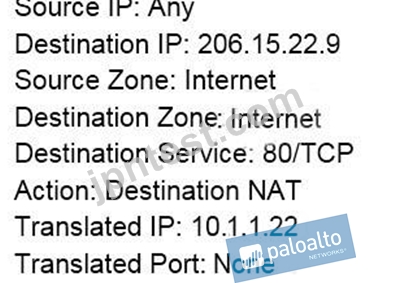
D: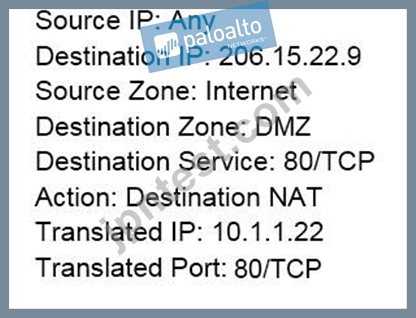
- A. Option B
- B. Option D
- C. Option A
- D. Option C
正解:D
質問 # 72
Which option enables a Palo Alto Networks NGFW administrator to schedule Application and Threat updates while applying only new content-IDs to traffic?
- A. Select download-only
- B. Select download-and-install
- C. Select download-and-install, with "Disable new apps in content update" selected
- D. Select disable application updates and select "Install only Threat updates"
正解:B
解説:
Explanation
質問 # 73
The same route appears in the routing table three times using three different protocols Which mechanism determines how the firewall chooses which route to use?
- A. Round Robin load balancing
- B. Order in the routing table
- C. Administrative distance
- D. Metric
正解:C
解説:
Explanation
Administrative distance is the measure of trustworthiness of a routing protocol. It is used to determine the best path when multiple routes to the same destination exist. The route with the lowest administrative distance is chosen as the best route.
質問 # 74
If an administrator does not possess a website's certificate, which SSL decryption mode will allow the Palo Alto networks NGFW to inspect when users browse to HTTP(S) websites?
- A. SSL Forward Proxy
- B. TLS Bidirectional proxy
- C. SSL Inbound Inspection
- D. SSL Outbound Inspection
正解:C
質問 # 75
An engineer needs to see how many existing SSL decryption sessions are traversing a firewall What command should be used?
- A. debug sessions I match proxy
- B. debug dataplane pool statistics I match proxy
- C. show sessions all
- D. show dataplane pool statistics I match proxy
正解:B
解説:
Explanation
https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClhdCAC
質問 # 76
An internal system is not functioning. The firewall administrator has determined that the incorrect egress interface is being used.
After looking at the configuration, the administrator believes that the firewall is not using a static route.
What are two reasons why the firewall might not use a static route? (Choose two.)
- A. duplicate static route
- B. no install on the route
- C. path monitoring on the static route
- D. disabling of the static route
正解:B、D
解説:
https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/networking/static-routes/static-route- removal-based-on-path-monitoring.html
https://docs.paloaltonetworks.com/pan-os/9-0/pan-os-admin/networking/static-routes/configure-a- static-route.html
質問 # 77
......
検証済みのPCNSE問題集で問題と解答で合格保証試験問題集テストエンジン:https://www.jpntest.com/shiken/PCNSE-mondaishu
