2023年最新のEX294試験解答最新版JPNTest EX294のPDF問題集をダウンロードせよ(35問題と解答)
無料2023年最新のRHCE EX294問題集を提供しております!JPNTest
質問 # 20
Create the users in the file usersjist.yml file provided. Do this in a playbook called users.yml located at /home/sandy/ansible. The passwords for these users should be set using the lock.yml file from TASK7. When running the playbook, the lock.yml file should be unlocked with secret.txt file from TASK 7.
All users with the job of 'developer' should be created on the dev hosts, add them to the group devops, their password should be set using the pw_dev variable. Likewise create users with the job of 'manager' on the proxy host and add the users to the group 'managers', their password should be set using the pw_mgr variable.
正解:
解説:
ansible-playbook users.yml -vault-password-file=secret.txt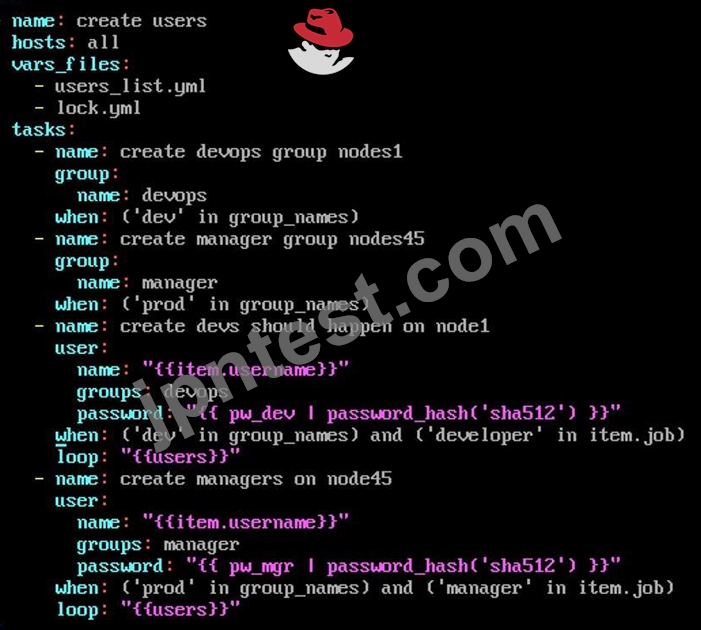
質問 # 21
Create and run an Ansible ad-hoc command.
--> As a system administrator, you will need to install software on the managed
nodes.
--> Create a shell script called yum-pack.sh that runs an Ansible ad-hoc command to
create yum-repository on each of the managed nodes as follows:
--> repository1
-----------
1. The name of the repository is EX407
2. The description is "Ex407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEYredhat-
release
6. The repository is enabled
--> repository2
-----------
1. The name of the repository is EXX407
2. The description is "Exx407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/AppStream/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/ RPM-GPG-KEYredhat-
release
6. The repository is enabled
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# vim yum-pack.sh
#!/bin/bash
ansible all -m yum_repository -a 'name=EX407 description="Ex407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/ gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
ansible all -m yum_repository -a 'name=EXX407 description="Exx407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/AppStream/ gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
:!wq
# chmod +x yum-pack.sh
# bash yum-pack.sh
# ansible all -m command -a 'yum repolist all'
質問 # 22
Create a jinja template in /home/sandy/ansible/ and name it hosts.j2. Edit this file so it looks like the one below. The order of the nodes doesn't matter. Then create a playbook in /home/sandy/ansible called hosts.yml and install the template on dev node at /root/myhosts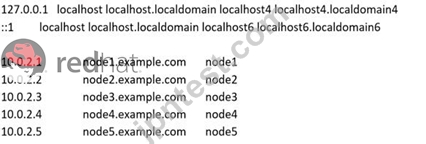
- A. Solution as:
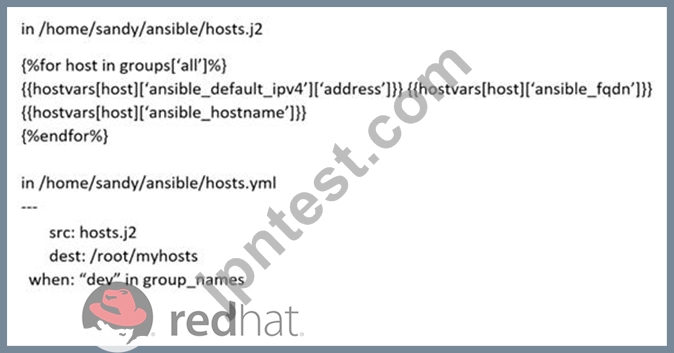
- B. Solution as:

正解:B
質問 # 23
Create an ansible vault password file called lock.yml with the password reallysafepw in the /home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called secret.txt which contains the password for lock.yml.
正解:
解説:
ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
質問 # 24
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in /home/sandy/ansible/invenlory.
You will have access to 5 nodes.
node1.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
正解:
解説:
In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
[proxy]
node3 .example.com
[prod]
node4.example.com
node5 .example.com
[webservers:children]
prod
質問 # 25
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the second php-role. The roles should be installed in /home/sandy/ansible/roles.
正解:
解説:
in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles
質問 # 26
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
- A. Solution as:

- B. Solution as:

正解:A
質問 # 27
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
正解:
解説:
Solution as: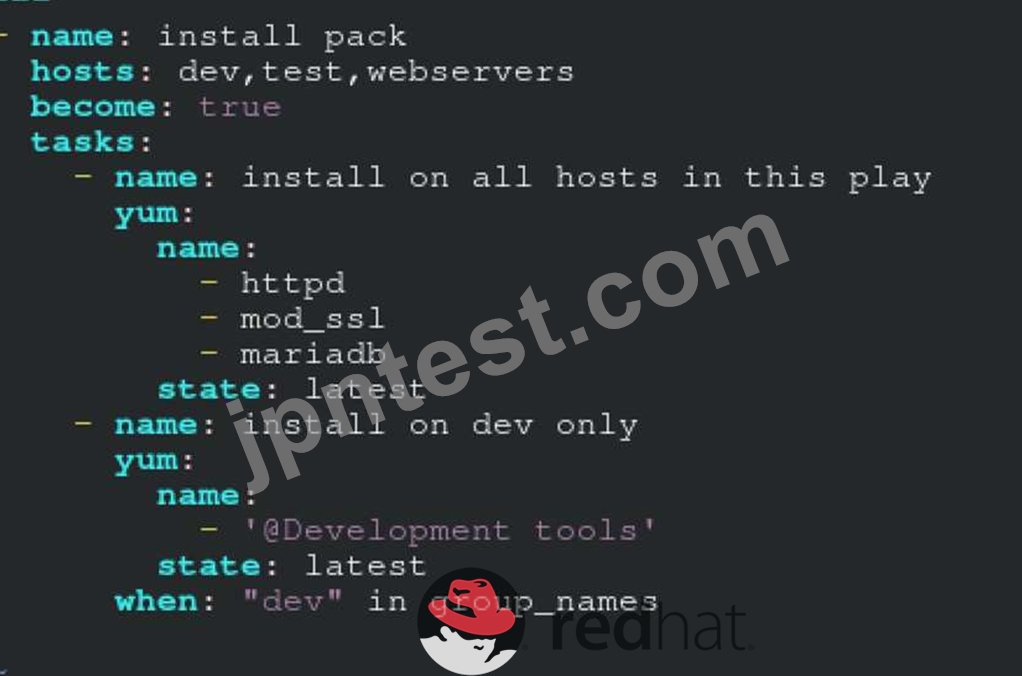
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest
state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
質問 # 28
Create user accounts
------------------------
--> A list of users to be created can be found in the file called user_list.yml
which you should download from http://classroom.example.com/user_list.yml and
save to /home/admin/ansible/
--> Using the password vault created elsewhere in this exam, create a playbook called
create_user.yml
that creates user accounts as follows:
--> Users with a job description of developer should be:
--> created on managed nodes in the "dev" and "test" host groups assigned the
password from the "dev_pass"
variable and these user should be member of supplementary group "devops".
--> Users with a job description of manager should be:
--> created on managed nodes in the "prod" host group assigned the password from
the "mgr_pass" variable
and these user should be member of supplementary group "opsmgr"
--> Passwords should use the "SHA512" hash format. Your playbook should work using
the vault password file
created elsewhere in this exam.
while practising you to create these file hear. But in exam have to download as per
questation.
user_list.yml file consist:
---
user:
- name: user1
job: developer
- name: user2
job: manager
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# wget http://classroom.example.com/user_list.yml
# cat user_list.yml
# vim create_user.yml
---
- name:
hosts: all
vars_files:
- ./user_list.yml
- ./vault.yml
tasks:
- name: creating groups
group:
name: "{{ item }}"
state: present
loop:
- devops
- opsmgr
- name: creating user
user:
name: "{{ item.name }}"
state: present
groups: devops
password: "{{ dev_pass|password_hash ('sha512') }}"
loop: "{{ user }}"
when: (inventory_hostname in groups['dev'] or inventory_hostname in
groups['test']) and item.job == "developer"
- name: creating user
user:
name: "{{ item.name }}"
state: present
groups: opsmgr
password: "{{ mgr_pass|password_hash ('sha512') }}"
loop: "{{ user }}"
when: inventory_hostname in groups['prod'] and item.job == "manager"
:wq!
# ansible-playbook create_user.yml --vault-password-file=password.txt --syntax-check
# ansible-playbook create_user.yml --vault-password-file=password.txt
質問 # 29
Create a file called requirements.yml in /home/sandy/ansible/roles a file called role.yml in /home/sandy/ansible/. The haproxy-role should be used on the proxy host. And when you curl http://node3.example.com it should display "Welcome to node4.example.com" and when you curl again "Welcome to node5.example.com" The php-role should be used on the prod host.
- A. Solution as:
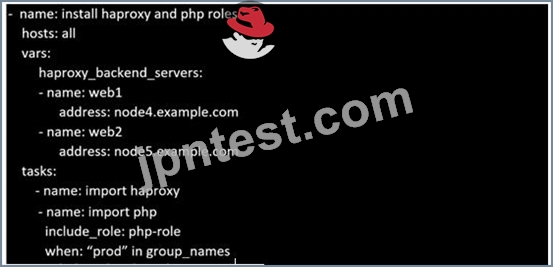
Check the proxy host by curl http://node3.example.com - B. Solution as:
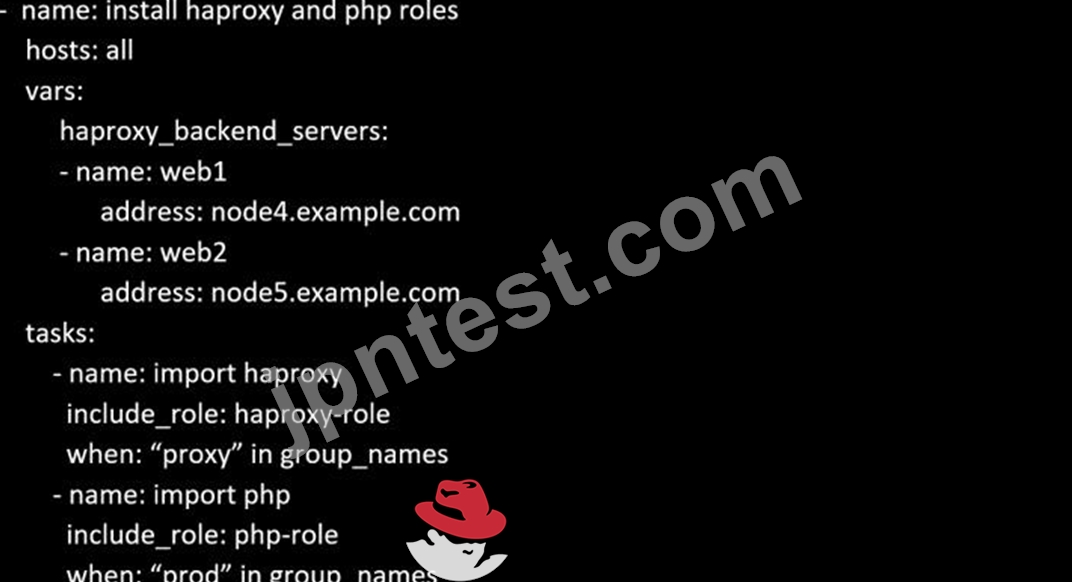
Check the proxy host by curl http://node3.example.com
正解:B
質問 # 30
Create a playbook called balance.yml as follows:
* The playbook contains a play that runs on hosts in balancers host group and uses
the balancer role.
--> This role configures a service to loadbalance webserver requests between hosts
in the webservers host group.curl
--> When implemented, browsing to hosts in the balancers host group (for example
http://node5.example.com) should produce the following output:
Welcome to node3.example.com on 192.168.10.z
--> Reloading the browser should return output from the alternate web server:
Welcome to node4.example.com on 192.168.10.a
* The playbook contains a play that runs on hosts in webservers host group and uses
the phphello role.
--> When implemented, browsing to hosts in the webservers host group with the URL /
hello.php should produce the following output:
Hello PHP World from FQDN
--> where FQDN is the fully qualified domain name of the host. For example,
browsing to http://node3.example.com/hello.php, should produce the following output:
Hello PHP World from node3.example.com
* Similarly, browsing to http://node4.example.com/hello.php, should produce the
following output:
Hello PHP World from node4.example.com
正解:
解説:
Solution as:
# pwd
/home/admin/ansible/
# vim balancer.yml
---
- name: Including phphello role
hosts: webservers
roles:
- ./roles/phphello
- name: Including balancer role
hosts: balancer
roles:
- ./roles/balancer
:wq!
# ansible-playbook balancer.yml --syntax-check
# ansible-playbook balancer.yml
質問 # 31
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
- A. Option
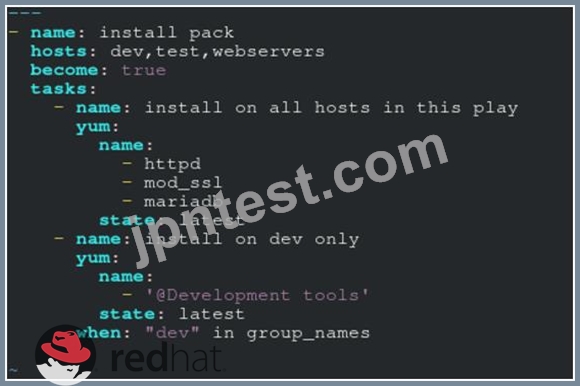
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest - B. Option
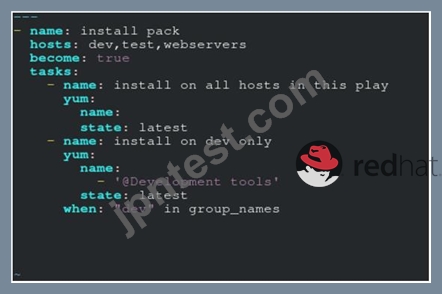
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
正解:A
質問 # 32
Create a file in /home/sandy/ansible/ called report.yml. Using this playbook, get a file called report.txt (make it look exactly as below). Copy this file over to all remote hosts at /root/report.txt. Then edit the lines in the file to provide the real information of the hosts. If a disk does not exist then write NONE.
正解:
解説:
Solution as:
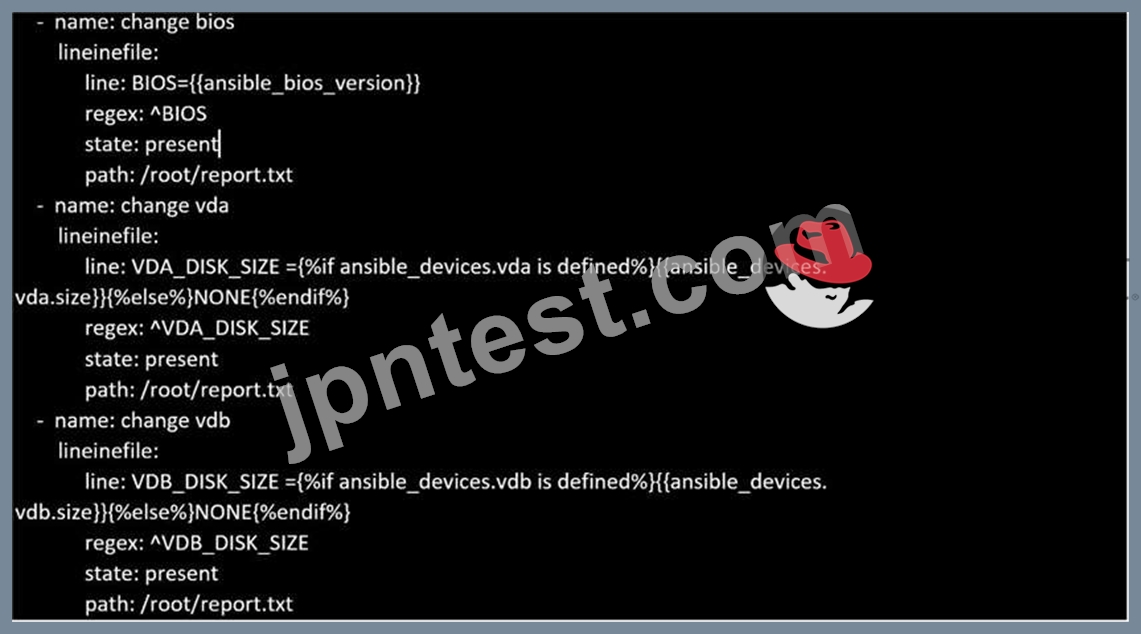
質問 # 33
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all managed nodes: If host is a member of (lev then write "Development" If host is a member of test then write "Test" If host is a member of prod then write "Production"
- A. Solution as:
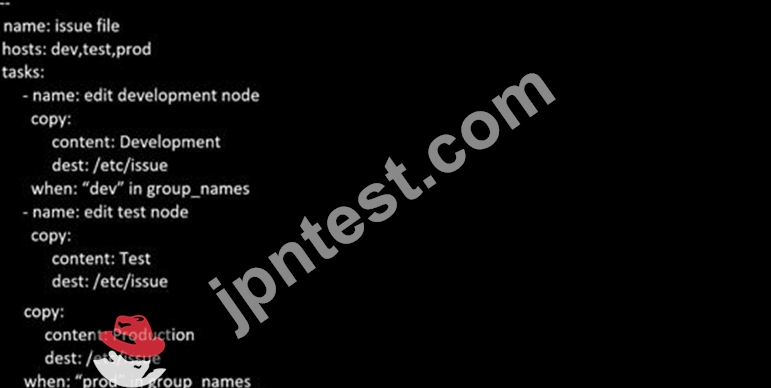
- B. Solution as:

正解:B
質問 # 34
Create an empty encrypted file called myvault.yml in /home/sandy/ansible and set the password to notsafepw. Rekey the password to iwejfj2221.
正解:
解説:
ansible-vault create myvault.yml
Create new password: notsafepw Confirm password: notsafepw ansible-vault rekey myvault.yml
Current password: notsafepw New password: iwejfj2221 Confirm password: iwejfj2221
質問 # 35
Create Logical volumes with lvm.yml in all nodes according to following
requirements.
----------------------------------------------------------------------------------------
* Create a new Logical volume named as 'data'
* LV should be the member of 'research' Volume Group
* LV size should be 1500M
* It should be formatted with ext4 file-system.
--> If Volume Group does not exist then it should print the message "VG Not found"
--> If the VG can not accommodate 1500M size then it should print "LV Can not be
created with
following size", then the LV should be created with 800M of size.
--> Do not perform any mounting for this LV.
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# vim lvm.yml
---
- name:
hosts: all
ignore_errors: yes
tasks:
- name:
lvol:
lv: data
vg: research
size: "1500"
- debug:
msg: "VG Not found"
when: ansible_lvm.vgs.research is not defined
- debug:
msg: "LV Can not be created with following size"
when: ansible_lvm.vgs.research.size_g < "1.5"
- name:
lvol:
lv: data
vg: research
size: "800"
when: ansible_lvm.vgs.research.size_g < "1.5"
- name:
filesystem:
fstype: ext4
dev: /dev/research/data
:wq!
# ansible-playbook lvm.yml --syntax-check
# ansible-playbook lvm.yml
質問 # 36
......
EX294試験解答問題集:https://www.jpntest.com/shiken/EX294-mondaishu(35問題と解答)
