EX294試験問題集を使って一日でRHCE試験合格目指す(最新の35解答)
EX294試験正確な問題集、学習ノートと理論
RedHat EX294試験は、RHEL 8の管理に関連する幅広いトピックをカバーしています。これらのトピックには、ネットワークサービス、ストレージ、セキュリティ、仮想化の設定、管理、トラブルシューティングが含まれます。試験はまた、Ansibleなどの自動化ツールを使用してシステム管理タスクを効率化するITプロフェッショナルの知識とスキルを評価します。さらに、試験は、RHEL 8システムにさまざまなアプリケーションやサービスをインストールおよび構成するITプロフェッショナルの能力を評価します。
Red HatのEX294試験は、システムの設定と管理、ネットワークサービス、セキュリティ、仮想化、および自動化など、幅広いトピックをカバーしています。候補者は、これらのトピックについての深い理解力と、複雑な問題をトラブルシューティングして解決する能力を持っていることが期待されています。この試験は、実践的なスキルと理論的な知識の両方をテストするよう設計されており、候補者は自分のスキルを実世界のシナリオに適用する能力を示すことが期待されます。
質問 # 21
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd, enables and starts the firewall and allows the webserver service. Create a template called index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the content of the file changes, restart the webserver service.
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with the ip address of the node using ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role to serve the index file on webserver hosts.
正解:
解説:
/home/sandy/ansible/apache.yml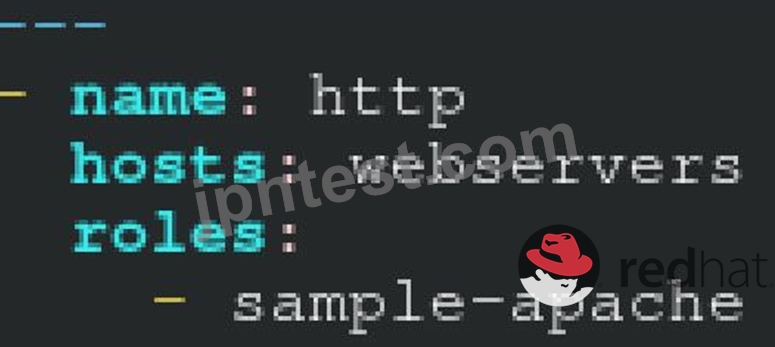
/home/sandy/ansible/roles/sample-apache/tasks/main.yml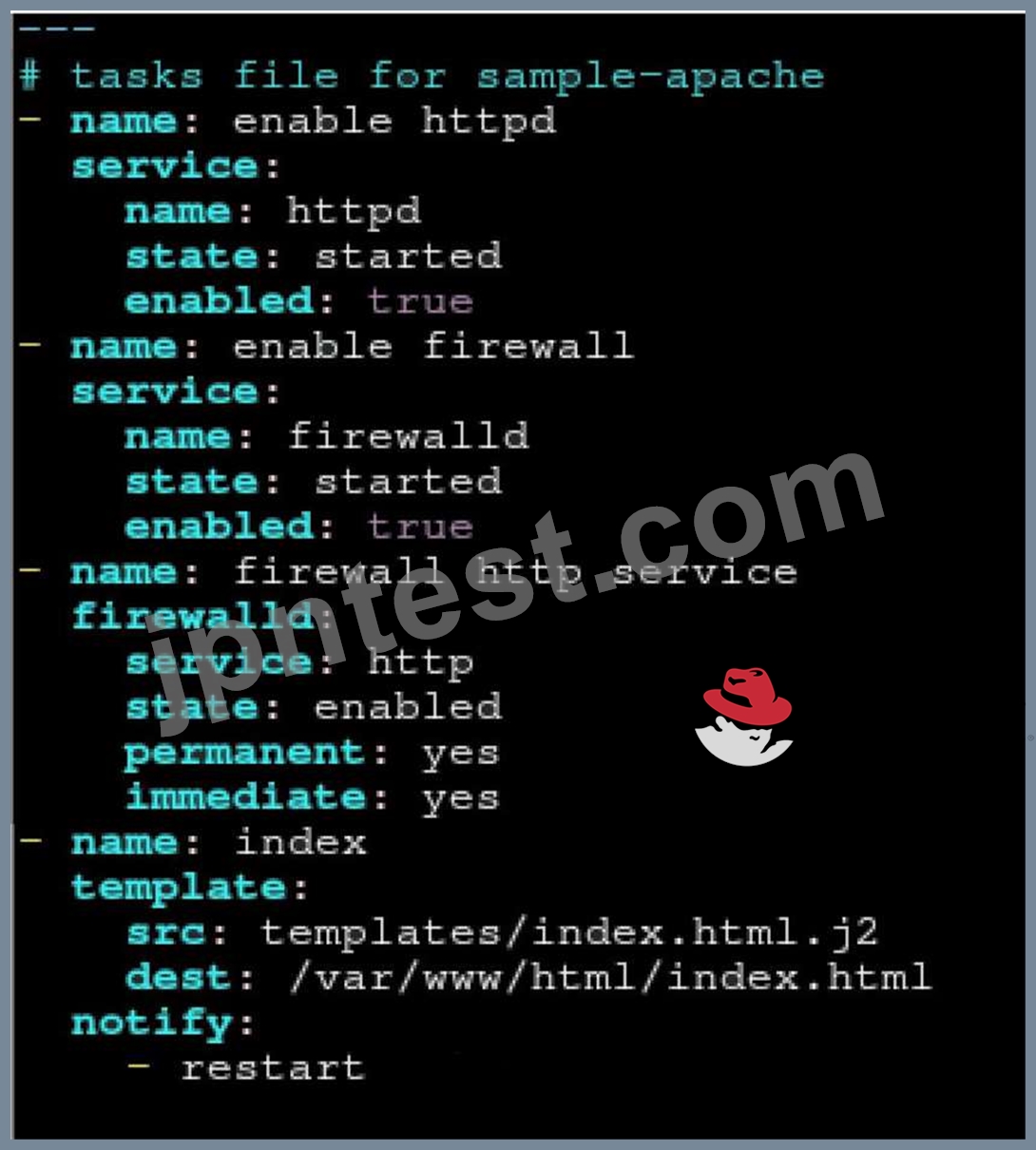
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
質問 # 22
Create a playbook called balance.yml as follows:
* The playbook contains a play that runs on hosts in balancers host group and uses
the balancer role.
--> This role configures a service to loadbalance webserver requests between hosts
in the webservers host group.curl
--> When implemented, browsing to hosts in the balancers host group (for example
http://node5.example.com) should produce the following output:
Welcome to node3.example.com on 192.168.10.z
--> Reloading the browser should return output from the alternate web server:
Welcome to node4.example.com on 192.168.10.a
* The playbook contains a play that runs on hosts in webservers host group and uses
the phphello role.
--> When implemented, browsing to hosts in the webservers host group with the URL /
hello.php should produce the following output:
Hello PHP World from FQDN
--> where FQDN is the fully qualified domain name of the host. For example,
browsing to http://node3.example.com/hello.php, should produce the following output:
Hello PHP World from node3.example.com
* Similarly, browsing to http://node4.example.com/hello.php, should produce the
following output:
Hello PHP World from node4.example.com
正解:
解説:
Solution as:
# pwd
/home/admin/ansible/
# vim balancer.yml
---
- name: Including phphello role
hosts: webservers
roles:
- ./roles/phphello
- name: Including balancer role
hosts: balancer
roles:
- ./roles/balancer
:wq!
# ansible-playbook balancer.yml --syntax-check
# ansible-playbook balancer.yml
質問 # 23
Install and configure Ansible on the control-node control.realmX.example.com as
follows:
-------------------------------------------------------------------------------------------
--> Install the required packages
--> Create a static inventory file called /home/admin/ansible/inventory as follows:
node1.realmX.example.com is a member of the dev host group
node2.realmX.example.com is a member of the test host group
node3.realmX.example.com & node4.realmX.example.com are members of the prod
host group
node5.realmX.example.com is a member of the balancers host group.
prod group is a member of the webservers host group
--> Create a configuration file called ansible.cfg as follows:
--> The host inventory file /home/admin/ansible/inventory is defined
--> The location of roles used in playbooks is defined as /home/admin/ansible/ roles
正解:
解説:
Solution as:
Through physical host, login to workstation.lab.example.com with user root.
# ssh [email protected]
# hostname
workstation.lab.example.com
# yum install platform-python*
# su - admin
# pwd
/home/admin/
# vim .vimrc
# mkdir -p ansible/roles
# cd ansible
# vim inventory
[dev]
servera.lab.example.com
[test]
serverb.example.com
[prod]
serverc.example.com
serverd.example.com
[balancer]
serverd.lab.example.com
[webservers:children]
prod
:!wq
# vim ansible.cfg
[defaults]
inventory = ./inventory
role_path = ./roles
remote_user = admin
ask_pass = false
[privilege_escalation]
become = true
become_method = sudo
become_user = root
become_ask_pass = false
:!wq
# ansible all --list-hosts
質問 # 24
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the second php-role. The roles should be installed in /home/sandy/ansible/roles.
- A. in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles - B. in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles
正解:A
質問 # 25
Create a file called requirements.yml in /home/sandy/ansible/roles to install two roles. The source for the first role is geerlingguy.haproxy and geerlingguy.php. Name the first haproxy-role and the second php-role. The roles should be installed in /home/sandy/ansible/roles.
正解:
解説:
in /home/sandy/ansible/roles
vim requirements.yml
Run the requirements file from the roles directory:
ansible-galaxy install -r requirements.yml -p /home/sandy/ansible/roles
質問 # 26
Create an ansible vault password file called lock.yml with the password reallysafepw in the /home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called secret.txt which contains the password for lock.yml.
正解:
解説:
ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
質問 # 27
Create a file called adhoc.sh in /home/sandy/ansible which will use adhoc commands to set up a new repository.
The name of the repo will be 'EPEL' the description 'RHEL8' the baseurl is 'https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rmp' there is no gpgcheck, but you should enable the repo.
* You should be able to use an bash script using adhoc commands to enable repos.
Depending on your lab setup, you may need to make this repo "state=absent" after you pass this task.
正解:
解説:
chmod 0777 adhoc.sh
vim adhoc.sh
#I/bin/bash
ansible all -m yum_repository -a 'name=EPEL description=RHEL8
baseurl=https://dl.fedoraproject.org/pub/epel/epel-release-latest-8.noarch.rmp
gpgcheck=no enabled=yes'
質問 # 28
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
正解:
解説:
Solution as:
質問 # 29
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all managed nodes: If host is a member of (lev then write "Development" If host is a member of test then write "Test" If host is a member of prod then write "Production"
正解:
解説:
Solution as:
質問 # 30
Create a playbook called webdev.yml in 'home/sandy/ansible. The playbook will create a directory Avcbdev on dev host. The permission of the directory are 2755 and owner is webdev. Create a symbolic link from /Webdev to /var/www/html/webdev. Serve a file from Avebdev7index.html which displays the text "Development" Curl http://node1.example.com/webdev/index.html to test
正解:
解説:
Solution as: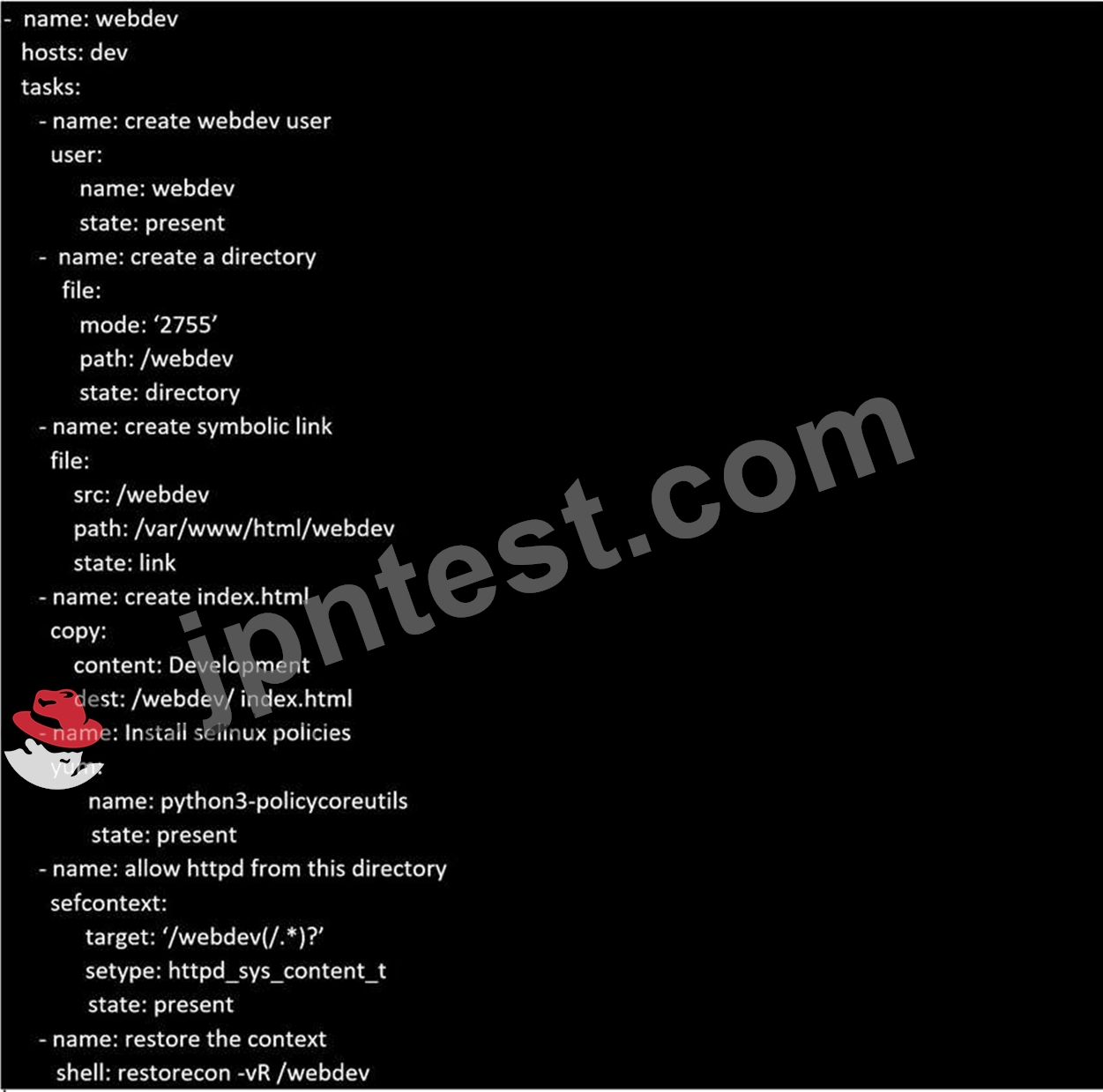
質問 # 31
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd, enables and starts the firewall and allows the webserver service. Create a template called index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the content of the file changes, restart the webserver service.
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with the ip address of the node using ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role to serve the index file on webserver hosts.
- A. Option

/home/sandy/ansible/roles/sample-apache/tasks/main.yml
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
- B. Option

/home/sandy/ansible/roles/sample-apache/tasks/main.yml
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
正解:A
質問 # 32
Create a playbook called packages.yml that:
----------------------------------------------
--> Installs the php and mariadb packages on hosts in the dev, test, and prod host
groups.
--> Installs the Development Tools package group on hosts in the dev host group.
--> Updates all packages to the latest version on hosts in the dev host group.
正解:
解説:
Solution as:
# pwd
home/admin/ansible/
# vim packages.yml
---
- name: Install the packages
hosts: dev,test,prod
vars:
- php_pkg: php
- mariadb_pkg: mariadb
tasks:
- name: install the packages
yum:
name:
- "{{ php_pkg }}"
- "{{ mariadb_pkg }}"
state: latest
- name: install the devops tool packages
hosts: dev
tasks:
- name: install devepment tools
yum:
name: "@Development Tools"
state: latest
- name: upgrade all the packages
yum:
name: "*"
state: latest
exclude: kernel*
!wq
# ansible-playbook package.yml --syntax-check
# ansible-playbook package.yml
質問 # 33
Create a file in /home/sandy/ansible/ called report.yml. Using this playbook, get a file called report.txt (make it look exactly as below). Copy this file over to all remote hosts at /root/report.txt. Then edit the lines in the file to provide the real information of the hosts. If a disk does not exist then write NONE.
- A. Solution as:

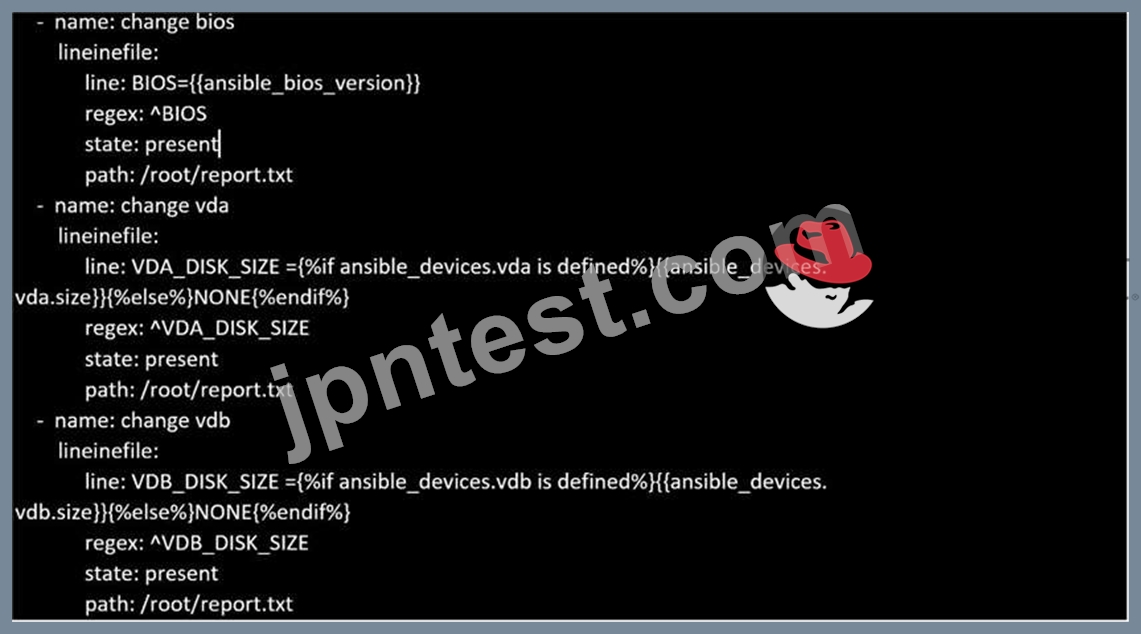
- B. Solution as:
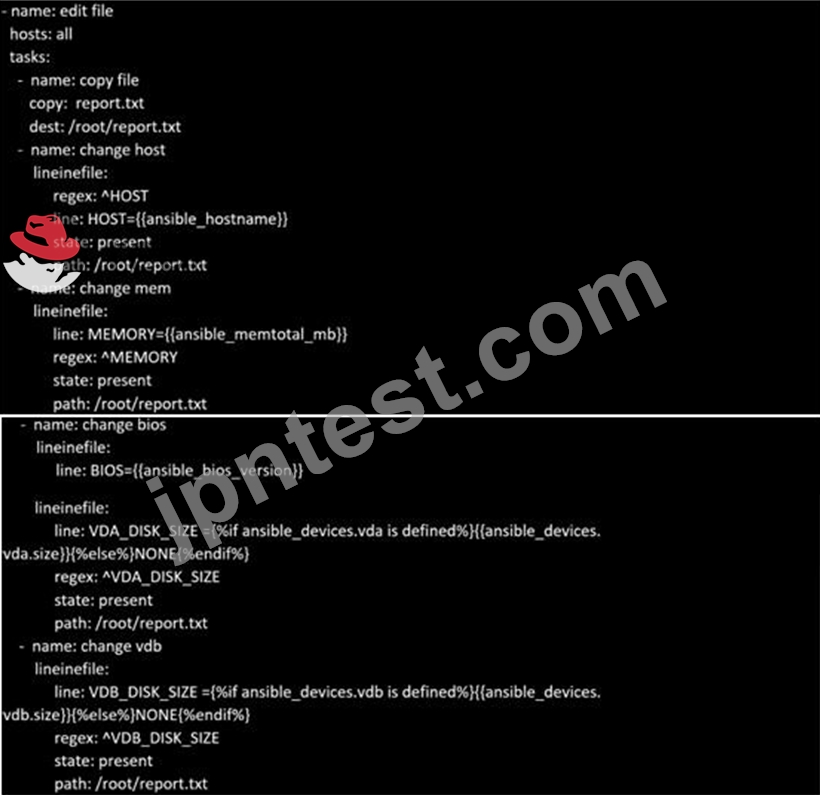
正解:A
質問 # 34
Create an ansible vault password file called lock.yml with the password reallysafepw in the /home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called secret.txt which contains the password for lock.yml.
- A. ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
- B. ansible-vault create lock.yml
New Vault Password: reallysafepw
正解:A
質問 # 35
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes' path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to reflect the appropriate ansible facts.
- A. Solution as:
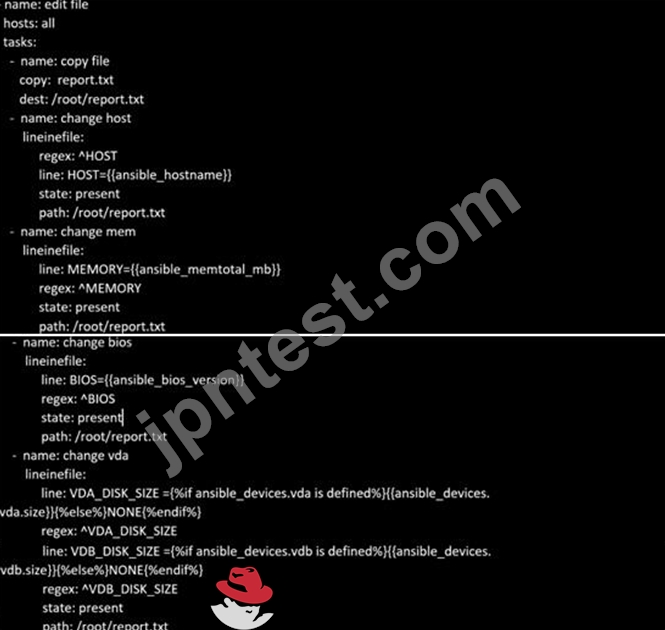
- B. Solution as:


正解:A
質問 # 36
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
- A. Option
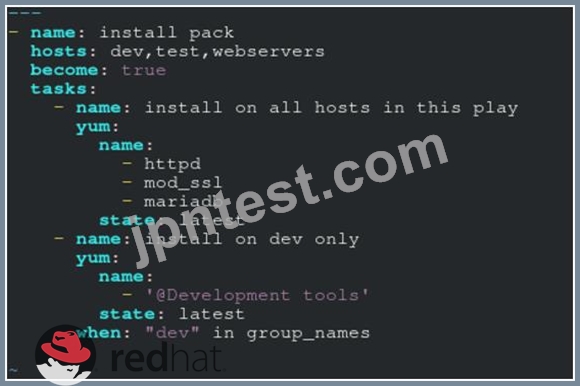
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest - B. Option
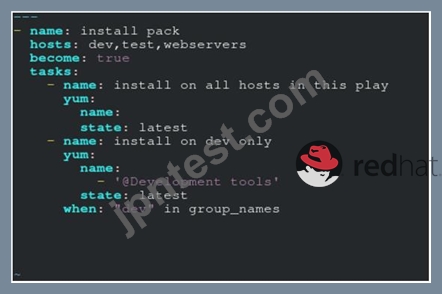
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
正解:A
質問 # 37
......
EX294問題集PDFで最速合格希望EX294:https://www.jpntest.com/shiken/EX294-mondaishu
