EX294のPDF問題集で2023年12月13日試験問題 有効なEX294問題集
究極のEX294準備ガイドで無料最新のRedHat練習テスト問題集
質問 # 12
Create an ansible vault password file called lock.yml with the password reallysafepw in the /home/sandy/ansible directory. In the lock.yml file define two variables. One is pw_dev and the password is 'dev' and the other is pw_mgr and the password is 'mgr' Create a regular file called secret.txt which contains the password for lock.yml.
- A. ansible-vault create lock.yml
New Vault Password: reallysafepw
Confirm: reallysafepw
- B. ansible-vault create lock.yml
New Vault Password: reallysafepw
正解:A
質問 # 13
Create an Ansible vault to store user passwords as follows:
* The name of the vault is valut.yml
* The vault contains two variables as follows:
- dev_pass with value wakennym
- mgr_pass with value rocky
* The password to encrypt and decrypt the vault is atenorth
* The password is stored in the file /home/admin/ansible/password.txt
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# echo "atenorth" >password.txt
# chmod 0600 password.txt
# ansible-vault create vault.yml --vault-password-file=password.txt
---
- dev_pass: wakennym
- mgr_pass: rocky
:wq
# cat vault.yml
$ANSIBLE_VAULT;1.1;AES256
36383862376164316436353665343765643331393433373564613762666531313034336438353662
3464346331346461306337633632393563643531376139610a343531326130663266613533633562
38623439316631306463623761343939373263333134353264333834353264343934373765643737
3535303630626666370a643663366634383863393338616661666632353139306436316430616334
65386134393363643133363738656130636532346431376265613066326162643437643064313863
6633333537303334333437646163343666666132316639376531
# ansible-vault view vault.yml
password:******
---
- dev_pass: wakennym
- mgr_pass: rocky
質問 # 14
Create a playbook called web.yml as follows:
* The playbook runs on managed nodes in the "dev" host group
* Create the directory /webdev with the following requirements:
--> membership in the apache group
--> regular permissions: owner=r+w+execute, group=r+w+execute, other=r+execute
s.p=set group-id
* Symbolically link /var/www/html/webdev to /webdev
* Create the file /webdev/index.html with a single line of text that reads:
"Development"
--> it should be available on http://servera.lab.example.com/webdev/index.html
正解:
解説:
Solution as:
# pwd
/home/admin/ansible/
# vim web.yml
---
- name:
hosts: dev
tasks:
- name: create group
yum:
name: httpd
state: latest
- name: create group
group:
name: apache
state: present
- name: creating directiory
file:
path: /webdev
state: directory
mode: '2775'
group: apache
- sefcontext:
target: '/webdev/index.html'
setype: httpd_sys_content_t
state: present
- name: Apply new SELinux file context to filesystem
command: restorecon -irv
- name: creating symbolic link
file:
src: /webdev
dest: /var/www/html/webdev
state: link
force: yes
- name: creating file
file:
path: /webdev/index.html
sate: touch
- name: Adding content to index.html file
copy:
dest: /webdev/index.html
content: "Development"
- name: add service to the firewall
firewalld:
service: http
permanent: yes
state: enabled
immediate: yes
- name: active http service
service:
name: httpd
state: restarted
enabled: yes
:wq
# ansible-playbook web.yml --syntax-check
# ansible-playbook web.yml
質問 # 15
Create a playbook /home/bob /ansible/motd.yml that runs on all inventory hosts and docs the following: The playbook should replaee any existing content of/etc/motd in the following text. Use ansible facts to display the FQDN of each host
On hosts in the dev host group the line should be "Welcome to Dev Server FQDN".
On hosts in the webserver host group the line should be "Welcome to Apache Server FQDN".
On hosts in the database host group the line should be "Welcome to MySQL Server FQDN".
正解:
解説:
/home/sandy/ansible/apache.yml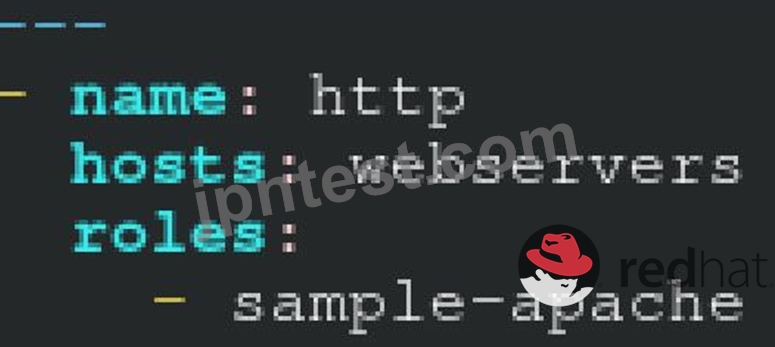
/home/sandy/ansible/roles/sample-apache/tasks/main.yml
Topic 2, LAB SETUP - 2
control.realmX.example.com _ workstation.lab.example.com
node1.realmX.example.com _ servera.lab.example.com
node2.realmX.example.com _ serverb.lab.example.com
node3.realmX.example.com _ serverc.lab.example.com
node4.realmX.example.com _ serverd.lab.example.com
node5.realmX.example.com
- username:root, password:redhat
- username:admin, password:redhat
note1. don't change 'root' or 'admin' password.
note2. no need to create ssh-keygen for access, its pre-defined
note3. SELinux is in enforcing mode and firewalld is disabled/stop on whole managed hosts.
質問 # 16
Use Ansible Galaxy with a requirements file called /home/admin/ansible/roles/
install.yml to download and install roles to /home/admin/ansible/roles from the
following URLs:
http:// classroom.example.com /role1.tar.gz The name of this role should be balancer
http:// classroom.example.com /role2.tar.gz The name of this role should be phphello
正解:
解説:
Solution as:
# pwd
/home/admin/ansible/roles
# vim install.yml
---
- src: http://classroom.example.com/role1.tar.gz
name: balancer
- src: http://classroom.example.com/role2.tar.gz
name: phphello
:wq!
# pwd
/home/admin/ansible
# ansible-galaxy install -r roles/install.yml -p roles
質問 # 17
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in /home/sandy/ansible/invenlory.
You will have access to 5 nodes.
node1.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
正解:
解説:
In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
[proxy]
node3 .example.com
[prod]
node4.example.com
node5 .example.com
[webservers:children]
prod
質問 # 18
Install and configure ansible
User bob has been created on your control node. Give him the appropriate permissions on the control node. Install the necessary packages to run ansible on the control node.
Create a configuration file /home/bob/ansible/ansible.cfg to meet the following requirements:
* The roles path should include /home/bob/ansible/roles, as well as any other path that may be required for the course of the sample exam.
* The inventory file path is /home/bob/ansible/inventory.
* Ansible should be able to manage 10 hosts at a single time.
* Ansible should connect to all managed nodes using the bob user.
Create an inventory file for the following five nodes:
nodel.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node1 is a member of group dev. nodc2 is a member of group test, nodc3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
正解:
解説:
In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
[proxy]
node3 .example.com
[prod]
node4.example.com
node5 .example.com
[webservers:children]
prod
質問 # 19
Create a playbook called timesvnc.yml in /home/sandy/ansible using rhel system role timesync. Set the time to use currently configured nip with the server 0.uk.pool.ntp.org. Enable burst. Do this on all hosts.
- A. Solution as:

- B. Solution as:

正解:A
質問 # 20
Modify file content.
------------------------
Create a playbook called /home/admin/ansible/modify.yml as follows:
* The playbook runs on all inventory hosts
* The playbook replaces the contents of /etc/issue with a single line of text as
follows:
--> On hosts in the dev host group, the line reads: "Development"
--> On hosts in the test host group, the line reads: "Test"
--> On hosts in the prod host group, the line reads: "Production"
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# vim modify.yml
---
- name:
hosts: all
tasks:
- name:
copy:
content: "Development"
dest: /etc/issue
when: inventory_hostname in groups['dev']
- name:
copy:
content: "Test"
dest: /etc/issue
when: inventory_hostname in groups['test']
- name:
copy:
content: "Production"
dest: /etc/issue
when: inventory_hostname in groups['prod']
:wq
# ansible-playbook modify.yml --syntax-check
# ansible-playbook modify.yml
質問 # 21
Create a playbook called regulartasks.yml which has the system that append the date to /root/datefile every day at noon. Name is job 'datejob'
- A. Solution as:

- B. Solution as:

正解:A
質問 # 22
Create a playbook called issue.yml in /home/sandy/ansible which changes the file /etc/issue on all managed nodes: If host is a member of (lev then write "Development" If host is a member of test then write "Test" If host is a member of prod then write "Production"
- A. Solution as:

- B. Solution as:
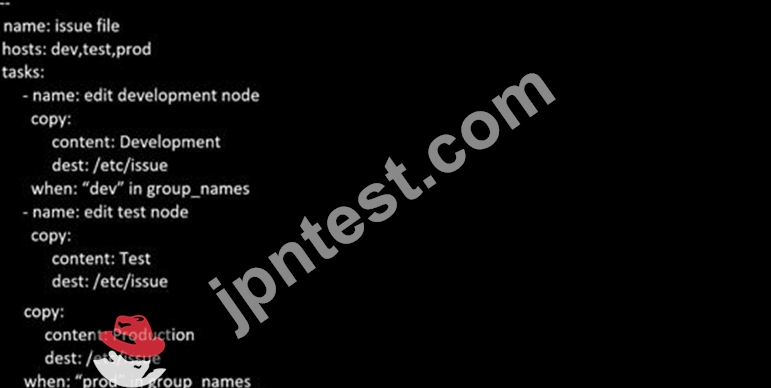
正解:A
質問 # 23
Create a file called packages.yml in /home/sandy/ansible to install some packages for the following hosts. On dev, prod and webservers install packages httpd, mod_ssl, and mariadb. On dev only install the development tools package. Also, on dev host update all the packages to the latest.
正解:
解説:
Solution as: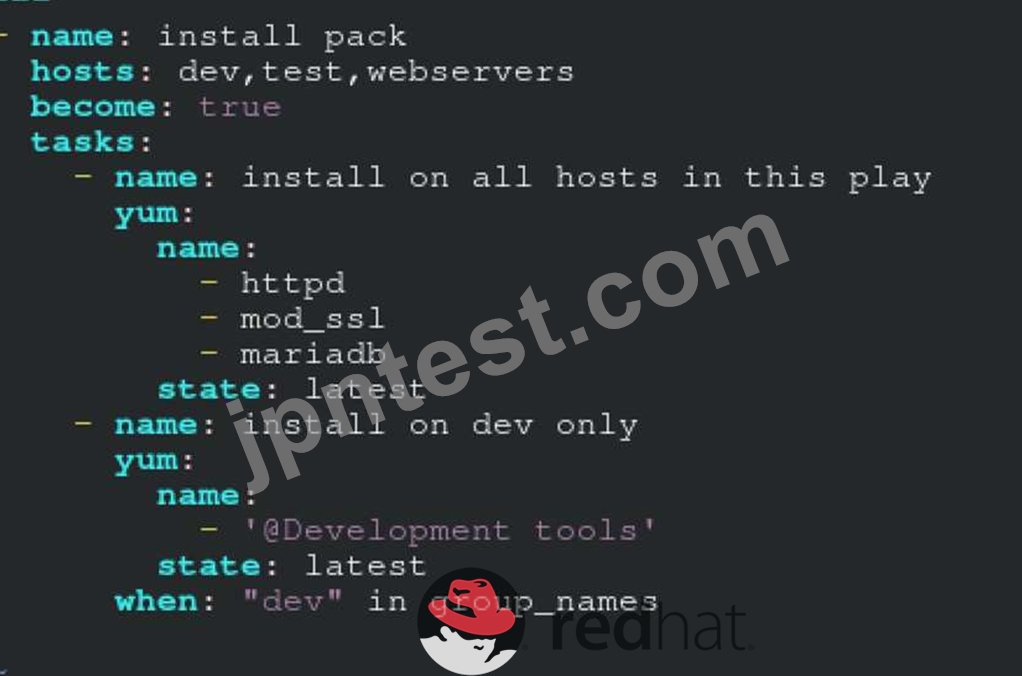
** NOTE 1 a more acceptable answer is likely 'present' since it's not asking to install the latest
state: present
** NOTE 2 need to update the development node
- name: update all packages on development node
yum:
name: '*'
state: latest
質問 # 24
Create a playbook /home/bob /ansible/motd.yml that runs on all inventory hosts and docs the following: The playbook should replaee any existing content of/etc/motd in the following text. Use ansible facts to display the FQDN of each host On hosts in the dev host group the line should be "Welcome to Dev Server FQDN".
On hosts in the webserver host group the line should be "Welcome to Apache Server FQDN".
On hosts in the database host group the line should be "Welcome to MySQL Server FQDN".
- A. /home/sandy/ansible/apache.yml
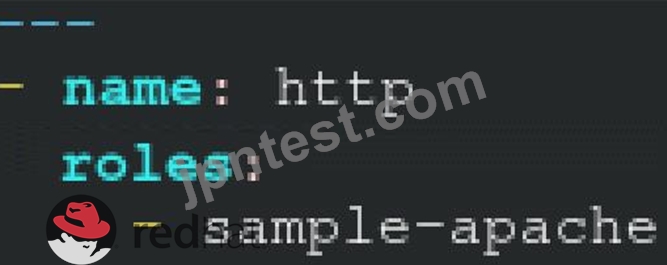
/home/sandy/ansible/roles/sample-apache/tasks/main.yml - B. /home/sandy/ansible/apache.yml

/home/sandy/ansible/roles/sample-apache/tasks/main.yml
正解:B
質問 # 25
Install and configure ansible
User sandy has been created on your control node with the appropriate permissions already, do not change or modify ssh keys. Install the necessary packages to run ansible on the control node. Configure ansible.cfg to be in folder /home/sandy/ansible/ansible.cfg and configure to access remote machines via the sandy user. All roles should be in the path /home/sandy/ansible/roles. The inventory path should be in /home/sandy/ansible/invenlory.
You will have access to 5 nodes.
node1.example.com
node2.example.com
node3.example.com
node4.example.com
node5.example.com
Configure these nodes to be in an inventory file where node I is a member of group dev. nodc2 is a member of group test, node3 is a member of group proxy, nodc4 and node 5 are members of group prod. Also, prod is a member of group webservers.
- A. In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_method=sudo
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
[proxy]
node3 .example.com
[prod]
node4.example.com
node5 .example.com
[webservers:children]
prod - B. In/home/sandy/ansible/ansible.cfg
[defaults]
inventory=/home/sandy/ansible/inventory
roles_path=/home/sandy/ansible/roles
remote_user= sandy
host_key_checking=false
[privilegeescalation]
become=true
become_user=root
become_ask_pass=false
In /home/sandy/ansible/inventory
[dev]
node 1 .example.com
[test]
node2.example.com
node4.example.com
node5 .example.com
[webservers:children]
prod
正解:A
質問 # 26
In /home/sandy/ansible/ create a playbook called logvol.yml. In the play create a logical volume called Iv0 and make it of size 1500MiB on volume group vgO If there is not enough space in the volume group print a message "Not enough space for logical volume" and then make a 800MiB Iv0 instead. If the volume group still doesn't exist, create a message "Volume group doesn't exist" Create an xfs filesystem on all Iv0 logical volumes. Don't mount the logical volume.
正解:
解説:
Solution as: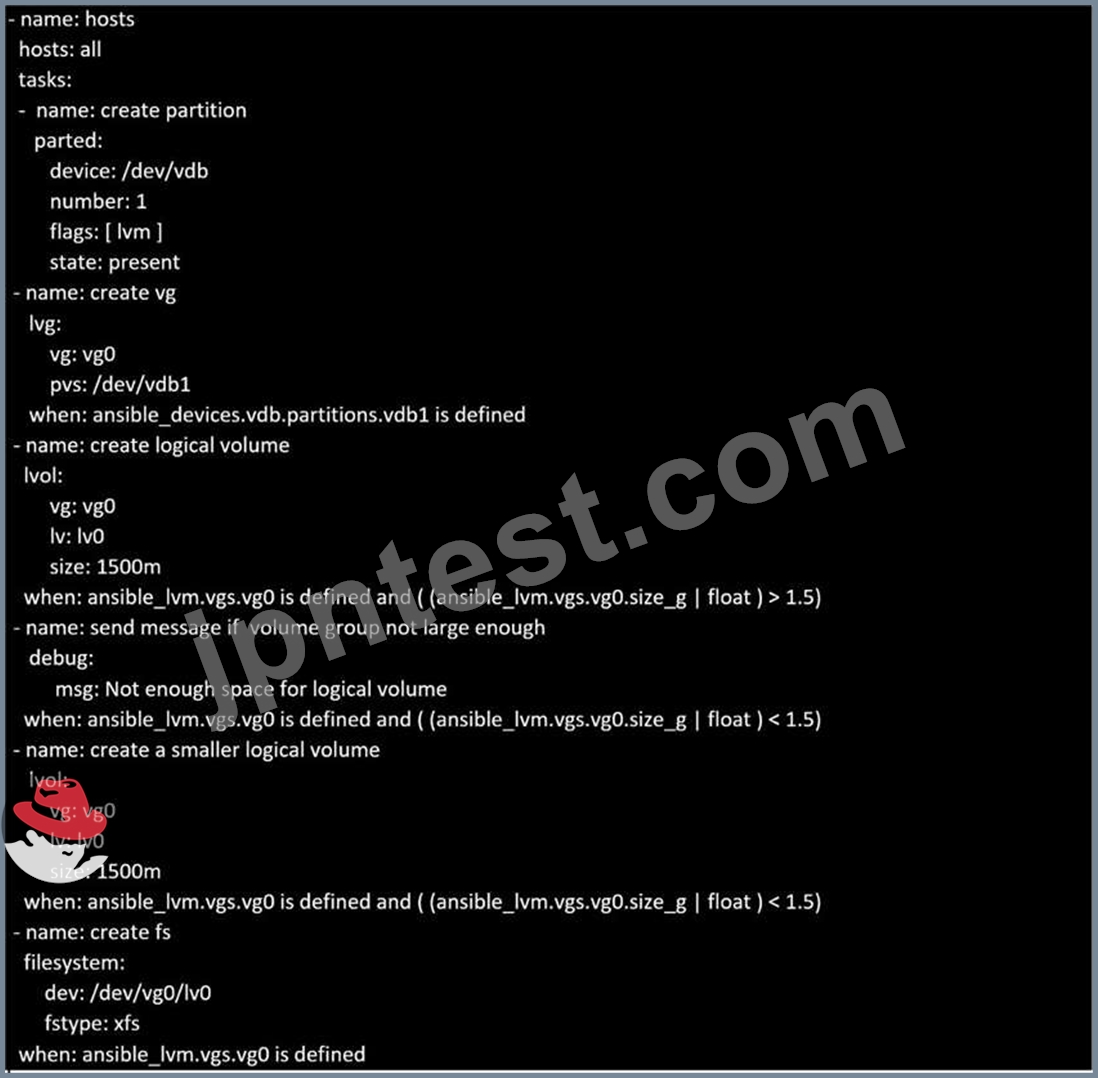
Topic 1, LAB SETUP
You will need to set up your lab by creating 5 managed nodes and one control node.
So 6 machines total. Download the free RHEL8 iso from Red Hat Developers website.
***Control node you need to set up***
You need to create some static ips on your managed nodes then on the control node set them up in the
/etc/hosts file as follows:
vim /etc/hosts
10.0.2.21 node1.example.com
10.0.2.22 node2.example.com
10.0.2.23 node3.example.com
10.0.2.24 node4.example.com
10.0.2.25 node5.example.com
yum -y install ansible
useradd ansible
echo password | passwd --stdin ansible
echo "ansible ALL=(ALL) NOPASSWD:ALL
su - ansible; ssh-keygen
ssh-copy-id node1.example.com
ssh-copy-id node2.example.com
ssh-copy-id node3.example.com
ssh-copy-id node4.example.com
ssh-copy-id node5.example.com
***Each manage node setup***
First, add an extra 2GB virtual harddisk to each control node 1,2,3. Then add an extra hard disk to control
node 4. Do not add an extra hard disk to node 5. When you start up these machines the extra disks should be
automatically located at /dev/sdb (or /dev/vdb depending on your hypervisor).
useradd ansible
echo password | passwd --stdin ansible
echo "ansible ALL=(ALL) NOPASSWD:ALL" > /etc/sudoers.d/ansible
Note python3 should be installed by default, however if it is not then on both the control node and managed
nodes you can install it also set the default python3 if you are having trouble with python2 being the default.
yum -y install python3
alternatives --set python /usr/bin/python3
All machines need the repos available. You did this in RHSCA. To set up locally you just need to do the same
for each machine. Attach the rhel8 iso as a disk to virtualbox, kvm or whatever hypervisor you are using (this
will be /dev/sr0). Then inside the machine:
mount /dev/sr0 to /mnt
Then you will have all the files from the iso in /mnt.
mkdir /repo
cp -r /mnt /repo
vim /etc/yum.repos.d/base.repo
Inside this file:
[baseos]
name=baseos
baseurl=file:///repo/BaseOS
gpgcheck=0
Also the appstream
vim /etc/yum.repos.d/appstream.repo
Inside this file:
[appstream]
name=appstream
baseurl=file:///repo/AppStream
gpgcheck=0
質問 # 27
Create a playbook that changes the default target on all nodes to multi-user tarqet. Do this in playbook file called target.yml in /home/sandy/ansible
- A. - name: change default target
hosts: all
- name: change target
file:
src: /usr/lib/systemd/system/multi-user.target dest: /etc/systemd/system/default.target state: link - B. - name: change default target
hosts: all
tasks:
- name: change target
file:
src: /usr/lib/systemd/system/multi-user.target dest: /etc/systemd/system/default.target state: link
正解:B
質問 # 28
Create and run an Ansible ad-hoc command.
--> As a system administrator, you will need to install software on the managed
nodes.
--> Create a shell script called yum-pack.sh that runs an Ansible ad-hoc command to
create yum-repository on each of the managed nodes as follows:
--> repository1
-----------
1. The name of the repository is EX407
2. The description is "Ex407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEYredhat-
release
6. The repository is enabled
--> repository2
-----------
1. The name of the repository is EXX407
2. The description is "Exx407 Description"
3. The base URL is http://content.example.com/rhel8.0/x86_64/dvd/AppStream/
4. GPG signature checking is enabled
5. The GPG key URL is http://content.example.com/rhel8.0/x86_64/dvd/ RPM-GPG-KEYredhat-
release
6. The repository is enabled
正解:
解説:
Solution as:
# pwd
/home/admin/ansible
# vim yum-pack.sh
#!/bin/bash
ansible all -m yum_repository -a 'name=EX407 description="Ex407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/BaseOS/ gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
ansible all -m yum_repository -a 'name=EXX407 description="Exx407 Description"
baseurl=http://content.example.com/rhel8.0/x86_64/dvd/AppStream/ gpgcheck=yes
gpgkey=http://content.example.com/rhel8.0/x86_64/dvd/RPM-GPG-KEY-redhat-release
enabled=yes'
:!wq
# chmod +x yum-pack.sh
# bash yum-pack.sh
# ansible all -m command -a 'yum repolist all'
質問 # 29
Create an empty encrypted file called myvault.yml in /home/sandy/ansible and set the password to notsafepw. Rekey the password to iwejfj2221.
正解:
解説:
ansible-vault create myvault.yml
Create new password: notsafepw Confirm password: notsafepw ansible-vault rekey myvault.yml
Current password: notsafepw New password: iwejfj2221 Confirm password: iwejfj2221
質問 # 30
In /home/sandy/ansible/ create a playbook called logvol.yml. In the play create a logical volume called Iv0 and make it of size 1500MiB on volume group vgO If there is not enough space in the volume group print a message "Not enough space for logical volume" and then make a 800MiB Iv0 instead. If the volume group still doesn't exist, create a message "Volume group doesn't exist" Create an xfs filesystem on all Iv0 logical volumes. Don't mount the logical volume.
- A. Solution as:
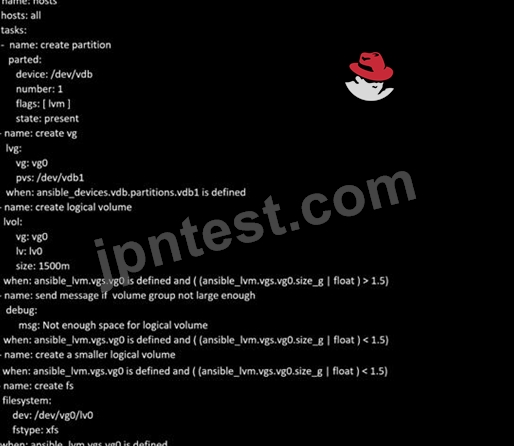
- B. Solution as:

正解:B
質問 # 31
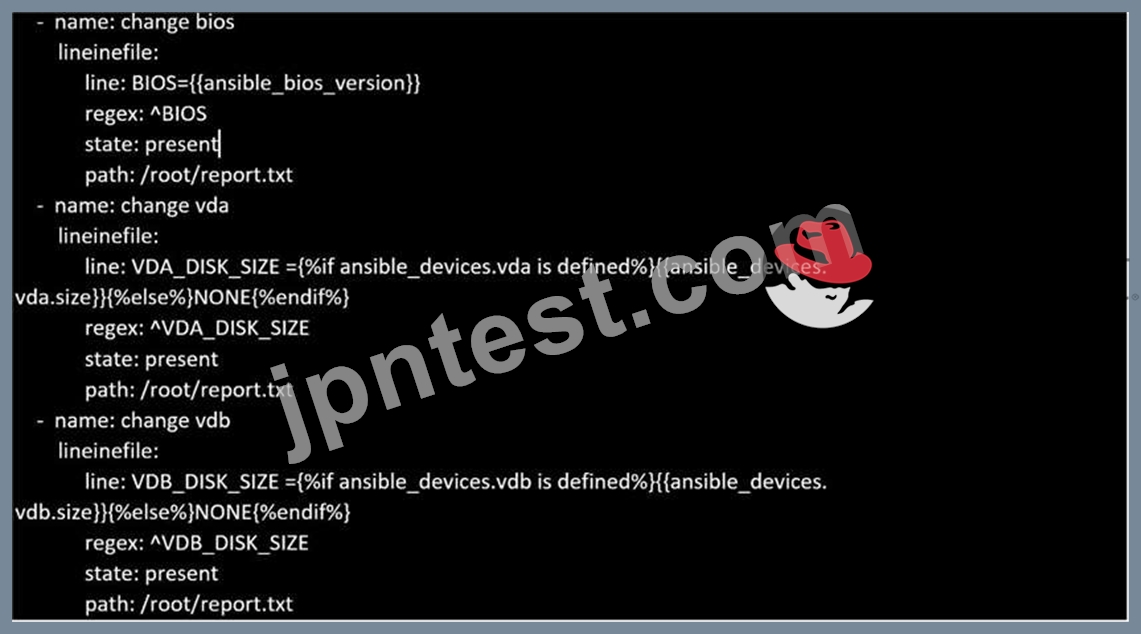
Create a file called specs.empty in home/bob/ansible on the local machine as follows:
HOST=
MEMORY=
BIOS=
VDA_DISK_SIZE=
VDB_DISK_SIZE=
Create the playbook /home/bob/ansible/specs.yml which copies specs.empty to all remote nodes' path /root/specs.txt. Using the specs.yml playbook then edit specs.txt on the remote machines to reflect the appropriate ansible facts.
正解:
解説:
Solution as:
質問 # 32
Create a playbook called webdev.yml in 'home/sandy/ansible. The playbook will create a directory Avcbdev on dev host. The permission of the directory are 2755 and owner is webdev. Create a symbolic link from /Webdev to /var/www/html/webdev. Serve a file from Avebdev7index.html which displays the text "Development" Curl http://node1.example.com/webdev/index.html to test
正解:
解説:
Solution as: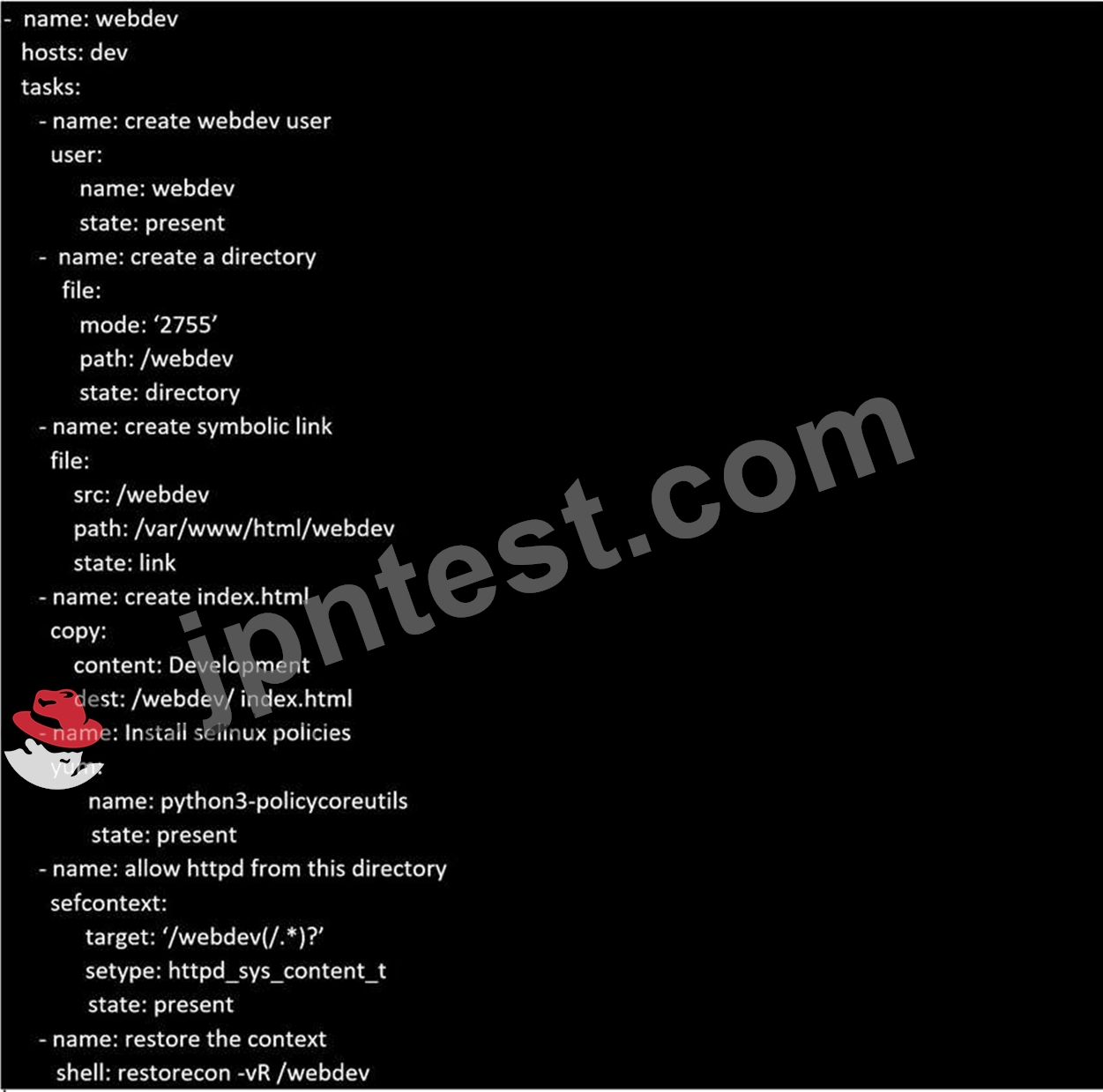
質問 # 33
Create a role called sample-apache in /home/sandy/ansible/roles that enables and starts httpd, enables and starts the firewall and allows the webserver service. Create a template called index.html.j2 which creates and serves a message from /var/www/html/index.html Whenever the content of the file changes, restart the webserver service.
Welcome to [FQDN] on [IP]
Replace the FQDN with the fully qualified domain name and IP with the ip address of the node using ansible facts. Lastly, create a playbook in /home/sandy/ansible/ called apache.yml and use the role to serve the index file on webserver hosts.
- A. Option

/home/sandy/ansible/roles/sample-apache/tasks/main.yml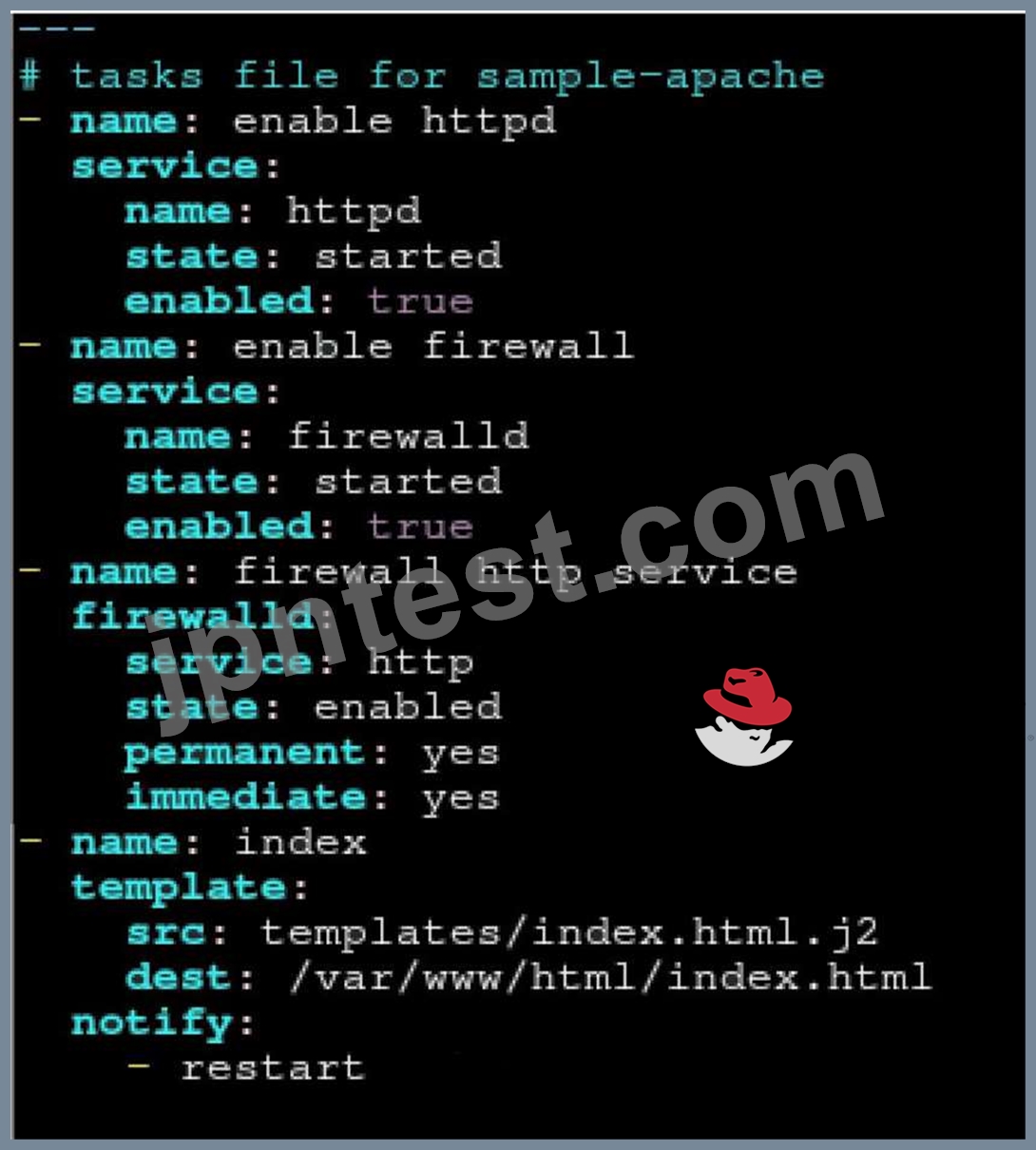
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
- B. Option

/home/sandy/ansible/roles/sample-apache/tasks/main.yml
/home/sandy/ansible/roles/sample-apache/templates/index.html.j2
In /home/sandy/ansible/roles/sample-apache/handlers/main.yml
正解:A
質問 # 34
......
合格率 取得する秘訣はEX294認定試験エンジンPDF:https://www.jpntest.com/shiken/EX294-mondaishu
