問題集を購入するなら最新の2024年01月10日 CS0-002試験問題と解答PDFで一年間無料更新
時間限定無料ダウンロード!最新のCS0-002問題集で2024年最新のCS0-002試験問題
CompTIA CS0-002認定試験の準備をするためには、個人はサイバーセキュリティの概念と原則に強い基盤を持っている必要があります。また、サイバーセキュリティツールやテクノロジーを扱った経験が必要です。この試験に備えるためには、書籍、オンラインコース、模擬試験など、多くのトレーニングプログラムや学習資料が用意されています。
質問 # 87
During a review of the vulnerability scan results on a server, an information security analyst notices the following: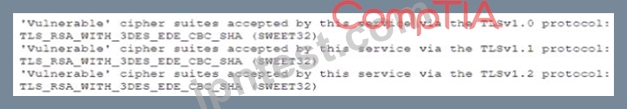
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
- A. SSL/TLS is offloaded to a WAF and load balancer
- B. It only accepts TLSvl 2
- C. It only accepts cipher suites using AES and SHA
- D. It no longer accepts the vulnerable cipher suites
正解:B
質問 # 88
The IT department is concerned about the possibility of a guest device infecting machines on the corporate network or taking down the company's singe internet connection. Which of the following should a security analyst recommend to BEST meet the requirements outlined by the IT Department?
- A. Place a firewall In between the corporate network and the guest network
- B. Configure the IPS with rules that will detect common malware signatures traveling from the guest network.
- C. Configure NAC to only allow machines on the network that are patched and have active antivirus.
- D. Require the guest machines to install the corporate-owned EDR solution.
正解:C
質問 # 89
The help desk has reported that users are reusing previous passwords when prompted to change them.
Which of the following would be the MOST appropriate control for the security analyst to configure to prevent password reuse? (Choose two.)
- A. Implement role-based access control within directory services.
- B. Deploy Group Policy Objects to domain resources.
- C. Deploy a single-sing-on solution for both Windows and Linux hosts.
- D. Implement mandatory access control on all workstations.
- E. Implement scripts to automate the configuration of PAM on Linux hosts.
正解:B、E
質問 # 90
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.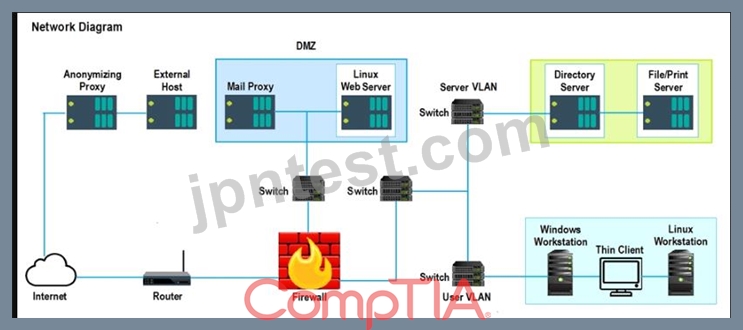
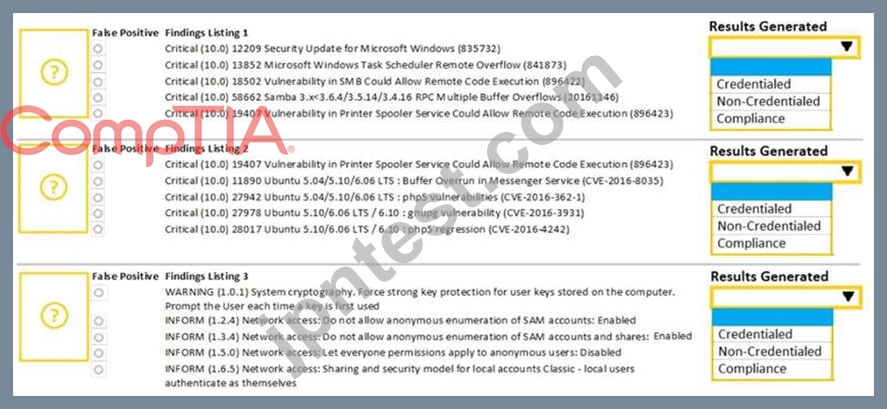
正解:
解説: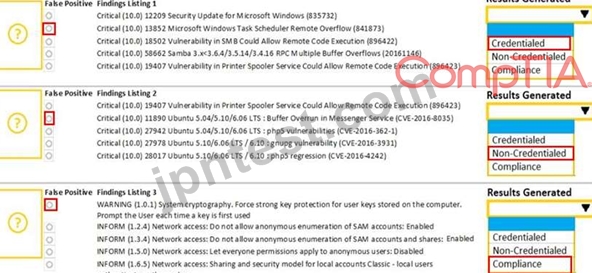
質問 # 91
Which of the following is a switch attack?
- A. XSS
- B. CSRF
- C. MAC overflow
- D. Inference
正解:C
質問 # 92
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
- A. Development phases occurring at multiple sites may produce change management issues.
- B. Moving the FPGAs between development sites will lessen the time that is available for security testing.
- C. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
- D. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
正解:A
解説:
Reference: https://www.eetimes.com/how-to-protect-intellectual-property-in-fpgas-devices-part-1/#
質問 # 93
A company is required to monitor for unauthorized changes to baselines on all assets to comply with industry regulations. Two of the remote units did not recover after scans were performed on the assets. An analyst needs to recommend a solution to prevent recurrence. Which of the following is the best way to satisfy the regulatory requirement without impacting the availability to similar assets and creating an unsustainable process?
- A. Manually review the baselines daily and document the results in a change history log
- B. Purchase new remote units from other vendors with a proven ability to support scanning requirements.
- C. Implement a new scanning technology to satisfy the monitoring requirement and train the team.
- D. Document exceptions with compensating controls to demonstrate the risk mitigation efforts.
正解:D
解説:
A) Manually review the baselines daily and document the results in a change history log is not correct. This option would not prevent the recurrence of the problem, as it does not address the root cause of why the remote units did not recover after scans were performed. Moreover, this option would create an unsustainable process, as it would require a lot of time and resources to manually review and document the baselines of all assets on a daily basis.
C) Implement a new scanning technology to satisfy the monitoring requirement and train the team is not correct. This option would not guarantee that the problem would not recur, as it is possible that the new scanning technology would also cause issues with the remote units or other assets. Furthermore, this option would incur additional costs and efforts to acquire, deploy, and maintain the new scanning technology and train the team on how to use it.
D) Purchase new remote units from other vendors with a proven ability to support scanning requirements is not correct. This option would not be feasible or cost-effective, as it would require replacing all the remote units with new ones from different vendors. This option would also introduce new risks and challenges, such as compatibility, interoperability, or vendor lock-in.
Explanation:
The correct answer is B. Document exceptions with compensating controls to demonstrate the risk mitigation efforts. Compensating controls are alternative or additional controls that are implemented when the primary or required controls are not feasible or effective. Compensating controls can help to reduce the risk to an acceptable level and satisfy the regulatory requirements, as long as they are documented and justified1.
質問 # 94
An organization was alerted to a possible compromise after its proprietary data was found for sale on the Internet. An analyst is reviewing the logs from the next-generation UTM in an attempt to find evidence of this breach. Given the following output: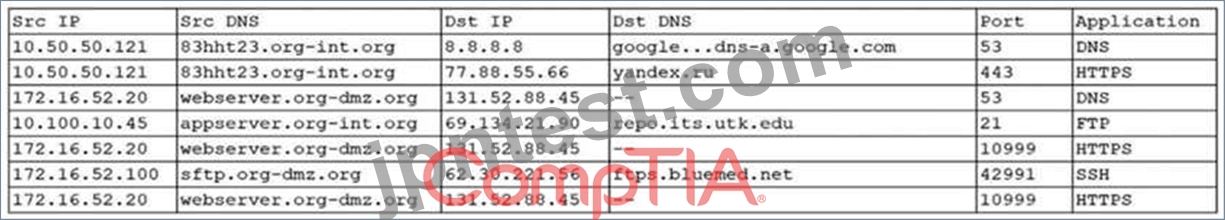
Which of the following should be the focus of the investigation?
- A. sftp.org-dmz.org
- B. ftps.bluemed.net
- C. webserver.org-dmz.org
- D. 83hht23.org-int.org
正解:C
質問 # 95
An organization recently discovered that spreadsheet files containing sensitive financial data were improperly stored on a web server. The management team wants to find out if any of these files were downloaded by pubic users accessing the server. The results should be written to a text file and should induce the date. time, and IP address associated with any spreadsheet downloads. The web server's log file Is named webserver log, and the report We name should be accessreport.txt. Following is a sample of the web servefs.log file:
2017-0-12 21:01:12 GET /index.htlm - @4..102.33.7 - return=200 1622
Which of the following commands should be run if an analyst only wants to include entries in which spreadsheet was successfully downloaded?
- A. more webserver.log | grep -A *.xIs < accessreport.txt
- B. more webserver.log | grep * xIs > accessreport.txt
- C. more webserver.log > grep ''xIs > egrep -E 'success' > accessreport.txt
- D. more webserver.log | grep ' -E ''return=200 | accessreport.txt
正解:D
解説:
The grep command is a tool that searches for a pattern of characters in a file or input and prints the matching lines1 The egrep command is a variant of grep that supports extended regular expressions, which allow more complex and flexible pattern matching2 The more command is a filter that displays the contents of a file or input one screen at a time3 The pipe symbol (|) is used to redirect the output of one command to the input of another command. The redirection symbol (>) is used to redirect the output of a command to a file.
The command given in option C performs the following steps:
It uses the more command to display the contents of the webserver.log file.
It pipes the output of the more command to the grep command, which searches for lines that contain '*.xls', which is a pattern that matches any file name ending with .xls (a spreadsheet file extension).
It pipes the output of the grep command to the egrep command, which searches for lines that contain 'return=200', which is a pattern that matches any HTTP status code of 200 (which indicates a successful request).
It redirects the output of the egrep command to a file named accessreport.txt, which contains the date, time, and IP address associated with any spreadsheet downloads.
質問 # 96
The Chief Information Security Officer (CISO) has decided that all accounts with elevated privileges must use a longer, more complicated passphrase instead of a password. The CISO would like to formally document management's intent to set this control level. Which of the following is the appropriate means to achieve this?
- A. A guideline
- B. A control
- C. A policy
- D. A standard
正解:C
質問 # 97
A software development company in the manufacturing sector has just completed the alpha version of its flagship application. The application has been under development for the past three years. The SOC has seen intrusion attempts made by indicators associated with a particular APT.
The company has a hot site location for COOP. Which of the following threats would most likely incur the BIGGEST economic impact for the company?
- A. DDoS
- B. IP theft
- C. IPS evasion
- D. ICS destruction
正解:A
質問 # 98
Scan results identify critical Apache vulnerabilities on a company's web servers. A security analyst believes many of these results are false positives because the web environment mostly consists of Windows servers.
Which of the following is the BEST method of verifying the scan results?
- A. Perform a top-ports scan against the identified servers.
- B. Run a service discovery scan on the identified servers.
- C. Review logs of each host in the SIEM.
- D. Refer to the identified servers in the asset inventory.
正解:B
質問 # 99
A large software company wants to move as source control and deployment pipelines into a cloud-computing environment. Due to the nature of the business management determines the recovery time objective needs to be within one hour. Which of the following strategies would put the company in the BEST position to achieve the desired recovery time?
- A. Configure a duplicate environment in the same region and load balance between both instances
- B. Set up every cloud component with duplicated copies and auto scaling turned on
- C. Establish an alternate site with active replication to other regions
- D. Create a duplicate copy on premises that can be used for failover in a disaster situation
正解:C
質問 # 100
When of the following techniques can be implemented to safeguard the confidentiality of sensitive information while allowing limited access to authorized individuals?
- A. Masking
- B. Deidentification
- C. Salting
- D. Hashing
正解:A
解説:
https://www.techtarget.com/searchsecurity/definition/data-masking
質問 # 101
A cybersecurity analyst is currently using Nessus to scan several FTP servers. Upon receiving the results of the scan, the analyst needs to further test to verify that the vulnerability found exists.
The analyst uses the following snippet of code:
Which of the following vulnerabilities is the analyst checking for?
- A. SQL injection
- B. Default passwords
- C. Buffer overflow
- D. Format string attack
正解:A
質問 # 102
A security analyst is reviewing a new Internet portal that will be used for corporate employees to obtain their pay statements. Corporate policy classifies pay statement information as confidential, and it must be protected by MFA. Which of the following would best fulfill the MFA requirement while keeping the portal accessible from the internet?
- A. Distributing a shared password that must be provided before the internet portal loads and requiring a username and password
- B. Obtaining home public IP addresses of corporate employees to implement source IP restrictions and requiring a username and password
- C. Requiring the internet portal to be accessible from only the corporate SSO internet endpoint and requiring a smart card and PIN
- D. Moving the internet portal server to a DMZ that is only accessible from the corporate VPN and requiring a username and password
正解:C
解説:
Requiring the internet portal to be accessible from only the corporate SSO internet endpoint and requiring a smart card and PIN. This option provides the best MFA requirement because it uses two factors of authentication: something you have (smart card) and something you know (PIN). It also restricts access to the portal from a trusted source (corporate SSO internet endpoint).
質問 # 103
A security analyst is reviewing a suspected phishing campaign that has targeted an organisation. The organization has enabled a few email security technologies in the last year: however, the analyst believes the security features are not working. The analyst runs the following command:
> dig domain._domainkey.comptia.orq TXT
Which of the following email protection technologies is the analyst MOST likely validating?
- A. DMARC
- B. SPF
- C. DNSSEC
- D. DKIM
正解:B
質問 # 104
Because some clients have reported unauthorized activity on their accounts, a security analyst is reviewing network packet captures from the company's API server. A portion of a capture file is shown below:
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.s/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/">
<request+xmlns:a="http://schemas.somesite.org"+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"></s:Body></s:Envelope> 192.168.1.22 - - api.somesite.com 200 0 1006 1001 0 192.168.1.22 POST /services/v1_0/Public/Members.svc/soap <<a:Password>Password123</a:Password><a:ResetPasswordToken+i:nil="true"/> <a:ShouldImpersonatedAuthenticationBePopulated+i:nil="true"/><a:Username>[email protected]</a:Username></request></Login></s:Body></s:Envelope> 192.168.5.66 - - api.somesite.com 200 0 11558 1712 2024 192.168.4.89 POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/"> <a:IPAddress>516.7.446.605</a:IPAddress><a:ZipCode+i:nil="true"/></request></GetIPLocation></s:Body></s:Envelope> 192.168.1.22 - - api.somesite.com 200 0 1003 1011 307 192.168.1.22 POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.xmlsoap.org/soap/envelope/"><s:Body><IsLoggedIn+xmlns="http://tempuri.org/"> <request+xmlns:a="http://schemas.datacontract.org/2004/07/somesite.web+xmlns:i="http://www.w3.org/2001/XMLSchema-instance"><a:Authentication> <a:ApiToken>kmL4krg2CwwWBan5BReGv5Djb7syxXTNKcWFuSjd</a:ApiToken><a:ImpersonateUserId>0</a:ImpersonateUserId><a:LocationId>161222</a:LocationId> <a:NetworkId>4</a:NetworkId><a:ProviderId>''1=1</a:ProviderId><a:UserId>13026046</a:UserId></a:Authentication></request></IsLoggedIn></s:Body></s:Envelope> 192.168.5.66 - - api.somesite.com 200 0 1378 1209 48 192.168.4.89 Which of the following MOST likely explains how the clients' accounts were compromised?
- A. The clients' authentication tokens were impersonated and replayed.
- B. An XSS scripting attack was carried out on the server.
- C. The clients' usernames and passwords were transmitted in cleartext.
- D. A SQL injection attack was carried out on the server.
正解:C
質問 # 105
A security team has begun updating the risk management plan incident response plan and system security plan to ensure compliance with secunty review guidelines Which of the (olowing can be executed by internal managers to simulate and validate the proposed changes'?
- A. Tabletop exercise
- B. Control assessment
- C. Internal management review
- D. Peer review
正解:A
解説:
A tabletop exercise is a simulation of a security incident or scenario that involves the participation of key stakeholders and decision-makers. It can be used to test and validate the effectiveness of the organization's plans, policies, and procedures, such as the risk management plan, incident response plan, and system security plan. A tabletop exercise can also help identify gaps or weaknesses in the plans and improve the communication and coordination among the participants. An internal management review, a control assessment, a peer review, or a scripting are other possible methods to evaluate and validate a new product's security capabilities, but they are not as comprehensive or interactive as a tabletop exercise. Reference: https://www.csoonline.com/article/3444488/what-is-a-tabletop-exercise-how-to-run-a-security-scenario-in-6-steps.html
質問 # 106
An email analysis system notifies a security analyst that the following message was quarantined and requires further review.
Which of the following actions should the security analyst take?
- A. Immediately contact a purchasing agent to expedite.
- B. Purchase the gift cards and submit an expense report.
- C. Release the email for delivery due to its importance.
- D. Delete the email and block the sender.
正解:D
質問 # 107
A company requests a security assessment of its network. Permission is given, but no details are provided. It is discovered that the company has a web presence, and the company's IP address is 70.182.11.4. Which of the following Nmap commands would reveal common open ports and their versions?
- A. nmap - oV
- B. nmap -vO
- C. nmap -sv
正解:C
質問 # 108
A system administrator has reviewed the following output: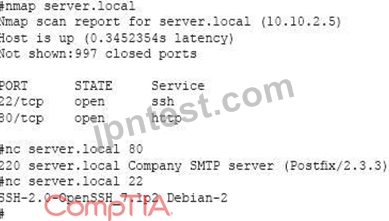
Which of the following can a system administrator infer from the above output?
- A. The company email server is running a non-standard port.
- B. The company web server has been compromised.
- C. The company is running a vulnerable SSH server.
- D. The company email server has been compromised.
正解:A
質問 # 109
An organization wants to ensure the privacy of the data that is on its systems Full disk encryption and DLP are already in use Which of the following is the BEST option?
- A. Update the AUP to restrict data sharing
- B. Require users to change their passwords more frequently
- C. Require all remote employees to sign an NDA
- D. Enforce geofencing to limit data accessibility
正解:D
解説:
Enforcing geofencing to limit data accessibility is the best option to ensure the privacy of the data that is on its systems. Geofencing is a technique that uses GPS or RFID technology to create a virtual geographic boundary around a specific location or area. Geofencing can be used to restrict data accessibility based on the location of the device or user that tries to access it. For example, geofencing can prevent employees from accessing sensitive data when they are outside the office premises or in a different country3. Geofencing can help protect data privacy and comply with data protection regulations that may vary across regions or jurisdictions.
質問 # 110
During a forensic investigation, a security analyst reviews some Session Initiation Protocol packets that came from a suspicious IP address. Law enforcement requires access to a VoIP call that originated from the suspicious IP address. Which of the following should the analyst use to accomplish this task?
- A. Netflow
- B. iptables
- C. Tcpdump
- D. Wireshark
正解:A
解説:
https://learningnetwork.cisco.com/s/question/0D53i00000KszWaCAJ/netflow-vs-packet-analyzer
質問 # 111
A security analyst is reviewing the following log from an email security service.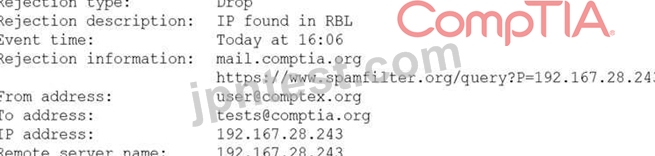
Which of the following BEST describes the reason why the email was blocked?
- A. The To address is invalid.
- B. The email originated from the www.spamfilter.org URL.
- C. The From address is invalid.
- D. The IP address was blacklisted.
- E. The IP address and the remote server name are the same.
正解:D
解説:
Explanation/Reference: https://www.webopedia.com/TERM/R/RBL.html
質問 # 112
......
検証済みのCS0-002問題集と解答で一年間無料最速更新:https://www.jpntest.com/shiken/CS0-002-mondaishu
