最新のCompTIA CS0-002のPDFと問題集で(2023)無料試験問題解答
あなたを合格させるCompTIA CySA+ CS0-002試験問題集で2023年11月29日には371問あります
CompTIA CS0-002試験は、サイバーセキュリティ分析のキャリアを追求したい個人を対象とした認定試験です。この認定は、ITプロフェッショナル向けのトレーニングと認定プログラムを提供するIT業界の主要な組織であるCompTIAによって提供されています。CompTIA CySA+認定試験は、候補者のサイバーセキュリティの脅威、脆弱性、およびリスクを特定し対処する能力をテストします。
CompTIA CS0-002(CompTIA Cybersecurity Analyst(CySA +)認定試験)は、サイバーセキュリティアナリストのスキルと知識を検証するために設計された、世界的に認められた認定試験です。この認定試験は雇用主に高く評価され、個人がサイバーセキュリティ分析の専門知識を証明する良い機会です。
質問 # 15
Wncn ol the following provides an automated approach 10 checking a system configuration?
- A. CI/CD
- B. OVAL
- C. SOAR
- D. Scripting
- E. SCAP
正解:E
解説:
SCAP stands for Security Content Automation Protocol, which is a set of standards and specifications that allows automated configuration and vulnerability management of systems. SCAP provides an automated approach to checking a system configuration by using standardized expressions and formats to evaluate the system's compliance with predefined policies or benchmarks. CI/CD, OVAL, scripting, or SOAR are other terms related to automation or security, but they do not provide an automated approach to checking a system configuration. Reference: https://csrc.nist.gov/projects/security-content-automation-protocol
質問 # 16
Which of the following BEST describes the process by which code is developed, tested, and deployed in small batches?
- A. SDLC
- B. Waterfall
- C. Agile
- D. Dynamic code analysis
正解:C
解説:
Reference:
https://www.cleverism.com/software-development-life-cycle-sdlc-methodologies/
質問 # 17
In order to meet regulatory compliance objectives for the storage of PHI, vulnerability scans must be conducted on a continuous basis.
The last completed scan of the network returned 5,682 possible vulnerabilities.
The Chief Information Officer (CIO) would like to establish a remediation plan to resolve all known issues.
Which of the following is the BEST way to proceed?
- A. Attempt to identify all false positives and exceptions, and then resolve all remaining items.
- B. Place assets that handle PHI in a sandbox environment, and then resolve all vulnerabilities.
- C. Hold off on additional scanning until the current list of vulnerabilities have been resolved.
- D. Reduce the scan to items identified as critical in the asset inventory, and resolve these issues first.
正解:D
質問 # 18
A security analyst is investigating a system compromise. The analyst verifies the system was up to date on OS patches at the time of the compromise. Which of the following describes the type of vulnerability that was MOST likely exploited?
- A. Insider threat
- B. Advanced persistent threat
- C. Buffer overflow
- D. Zero day
正解:D
質問 # 19
A security analyst is preparing for the company's upcoming audit. Upon review of the company's latest vulnerability scan, the security analyst finds the following open issues: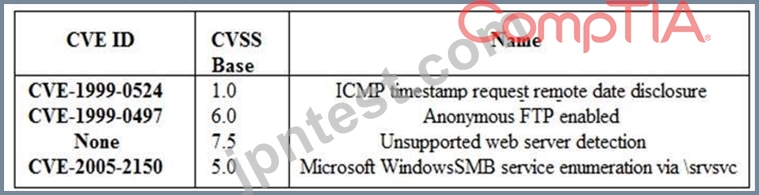
Which of the following vulnerabilities should be prioritized for remediation FIRST?
- A. Microsoft Windows SMB service enumeration via \srvsvc
- B. ICMP timestamp request remote date disclosure
- C. Anonymous FTP enabled
- D. Unsupported web server detection
正解:D
質問 # 20
A company is moving from the use of web servers hosted in an internal datacenter to a containerized cloud platform. An analyst has been asked to identify indicators of compromise in the containerized environment.
Which of the following would BEST indicate a running container has been compromised?
- A. A container from an approved software image has drifted
- B. An approved software orchestration container is running with root privileges
- C. A container from an approved software image fails to start
- D. A container from an approved software image has stopped responding
正解:A
質問 # 21
Which of the following BEST explains the function of a managerial control?
- A. To help design and implement the security planning, program development, and maintenance of the security life cycle
- B. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
- C. To guide the development of training, education, security awareness programs, and system maintenance
- D. To create data classification, risk assessments, security control reviews, and contingency planning
正解:A
質問 # 22
After examining a header and footer file, a security analyst begins reconstructing files by scanning the raw data bytes of a hard disk and rebuilding them. Which of the following techniques is the analyst using?
- A. Data recovery
- B. Metadata analysis
- C. Header analysis
- D. File carving
正解:D
質問 # 23
During a review of the vulnerability scan results on a server, an information security analyst notices the following: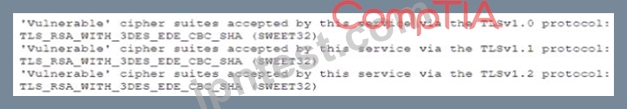
The MOST appropriate action for the analyst to recommend to developers is to change the web server so:
- A. It only accepts TLSvl 2
- B. It only accepts cipher suites using AES and SHA
- C. SSL/TLS is offloaded to a WAF and load balancer
- D. It no longer accepts the vulnerable cipher suites
正解:A
質問 # 24
A critical server was compromised by malware, and all functionality was lost. Backups of this server were taken; however, management believes a logic bomb may have been injected by a rootkit. Which of the following should a security analyst perform to restore functionality quickly?
- A. Stand up a new server and restore critical data from backups
- B. Restore the previous backup and scan with a live boot anti-malware scanner
- C. Work backward, restoring each backup until the server is clean
- D. Offload the critical data to a new server and continue operations
正解:B
質問 # 25
After running the cat file01.bin | hexdump -c command, a security analyst reviews the following output snippet:
00000000 ff d8 ft e0 00 10 4a 46 49 46 00 01 01 00 00 01 |......JFIF......| Which of the following digital-forensics techniques is the analyst using?
- A. Verifying the file type
- B. Debugging the binary file
- C. Implementing file carving
- D. Utilizing reverse engineering
- E. Reviewing the file hash
正解:A
解説:
This is the digital-forensics technique that the analyst is using by running the cat file01.bin | hexdump -c command. This command displays the contents of the binary file in hexadecimal and ASCII format, which can help identify the file type based on its header or signature. In this case, the output snippet shows that the file type is JPEG, as indicated by the ff d8 ff e0 bytes at the beginning and the JFIF string in ASCII.
質問 # 26
A system is experiencing noticeably slow response times, and users are being locked out frequently. An analyst asked for the system security plan and found the system comprises two servers: an application server in the DMZ and a database server inside the trusted domain. Which of the following should be performed NEXT to investigate the availability issue?
- A. Review the firewall logs.
- B. Review syslogs from critical servers.
- C. Install a WAF in front of the application server.
- D. Perform fuzzing.
正解:D
質問 # 27
An analyst determines a security incident has occurred Which of the following is the most appropnate NEXT step in an incident response plan?
- A. Consult the malware analysis process
- B. Consult the communications plan
- C. Consult the data classification process
- D. Consult the disaster recovery plan
正解:B
質問 # 28
A security analyst is trying to determine if a host is active on a network. The analyst first attempts the following: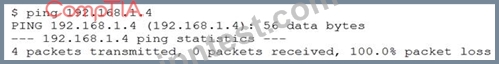
The analyst runs the following command next: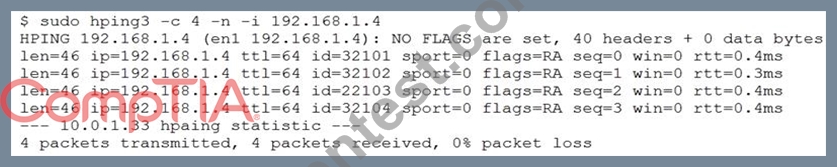
Which of the following would explain the difference in results?
- A. ICMP is being blocked by a firewall.
- B. The original ping command needed root permission to execute.
- C. The routing tables for ping and hping3 were different.
- D. hping3 is returning a false positive.
正解:A
質問 # 29
A security learn implemented a SCM as part for its security-monitoring program there is a requirement to integrate a number of sources Into the SIEM to provide better context relative to the events being processed.
Which of the following BEST describes the result the security learn hopes to accomplish by adding these sources?
- A. Continuous integration
- B. Workflow orchestration
- C. Machine learning
- D. Data enrichment
正解:D
質問 # 30
A security analyst needs to reduce the overall attack surface.
Which of the following infrastructure changes should the analyst recommend?
- A. Implement a cloud-based architecture.
- B. Increase the network segmentation.
- C. Implement a honeypot.
- D. Air gap sensitive systems.
正解:D
質問 # 31
NOTE: Question IP must be 192.168.192.123
During a network reconnaissance engagement, a penetration tester was given perimeter firewall ACLs to accelerate the scanning process. The penetration tester has decided to concentrate on trying to brute force log in to destination IP address 192.168.192.132 via secure shell.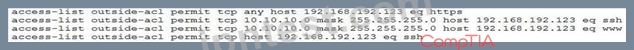
Given a source IP address of 10.10.10.30, which of the following ACLs will permit this access?
- A.

- B.

- C.

- D.

正解:D
質問 # 32
A company experienced a security compromise due to the inappropriate disposal of one of its hardware appliances. Sensitive information stored on the hardware appliance was not removed prior to disposal. Which of the following is the BEST manner in which to dispose of the hardware appliance?
- A. Dispose of all hardware appliances securely, thoroughly, and in compliance with company policies.
- B. Ensure the hardware appliance has the ability to encrypt the data before disposing of it.
- C. Return the hardware appliance to the vendor, as the vendor is responsible for disposal.
- D. Establish guidelines for the handling of sensitive information.
正解:A
解説:
Secure and thorough disposal can involve deleting or wiping all data from the hardware appliances, physically destroying or shredding them, or recycling them through certified vendors or programs. Compliance with company policies can help to ensure that the disposal follows the best practices and standards for data protection and environmental responsibility .
質問 # 33
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
- A. To reduce the attack surface
- B. To optimize system performance
- C. To create a system baseline
- D. To improve malware detection
正解:B
質問 # 34
While preparing of an audit of information security controls in the environment an analyst outlines a framework control that has the following requirements:
* All sensitive data must be classified
* All sensitive data must be purged on a quarterly basis
* Certificates of disposal must remain on file for at least three years This framework control is MOST likely classified as:
- A. corrective
- B. risk-based
- C. preventive
- D. prescriptive
正解:C
質問 # 35
During the security assessment of a new application, a tester attempts to log in to the application but receives the following message incorrect password for given username. Which of the following can the tester recommend to decrease the likelihood that a malicious attacker will receive helpful information?
- A. Disable error messaging for authentication
- B. Avoid using password-based authentication for the application
- C. Recognize that error messaging does not provide confirmation of the correct element of authentication
- D. Set the web page to redirect to an application support page when a bad password is entered.
正解:C
質問 # 36
A security analyst is running a routine vulnerability scan against a web farm. The farm consists of a single server acting as a load-balancing reverse proxy and offloads cryptographic processes to the backend servers. The backend servers consist of four servers that process the inquiries for the front end.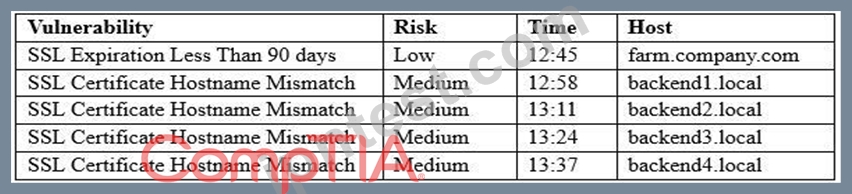
A web service SSL query of each server responds with the same output:
Connected (0x000003)
depth=0 /0=farm.company.com/CN=farm.company.com/OU=Domain Control Validated Which of the following results BEST addresses these findings?
- A. Create an exception in the vulnerability scanner, as the results and false positives and can be ignored safely
- B. Require that the application development team renews the farm certificate and includes a wildcard for the `local' domain in the certificate SAN field
- C. Notify the application development team of the findings and advise management of the results
- D. Advise the application development team that the SSL certificates on the backend servers should be revoked and reissued to match their hostnames
正解:A
質問 # 37
A business recently acquired a software company. The software company's security posture is unknown.
However, based on an assessment, there are limited security controls. No significant security monitoring exists. Which of the following is the NEXT step that should be completed to obtain information about the software company's security posture?
- A. Develop an asset inventory to determine the systems within the software company
- B. Baseline the software company's network to determine the ports and protocols in use.
- C. Perform penetration tests against the software company's Internal and external networks
- D. Review relevant network drawings, diagrams and documentation
正解:A
質問 # 38
A security team has begun updating the risk management plan, incident response plan, and system security plan to ensure compliance with security review guidelines. Which of the following can be executed by internal managers to simulate and validate the proposed changes?
- A. Internal management review
- B. Tabletop exercise
- C. Control assessment
- D. Peer review
正解:B
解説:
Explanation
According to the CompTIA CySA+ Certification Exam (CS0-002) study guide, a tabletop exercise can be executed by internal managers to simulate and validate changes to the risk management plan, incident response plan, and system security plan. In a tabletop exercise, participants discuss and work through a simulated scenario, usually in a classroom or conference room setting, to evaluate their readiness and understanding of the proposed changes. This type of exercise can help to identify any potential issues or gaps in the proposed changes and can provide valuable insights for refining and improving the plans.
質問 # 39
An organization has the following risk mitigation policy:
Risks with a probability of 95% or greater will be addressed before all others regardless of the impact.
All other prioritization will be based on risk value.
The organization has identified the following risks: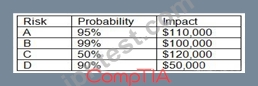
Which of the following is the order of priority for risk mitigation from highest to lowest?
- A. A, B, D, C
- B. D, A, C, B
- C. D, A, B, C
- D. A, B, C, D
正解:B
解説:
According to the risk mitigation policy, risks with a probability of 95% or greater will be addressed first, regardless of the impact. Therefore, risk D is the highest priority, as it has a probability of 95% and an impact of $100,000. The next priority is risk A, which has a probability of 90% and an impact of $200,000. The remaining risks will be prioritized based on their risk value, which is calculated by multiplying the probability and the impact. Risk C has a risk value of $40,000 (80% x $50,000), while risk B has a risk value of $30,000 (60% x $50,000). Therefore, risk C is higher priority than risk B.
質問 # 40
......
CompTIA CS0-002 認定を取得することは、候補者がサイバーセキュリティの概念、ツール、および方法論をしっかりと理解していることを潜在的な雇用主に示すものです。また、セキュリティインシデントの分析と対応能力を検証することで、現代のサイバーセキュリティの重要なスキルを証明します。この認定は、世界的に有名な組織や政府機関によって認められており、キャリアアップに向けた重要な資格となります。
CS0-002問題集はCompTIA CySA+認証済み試験問題と解答:https://www.jpntest.com/shiken/CS0-002-mondaishu
