CS0-002練習CompTIA高合格率回答あなたを試験は高確率で合格させます![2023]
最高の方法からパスCompTIA CySA+のCS0-002試験合格させます
CompTIA CS0-002試験は、85の多肢選択問題と性能ベースの問題から構成され、受験者は165分以内に回答する必要があります。試験は英語と日本語で利用可能で、受験者は認定を取得するために900点中750点以上の合格点を取得する必要があります。試験は、世界中のどのピアソンVUEテストセンターでも受験でき、受験者はCompTIAのウェブサイトで試験に登録できます。
質問 # 214
While conducting a cloud assessment, a security analyst performs a Prowler scan, which generates the following within the report: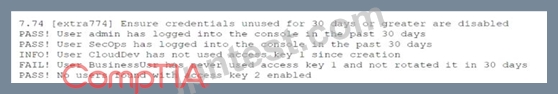
Based on the Prowler report, which of the following is the BEST recommendation?
- A. Delete access key 1.
- B. Delete access key 2.
- C. Delete BusinessUsr access key 1.
- D. Delete CloudDev access key 1.
正解:B
質問 # 215
Because some clients have reported unauthorized activity on their accounts, a security analyst is reviewing network packet captures from the company's API server. A portion of a capture file is shown below:
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="http://schemas.s/soap/envelope/
"><s:Body><GetIPLocation+xmlns="http://tempuri.org/">
<request+xmlns:a="http://schemas.somesite.org http://www.w3.org/2001/XMLSchema-instance
"></s:Body></s:Envelope> 192.168.1.22 - - api.somesite.com 200 0 1006 1001 0 192.168.1.22 POST /services/v1_0/Public/Members.svc/soap
<<a:Password>Password123</a:Password><a:ResetPasswordToken+i:nil="true"/>
<a:ShouldImpersonatedAuthenticationBePopulated+i:nil="true"/><a:Username>[email protected]
192.168.5.66 - - api.somesite.com 200 0 11558 1712 2024 192.168.4.89
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="
http://schemas.xmlsoap.org/soap/envelope/"><s:Body><GetIPLocation+xmlns="http://tempuri.org/">
<a:IPAddress>516.7.446.605</a:IPAddress><a:ZipCode+i:nil="true"/></request></GetIPLocation></s:Body><
192.168.1.22 - - api.somesite.com 200 0 1003 1011 307 192.168.1.22
POST /services/v1_0/Public/Members.svc/soap <s:Envelope+xmlns:s="
http://schemas.xmlsoap.org/soap/envelope/ http://tempuri.org/">
<request+xmlns:a="http://schemas.datacontract.org/2004/07/somesite.web+xmlns:i="
http://www.w3.org/2001/XMLSchema-instance
<a:ApiToken>kmL4krg2CwwWBan5BReGv5Djb7syxXTNKcWFuSjd</a:ApiToken><a:ImpersonateUserId>0<
<a:NetworkId>4</a:NetworkId><a:ProviderId>''1=1</a:ProviderId><a:UserId>13026046</a:UserId></a:Authe
192.168.5.66 - - api.somesite.com 200 0 1378 1209 48 192.168.4.89
Which of the following MOST likely explains how the clients' accounts were compromised?
- A. An XSS scripting attack was carried out on the server.
- B. The clients' authentication tokens were impersonated and replayed.
- C. A SQL injection attack was carried out on the server.
- D. The clients' usernames and passwords were transmitted in cleartext.
正解:D
質問 # 216
A cyber-security analyst is implementing a new network configuration on an existing network access layer to prevent possible physical attacks. Which of the following BEST describes a solution that would apply and cause fewer issues during the deployment phase?
- A. Configure 802.1X and EAPOL across the network
- B. Implement port security with one MAC address per network port of the switch.
- C. Implement software-defined networking and security groups for isolation
- D. Deploy network address protection with DHCP and dynamic VLANs.
正解:B
解説:
The security analyst should implement port security with one MAC address per network port of the switch. This will help prevent possible physical attacks on the network access layer, such as MAC flooding or MAC spoofing. Port security is a feature that allows a switch to limit the number of MAC addresses that can be learned on a specific port. By setting the limit to one MAC address per port, the switch will only allow traffic from the device that is connected to that port, and drop any traffic from other devices that try to use that port. This will prevent attackers from connecting unauthorized devices to the network or impersonating legitimate devices by changing their MAC addresses3.
質問 # 217
An analyst is conducting a log review and identifies the following snippet in one of the logs: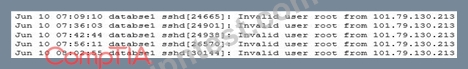
Which of the following MOST likely caused this activity?
- A. Forgotten password
- B. SQL injection
- C. Privilege escalation
- D. Brute force
正解:D
質問 # 218
A security analyst is running a tool against an executable of an unknown source. The Input supplied by the tool to the executable program and the output from the executable are shown below:
Which of the following should the analyst report after viewing this Information?
- A. A dynamic library that is needed by the executable a missing
- B. The executable attempted to execute a malicious command
- C. The toot caused a buffer overflow in the executable's memory
- D. Input can be crafted to trigger an Infection attack in the executable
正解:D
質問 # 219
A cybersecurity analyst is currently auditing a new Active Directory server for compliance. The analyst uses Nessus to do the initial scan, and Nessus reports the following: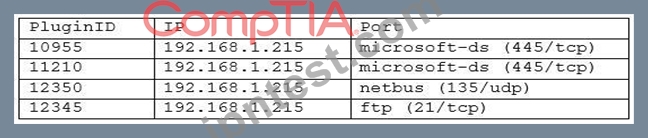
Which of the following critical vulnerabilities has the analyst discovered?
- A. Zero-day
- B. User enumeration
- C. Known backdoor
- D. Path disclosure
正解:C
質問 # 220
A security analyst needs to provide the development team with secure connectivity from the corporate network to a three-tier cloud environment. The developers require access to servers in all three tiers in order to perform various configuration tasks. Which of the following technologies should the analyst implement to provide secure transport?
- A. CASB
- B. Federation
- C. VPC
- D. VPN
正解:D
解説:
Explanation
A VPN is a secure network connection that allows users to access their private corporate networks over the internet, while keeping the connection encrypted and secure. This makes it an ideal solution for providing the development team with secure connectivity from the corporate network to a three-tier cloud environment.
https://www.comptia.org/content/virtual-private-networks
質問 # 221
A security analyst is reviewing the network security monitoring logs listed below: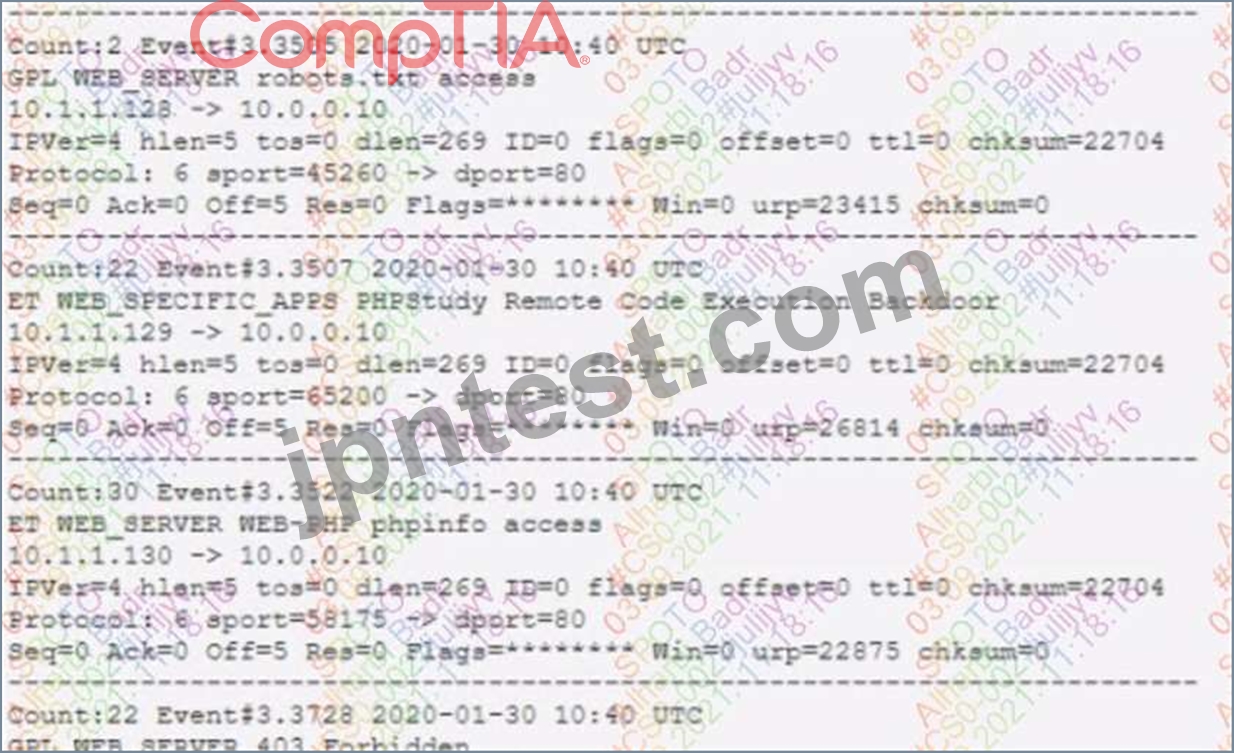
Which of the following is the analyst MOST likely observing? (Select TWO).
- A. 10.1.1.129 sent non-malicious requests, and the alert is a false positive.
- B. 10.1.1 .129 successfully exploited a vulnerability on the web server.
- C. 10.1.1.128 sent potential malicious traffic to the web server.
- D. 10.1.1.129 sent potential malicious requests to the web server.
- E. 10.1.1.128 sent malicious requests, and the alert is a false positive.
正解:B、E
質問 # 222
A customer notifies a security analyst that a web application is vulnerable to information disclosure The analyst needs to indicate the seventy of the vulnerability based on its CVSS score, which the analyst needs to calculate When analyzing the vulnerability the analyst realizes that tor the attack to be successful, the Tomcat configuration file must be modified Which of the following values should the security analyst choose when evaluating the CVSS score?
- A. Local
- B. Adjacent
- C. Physical
- D. Network
正解:A
解説:
The Common Vulnerability Scoring System (CVSS) is a standard for measuring the severity of vulnerabilities in software systems. One of the factors that affects the CVSS score is the attack vector, which describes how the vulnerability can be exploited. The possible values for the attack vector are network, adjacent network, local, or physical. In this case, the analyst should choose local as the value for the attack vector, because the Tomcat configuration file must be modified for the attack to be successful, which implies that the attacker needs local access to the system. Network, adjacent network, or physical are not appropriate values for the attack vector in this scenario. Reference: https://www.first.org/cvss/v3.1/specification-document#Vector-String
質問 # 223
When reviewing a compromised authentication server, a security analyst discovers the following hidden file: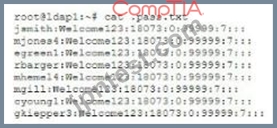
Further analysis shows these users never logged in to the server. Which of the following types of attacks was used to obtain the file and what should the analyst recommend to prevent this type of attack from reoccurring?
- A. A phishing attack was used to compromise the account. The analyst should recommend users install endpoint protection to disable phishing links.
- B. A rainbow tables attack was used to compromise the accounts. The analyst should recommend that future password hashes contains a salt.
- C. A password spraying attack was used to compromise the passwords. The analyst should recommend that all users receive a unique password.
- D. A rogue LDAP server is installed on the system and is connecting passwords. The analyst should recommend wiping and reinstalling the server.
正解:C
質問 # 224
A system's authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now. The cybersecurity group just performed a vulnerability scan with the partial set of results shown below: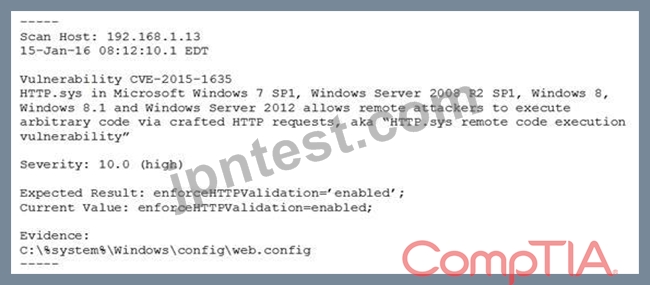
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A. Ignore it. This is false positive, and the organization needs to focus its efforts on other findings.
- B. Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- C. Ensure HTTP validation is enabled by rebooting the server.
- D. Accept this risk for now because this is a "high" severity, but testing will require more than the four days available, and the system ATO needs to be competed.
正解:B
質問 # 225
An organization subscribes to multiple third-party security intelligence feeds. It receives a notification from one of these feeds indicating a zero-day malware attack is impacting the SQL server prior to SP 2. The notification also indicates that infected systems attempt to communicate to external IP addresses on port 2718 to download additional payload. After consulting with the organization's database administrator, it is determined that there are several SQL servers that are still on SP 1, and none of the SQL servers would normally communicate over port 2718. Which of the following is the BEST mitigation step to implement until the SQL servers can be upgraded to SP 2 with minimal impact to the network?
- A. Create alert rules on the IDS for all outbound traffic on port 2718 from the IP addresses if the SQL servers running SQL SP 1
- B. Place all the SQL servers running SP 1 on a separate subnet On the firewalls, create a new rule blocking connections to destination addresses external to the organization's network
- C. On the organization's firewalls, create a new rule that blocks outbound traffic on port 2718 from the IP addresses of the servers running SQL SP 1
- D. On the SQL servers running SP 1, install vulnerability scanning software
正解:C
質問 # 226
An organization recently discovered some inconsistencies in the motherboards it received from a vendor. The organization's security team then provided guidance on how to ensure the authenticity of the motherboards it received from vendors.
Which of the following would be the BEST recommendation for the security analyst to provide'?
- A. The organization should use a certified, trusted vendor as part of the supply chain.
- B. The organization should ensure all motherboards are equipped with a TPM.
- C. The organization should maintain the relationship with the vendor and enforce vulnerability scans.
- D. The organization should evaluate current NDAs to ensure enforceability of legal actions.
正解:A
質問 # 227
A company employee downloads an application from the internet. After the installation, the employee begins experiencing noticeable performance issues, and files are appearing on the desktop.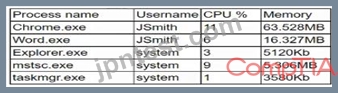
Which of the following processes will the secuhty analyst Identify as the MOST likely indicator of system compromise given the processes running in Task Manager?
- A. Word.exe
- B. mstsc.exe
- C. taskmgr.exe
- D. Chrome.exe
- E. Explorer.exe
正解:B
質問 # 228
A cybersecurity analyst is contributing to a team hunt on an organization's endpoints.
Which of the following should the analyst do FIRST?
- A. Write detection logic.
- B. Profile the threat actors and activities.
- C. Perform a process analysis.
- D. Establish a hypothesis.
正解:D
質問 # 229
An analyst performs a routine scan of a host using Nmap and receives the following output: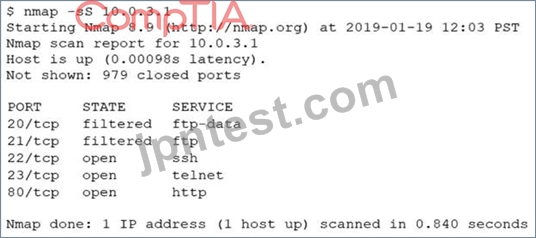
Which of the following should the analyst investigate FIRST?
- A. Port 23
- B. Port 80
- C. Port 22
- D. Port 21
正解:A
質問 # 230
A security analyst is investigating malicious traffic from an internal system that attempted to download proxy avoidance software as identified from the firewall logs but the destination IP is blocked and not captured. Which of the following should the analyst do?
- A. Take a snapshot
- B. Determine if DNS logging is enabled.
- C. Shut down the computer
- D. Review the network logs.
- E. Capture live data using Wireshark
正解:B
解説:
The DNS debug log provides extremely detailed data about all DNS information that is sent and received by the DNS server, similar to the data that can be gathered using packet capture tools such as network monitor. https://docs.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2012-r2-and-2012/dn800669(v=ws.11)#:~:text=The%20DNS%20debug%20log%20provides,tools%20such%20as%20network%20monitor.
質問 # 231
An information security analyst is working with a data owner to identify the appropriate controls to preserve the confidentiality of data within an enterprise environment One of the primary concerns is exfiltration of data by malicious insiders Which of the following controls is the MOST appropriate to mitigate risks?
- A. Data loss prevention
- B. OS fingerprinting
- C. Data deduplication
- D. Digital watermarking
正解:A
質問 # 232
......
CS0-002試験では、脅威管理、脆弱性管理、インシデント対応、コンプライアンスなど、サイバーセキュリティ分析に関連する幅広いトピックをカバーしています。この試験では、ネットワークセキュリティ、ログ分析、エンドポイント保護などの主要な技術的スキルもカバーしています。この試験は、セキュリティの脅威を特定して分析し、効果的なセキュリティソリューションを開発し、タイムリーで効果的な方法でセキュリティインシデントに対応する候補者の能力を評価するように設計されています。
CompTIA CS0-002事前に試験練習テストJPNTest: :https://www.jpntest.com/shiken/CS0-002-mondaishu
