[2024年01月]更新のCS0-002試験問題と有効なCS0-002問題集PDF
CS0-002ブレーン問題集学習ガイドにはヒントとコツで試験合格を目指そう
質問 # 74
An executive assistant wants to onboard a new cloud based product to help with business analytics and dashboarding. When of the following would be the BEST integration option for the service?
- A. Have the internal development team script connectivity and file translate to the new service.
- B. Create a dedicated SFTP sue and schedule transfers to ensue file transport security
- C. Utilize the cloud products API for supported and ongoing integrations
- D. Manually log in to the service and upload data files on a regular basis.
正解:D
質問 # 75
An organization that uses SPF has been notified emails sent via its authorized third-party partner are getting rejected A security analyst reviews the DNS entry and sees the following:
v=spf1 ip4:180.10.6.5 ip4:180.10.6.10 include:robustmail.com -all
The organization's primary mail server IP is 180.10 6.6, and the secondary mail server IP is 180.10.6.5. The organization's third-party mail provider is "Robust Mail" with the domain name robustmail.com.
Which of the following is the MOST likely reason for the rejected emails?
- A. The wrong domain name is in the SPF record.
- B. An incorrect IP version is being used.
- C. The primary and secondary email server IP addresses are out of sequence.
- D. SPF version 1 does not support third-party providers
正解:A
質問 # 76
A security analyst received a SIEM alert regarding high levels of memory consumption for a critical system. After several attempts to remediate the issue, the system went down. A root cause analysis revealed a bad actor forced the application to not reclaim memory. This caused the system to be depleted of resources.
Which of the following BEST describes this attack?
- A. Injection attack
- B. Denial of service
- C. Memory corruption
- D. Array attack
正解:C
解説:
Reference:
https://economictimes.indiatimes.com/definition/memory-corruption
質問 # 77
A company has recently launched a new billing invoice website for a few key vendors.
The cybersecurity analyst is receiving calls that the website is performing slowly and the pages sometimes time out.
The analyst notices the website is receiving millions of requests, causing the service to become unavailable.
Which of the following can be implemented to maintain the availability of the website?
- A. Whitelisting
- B. DMZ
- C. MAC filtering
- D. VPN
- E. Honeypot
正解:A
質問 # 78
An organization has a policy that requires servers to be dedicated to one function and unneeded services to be disabled. Given the following output from an Nmap scan of a web server:
Which of the following ports should be closed?
- A. 0
- B. 1
- C. 2
- D. 3
正解:B
質問 # 79
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.

正解:
解説:
質問 # 80
After receiving reports latency, a security analyst performs an Nmap scan and observes the following output:
Which of the following suggests the system that produced output was compromised?
- A. Standard HTP is open on the system and should be closed.
- B. MySQL services is identified on a standard PostgreSQL port.
- C. Secure shell is operating of compromise on this system.
- D. There are no indicators of compromise on this system.
正解:C
質問 # 81
The Cruel Executive Officer (CEO) of a large insurance company has reported phishing emails that contain malicious links are targeting the entire organza lion Which of the following actions would work BEST to prevent against this type of attack?
- A. Turn on full behavioral analysis to avert an infection
- B. Ensure EDR signatures are updated every day to avert infection.
- C. Reconfigure the EDR solution to perform real-time scanning of all files
- D. Modify the EDR solution to use heuristic analysis techniques for malware.
- E. Implement an EDR mail module that will rewrite and analyze email links.
正解:E
解説:
Explanation
If you're concerned about spear phishing and other advanced threats that may impact your organization, a next-gen EDR endpoint protection platform offers a lot of advantages over traditional antivirus.
質問 # 82
A company is experiencing a malware attack within its network. A security engineer notices many of the impacted assets are connecting outbound to a number of remote destinations and exfiltrating dat
a. The security engineer also see that deployed, up-to-date antivirus signatures are ineffective. Which of the following is the BEST approach to prevent any impact to the company from similar attacks in the future?
- A. Port security
- B. Data loss prevention
- C. Sinkholing
- D. IDS signatures
正解:D
質問 # 83
A system's authority to operate (ATO) is set to expire in four days. Because of other activities and limited staffing, the organization has neglected to start reauthentication activities until now. The cybersecurity group just performed a vulnerability scan with the partial set of results shown below: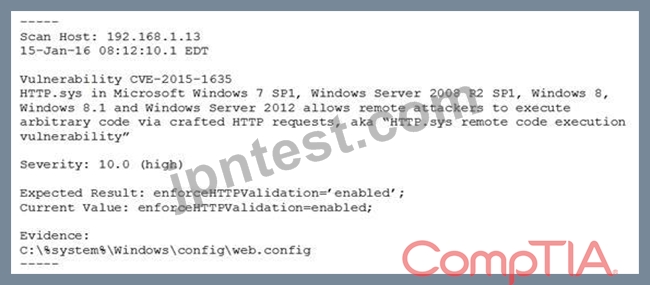
Based on the scenario and the output from the vulnerability scan, which of the following should the security team do with this finding?
- A. Accept this risk for now because this is a "high" severity, but testing will require more than the four days available, and the system ATO needs to be competed.
- B. Ignore it. This is false positive, and the organization needs to focus its efforts on other findings.
- C. Remediate by going to the web config file, searching for the enforce HTTP validation setting, and manually updating to the correct setting.
- D. Ensure HTTP validation is enabled by rebooting the server.
正解:C
質問 # 84
Which of the following would MOST likely be included in the incident response procedure after a security breach of customer PII?
- A. Internal network operations center
- B. Public relations
- C. Human resources
- D. Marketing
正解:B
質問 # 85
A security analyst on the threat-hunting team has developed a list of unneeded, benign services that are currently running as part of the standard OS deployment for workstations. The analyst will provide this list to the operations team to create a policy that will automatically disable the services for all workstations in the organization.
Which of the following BEST describes the security analyst's goal?
- A. To create a system baseline
- B. To reduce the attack surface
- C. To improve malware detection
- D. To optimize system performance
正解:B
解説:
Reducing the attack surface area means limiting the features and functions that are available to an attacker. For example, if I lock all doors to the facility with the exception of one, I have reduced the attack surface. Another term for reducing the attack surface area is system hardening because it involves ensuring that all systems have been hardened to the extent that is possible and still provide functionality
質問 # 86
The new Chief Technology Officer (CTO) is seeking recommendations for network monitoring services for the local intranet. The CTO would like the capability to monitor all traffic to and from the gateway, as well as the capability to block certain content. Which of the following recommendations would meet the needs of the organization?
- A. Recommend setup of IP filtering on both the internal and external interfaces of the gateway router.
- B. Recommend installation of an IPS on both the internal and external interfaces of the gateway router.
- C. Recommend installation of a firewall on the internal interface and a NIDS on the external interface of the gateway router.
- D. Recommend installation of an IDS on the internal interface and a firewall on the external interface of the gateway router.
正解:C
質問 # 87
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
Which of the following actions should be taken?
- A. Document the finding as an exception.
- B. Remove Microsoft Office from the server.
- C. Install a newer version of Microsoft Office on the server.
- D. Patch Microsoft Office on the server.
正解:D
質問 # 88
A security analyst is correlating, ranking, and enriching raw data into a report that will be interpreted by humans or machines to draw conclusions and create actionable recommendations Which of the following steps in the intelligence cycle is the security analyst performing?
- A. Data collection
- B. Analysis and production
- C. Dissemination and evaluation
- D. Planning and direction
- E. Processing and exploitation
正解:B
解説:
Explanation
Analysis is a human process that turns processed information into intelligence that can inform decisions.
Depending on the circumstances, the decisions might involve whether to investigate a potential threat, what actions to take immediately to block an attack, how to strengthen security controls, or how much investment in additional security resources is justified. https://www.recordedfuture.com/threat-intelligence-lifecycle-phases
質問 # 89
A vulnerability assessment solution is hosted in the cloud This solution will be used as an accurate inventory data source for both the configuration management database and the governance nsk and compliance tool An analyst has been asked to automate the data acquisition Which of the following would be the BEST way to acqutre the data'
- A. Machine learning
- B. SOAR
- C. CSV export
- D. API
正解:D
解説:
An example of API is google weather app, using the weather channel's API to collect accurate weather data and broadcast it on goggle weather app, so google doesn't have to do it their selves API stands for application programming interface, which is a set of rules and protocols that allows different software applications or components to communicate and exchange data. Using an API would be the best way to acquire data from a cloud-based vulnerability assessment solution for both the configuration management database and the governance risk and compliance tool, because it would allow automated and standardized data transfer between different systems. CSV export, SOAR, or machine learning are not methods of data acquisition, but rather formats or tools that can be used for data analysis or processing. Reference: https://www.redhat.com/en/topics/api/what-are-application-programming-interfaces
質問 # 90
......
CS0-002試験問題無料PDFダウンロード 最近更新された問題です:https://www.jpntest.com/shiken/CS0-002-mondaishu
