2023年04月05日に更新された最新のJPNTest CS0-002試験問題リアルCS0-002問題集で
CS0-002別格な問題集で最上級の成績にさせるCS0-002問題
質問 173
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets: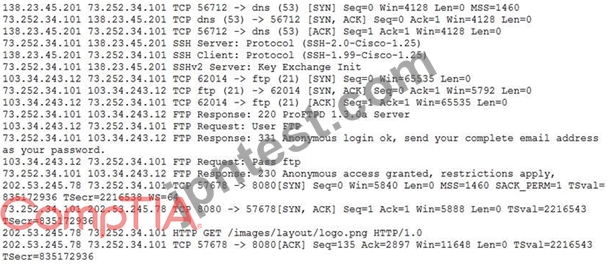
Which of the following traffic patterns or data would be MOST concerning to the security analyst?
- A. Port used for SMTP traffic from 73.252.34.101
- B. Ports used for HTTP traffic from 202.53.245.78
- C. Anonymous access granted by 103.34.243.12
- D. Unencrypted password sent from 103.34.243.12
正解: C
質問 174
A company's data is still being exfiltered to business competitors after the implementation of a DLP solution. Which of the following is the most likely reason why the data is still being compromised?
- A. DRM must be implemented with the DLP solution
- B. Users are not labeling the appropriate data sets
- C. DLP solutions are only effective when they are implemented with disk encryption
- D. Printed reports from the database contain sensitive information
正解: A
質問 175
A company's Chief Information Security Officer (CISO) is concerned about the integrity of some highly confidential files. Any changes to these files must be tied back to a specific authorized user's activity session.
Which of the following is the BEST technique to address the CISO's concerns?
- A. Use Wireshark to scan all traffic to and from the directory. Monitor the files for unauthorized changes.
- B. Configure DLP to reject all changes to the files without pre-authorization. Monitor the files for unauthorized changes.
- C. Regularly use SHA-256 to hash the directory containing the sensitive information. Monitor the files for unauthorized changes.
- D. Place a legal hold on the files. Require authorized users to abide by a strict time context access policy.
Monitor the files for unauthorized changes.
正解: B
質問 176
Which of the following will allow different cloud instances to share various types of data with a minimal amount of complexity?
- A. Application log collectors
- B. Reverse engineering
- C. API integration
- D. Scripting
- E. Workflow orchestration
正解: C
質問 177
A financial institution's business unit plans to deploy a new technology in a manner that violates existing information security standards. Which of the following actions should the Chief Information Security Officer (CISO) take to manage any type of violation?
- A. Enforce the existing security standards and controls.
- B. Enforce the standard permits.
- C. Perform research and propose a better technology.
- D. Perform a risk analysis and qualify the risk with legal.
正解: D
解説:
The International Standards Organization, or ISO, develops standards for businesses around the world so that they may operate using a uniform set of best practices. These standards are not enforceable laws, but companies who choose to follow them stand to gain international credibility from their compliance; standards are set as guidance for best practices but are not enforceable laws
質問 178
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
Which of the following actions should be taken?
- A. Document the finding as an exception.
- B. Remove Microsoft Office from the server.
- C. Patch Microsoft Office on the server.
- D. Install a newer version of Microsoft Office on the server.
正解: C
質問 179
To validate local system-hardening requirements, which of the following types of vulnerability scans would work BEST to verify the scanned device meets security policies?
- A. DACS
- B. DAST
- C. SAST
- D. SCAP
正解: D
質問 180
A critical server was compromised by malware, and all functionality was lost. Backups of this server were taken; however, management believes a logic bomb may have been injected by a rootkit. Which of the following should a security analyst perform to restore functionality quickly?
- A. Work backward, restoring each backup until the server is clean
- B. Offload the critical data to a new server and continue operations
- C. Restore the previous backup and scan with a live boot anti-malware scanner
- D. Stand up a new server and restore critical data from backups
正解: D
質問 181
A security analyst suspects a malware infection was caused by a user who downloaded malware after clicking http://<malwaresource>/a.php in a phishing email.
To prevent other computers from being infected by the same malware variation, the analyst should create a rule on the __________.
- A. proxy to block all connections to <malwaresource>.
- B. IDS to match the malware sample.
- C. email server that automatically deletes attached executables.
- D. firewall to block connection attempts to dynamic DNS hosts.
正解: B
質問 182
A security analyst discovers a vulnerability on an unpatched web server that is used for testing machine learning on Bing Data sets. Exploitation of the vulnerability could cost the organization $1.5 million in lost productivity. The server is located on an isolated network segment that has a 5% chance of being compromised. Which of the following is the value of this risk?
- A. $75.000
- B. $1.5 million
- C. $300.000
- D. $1.425 million
正解: A
質問 183
A system administrator is doing network reconnaissance of a company's external network to determine the vulnerability of various services that are running. Sending some sample traffic to the external host, the administrator obtains the following packet capture: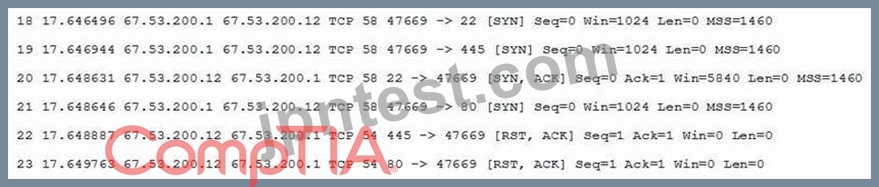
Based on the output, which of the following services should be further tested for vulnerabilities?
- A. SSH
- B. HTTPS
- C. HTTP
- D. SMB
正解: D
質問 184
A security analyst wants to identify which vulnerabilities a potential attacker might initially exploit if the network is compromised. Which of the following would provide the BEST results?
- A. Baseline configuration assessment
- B. Uncredentialed scan
- C. External penetration test
- D. Network ping sweep
正解: B
質問 185
A security administrator recently deployed a virtual honeynet. The honeynet is not protected by the company's firewall, while all production networks are protected by a stateful firewall. Which of the following would BEST allow an external penetration tester to determine which one is the honeynet's network?
- A. TCP ACK scan
- B. Fuzzer
- C. Banner grab
- D. Packet analyzer
正解: A
質問 186
A security analyst is evaluating two vulnerability management tools for possible use in an organization. The analyst set up each of the tools according to the respective vendor's instructions and generated a report of vulnerabilities that ran against the same target server.
Tool A reported the following: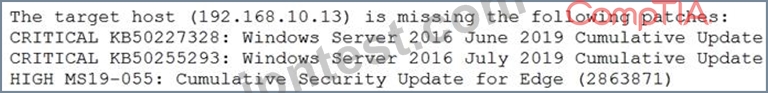
Tool B reported the following:
Which of the following BEST describes the method used by each tool? (Choose two.)
- A. Tool A is unauthenticated.
- B. Tool B is unauthenticated.
- C. Tool A is agent based.
- D. Tool A used fuzzing logic to test vulnerabilities.
- E. Tool B utilized machine learning technology.
- F. Tool B is agent based.
正解: A,F
質問 187
An organization has recently found some of its sensitive information posted to a social media site.
An investigation has identified large volumes of data leaving the network with the source traced back to host 192.168.1.13. An analyst performed a targeted Nmap scan of this host with the results shown below: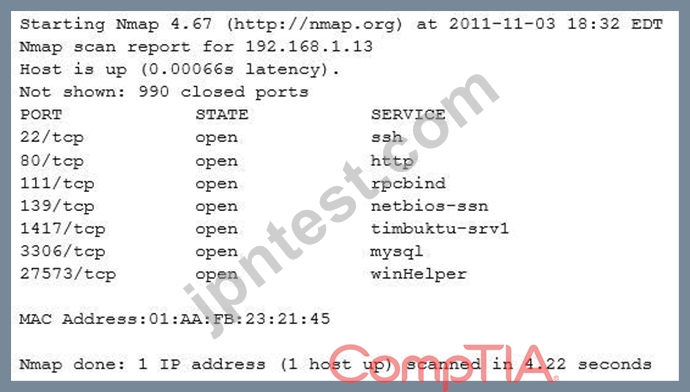
Subsequent investigation has allowed the organization to conclude that all of the well-known, standard ports are secure. Which of the following services is the problem?
- A. mysql
- B. ssh
- C. winHelper
- D. rpcbind
- E. timbuktu-serv1
正解: E
質問 188
When investigating a report of a system compromise, a security analyst views the following /var/log/secure log file: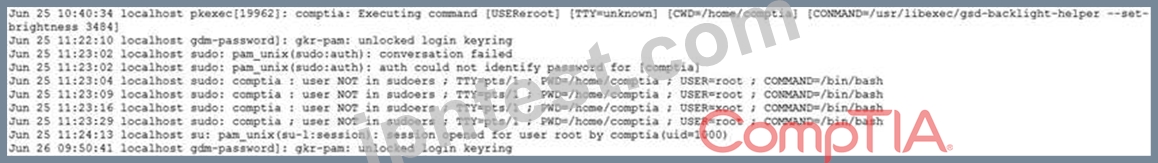
Which of the following can the analyst conclude from viewing the log file?
- A. The comptia user knows the root password.
- B. The comptia user knows the sudo password.
- C. The comptia user executed the sudo su command.
- D. The comptia user added himself or herself to the /etc/sudoers file.
正解: A
解説:
the user is not in the sudoers file. you use your own password for that. the user used the su command to switch user accounts. when no user is specified, the su command defaults to the root account. the user is now logged into the root account. you need to know the root password to log into the root account.
質問 189
The inability to do remote updates of certificates, keys, software, and firmware is a security issue commonly associated with:
- A. smartphones
- B. firewalls and UTM devices
- C. HVAC control systems
- D. web servers on private networks
正解: B
質問 190
An organization has several systems that require specific logons Over the past few months, the security analyst has noticed numerous failed logon attempts followed by password resets. Which of the following should the analyst do to reduce the occurrence of legitimate failed logons and password resets?
- A. Perform a manual privilege review
- B. Adjust the current monitoring and logging rules
- C. Use SSO across all applications
- D. Implement multifactor authentication
正解: C
質問 191
During the security assessment of a new application, a tester attempts to log in to the application but receives the following message incorrect password for given username. Which of the following can the tester recommend to decrease the likelihood that a malicious attacker will receive helpful information?
- A. Recognize that error messaging does not provide confirmation of the correct element of authentication
- B. Disable error messaging for authentication
- C. Avoid using password-based authentication for the application
- D. Set the web page to redirect to an application support page when a bad password is entered.
正解: B
質問 192
A security analyst received a series of antivirus alerts from a workstation segment, and users reported ransomware messages. During lessons- learned activities, the analyst determines the antivirus was able to alert to abnormal behavior but did not stop this newest variant of ransomware. Which of the following actions should be taken to BEST mitigate the effects of this type of threat in the future?
- A. Installing a firewall between the workstations and Internet
- B. Purchasing cyber insurance
- C. Enabling application blacklisting
- D. Enabling sandboxing technology
正解: D
質問 193
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the desk ticket queue.
INSTRUCTIONS
Click on me ticket to see the ticket details Additional content is available on tabs within the ticket First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu If at any time you would like to bring back the initial state of the simulation, please click the Reset All button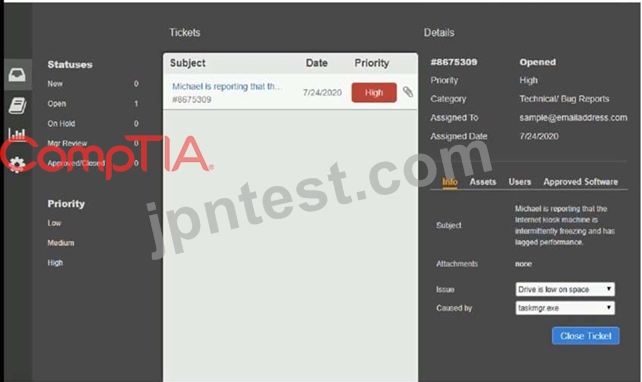
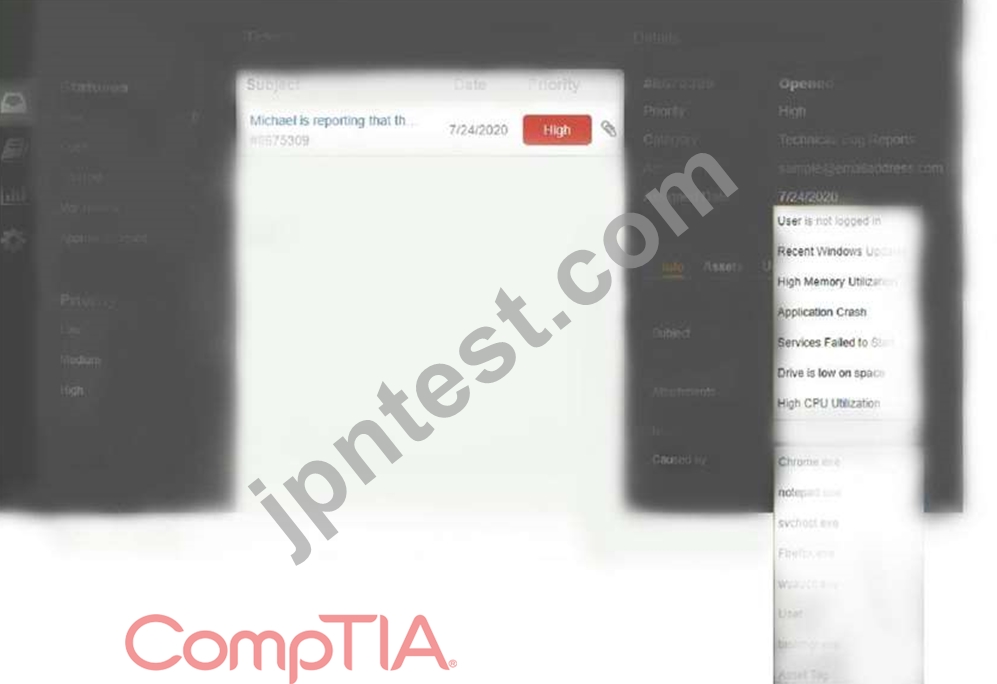
正解:
解説: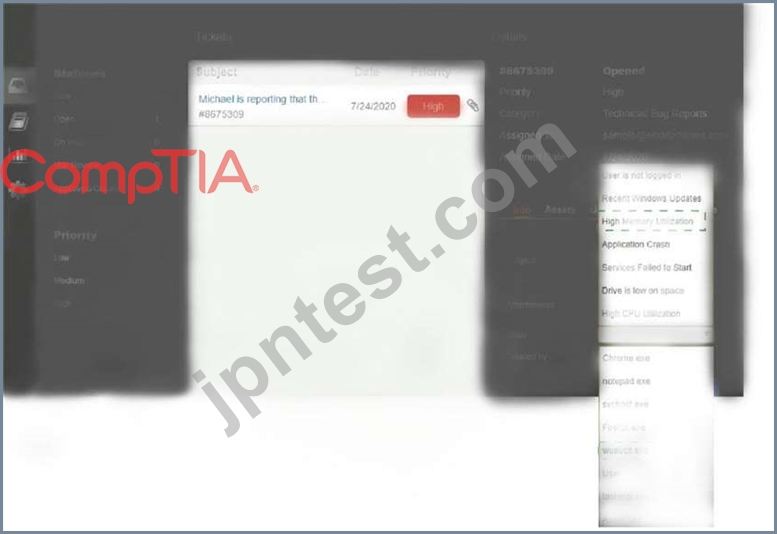
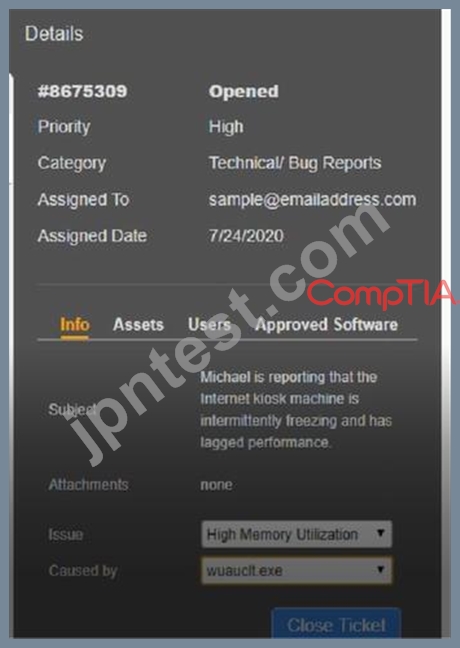
質問 194
A development team signed a contract that requires access to an on-premises physical server. Access must be restricted to authorized users only and cannot be connected to the Internet.
Which of the following solutions would meet this requirement?
- A. Establish a hosted SSO.
- B. Implement a CASB.
- C. Air gap the server.
- D. Virtualize the server.
正解: A
質問 195
A penetration tester is preparing for an audit of critical systems that may impact the security of the environment. This includes the external perimeter and the internal perimeter of the environment.
During which of the following processes is this type of information normally gathered?
- A. Authorization
- B. Scoping
- C. Enumeration
- D. Timing
正解: B
質問 196
......
CS0-002試験問題集でベストCS0-002試験問題を試そう:https://www.jpntest.com/shiken/CS0-002-mondaishu
