2023年最新の実際に出ると確認されたCS0-002試験問題集と解答でCS0-002無料更新
実際問題を使ってCS0-002問題集で100%無料CS0-002試験問題集
CompTIAサイバーセキュリティアナリスト(CySA +)認定は、高度な知識とスキルを持つサイバーセキュリティ専門家を求める雇用主に高く評価されています。この認定は、グローバルに認められており、サイバーセキュリティ専門家が自分の専門知識を示し、キャリアの見通しを向上させるための優れた方法です。この試験は、サイバーセキュリティに経験があり、キャリアを次のレベルに進めたい人に最適です。
CySA+認定試験に備えるために、候補者はテキストブック、オンラインコース、練習問題など、様々な教材を活用することができます。サイバーセキュリティにおける実践的な経験を持つこと、最新のセキュリティトレンドや技術について常に最新情報を得ることが重要です。CySA+認定試験に合格することで、プロフェッショナルは就職市場で競争優位性を獲得し、サイバーセキュリティ分野でキャリアを進めることができます。
CySA+認定は、政府機関、医療機関、金融機関、サイバーセキュリティベンダーなど、多くの組織や産業に認められています。この認定は、サイバーセキュリティ分野でキャリアを進めたい人にとって貴重な資産です。認定されたプロフェッショナルがセキュリティインシデントや脅威を特定し、対応する必要なスキルと知識を持っていることを雇用主に示します。
質問 # 23
During a review of recent network traffic, an analyst realizes the team has seen this same traffic multiple times in the past three weeks, and it resulted in confirmed malware activity The analyst also notes there is no other alert in place for this traffic After resolving the security incident, which of the following would be the BEST action for the analyst to take to increase the chance of detecting this traffic in the future?
- A. Report the security incident to a manager for inclusion in the daily report
- B. Share details of the security incident with the organization's human resources management team
- C. Note the secunty incident so other analysts are aware the traffic is malicious
- D. Communicate the secunty incident to the threat team for further review and analysis
正解:D
質問 # 24
A development team signed a contract that requires access to an on-premises physical server. Access must be restricted to authorized users only and cannot be connected to the Internet.
Which of the following solutions would meet this requirement?
- A. Establish a hosted SSO.
- B. Air gap the server.
- C. Implement a CASB.
- D. Virtualize the server.
正解:B
質問 # 25
A security analyst performs various types of vulnerability scans. Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.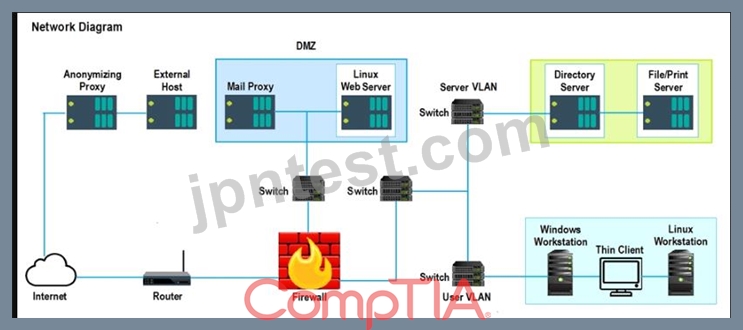
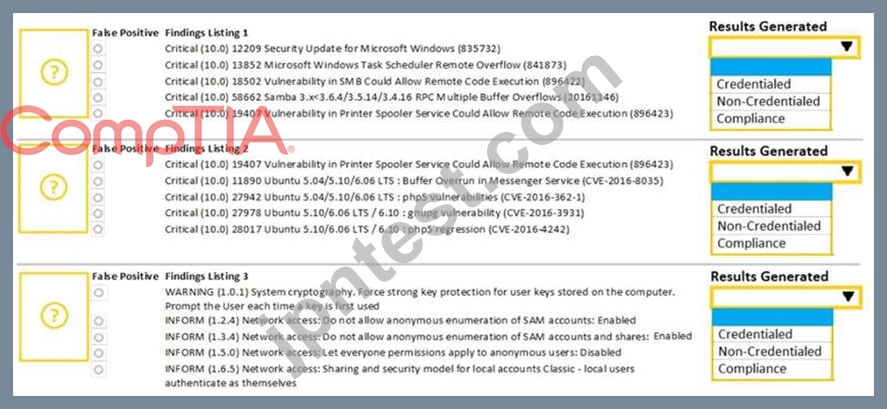
正解:
解説: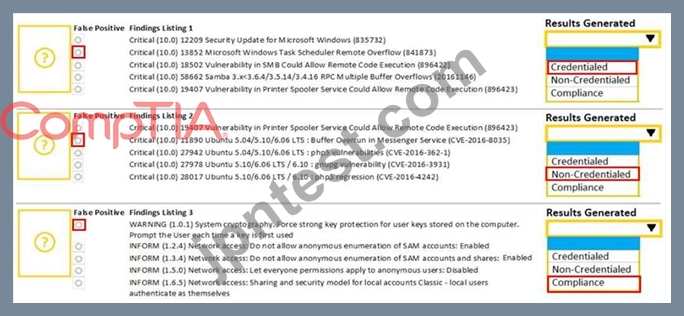
質問 # 26
Some hard disks need to be taken as evidence for further analysis during an incident response Which of the following procedures must be completed FIRST for this type of evtdertce acquisition?
- A. Extract the hard drives from the compromised machines and then plug them into a forensics machine to apply encryption over the stored data to protect it from non-authorized access
- B. Perform a disk sanitation using the command 8dd if=/daT/zaro of=/daT/adc ba=iM over the media that wil receive a copy of the coHected data
- C. Build the chain-of-custody document, noting the media model senal number size vendor, date, and time of acquisition
- D. Execute the command #dd if=/dev/ada of=/dev/adc ba=5i2 to clone the evidence data to external media to prevent any further change
正解:C
質問 # 27
After receiving reports latency, a security analyst performs an Nmap scan and observes the following output:
Which of the following suggests the system that produced output was compromised?
- A. There are no indicators of compromise on this system.
- B. Standard HTP is open on the system and should be closed.
- C. Secure shell is operating of compromise on this system.
- D. MySQL services is identified on a standard PostgreSQL port.
正解:A
質問 # 28
A security team wants to make SaaS solutions accessible from only the corporate campus.
Which of the following would BEST accomplish this goal?
- A. IP restrictions
- B. Reverse proxy
- C. Single sign-on
- D. Geofencing
正解:D
質問 # 29
An analyst performs a routine scan of a host using Nmap and receives the following output: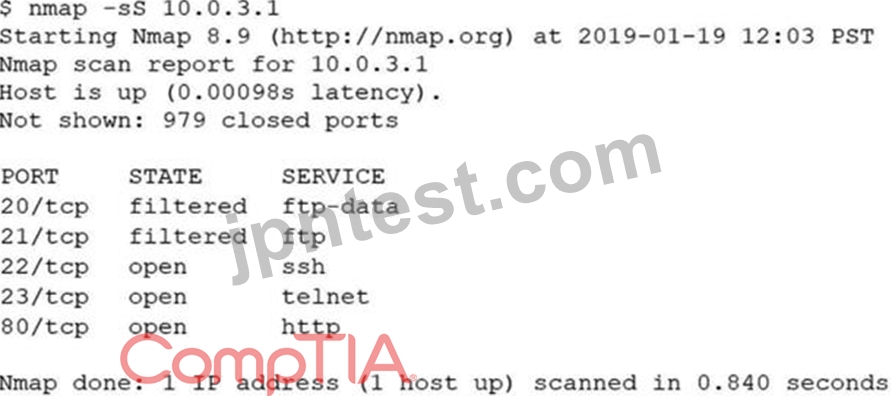
Which of the following should the analyst investigate FIRST?
- A. Port 23
- B. Port 80
- C. Port 21
- D. Port 22
正解:A
質問 # 30
A computer at a company was used to commit a crime. The system was seized and removed for further analysis. Which of the following is the purpose of labeling cables and connections when seizing the computer system?
- A. To capture the system configuration as it was at the time it was removed
- B. To document the model, manufacturer, and type of cables connected
- C. To maintain the chain of custody
- D. To block any communication with the computer system from attack
正解:A
質問 # 31
An analyst is responding 10 an incident involving an attack on a company-owned mobile device that was being used by an employee to collect data from clients in the held. Maiware was loaded on the device via the installation of a third-party software package The analyst has baselined the device Which of the following should the analyst do to BEST mitigate future attacks?
- A. Update the maiware catalog
- B. Implement MDM
- C. Patch the mobile device's OS
- D. Block third-party applications
正解:D
解説:
Blocking third-party applications would be the best way to mitigate future attacks on company-owned mobile devices that are used by employees to collect data from clients in the field. Third-party applications are applications that are not developed or authorized by the device manufacturer or operating system provider1. Third-party applications can pose a security risk for mobile devices, as they may contain malware, spyware, or other malicious code that can compromise the device or its data2. Blocking third-party applications can help prevent employees from installing unauthorized or untrusted applications on company-owned mobile devices and reduce the attack surface.
質問 # 32
Which of the following can detect vulnerable third-parly libraries before code deployment?
- A. Static analysis
- B. Impact analysis
- C. Dynamic analysis
- D. Protocol analysis
正解:A
質問 # 33
A code review reveals a web application is using lime-based cookies for session management. This is a security concern because lime-based cookies are easy to:
- A. decrypt.
- B. guess.
- C. parameterize.
- D. decode.
正解:D
解説:
Lime-based cookies are a type of cookies that use lime encoding to store data in a web browser. Lime encoding is a simple substitution cipher that replaces each character in a string with another character based on a fixed key. Lime-based cookies are easy to decode because the key is publicly available and the encoding algorithm is simple. Anyone who intercepts or accesses the lime-based cookies can easily decode them and read the data stored in them. This is a security concern because lime-based cookies are often used for session management, which means they store information about the user's identity and preferences on a web application. If an attacker can decode the lime-based cookies, they can impersonate the user or access their sensitive information.
質問 # 34
A company that is hiring a penetration tester wants to exclude social engineering from the list of authorized activities.
Which of the following documents should include these details?
- A. Rules of engagement
- B. Memorandum of understanding
- C. Acceptable use policy
- D. Service level agreement
- E. Master service agreement
正解:A
質問 # 35
A small electronics company decides to use a contractor to assist with the development of a new FPGA-based device. Several of the development phases will occur off-site at the contractor's labs.
Which of the following is the main concern a security analyst should have with this arrangement?
- A. Development phases occurring at multiple sites may produce change management issues.
- B. FPGA applications are easily cloned, increasing the possibility of intellectual property theft.
- C. Making multiple trips between development sites increases the chance of physical damage to the FPGAs.
- D. Moving the FPGAs between development sites will lessen the time that is available for security testing.
正解:B
質問 # 36
A security analyst reviews the following aggregated output from an Nmap scan and the border firewall ACL: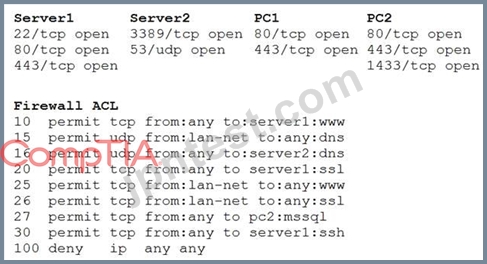
Which of the following should the analyst reconfigure to BEST reduce organizational risk while maintaining current functionality?
- A. Firewall
- B. PC1
- C. Server2
- D. PC2
- E. Server1
正解:D
質問 # 37
An analyst wants to identify hosts that are connecting to the external FTP servers and what, if any, passwords are being used. Which of the following commands should the analyst use?
- A. tcpdump -X dst port 21
- B. telnet ftp.server 21
- C. ftp ftp.server -p 21
- D. nmap -o ftp.server -p 21
正解:A
質問 # 38
A Chief Executive Officer (CEO) is concerned the company will be exposed to data sovereignty issues as a result of some new privacy regulations to help mitigate this risk. The Chief Information Security Officer (CISO) wants to implement an appropriate technical control. Which of the following would meet the requirement?
- A. Data masking procedures
- B. Regular business impact analysis functions
- C. Geographic access requirements
- D. Enhanced encryption functions
正解:C
解説:
Data Sovereignty means that data is subject to the laws and regulations of the geographic location where that data is collected and processed. Data sovereignty is a country-specific requirement that data must remain within the borders of the jurisdiction where it originated. At its core, data sovereignty is about protecting sensitive, private data and ensuring it remains under the control of its owner. You're only worried about that if you're in multiple locations. . https://www.virtru.com/blog/gdpr-data-sovereignty-matters-globally
質問 # 39
For machine learning to be applied effectively toward security analysis automation, it requires .
- A. a multicore, multiprocessor system.
- B. a threat feed API.
- C. anomalous traffic signatures.
- D. relevant training data.
正解:D
質問 # 40
It is important to parameterize queries to prevent __________.
- A. a memory overflow that executes code with elevated privileges.
- B. the execution of unauthorized actions against a database.
- C. the establishment of a web shell that would allow unauthorized access.
- D. the queries from using an outdated library with security vulnerabilities.
正解:B
質問 # 41
A security analyst is performing ongoing scanning and continuous monitoring of the corporate datacenter. Over time, these scans are repeatedly showing susceptibility to the same vulnerabilities and an increase in new vulnerabilities on a specific group of servers that are clustered to run the same application. Which of the following vulnerability management processes should be implemented?
- A. Frequent server scanning
- B. Automated report generation
- C. Group policy modification
- D. Regular patch application
正解:D
質問 # 42
An organizational policy requires one person to input accounts payable and another to do accounts receivable. A separate control requires one person to write a check and another person to sign all checks greater than $5,000 and to get an additional signature for checks greater than $10,000. Which of the following controls has the organization implemented?
- A. Dual control
- B. Job rotation
- C. Segregation of duties
- D. Non-repudiaton
正解:C
解説:
Segregation of duties is a security control that requires multiple people to be involved with completing a task. This helps prevent fraud, as it ensures that no one individual has the ability to commit fraud or make mistakes without other people being aware of it
質問 # 43
......
合格させるCS0-002試験問題は更新された277問あります:https://www.jpntest.com/shiken/CS0-002-mondaishu
